This week is sort of a follow-up on my previous posts about restricting the local log on to specific users. While those posts were focused on restricting the local log on, this post will be focused on enabling remote access for specific users. More specifically, remote access for specific users on Azure AD joined devices. That’s not something to exciting, but definitely something that comes in useful every now and then. Besides that, this was already possible – for a long time – but would often require the device to be joined to the same tenant and take out some security configurations (like Network Level Authentication). That’s no longer required – already for almost a year – as it it can now rely on Azure AD authentication. That can help in those specific cases were it’s needed to provide users with full remote access, but IT only wants to provide that while still relying on the available security capabilities of Azure AD (like Conditional Access). This is definitely not a solution for providing remote assistance. There are many better solutions available for that. For example, using Remote Help or Quick Assist. The configurations for providing remote access on a Azure AD joined device contains of a Remote Desktop configuration, a Windows Firewall configuration, and a local group membership. This post will start with a few prerequisites for this scenario, followed with steps for the required configurations. This post will end with experiencing the applied configuration.
Note: Keep in mind that Remote Help is part of the Microsoft Intune Suite and requires additional licenses.
Important prerequisites and implications
When looking at providing specific users with remote access to Azure AD joined devices, there a multiple options available. The focus for this post will be to rely on Azure AD authentication. That makes it possible to get remote access to Azure AD joined devices, without needing to have an Azure AD joined device in the same tenant. And also without having to turn of Network Level Authentication. Besides the further configurations in this post, to take advantage of Azure AD authentication the following versions and configurations must be in place:
- The local and remote device must be running Windows 10/11, with at least the 2022-10 cumulative update installed
- Remote Credential Guard should not be enabled on the local device
- Conditional Access for the Microsoft Remote Desktop app must be configured accurate for the user
Note: The local device is the device used for initiating the remote connection and the remote device is the device that the connection made with.
Enabling Remote Desktop on a Windows device
The first configuration that should be in place, is enabling Remote Desktop on the remote device. The device that the user wants to remotely connect to. When looking at the configuration options, the most important and useful option is the Settings Catalog profile in Microsoft Intune. The Settings Catalog contains the settings that are available via the TerminalServer.admx, which includes the required setting for allowing remote access. That means that those settings are ADMX-backed and directly available for use. The following eight steps walk through the creation of a Settings Catalog profile that contains the required setting to enable Remote Desktop on the remote device, by using the required policy setting.
- Open the Microsoft Intune admin center portal and navigate to Devices > Windows > Configuration profiles
- On the Windows | Configuration profiles blade, click Create profile
- On the Create a profile blade, provide the following information and click Create
