This week is all about Security Management for Microsoft Defender for Endpoint. Security Management for Microsoft Defender for Endpoint is the new configuration channel that can be used for managing the security configuration for Microsoft Defender for Endpoint (MDE) on devices that are not enrolled into Microsoft Endpoint Manager (MEM). Not in Microsoft Intune, nor in Configuration Manager. With that new configuration channel, MDE retrieves, enforces, and reports on the policies that are assigned via MEM. After onboarding to MDE, the devices are automatically joined to Azure AD and become visible in the MEM (and Azure AD and Microsoft 365 Defender). Within MEM those devices are marked as managed by MDE.
This post will go through the steps to configure the required tenant configurations, the steps to enroll and group devices and the steps to assign security configurations. That means that the following will be addressed.
- Configuring the tenant for Security Management with Microsoft Defender for Endpoint
- Onboarding devices in Microsoft Defender for Endpoint
- Tagging devices for Security Management for Microsoft Defender for Endpoint (required during preview)
- Grouping devices based on Security Management for Microsoft Defender for Endpoint
- Assigning policies for Security Management for Microsoft Defender for Endpoint
- Experiencing Security Management for Microsoft Defender for Endpoint
Important: At the moment of writing Security Management for Microsoft Defender for Endpoint is still in preview.
Configuring the tenant for Security Management with Microsoft Defender for Endpoint
The first step is to configure the tenant to support the Security Management for Microsoft Defender for Endpoint configuration channel. That configuration channel will make sure that security settings management in MEM can be enforced by MDE. To enable that configuration channel, the following two configurations are required to enable the integration between MEM and MDE.
Configuration 1: Enable security setting management in Microsoft 365 Defender
The first configuration that is required for this integration is to enable security setting management in Microsoft 365 Defender. That configuration can be achieved by following the two steps below.
- Open the Microsoft 365 Defender portal and navigate to Settings > Endpoints > Enforcement scope
- On the Enable security setting management page (as shown in Figure 1), navigate to OS platform, switch the slider with Windows Client devices and Windows Server devices to On and click Save to enable security settings management for Windows client and server devices
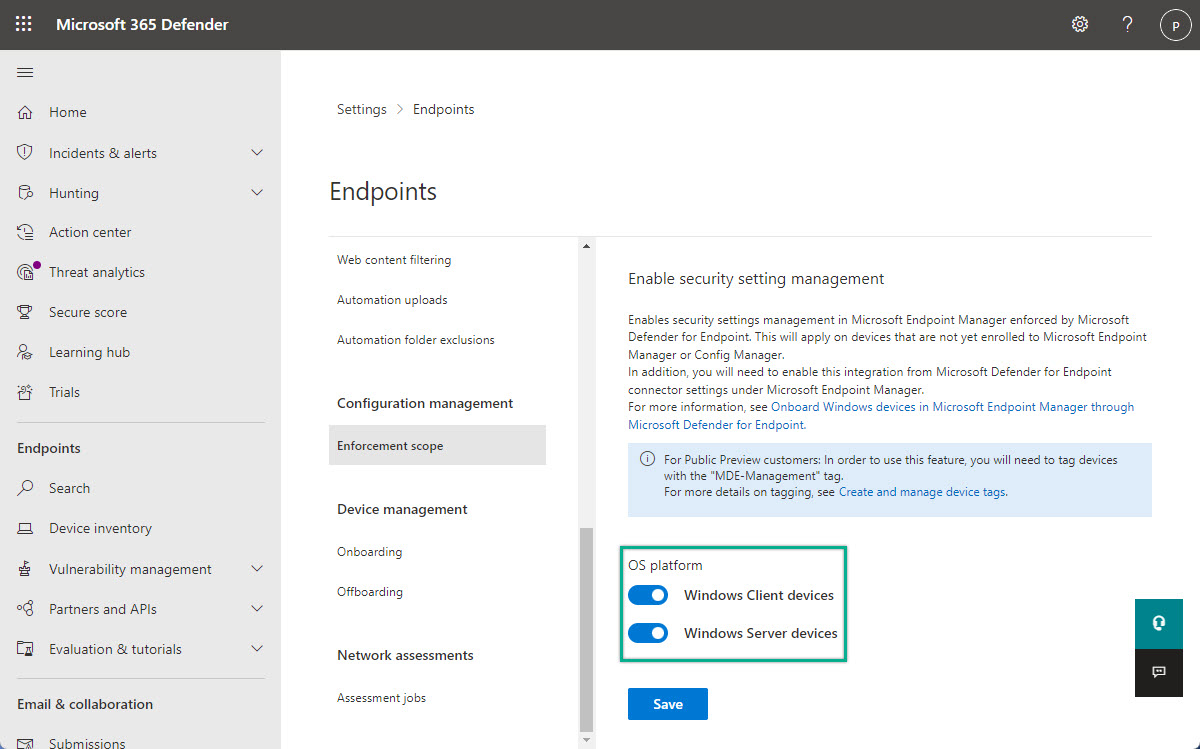
Note: This step assumes that the Microsoft Intune connection was already enabled for compliance information.
