Microsoft recently declared Microsoft Defender for Endpoint (MDE) for Android – previously known as Microsoft Defender ATP for Android – general available. That’s really good news and also a really good trigger for a new blog post. MDE for Android provides protection against phishing, unsafe network connections, and malicious apps. All events and alerts around those subjects will be available in the Microsoft Defender Security Center and will be used to determine the risk level of the device. To add-on to that, through the connection with Microsoft Intune that risk information can be used to determine the compliance of the device with the company policies and to determine the eventual access of the device to company data.
In this post I want to start with a short introduction about MDE for Android, followed by the required configurations. I’ll end this post by having a look at the experience. That means that the following will be addressed.
- Introduction to Microsoft Defender for Endpoint for Android
- Integration of Microsoft Defender for Endpoint with Microsoft Intune
- Distribution of the Microsoft Defender for Endpoint for Android app
- Configuration of the Microsoft Defender for Endpoint for Android app
- Configuration of the device risk compliance policy for Android Enterprise devices
- Experience with Microsoft Defender for Endpoint for Android
Note: At this moment many configurations still refer to Microsoft Defender ATP. This will change over time.
Introduction to Microsoft Defender for Endpoint for Android
Let’s start with a short introduction about MDE for Android. At this moment MDE for Android contains two key capabilities: 1) Web protection and 2) Malware scanning.
The Web protection capability relies on a local/self-looping VPN that does not take traffic outside of the device. That capability helps with addressing the challenge of phishing, by instantly blocking access to unsafe websites (coming from SMS, email, browsers and other apps). It also helps with addressing the challenge of unsafe network connections that some apps automatically make, by immediately blocking access to unsafe network connections. The key service that is leveraged for providing this functionality is Microsoft Defender SmartScreen. Besides that default functionality, an administrator can also configure custom indicators for allowing or blocking access to specific URLs and domains.
The Malware scanning capability fortifies the existing functionality of Google Play Protect and the ability to limit the installation of apps to trusted sources. That’s achieved by using cloud protection for apps and data on the device. When apps are downloaded, scans are instantly performed to detect malware of potentially unwanted applications (PUA).
In addition to those capabilities, MDE can also integrate with Microsoft Intune. That integration can provide information about the device risk to Microsoft Intune. That information about the risk level of the device can be used in a compliance policy in Microsoft Intune, to determine if a device is compliant with the company policies. That compliance state can be used in Conditional Access to determine the access of a device to company apps and data.
Integration of Microsoft Defender for Endpoint with Microsoft Intune
One of the main benefits of using MDE, is the integration with Microsoft Intune. That integration makes sure that the information about the risk level of a device, of any supported platform, can be provided to Microsoft Intune for usage in compliance policies. To achieve that integration, the following two configurations are required.
Enable Microsoft Intune connection in Microsoft Defender Security Center
The connection with Microsoft Intune should be enabled in Microsoft Defender Security Center. This is a generic configuration that is applicable to any supported platform. When this connection is already used for another platform, these actions can be ignored. To enable the Microsoft Intune connection, follow the two steps below.
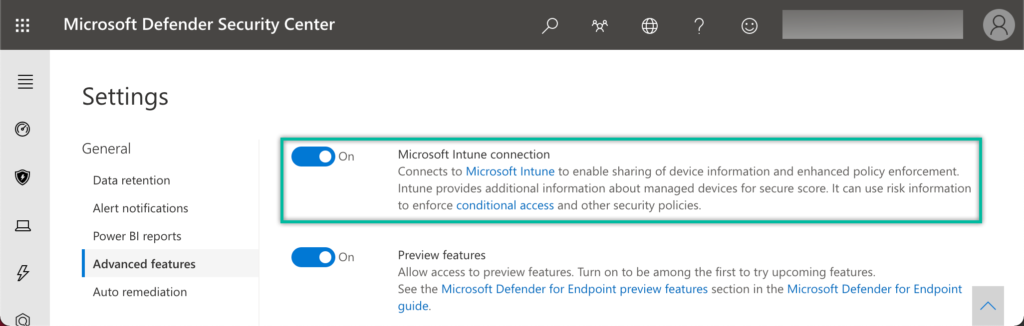
- Open the Microsoft Defender Security Center portal and navigate to Settings > Advanced features to open the Settings page for the advanced features
- On the Settings page, scroll down to Microsoft Intune connection (as shown in Figure 1) and switch the slider to On
Enable Android devices in Microsoft Endpoint Manager admin center
When the connection between MDE and Microsoft Intune is established, a configuration can be done per platform to use risk information that is provided via the connection. To enable that for Android, follow the two steps below.
