Managing privacy controls for Office products
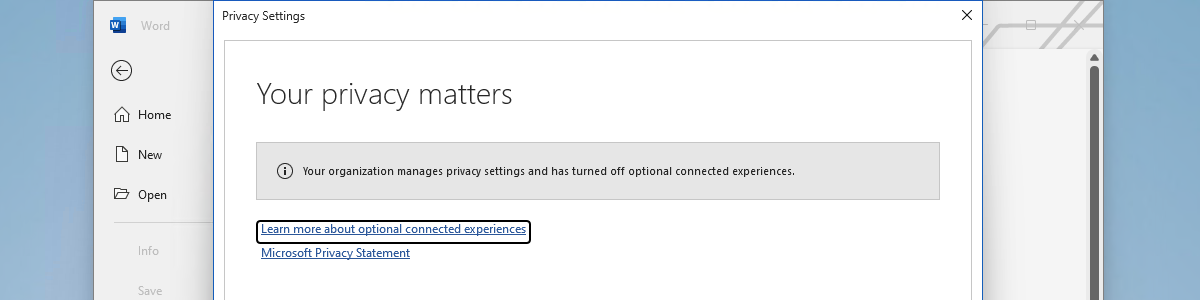
This week is all about managing privacy controls for Office products. That includes Office on Android devices, Office on iOS devices, Office for Mac devices, Office for the web, and Microsoft 365 apps for enterprise on Windows devices. Most organizations often already have a good look at the required configurations options for the privacy controls on Windows devices. Office for other platforms, however, are often forgotten. Just like Office for the web. Good thing, though, is that there are nowadays multiple privacy controls available that can be configured for Office on all platforms. For some platforms there are even multiple configurations options. Best part of those configuration options is that there is also an option to configure the privacy controls cross platforms. This post will …