Configuration 2: Allow Microsoft Defender for Endpoint to enforce Endpoint Security Configurations in Microsoft Endpoint Manager admin center
The second configuration that is required for this integration is to allow MDE to enforce endpoint security configurations in MEM. That configuration can be achieved by following the two steps below.
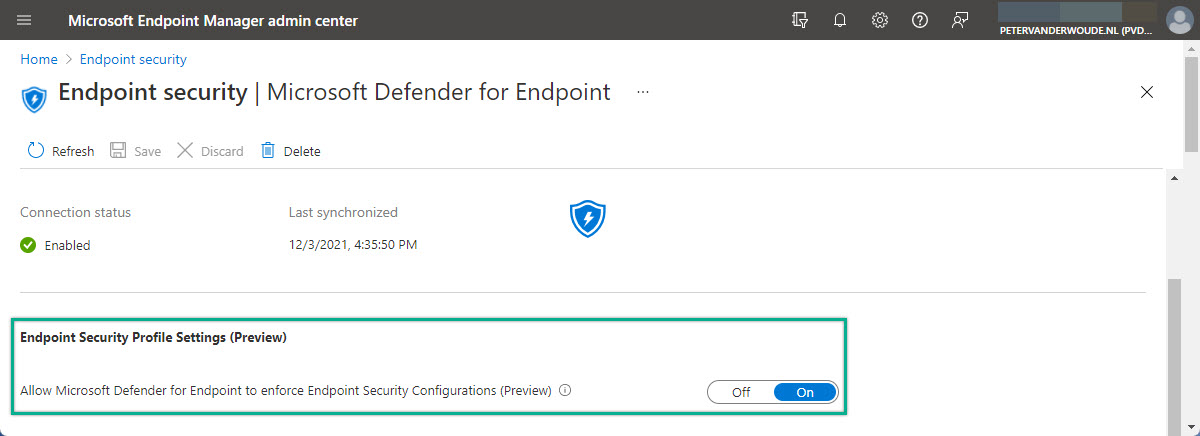
- Open the Microsoft Endpoint Manager admin center portal and navigate to Endpoint security > Microsoft Defender for Endpoint
- On the Endpoint security | Microsoft Defender for Endpoint blade (as shown in Figure 2), navigate to the setting Allow Microsoft Defender for Endpoint to enforce Endpoint Security Configurations and switch the slider to On to enable devices to qualify to onboard to MDE
Onboarding devices in Microsoft Defender for Endpoint
The second step is to onboard Windows devices in MDE. There are different options for onboarding Windows devices in MDE, but not all methods might fit the current purpose. Pick the best option. The following two steps walk through the process of selecting the onboarding process and the deployment method. After going through those steps, use the deployment package to actually onboard devices in MDE.