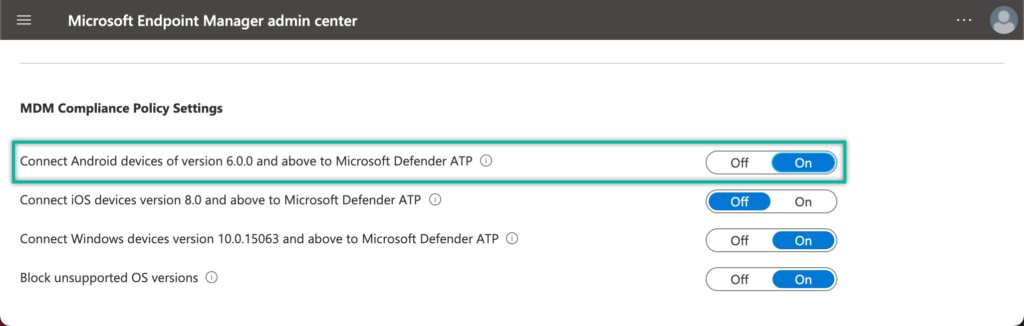
- Open the Microsoft Endpoint Manager admin center portal and navigate to Endpoint security > Microsoft Defender for ATP to open the Endpoint security | Microsoft Defender ATP blade
- On the Endpoint security | Microsoft Defender ATP blade, navigate to the setting Connect Android devices of version 6.0.0 and above to Microsoft Defender ATP (as shown in Figure 2) and switch the slider to On
Distribution of the Microsoft Defender for Endpoint for Android app
The MDE for Android app can be distributed by using Microsoft Intune. That will help with a smoother adoption of MDE on Android devices. Distribution of that app can be achieved by following the seven steps below.
- Open the Microsoft Endpoint Manager admin center portal navigate to Apps > All apps > Android to open the Android | Android apps blade
- On the Android | Android apps blade, click Add to open the Select app type page
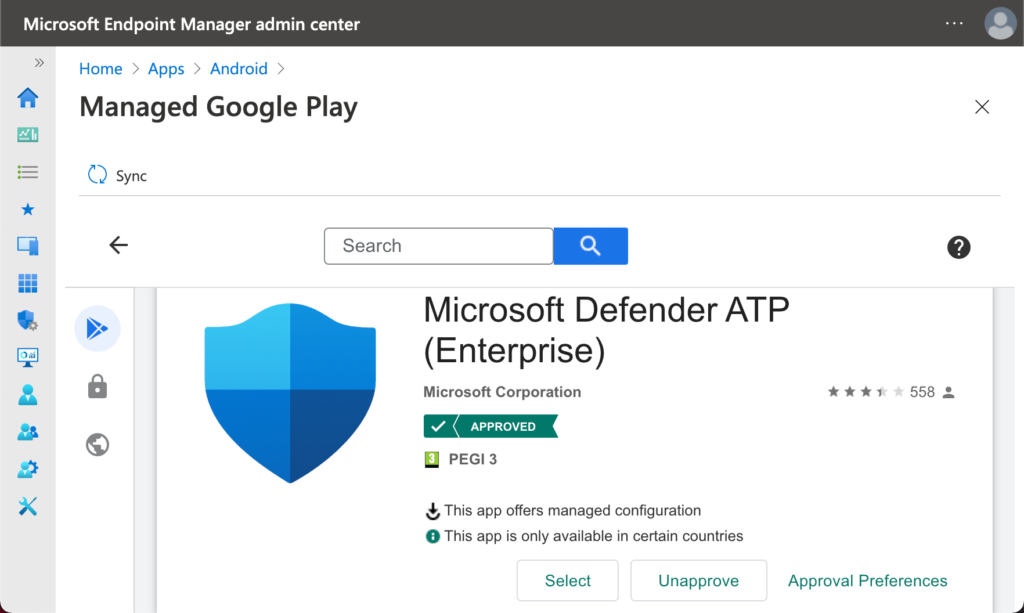
- On the Select app type page, select Managed Google Play app as App type and click Select to open the Managed Google Play page
- On the Managed Google Play page, search for the Microsoft Defender ATP (Enterprise) app, select the app and click Approve to open the Permissions dialog
- On the Permissions dialog, click Approve to open the Approval settings dialog
- On the Approval settings dialog, select Keep approved when app requests new permissions click Done
- Click Sync (as shown in Figure 3) to synchronize the approved app to Microsoft Intune
After successfully synchronizing the MDE for Android app to Microsoft Intune, assign the app to the required group of users or devices to distribute the app.