- Platform: Select Windows 10 and later to create a profile for Windows 10 and Windows 11 devices
- Profile: Select Settings catalog to select the required setting from the catalog
- On the Basics page, provide the following information and click Next
- Name: Provide a name for the profile to distinguish it from other similar profiles
- Description: (Optional) Provide a description for the profile to further differentiate profiles
- Platform: (Greyed out) Windows 10 and later
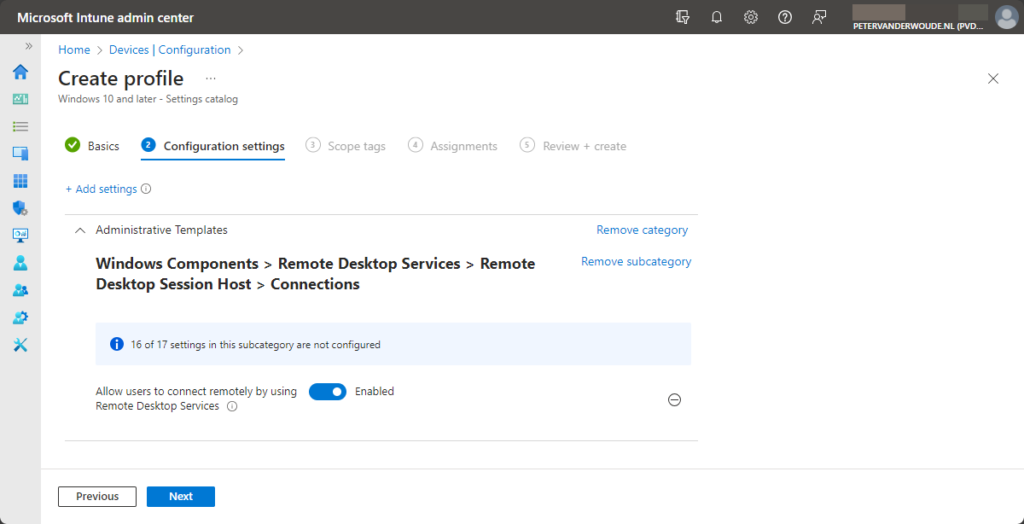
- On the Configuration settings page, as shown below in Figure 1, perform the following actions
- Click Add settings and perform the following in Settings picker
- Select Windows Components > Remote Desktop Services > Remote Desktop Session Host > Connections as category
- Select Allow users to connect remotely by using Remote Desktop Services as setting
- Switch the slider with Allow users to connect remotely by using Remote Desktop Services to Enabled and click Next
- On the Scope tags page, configure the required scope tags and click Next
- On the Assignments page, configure the assignment and click Next
- On the Review + create page, verify the configuration and click Create
Important: When relying on Azure AD authentication, it’s not required to disable Require user authentication for remote connections by using Network Level Authentication.
Allowing Remote Desktop in the Windows Firewall
The second configuration that should be in place, is allowing Remote Desktop through the Windows Firewall on the remote device. The device that the user wants to remotely connect to. When looking at the configuration options, the best option is the relatively new Microsoft Defender Firewall Rules profile in Microsoft Intune. That profile enables IT administrators to configure firewall rules for specific apps on Windows devices, by relying on the Firewall CSP. The following eight steps walk through the creation of a Microsoft Defender Firewall Rules profile that contains the required settings to allow Remote Desktop through the Firewall.
- Open the Microsoft Intune admin center portal and navigate to Endpoint Security > Firewall
- On the Endpoint security | Firewall blade, click Create Policy
- On the Create a profile page, provide the following information and click Create
- Platform: Select Windows 10 and later as value
- Profile: Select Microsoft Defender Firewall Rules as value
- On the Basics page, provide a valid name for the firewall rules profile and click Next
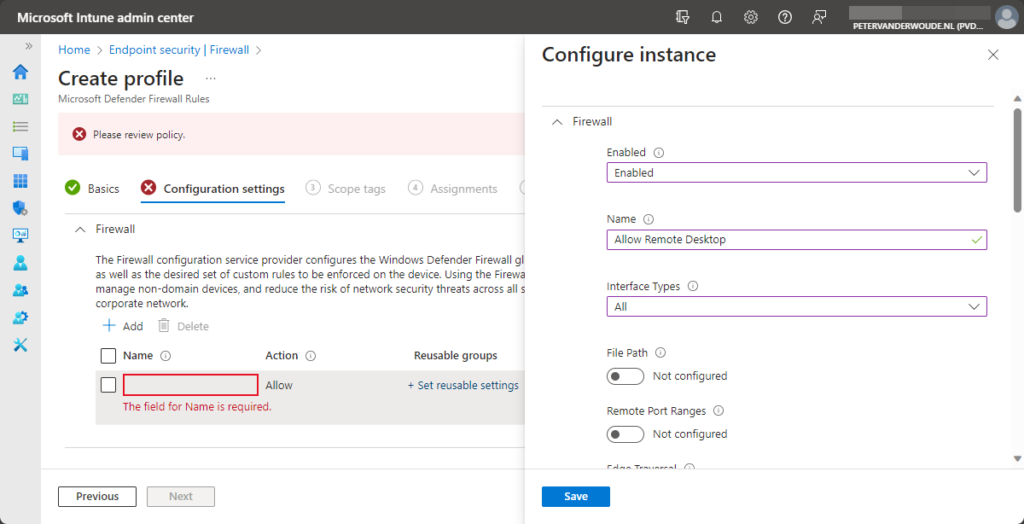
- On the Configuration settings page, as shown below in Figure 2, provide at least the following information and click Next
- Enabled: Select Enabled, to make sure that this Firewall rule will be enabled when configured
- Name: Specify a valid name, to easily recognize the Firewall rule when configured
- Interface Types: Select All, to apply the Firewall rule to all interfaces on the device
- Direction: Select The rule applies to inbound traffic, to apply the Firewall rule only to inbound traffic on the device
- Local Port Ranges: Switch the slider to Configured, and specify 3389, to only allow that port with the Firewall rule
- Action: Select Allow, to allow the traffic that is captured with this Firewall rule
- Protocol: Specify 6, to only allow TCP traffic with this Firewall rule
- On the Scope tags page, configure the required scope tags and click Next
- On the Assignments page, add the required user/device group and click Next
- On the Review + create page, review the configuration and click Create
Note: For tracing and troubleshooting hints for Firewall rules, have a look at the the Intune Customer Success blog.
