Managing Copilot in Microsoft Edge
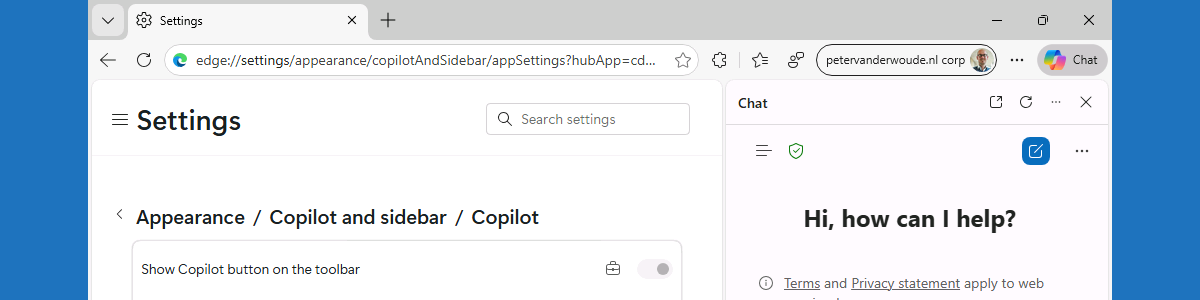
This week is all about managing Copilot within Microsoft Edge. There were already some nice configurations available for a while and recently an additional configuration was added around sharing tenant-approved browser history with Copilot search. That was a nice trigger for this post, focused on managing those available configurations. Working with Copilot in Microsoft Edge, does often require the organization to make that functionality available to the users. The good part is that it is often already disabled by default when using an organizational account. Especially in the EU, Copilot in Microsoft Edge has some default constraints that can be adjusted when needed. That is for example applicable to configuration around accessing Microsoft Edge page content for Entra accounts. This post will provide a closer …