Configuration of the Microsoft Defender for Endpoint for Android app
The MDE for Android app can also be configured with a few properties to enabled or disable features and to take away some end-user interaction. The latter, however, can’t be taken away completely, which means that there is still a user interaction required. The configurations that can be achieved are enabling and disabling (a part of) the Web protection capability of MDE for Android. The permissions that can be useful are providing access to the external storage. If needed, those configurations can be achieved by following the seven steps below.
- Open the Microsoft Endpoint Manager admin center portal navigate to Apps > App configuration profiles to open the Apps | App configuration policies blade
- On the Apps | App configuration policies blade, click Add > Managed devices to open the Create app configuration policy wizard
- On the Basics page, provide the following information and click Next
- Name: Provide a valid name for the app configuration policy
- Description: (Optional) Provide a valid name for the app configuration policy
- Device enrollment type: (Grayed out) Managed devices
- Platform: Select Android Enterprise
- Profile Type: Select All Profile Types, Fully Managed, Dedicated, and Corporate-Owned Work Profile Only or Personally-Owned Work Profile Only depending on the devices that should get this policy assigned
- Targeted app: Select Microsoft Defender ATP (Enterprise)
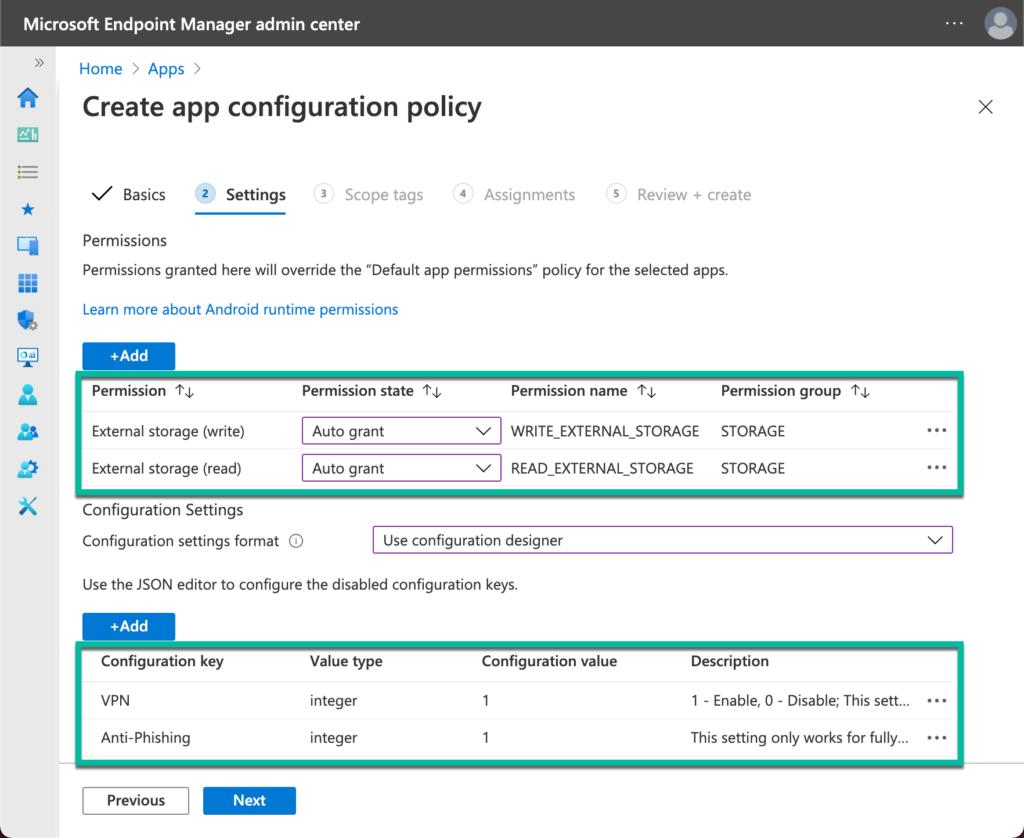
- On the Settings page, (if needed) provide the following information (as shown in Figure 4) and click Next
- Permissions
- Click Add to add External storage (read) and External storage (write) permissions and select Auto grant with the Permission state
Note: These permissions will save the users from manually approving these permissions on their device
- Configuration Settings
- Configuration settings format: Select Use configuration designer
- Click Add to add the Anti-Phishing or VPN configuration key and set the configuration value to 1 (enable) or to 0 (disable).
