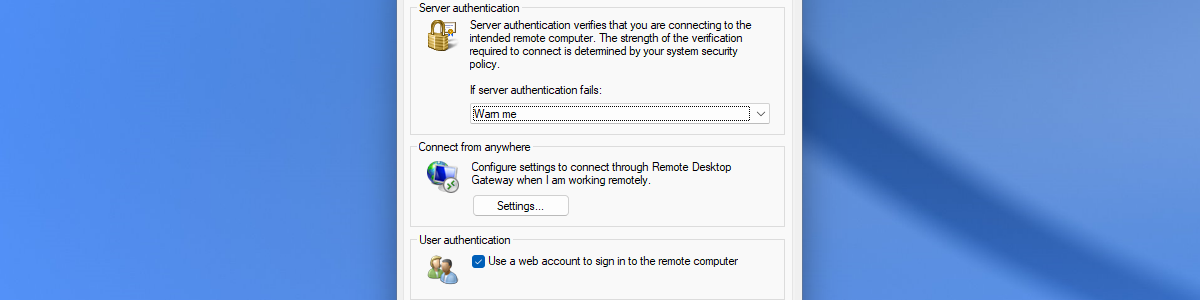
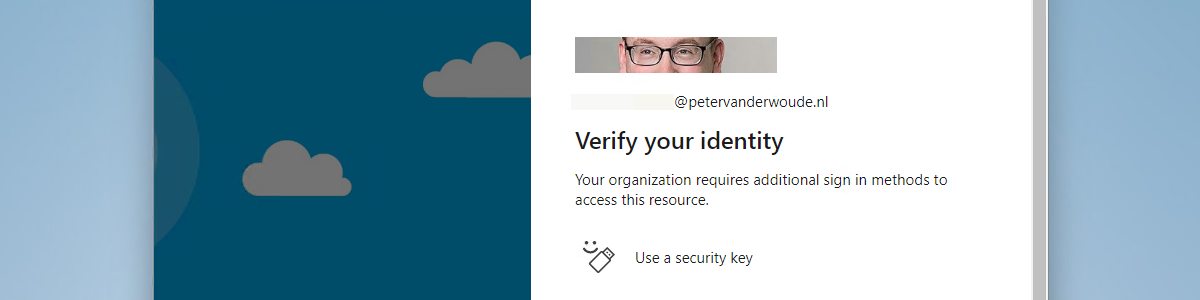
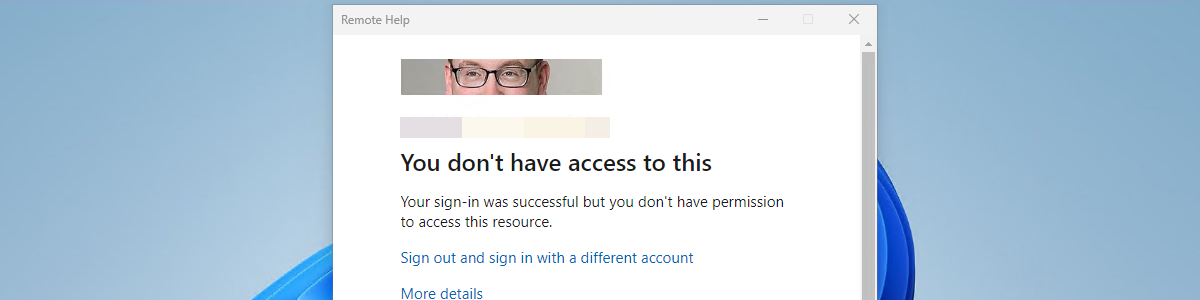
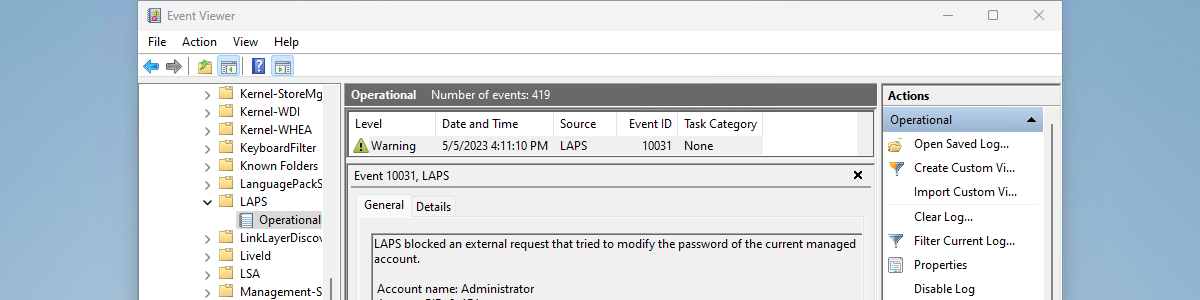
Enabling remote access for specific users on Azure AD joined devices
This week is sort of a follow-up on my previous posts about restricting the local log on to specific users. While those posts were focused on restricting the local log on, this post will be focused on enabling remote access for specific users. More specifically, remote access for specific users on Azure AD joined devices. That’s not something to exciting, but definitely something that comes in useful every now and then. Besides that, this was already possible – for a long time – but would often require the device to be joined to the same tenant and take out some security configurations (like Network Level Authentication). That’s no longer required – already for almost a year – as it it can now rely on Azure …