- Open the Microsoft 365 Defender portal and navigate to Settings > Endpoints > Onboarding
- On the Onboarding page (as shown in Figure 3), select the required operating system with Select operating system to start onboarding process, select the used deployment method with Deployment method and click Download onboarding package to download the package that can be used for onboarding Windows devices by using the preferred deployment method
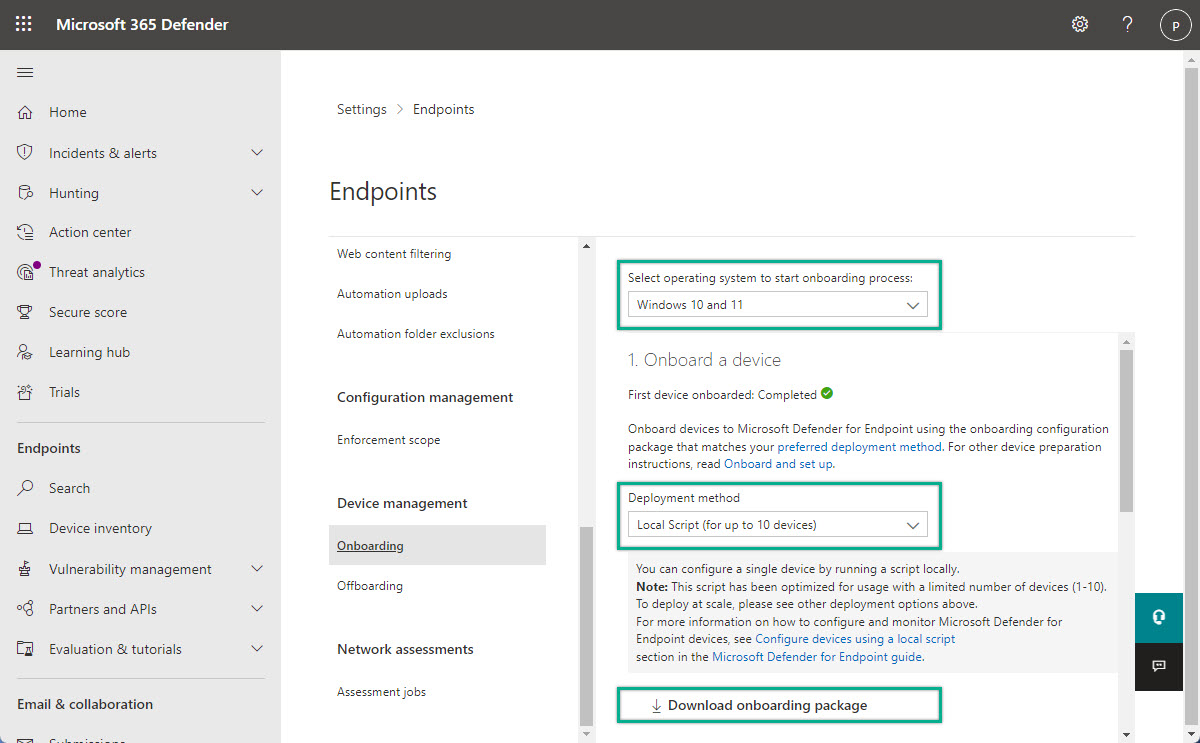
Note: For this example, the local script deployment was used to onboard a Windows 10 device.
Tagging devices for Security Management for Microsoft Defender for Endpoint (required during preview)
The third step is to tag devices that are onboarded in MDE with the MDE-Management tag. That tag is required during the preview and will make sure that devices are enrolled in the Security Management for Microsoft Defender for Endpoint configuration channel. That will also make sure that devices are automatically joined in Azure AD. Those objects can be used for grouping and targetting. The following three steps walk through adding the required machine tag to the devices.