Note: The Anti-Phishing configuration key only works for fully managed and dedicated devices and both configuration keys influence the Web protection capability.
- On the Scope tags page, configure the applicable scope tags and click Next
- On the Assignments page, configure the assignment by selecting the applicable group and click Next
- On the Review + create page, review the configuration and click Create
Configuration of the device risk compliance policy for Android Enterprise devices
The device compliance policy can be used to actively take advantage of the integration between MDE and Microsoft Intune. That policy can mark a device as noncompliant when the device risk is above the configured score. Eventually, that compliance state can be used with conditional access to determine the access of a device to company apps and data. Creation of such a device compliance policy can be achieved by following the nine steps below.
- Open the Microsoft Endpoint Manager admin center portal navigate to Devices > Device compliance policies to open the Compliance policies | Policies blade
- On the Compliance policies | Policies blade, click Create Policy to open the Create a policy page
- On the Create a policy page, provide the following information and click Create
- Platform: Select Android Enterprise
- Policy type: Select Fully managed, dedicated, and corporate-owned work profile or Personally-owned with work profile depending on the devices that should get this policy assigned
- On the Basics page, provide the following information and click Next
- Name: Provide a valid name for the device compliance policy
- Description: (Optional) Provide a valid name for the device compliance policy
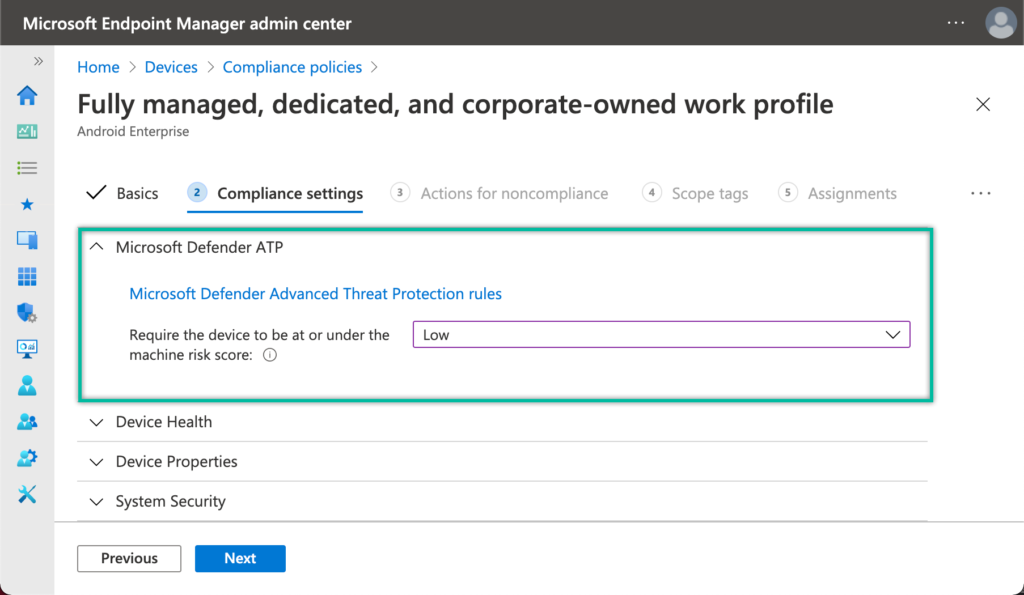
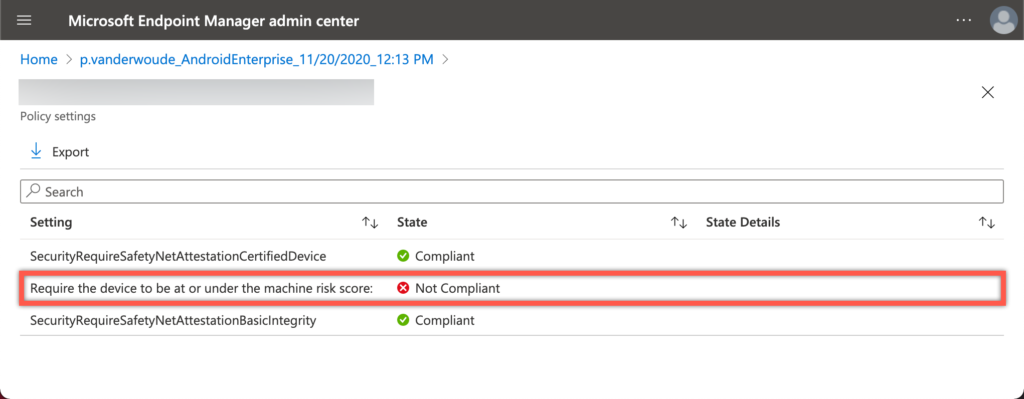
- On the Compliance settings page, navigate to the Microsoft Defender ATP section, select the risk score with Require the device to be at or under the machine risk score (see also Figure 5) and click Next
