This week another post about Microsoft Defender functionality, but on a completely different platform. This week is all about using Microsoft Defender for Endpoint, on Android devices, for protecting the personal profile. And for now, specifically focused on personally owned devices. That protection functionality is focused on providing users with the same level of protection in their personal profile, as provided in their work profile. It provides users – within their personal profile – with malware scanning on user-installed apps, protection from malicious URLs, network protection, and privacy controls. That provides users with better protection and organizations with more control on which devices are allowed to have access to company data. This post will mainly focus on the configuration of that additional protection of the personal profile and the experience on the device.
Note: For information on getting started with Microsoft Defender for Endpoint on Android, have a look at this post.
Configuring Microsoft Defender for Endpoint in the personal profile
When looking at the configuration to enable Microsoft Defender for Endpoint in the personal profile, it all starts with an app configuration policy. That app configuration policy is used to apply a configuration to the Microsoft Defender app to enable Microsoft Defender for Endpoint to support the personal profile. Once that app configuration policy is applied to the Microsoft Defender app, it’s up to the user to finish the configuration. The configuration to enable Microsoft Defender for Endpoint to support the personal profile, can be achieved by going through at least the seven steps below.
Note: These steps are only focused on applying the app configuration policy for this specific scenario.
- Open the Microsoft Endpoint Manager admin center portal navigate to Apps > App configuration profiles
- On the Apps | App configuration policies blade, click Add > Managed devices
- On the Basics page, provide the following information and click Next
- Name: Provide a valid name for the app configuration policy
- Description: (Optional) Provide a valid name for the app configuration policy
- Device enrollment type: (Grayed out) Managed devices
- Platform: Select Android Enterprise as the platform to get the required platform types available
- Profile Type: Select Personally-Owned Work Profile Only to apply the app configuration to personal devices
- Targeted app: Select Microsoft Defender as the app to configure
- On the Settings page, provide at least the following information (as shown below in Figure 1) and click Next
- Configuration Settings format: Select Use configuration designer to enable the selection of policy settings
- Click Add to add the Microsoft Defender in Personal Profile configuration key and set the configuration value to 1 to enable Microsoft Defender for Endpoint to support the personal profile
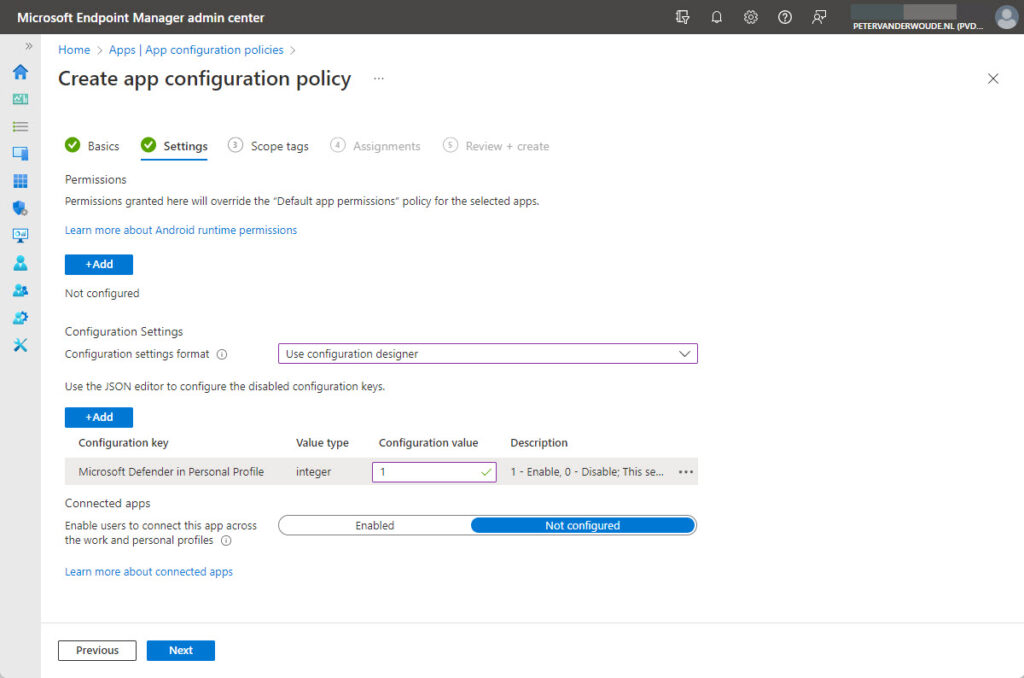
- On the Scope tags page, configure the applicable scope tags and click Next
- On the Assignments page, configure the assignment by selecting the applicable group and click Next
- On the Review + create page, review the configuration and click Create
Experiencing Microsoft Defender for Endpoint in the personal profile
When looking at the experience with Microsoft Defender for Endpoint in the personal profile, it all starts with getting it up-and-running. And to get it up-and-running in the personal profile, it requires a little bit effort of the IT administrator and a bit more effort of the user. The effort of the IT administrator was described earlier and that effort by the user will follow now. For the user to get started, it’s important that the following is available on the Android device of the user:
- The Microsoft Defender app is installed, activated, and configured in the work profile
- The user installed the Company Portal app in their personal profile (no sign-in required)
- The Microsoft Defender app is installed in the personal profile
Important: The user must install the Company Portall app and the Microsoft Defender app in the personal profile.