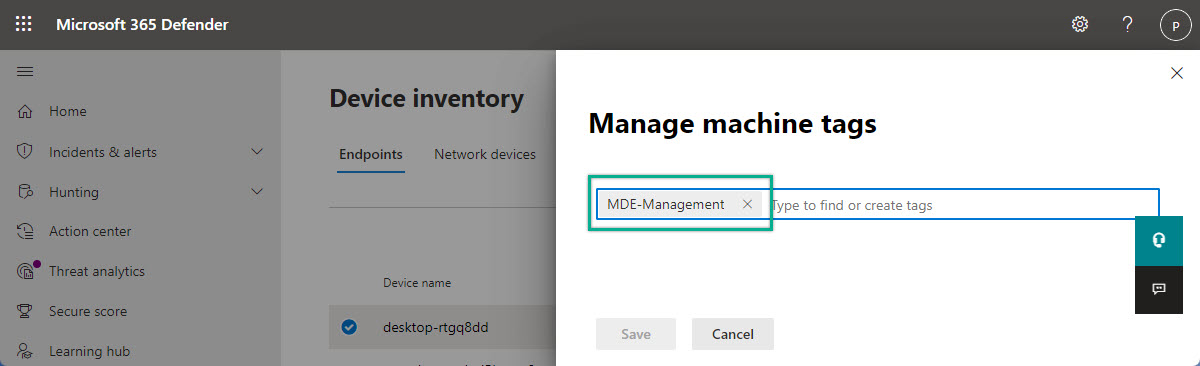
- Open the Microsoft 365 Defender portal and navigate to Device inventory
- On the Device inventory page, select the onboarded device and click Manage tags
- On the Manage machine tags page (as shown in Figure 4), specify MDE-Management as tag and click Save
Grouping devices based on Security Management for Microsoft Defender for Endpoint
The fourth step is to group devices based on the Security Management for Microsoft Defender for Endpoint configuration channel. That group can be used for assigning endpoint security policies to the required devices. The following four steps walk through the creation of such a group, by highlighting the main setting that is required for filtering the required devices.
- Open the Microsoft Endpoint Manager admin center portal and navigate to Groups
- On the Groups | All groups page, click New group
- On the New group page, specify the basic information, select Dynamic device as Membership type and click Add dynamic query with Dynamic device members
- On the Dynamic membership rules page (as shown in Figure 5), specify (device.managementType -eq “MicrosoftSense”) with the Rule syntax and click Save
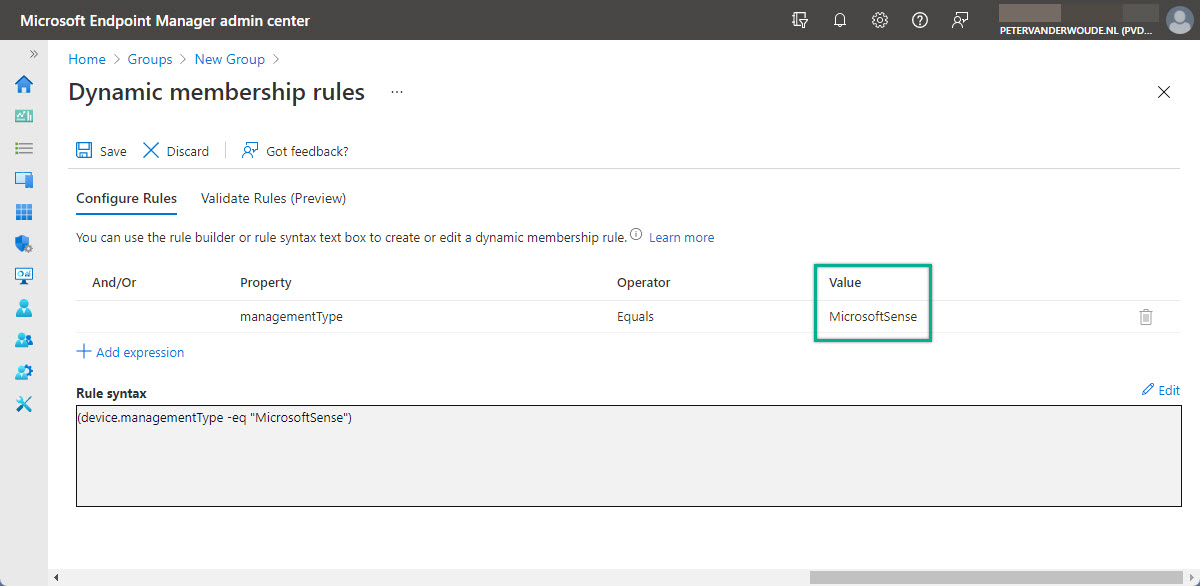
Note: Querying for MicrosoftSense as the managementType makes sure that the devices that are configured via the Security Management for Microsoft Defender for Endpoint configuration channel, are filtered.
