This week is all about some new and exiting functionality related to Microsoft Defender for Endpoint (MDE) that was announced around Microsoft Ignite. That new and exiting functionality is that MDE risk signals can now be used in app protection policies for Android and iOS. Those signals are based on the protection against phishing, unsafe network connections (on Android and iOS), and malicious apps (on Android only). That enables the usage of MDE on unmanaged devices for even better protection of work data. This behavior can be achieved by configuring an integration between MDE and Microsoft Intune, to send the required signals to Microsoft Intune, and by configuring an app protection policy, to create a conditional launch for the app, based on the signals provided by MDE. This post will go through those configurations and it will show the user experience.
Important: At the moment of writing this article, this functionality is still in preview.
Note: More information about getting started with MDE for iOS can be found here and more information about getting started with MDE for Android can be found here.
Integration of Microsoft Defender for Endpoint with Microsoft Intune
The first action is to configure the integration between MDE and Microsoft Intune. That integration makes sure that the information about the risk signals can be provided to Microsoft Intune for usage within the app protection policy evaluation. Similar actions are also required for using the risk signals with compliance policies. More information about that can be found in the earlier noted blog posts. The integration requires a configuration in Microsoft Defender Security Center and in Microsoft Endpoint Manager admin center.
Enable Microsoft Intune connection in Microsoft Defender Security Center
The connection with Microsoft Intune can be enabled in Microsoft Defender Security Center. This is a generic configuration that is applicable to any supported platform and to compliance policies and app protection policies. When this connection is already used for another platform, or use case, these actions can be ignored. The following two steps described the steps to enable the Microsoft Intune connection.
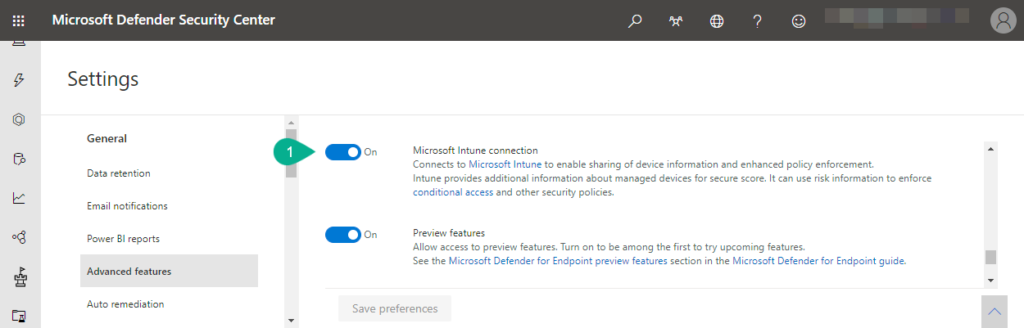
- Open the Microsoft Defender Security Center portal and navigate to Settings > Advanced features to open the Settings page for the advanced features
- On the Settings page, scroll down to Microsoft Intune connection (as shown in Figure 1, with number 1) and switch the slider to On
Enable Android and iOS devices in Microsoft Endpoint Manager admin center
When the connection with Microsoft Intune is established, a configuration can be done per platform to use risk signals – provided via the connection – for app protection policy evaluation. The following two steps enable Android and iOS to use the MDE risk information for app protection policy evaluation.
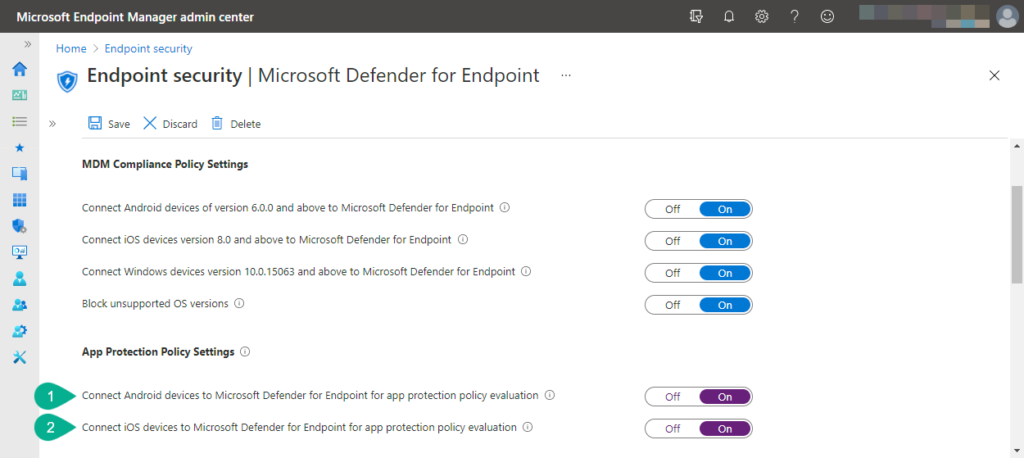
- Open the Microsoft Endpoint Manager admin center portal and navigate to Endpoint security > Microsoft Defender for Endpoint to open the Endpoint security | Microsoft Defender for Endpoint blade
- On the Endpoint security | Microsoft Defender for Endpoint blade, navigate to the setting Connect Android devices to Microsoft Defender for Endpoint for app protection policy evaluation (as shown in Figure 2, with number 1) and Connect iOS devices to Microsoft Defender for Endpoint for app protection policy evaluation (as shown in Figure 2, with number 2) and switch the sliders to On
Configuration of the app protection policy for Android and iOS devices
The second action is to configure the app protection policies for Android and/or iOS devices. Those app protection policies can be used to create a conditional launch configuration with a device condition that can be used to evaluate the risk information of MDE, before starting the app. The following steps walk through the creation of an app protection policy – for Android and iOS – with the focus on the configuration of the device conditions in the conditional launch configuration.