- On the Actions for noncompliance page, leave the default configuration of Action on Mark device noncompliant with Schedule (days after noncompliance) on Immediately and click Next
- On the Scope tags page, configure the applicable scope tags and click Next
- On the Assignments page, configure the assignment by selecting the applicable group and click Next
- On the Review + create page, review the configuration and click Create
Note: Configure a conditional access policy that requires a compliant device to use this compliance state for verifying access to company apps and data.
Experience with Microsoft Defender for Endpoint for Android
When the integration is configured between MDE and Microsoft Intune, the MDE for Android apps is configured and distributed and the compliance policy is in place, it’s time to look at the experience. Both, from an end-user perspective and from an administrator perspective.
End-user experience with the Microsoft Defender for Endpoint for Android app
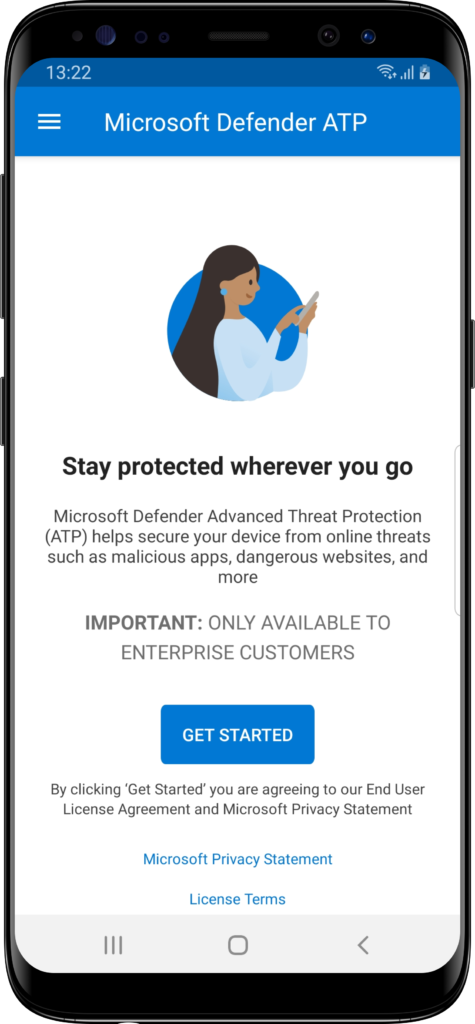
When looking at the end-user experience, it starts with the initial start of the MDE for Android app. After the MDE for Android app is installed, users should start it the first time to get it up-and-running. This does require the user to have the correct license (Windows 10 E5/A5, Microsoft 365 E5/A5, or Microsoft 365 E5 Security). When initially starting the MDE for Android app, the user needs to agree with the license agreement and privacy statement, by clicking Get started (as shown in Figure 6). That will bring users to the the wizard that will provide the MDE for Android app with the required permissions locally on the device (see Figure 7). When using the mentioned permissions in the app configuration, the storage permissions will already be in place. Once all the permissions are provided, the MDE for Android app is up-and-running.