Assigning policies for Security Management for Microsoft Defender for Endpoint
The fifth and last step is to create and assign endpoint security policies to devices via the Security Management for Microsoft Defender for Endpoint configuration channel. At this moment the Antivirus, Firewall, Firewall Rules and Endpoint Detection and Response endpoint security policies are available via this channel. The following six steps walk through the creation of such a endpoint security policy, by only highlighting the main settings that are required for this channel.
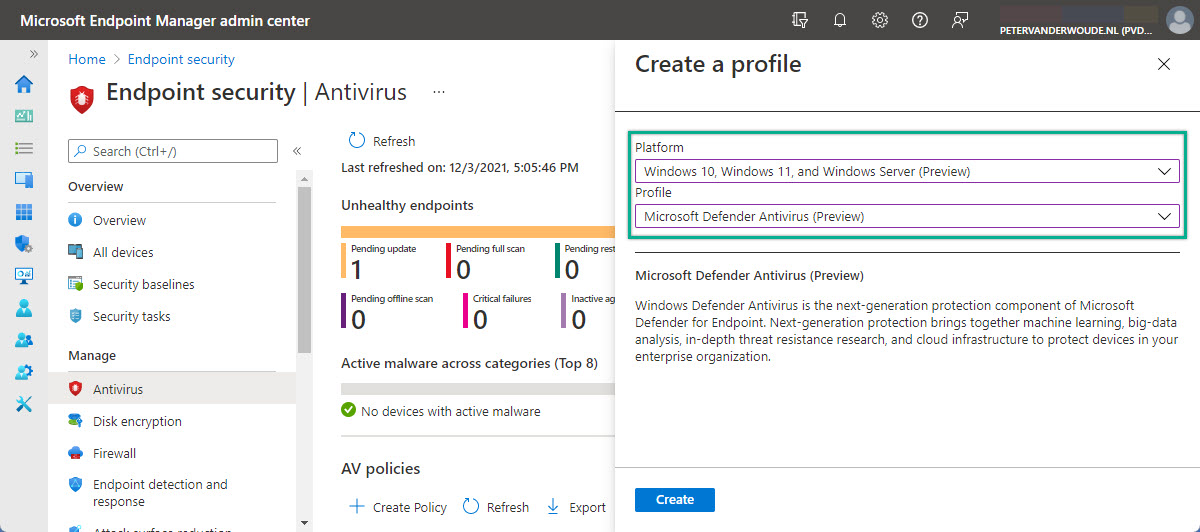
- Open the Microsoft Endpoint Manager admin center portal and navigate to Endpoint security > and select one of the available endpoint security policies for the Security Management for Microsoft Defender for Endpoint channel
- On the Create a profile page (as shown in Figure 6), select Windows 10, Windows 11 and Windows Server as Platform, select the Profile and click Create
- On the Basics page, provide a Name and Description for the policy and click Next
- On the Configuration settings page, configure the settings to manage with the policy and click Next
- On the Assignments page, add the just created group that contains the required devices and click Next
- On the Review + create page, review the configuration and click Create
Important: Assignment filters are not supported for policies that are used for the Security Management for Microsoft Defender for Endpoint configuration channel and the assignments are only applicable to device objects.
Note: These policies will also apply to devices that are managed via Microsoft Intune.
Experiencing Security Management for Microsoft Defender for Endpoint
There are multiple ways to experience Security Management for Microsoft Defender for Endpoint. The biggest changes, however, are shown in the MEM admin center portal. That portal provides status information about the different assigned endpoint security policies, but – even more interesting – it also provides very clear information about the management status of the devices. Below, in Figure 7, a device is shown that’s managed via Security Management for Microsoft Defender for Endpoint. A few interesting properties are highlighted, being MDE as Managed by (1), no compliance information (2) and Azure AD joined as Join Type (3). Especially the first and the last property are specific to Security Management for Microsoft Defender for Endpoint. The combination of the management and the join type.