- Open the Microsoft Endpoint Manager admin center portal and navigate to Apps > App protection policies to open the Apps | App protection policies blade
- On the Apps | App protection policies blade and click Create policy > Android or iOS/iPadOS to open the Create policy wizard
Note: Select either Android or iOS/iPadOS, depending on the platform that should be targeted. The conditional launch configuration is the same for both platforms.
- On the Basics page, specify a Name and Description and click Next
- On the Apps page, select with Device types at least Unmanaged devices, select the required apps and click Next
Note: Use this section to configure every app that should verify MDE risk information before launch, by selecting the required public and custom apps.
- On the Data protection page, specify the required data protection settings and click Next
Note: Use this section to configure any data loss prevention controls, by configuring how users interact with data in the apps.
- On the Access requirements page, specify the access requirements and click Next
Note: Use this section to configure any access requirements for the apps, by configuring the PIN and credential requirements that users must meet to access apps in a work context.
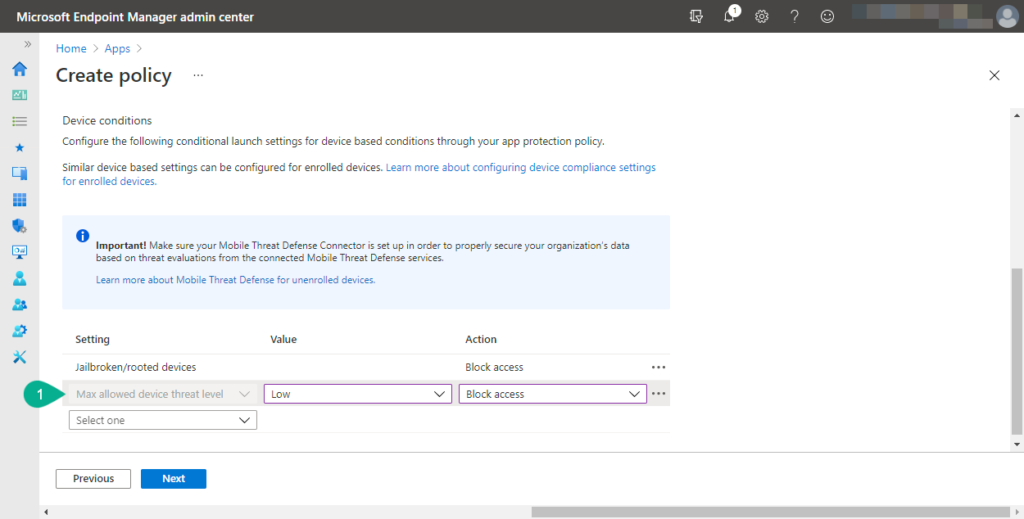
- On the Conditional launch page, specify the app conditions, specify the following device condition (as also shown in Figure 3) and click Next
- Setting: Select Max allowed device threat level as value to make sure that this conditional launch setting will verify the risk information that is provided via MDE.
- Value: Choose either Secured, Low, Medium, or High to determine the maximum allowed threat level of the risk information that is provided via MDE. Using High as a value should only be used for reporting purposes, as that’s the highest threat level and basically means that everything is allowed.
- Action: Choose either Block access, or Wipe data to determine the action that should be performed when a higher threat level was reported then configured. Using Block access will make sure that the user can receive access once the risk is solved and using Wipe data will make sure that the company data is immediately wiped.
Note: Use the first section to configure any app conditions, by configuring grace periods and app requirements that should be in place to allow access to company data.
