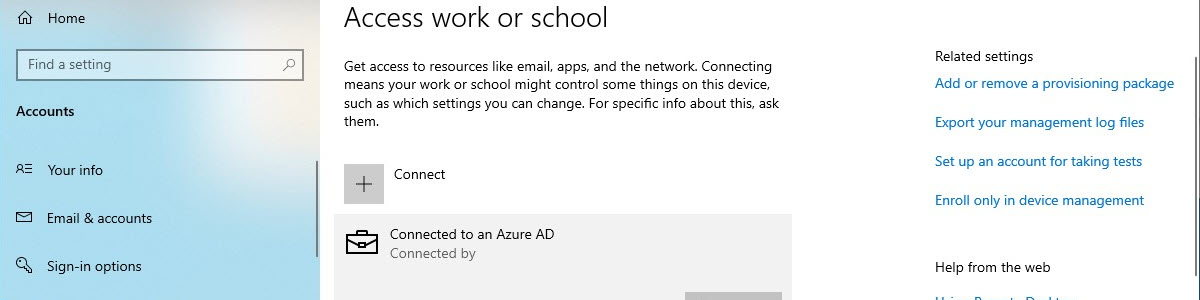
Using Microsoft Defender for Endpoint on Android for protecting the personal profile
This week another post about Microsoft Defender functionality, but on a completely different platform. This week is all about using Microsoft Defender for Endpoint, on Android devices, for protecting the personal profile. And for now, specifically focused on personally owned devices. That protection functionality is focused on providing users with the same level of protection in their personal profile, as provided in their work profile. It provides users – within their personal profile – with malware scanning on user-installed apps, protection from malicious URLs, network protection, and privacy controls. That provides users with better protection and organizations with more control on which devices are allowed to have access to company data. This post will mainly focus on the configuration of that additional protection of the …