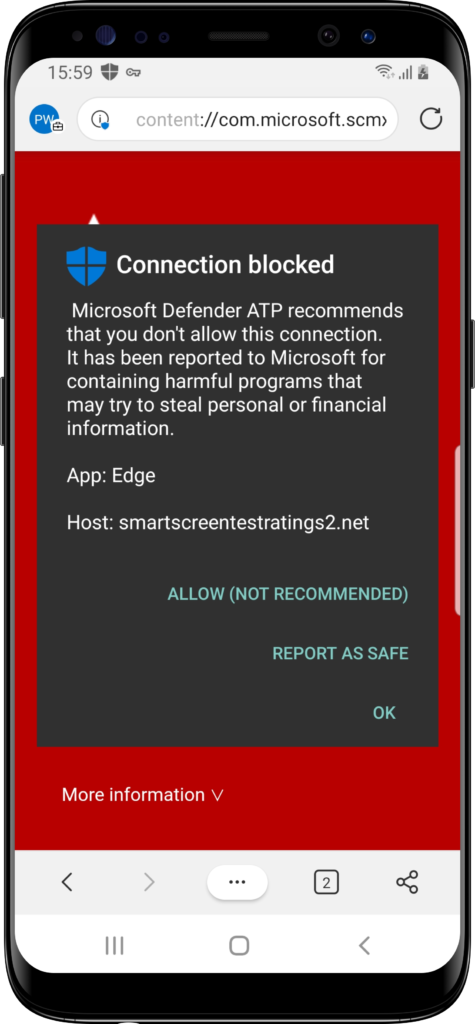
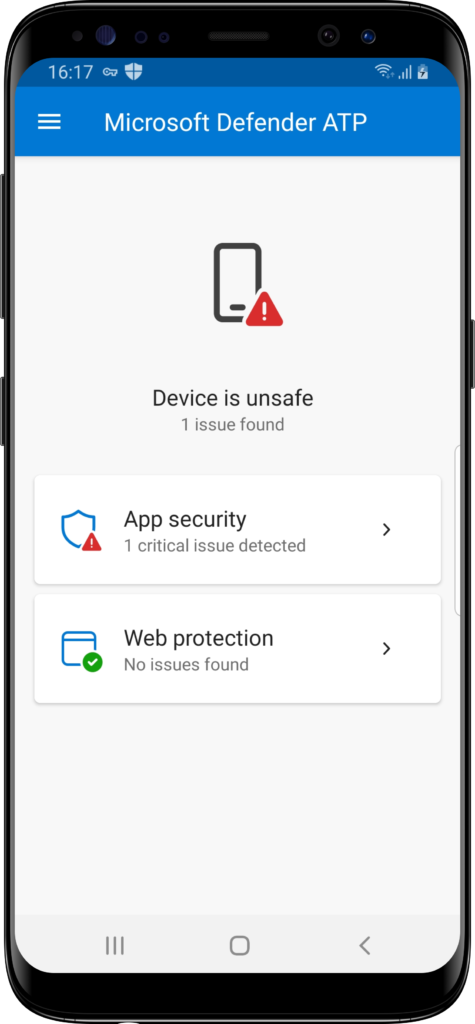
For testing the Web protection capability, Microsoft provides the smartscreentestratings2.net site. When navigating to that site, or any other phishing site, the user receives the “Connection blocked” message (as shown in Figure 8). That will be logged in the Microsoft Defender Security Center portal as “Informational“. Once the user ignores the message and continue to the site by clicking on Allow, the action will be logged as “Low“.
