Temporarily removing apps and configurations from mobile devices
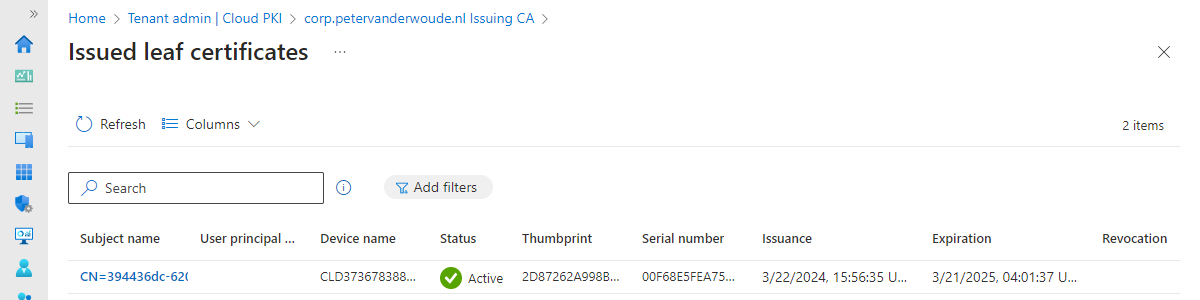
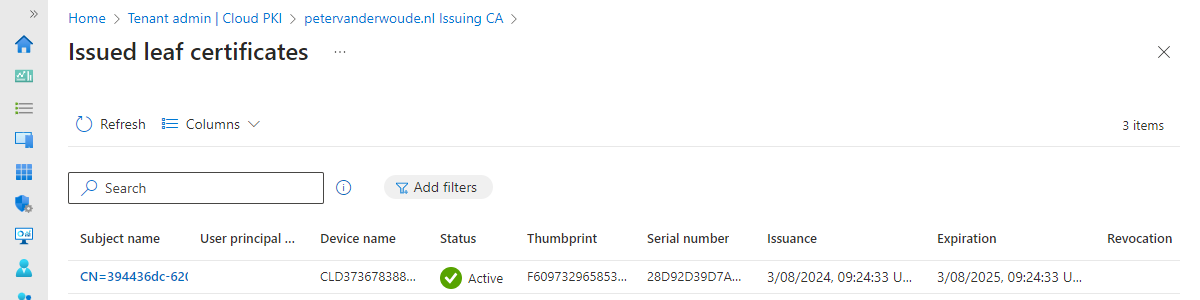
This week is all about a new feature that is specifically for mobile devices, and that feature is the ability to remove, reinstall, and re-apply specific configuration policies, configuration profiles, and apps. The best part is that it can be achieved without changing the assignments of those apps and configurations. That can be really useful to help with resolving specific challenges and to quickly restore the productivity of the user. The apps and configurations that were removed will automatically be restored within 8-24 hours. Alternatively, the IT administrator can also manually initiate an action to restore the removed apps and configurations earlier. So, in the end, the focus remains on ensuring that the devices remain consistent with the assigned apps and configurations. This post will …