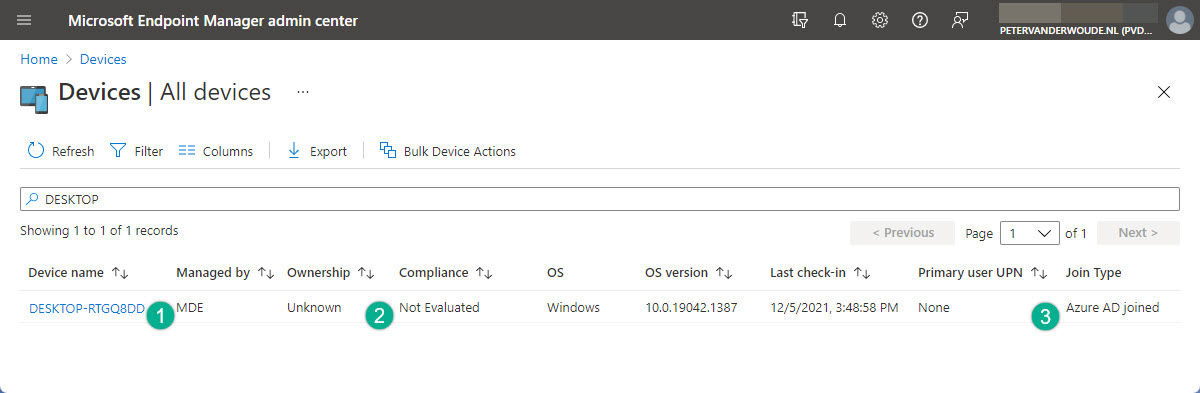
Note: This information shown above is about a personal Windows 10 device that is managed via Security Management for Microsoft Defender for Endpoint.
More information
For more information about Security Management for Microsoft Defender for Endpoint, refer to the following docs.
One little tidbit I grabbed from the CAT team for Defender for Endpoint that its in your screenshot:
Don’t use the local script deployment – there are some performance impacts to the Defender for Antivirus services over if you deploy with Endpoint Manager or Intune
Hi Chris,
That’s correct. The idea of this post, however, was to show the non-Intune/ConfigMgr route.
Regards, Peter
when i created the dynamic Azure AD group it got failed because I should have added contains not equal parameter
Hi Maged,
Not sure what you mean, because that would create a whole different result. Using equals should be possible.
Regards, Peter
Have you tested the scenario of onboarding Server 2012 R2 to Defender for Endpoint using Azure AD Hybrid Join. Did you manage to sync Server 2012 R2 computer objects to Azure AD?
Hi David,
I haven’t specifically tested that platform. What issue are you running into?
Regards, Peter
Specifically I cannot sync the computer object using AADC to AAD. It shows at cloudfiltered=true. If you have a look in this article: https://docs.microsoft.com/en-us/microsoft-365/security/defender-endpoint/troubleshoot-security-config-mgt?view=o365-worldwide
It has the information on what to change in AADC.
Thanks.
Hi David,
Did you make the adjustments and run a full sync?
Regards, Peter
Yes – Would be interested in seeing if anyone else can get this to work on Server 2012 R2.
Hi David,
In that case I can’t really provide any further suggestions as I don’t have any Server 2012R2 devices in my environment anymore. I hope somebody else might chime in with some suggestions.
Regards, Peter
Can you only enforce settings from the “Antivirus” tab? Or can you also configure settings from Firewall, Attack Surface Reduction etc?
We followed your guide, Antivirus settings are pushed correctly, but Attack Surface Reduction rules are still on pending.
Hi Wouter,
Attack surface reduction rules are not yet supported.
Regards, Peter
Peter, i’m confused. This article mentions ASR should be possible https://docs.microsoft.com/en-us/microsoft-365/security/defender-endpoint/security-config-management?view=o365-worldwide#which-solution-should-i-use
Do you know , know a link what’s not supported with the new MEM method?
Furthermore can you ‘combine’ the MEM method with MDE GPO’s. So if a policy is not possible via MEM can you configure it via GPO?
What method is prefered today when starting to implement MDE?
Hi Rkast,
Not sure what you mean. That link also mentions that MDE Security Configuration doesn’t support ASR at this moment.
Regards, Peter
Peter, kwartje valt, dank… I was in the assumption that the MEM column was the new security management method but its MDE Security column i understand now by your comment. Its a bit confusing because you deploy the policy via MEM (console).
So would this mean that we deploy Defender polcies via the new MDE Security and for example ASR polcies via GPO?