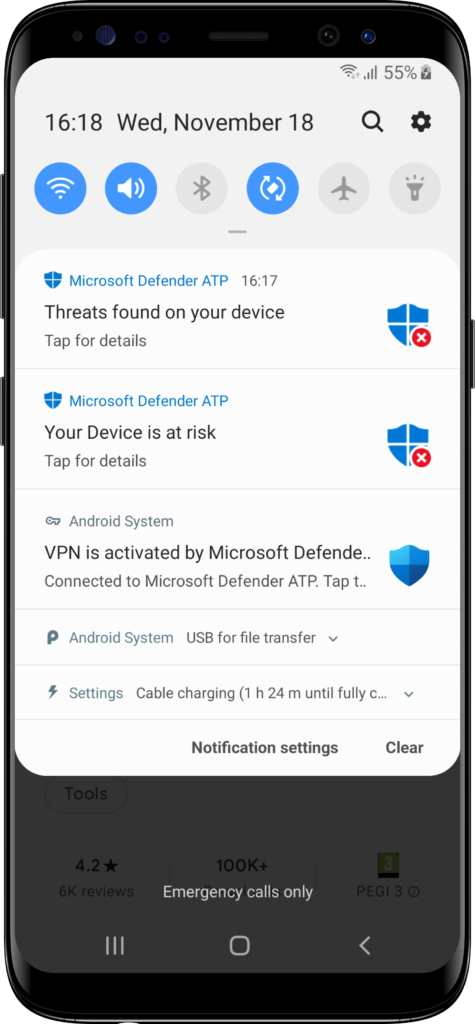
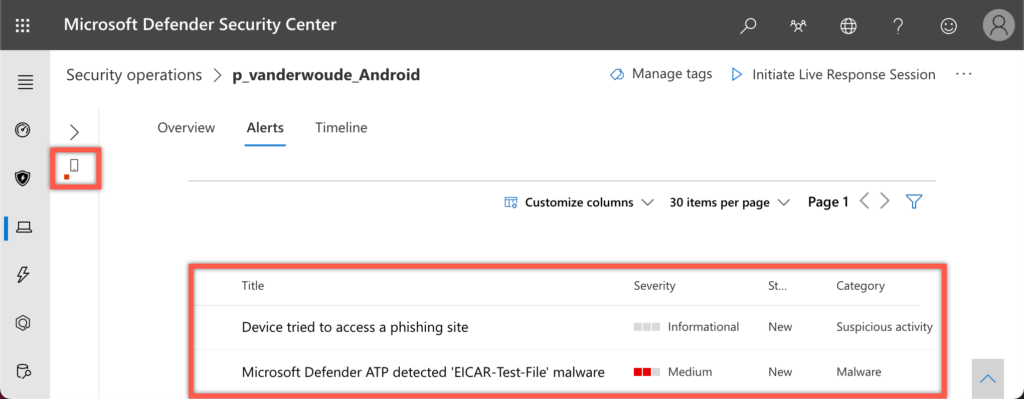
For testing the Malware scanning capability, Microsoft refers to the existing test apps in the Google Play store. Those apps simply contain an EICAR test file that should be captured by any antimalware app. For testing purposes my test user installed the first hit in the Google Play store, which is the Test Virus app. That app will immediately be caught by MDE for Android (as shown in Figure 9). When the user now checks the MDE for Android app, the device will be marked as unsafe (see Figure 10). When the user clicks on the notifications, or on the app security, they will be brought to the remediation action to uninstall the app. When the user wants to ignore that, the device will also be marked as noncompliant in Microsoft Intune (as shown in Figure 11). That will eventually block the access for the user to company data and apps. Assuming that conditional access is in place and requires a compliant device.
Note: When using MDE for Android on a device with a Work Profile (personally-owned or corporate-owned), it will only protect everything within the Work Profile.
Administrator experience
When looking at the administrator experience, I want to focus on the information that’s generated by the user. For an overview of the alerts, I’ve opened the Microsoft Defender Security Center portal and navigated to the Alerts of the device of the user. That provides the suspicious activity of visiting the test site and the malware of the test virus app. It also shows the earlier mentioned severity of the different actions.
As the user ignored the information that was provided by MDE for Android, the device will also be marked as noncompliant. For an overview of that message, I’ve opened the Microsoft Endpoint Manager admin center portal and navigate to device compliance policy settings of the compliance policy that was assigned to the user. That provides the current status of the device, based on the device risk.
More information
For more information about MDE for Android, the naming, the availability and the configuration, refer to the following docs.


Dag Peter,
is er echt geen mogelijkheid om de configuratie van de defender for android automatisch te laten gebeuren zonder tussenkomst van de eindgebruiker?
Hi Anthony,
To my knowledge the user still needs to approve some of the permissions.
Regards, Peter
Hi Peter, do you know if the web content filtering feature works on android devices please ? I can’t make it works 🙁
On my Windows 10 it works like a charms
Thanks !