User experience with Microsoft Defender for Endpoint on unmanaged devices
Important: Keep in mind that this functionality is currently in preview. The current behavior is not finalized and might change in the near future. Also, currently this functionality requires the use of a version of the app that’s available via the beta Google Play store (for Android) and Apple TestFlight (for iOS).
The best method to look at the user experience, is by simply experiencing it. Once the app protection policy is in place, the user will experience the behavior as described and shown below, in the targeted apps. That experience is shown for Android devices, as those devices can be tested the easiest by installing the Test Virus app from the Google Play store. That installation triggers an immediate risk level of Medium.
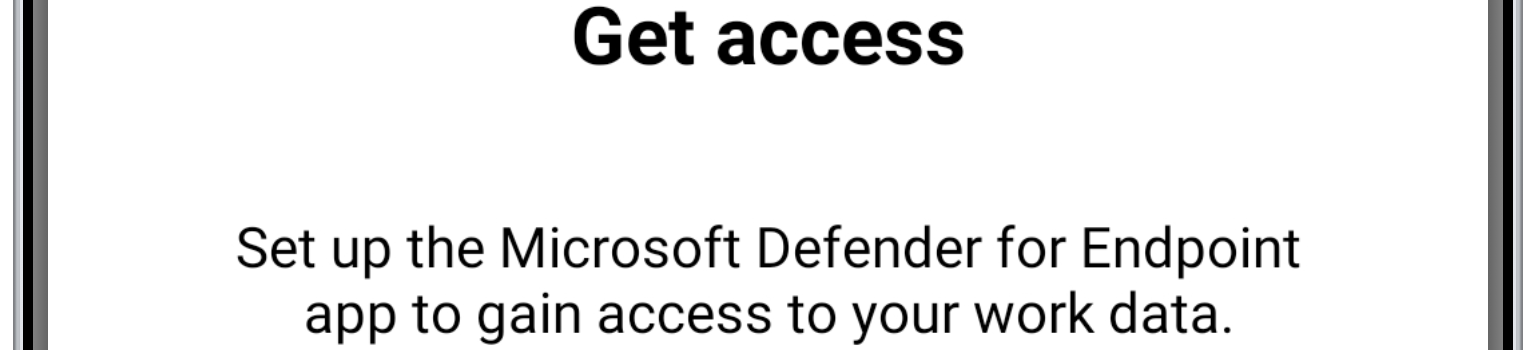
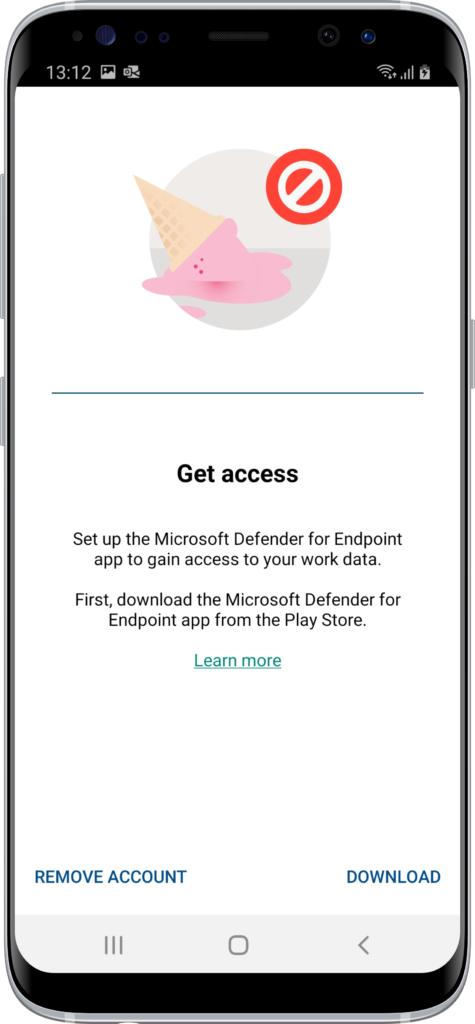
- When the user starts the Outlook app, the user receives the Get access message (as shown in Figure 4). That message tells the user to download and install the MDE app to gain access to work data.