Dank voor je reactie 🙂
Hi Rkast,
Correct. And yes, you’ve got to look at other methods for managing those settings. For servers that could be GPO.
Regards, Peter
Hi, one question please,
device enrolled in intune with company portal and azure ad registered
Company portal show me this warning “Enroll your device in Microsoft Defender for Endpoint” but, I can see the device in MDE dashboard in onboarded state
Why? Isn’t azure ad registered device compatible?
Hi Denis,
Can you provide some more details? It sounds like you’re referring to a “normal” Intune managed device with a compliance policy.
Regards, Peter
Hi, Peter, we would like to join our VCenter servers but only want Defender Antivirus to protect our servers and no other configs or policies. This seems to be the best options. When I turn on “Use MDE to enforce security configuration settings from MEM” my concerns are how will this affect devices we’ve already added to Endpoint management. It seems they would not be affected I’m I correct? Also when it says they will be AD joined, our server are already joined to our local AD so how will they be affected? I’m new to managing devices and have be tasked with this project.
Hi Shawn,
It will not have impact on your devices that are already managed by MEM.
Regards, Peter
Hi Peter
Thanks for the article , How can I enforce the compliance check with Intune ? when I open settings app –> Work Account , I can see that the machine is registered with Azure AD but I can’t find a way to a Sync as there is no account as it was joined automatically by MDE.
Hi Amr,
You mean force a checkin for a new policy? If so, not sure if you can enforce that at this moment.
Regards, Peter
Hello Peter,
Do you have more information about “Allow Microsoft Defender for Endpoint to enforce Endpoint Security Configurations”?
What exactly it is?
Why exactly it is needed? We have onboarded devices using Configuration profile from MS Docs PDF file and works fine.
Hi Oscar,
That configuration is required when you want to manage configurations on devices that are not managed via MDM.
Regards, Peter
Hello Peter,
Thanks for the info! Recently MS Support told us we should enable this as a very required parameter for security.microsoft.com portal, while the procedure to onboard managed devices by MDM does not explain this step or even MS Support cannot explain what exactly will be happening if this setting is enabled, like what is “enforced” as they say in the enabling menu 🙂
Hi Oscar,
That setting is only useful when you’re using MEM for creating the configuration profiles and not relying on MDM. In that case MDE will be making sure that the configuration will be applied.
Regards, Peter
Polices in MEM/MS Intune doesn’t reflect on assigned endpoints. please help. The endpoints was now managed by ‘MEM’ not ‘MDE’ yet as per the Device information. Do all the above configurations.. I used the MS intune deployment. The endpoint is also now enrolled into MS Intune..
Hi Mike,
How did you enroll/onboard those devices? This process doesn’t enroll devices in Intune.
Regards, Peter
On MEM, Devices> Configuration profiles> Created policy> Config settings below:
Configuration settings:
Microsoft Defender for Endpoint Microsoft Defender for Endpoint client configuration package type: Onboard
Onboard Configuration Package: WindowsDefenderATP.onboarding
Sample sharing for all files: Not configured
Expedite telemetry reporting frequency: Enable
Note:
– I believe MS Intune connection is working. (Just that the environment is a Hybrid Azure AD join for our laptops)
– ASR – Device control policy (with USB Storage blocking) reflected already… as it was change from USB being detected and when I have applied this policy and test an hour… my USB flash drive is not opening anymore.
I’m guessing a possible cause for this is that the clients are Hybrid Azure AD join. Meaning they got most of the settings on the AD GPO policy on prem.. Any MS Intune endpoint security settings that are not in AD onprem GPO will be working..
Now I’m I am looking why the other policy such as the Firewall (domain, private, public) are enabled in MS Intune security policy but in the testing assigned clients are still OFF. Do you a thoughts for this?
Thank you very much.
Hi Mike,
That sounds like you’ve enrolled the devices into Microsoft Intune (probably via a GPO?). Without that, you wouldn’t be able to configure ASR via Endpoint Manager.
Regards, Peter
Hello,
What if I want to create different policies for Defender for different type of servers (for example policy for DC servers, another for Exchange server, third for SCCM, etc.). Will I be able to do this?
Thank you
Hi Tester,
You can use different assignments.
Regards, Peter