Best regards, Nicolas
Hi Nicolas,
Web content filtering is for Windows devices, see also: https://docs.microsoft.com/en-us/microsoft-365/security/defender-endpoint/web-content-filtering?view=o365-worldwide#prerequisites
Regards, Peter
Hi Peter,
I am trying to enable defender in de personal profile but I get a license error?
We have all A5 licenses.
In the work profile it is working without issue?
Wim
Hi Wim,
Why would you also want to have it in the personal profile?
Regards, Peter
am i right to say it is by design that defender for endpoint only protects the work profile in android? it does not protect browser in personal profile.
Hi Jeff,
That is correct. This is focussed on the work profile. Good to know: there are now some options for the personal profiles also. See: https://learn.microsoft.com/en-us/microsoft-365/security/defender-endpoint/android-intune?view=o365-worldwide#set-up-microsoft-defender-in-personal-profile-on-android-enterprise-in-byod-mode
Regards, Peter
ms defender for ios and android does not scan downloaded attachment to check if it is virus. am i right?
That is correct, Jeff. That functionality is available via Defender for Office.
Regards, Peter
Hello Peter,
Have you tested if a second Defender on a Android phone heavily affects battery life?
I haven’t tested that, Patrick.
Regards, Peter
Which defender policy can we install on a work-profiled Android device to protect it from threats and malware? As per the above document, we cannot configure the anti-pishing policy for work profiles, so can you suggest the policy that is setup for Android Defender with a work profile
Hi Farheen,
Anti-phishing is part of the Web Protection.
Regards, Peter
Can you use defender for endpoint on Android devices in Azure AD shared mode with managed home screen?
Defender for Endpoint gets stuck loading in an infinite loop no matter what user is currently signed in. This behavior was identical on 3 android tablets that have been recently factory reset.
Hi Matt,
I don’t think that dedicated devices are supported, yet. See also: https://learn.microsoft.com/en-us/microsoft-365/security/defender-endpoint/microsoft-defender-endpoint-android?view=o365-worldwide#installation-instructions
Regards, Peter
Thank you for the reply.
Bummer! Hopefully this is on their near-term roadmap! We have ~20 android tablets that our automotive technicians share.
Hey,
I have been trying to find a way to disable the requirement for the VPN to be setup while installing the MS Defender for unmanaged Android (MAM) devices but no luck.
I have successfully disabled it for iOS/iPadOS devices but setting up an app configuration policy but the same doesn’t work for Android devices. I have tried creating both the ‘Managed apps’ and ‘Managed devices’ app configuration policies but nothing stops from Defender installing VPN.
You got any clue that might help?
Thanks!
Hi Manan,
Not sure exactly what you mean. To my knowledge, when you want to use Web Protection, you still need to use a VPN on Android devices.
Regards, Peter
I’m trialing a corporate -owned work profile (android) device, the compliance policy requires MDforE at or under Low. MDforE is installed but needs me to sign in to activate, but I can’t sign in as the device in non-compliant, so I’m stuck. what am I doing wrong?
Are you running into Conditional Access?
Regards, Peter
Hi,
I have implemented a conditional access on android with risk score “Low”. Everything works as expected except in one case: If my android device is compliant and then I uninstall defender on this device, the device remains compliant.
The installation of defender is required, so the app is reinstalled but no login has been made in the newly installed defender app. After 3 days without the app configured, the android device is still compliant with risk score “Low”.
Do you know how long it takes to be marked as non compliant? Does the risk score change after few days if the defender app is not discovered anymore? If yes, can we change the number of days?
Thanks,
Geoffrey.
Hi Geoffrey,
Apologies for the late reply, as I was enjoying my vacation. Sadly, we have experienced the same behavior and there was not much we could do as long as the user could uninstall the app. The best would be to contact Microsoft about this.
Regards, Peter
Hi, I implemented autogrant for storage as you described, but it’s not working. Could you tell me what the reasons could be?
Hi Federico,
Can you provide some more details about your configuration and experience?
Regards, Peter
I think the issue is due to this :
https://techcommunity.microsoft.com/t5/intune-customer-success/upcoming-permissions-changes-for-microsoft-defender-for-endpoint/ba-p/2945750
But 2 years later and still no auto grant its very disapointed
That indeed makes sense..
Regards, Peter