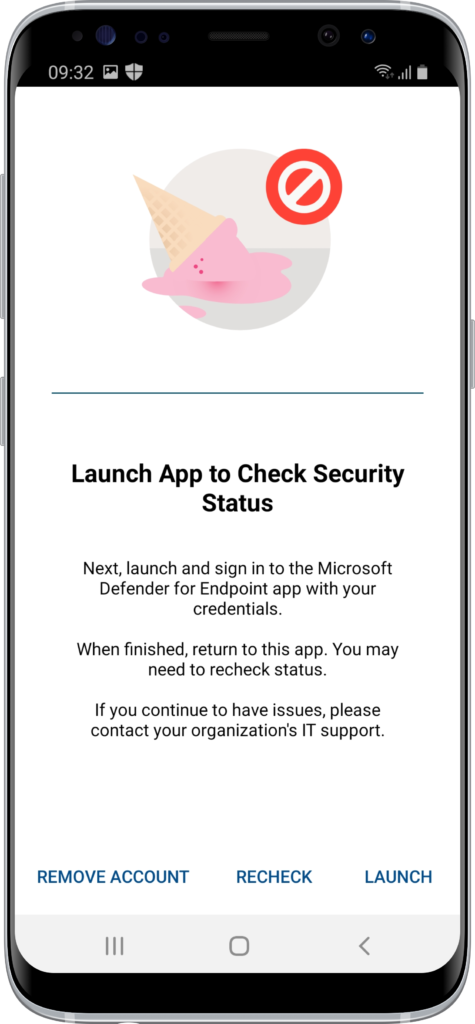
- When the MDE app is downloaded and the user returns to the Outlook app, the user receives the Launch App to Check the Security Status message (as shown in Figure 5). That message tells the user to launch the MDE app and to sign in. After sign in, and configuration, the user can return to the Outlook app and recheck access.
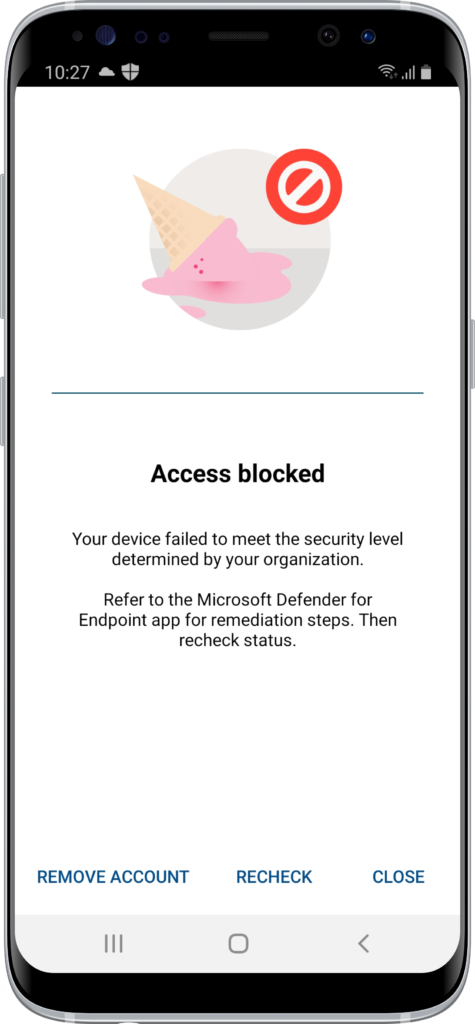
- When the MDE app is signed in and the user performed an action that caused a higher risk level than allowed, the user receives the Access blocked message (as shown in Figure 6). That message tells the user to return to the MDE app to remediate the issue. After remediating, the user can return to the Outlook app and recheck access.
Note: The MDE app for Android and iOS connects with the Microsoft Defender for Mobile application. That can be challenging in combination with Conditional Access. That specific application can’t be excluded yet. Also, the MDE app for Android and iOS isn’t part of the approved client apps list, or the list with supported apps for the app protection policy setting yet.
More information
For more information about app protection policies and Microsoft Defender for Endpoint, refer to the following docs.
Hi Peter, thank you very much for this useful information. I have one concern: Is there a way to deploy the Microsoft Defender for Endpoints app on the devices and bring them on board without the end user having to open the application on their device and authenticate? I mean, like in a silent way?
Not at this moment Danny.
Hi Peter,
Has anything changed since you wrote this blogpost some 20 months ago? We are having the same CA and approved client issues with Microsoft Defender for Mobile app on Android and iOS.
Hi Evb,
What issues are you seeing?
Regards, Peter
Client for Defender on IOS personal-enrol getting blocked still by CA requiring approved app or app protection policy. How to exclude “Microsoft Defender for Mobile” when it’s not an approved app?
Hi Andy,
There are now endpoint that you could use: https://learn.microsoft.com/en-us/microsoft-365/security/defender-endpoint/mobile-resources-defender-endpoint?view=o365-worldwide#microsoft-defender-mobile-app-exclusion-from-conditional-accessca-policies
Regards, Peter