Simplifying targetting groups of apps with app protection policies
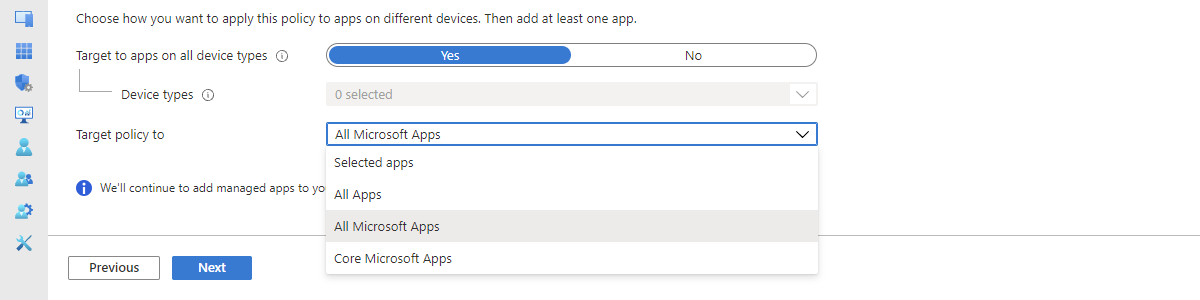
This week is all about the simplification in targetting groups of apps with app protection policies and a followup on my tweet of last week. That tweet provided a quick peak at the new targetting options of app protection policies for Android and iOS/iPadOS devices. The great thing about that simplification is that app protection policies can now be targeted at different categories (or groups) of apps. Those categories of apps are All apps, All Microsoft apps and Core Microsoft apps, and are dynamically updated to include the appropriate apps. That dynamic update will make sure that the already created app protection policies are automatically updated with the latest apps that are available for the different categories and will also make sure that newly created …