Once the Microsoft Defender app is installed, activated and configured in the work profile, and the Company Portal app and the Microsoft Defender app are installed by the user in the personal profile, it’s time to start the onboarding in the personal profile. For that, the user must open the Microsoft Defender app in the personal profile. Now the user should login using their work account, and walk through the UELA, the notices, and the permissions.
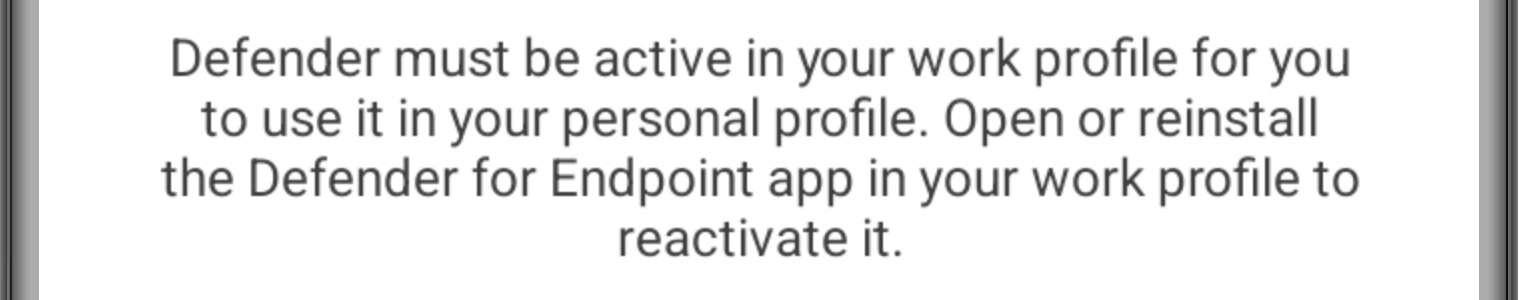
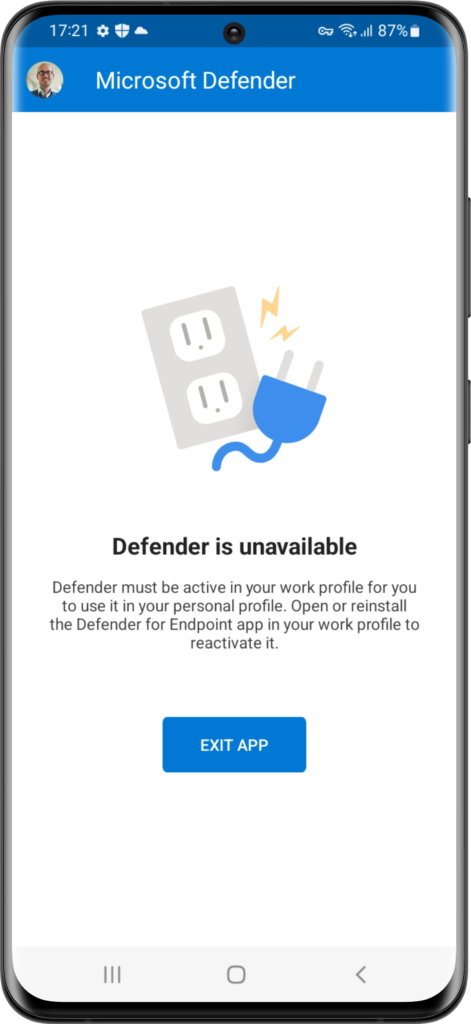
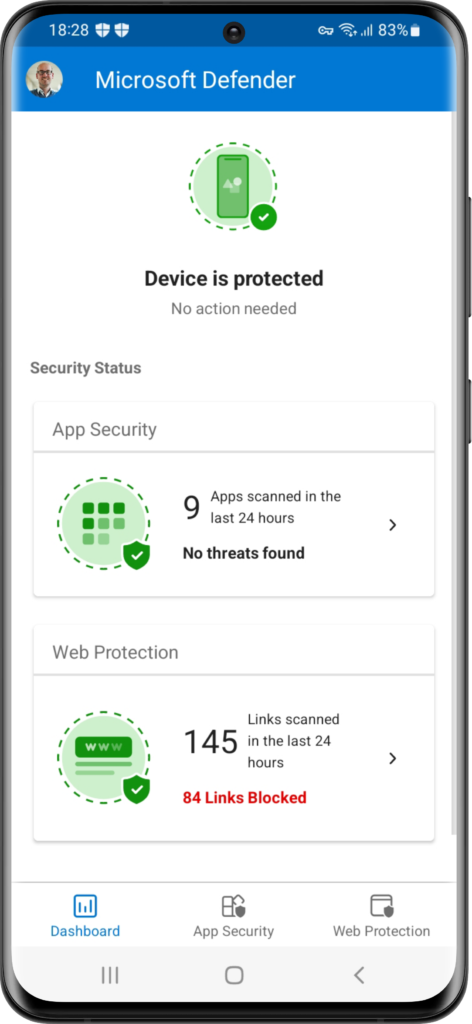
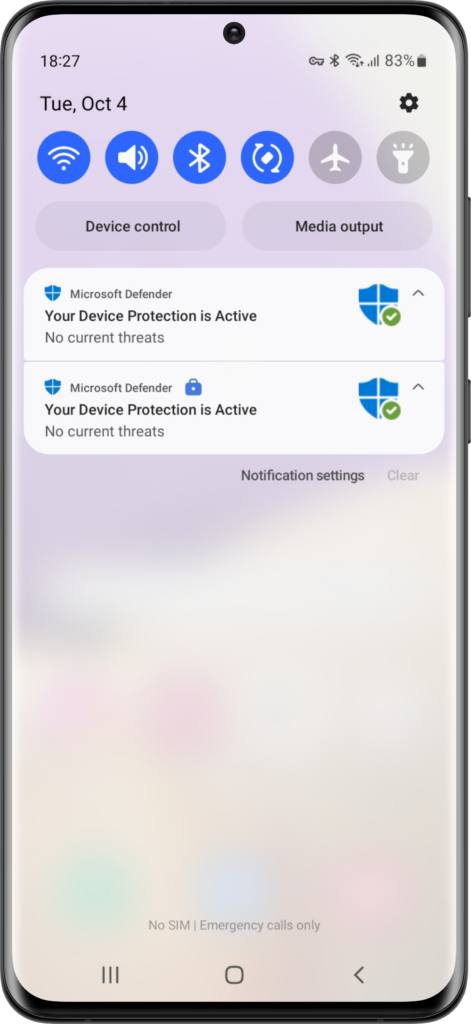
When not all of the mentioned apps and configurations are in place the user will get the message that Defender is unavailable (as shown in Figure 2). And when everything is in place, the user will get an active Microsoft Defender app (as shown in Figure 3). Once that is available, the best place to show the co-existence, of the Microsoft Defender app in the work and personal profile, is in the Notification area (as shown in Figure 4). That will show a Microsoft Defender app in the personal profile (without suitcase icon) and a Microsoft Defender app in the work profile (with suitcase icon).
Important: From an administrator perspective, this will also result into two device entries in the Microsoft 365 Defender portal. One normal entry with the expected name of username_platform and an additional entry with the name of username_platform_aepersonal.
Note: The described actions are not the most obvious actions for a user to perform. So, relying on Microsoft Defender for Endpoint in the personal profile of the user, does require very good communication with the user.
More information
For more information about Microsoft Defender for Endpoint on Android, and the protection of the personal profile on an Android devices, refer to the following docs.
what about the Corporated-owned Work profile scenario? If the device is owned by an organization and there is a working MDfE in the work profile, what should I do to protect the private profile? Installing COmpany Portal and Defender in a private profile causes me to get the message ‘Defender is unavailable’, which you included in the article…
Hi A,
This is focussed on personal devices with a work profile. I can’t find anything around the personal profile on corporate devices with a work profile.
Regards, Peter