Adding specific users to the Remote Desktop Users
The third configuration that should be in place, is providing the specific users with remote access to the remote device. That can be achieved by relying on the Remote Desktop Users group locally on the remote device. To add users to that group, the Local user group membership profile can be used. That profile enables IT administrators to configure local group memberships on Windows devices, by relying on the LocalUsersAndGroups section in the Policy CSP. The following eight steps walk through the creation of a Local user group membership profile that contains the required settings to add the specific users to the Remote Desktop Users.
- Open the Microsoft Intune admin center portal navigate to Endpoint security > Account protection
- On the Endpoint security | Account protection blade, click Create Policy
- On the Create a profile page, provide the following information and click Create
- Platform: Select Windows 10 and later as value
- Profile: Select Local user group membership as value
- On the Basics page, provide a valid name for the local user group membership profile and click Next
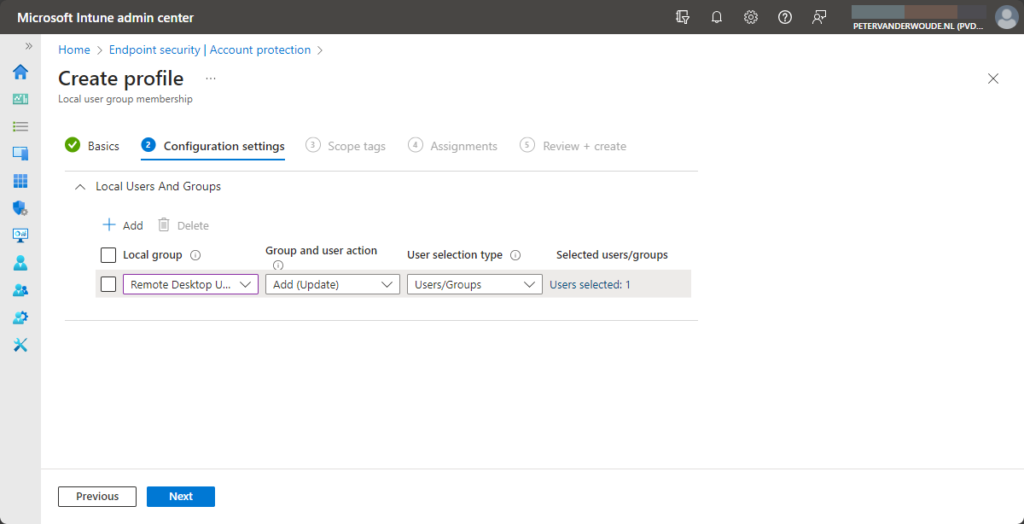
- On the Configuration settings page, as shown below in Figure 3, provide the following information and click Next
- Local group: Select Remote Desktop Users to configure the membership of the Remote Desktop Users group
- Group and user action: Select Add (Update) to update the membership of the Remote Desktop Users group
- User selection type: Select Users/Groups to enable the easy selection of the new members
- Selected users/groups: Click Select users/groups to open an additional blade to easily select the required new users and/or groups that should be member of the Remote Desktop Users group
- On the Scope tags page, configure the required scope tags and click Next
- On the Assignments page, add the required user/device group and click Next
- On the Review + create page, review the configuration and click Create
Note: Keep in mind that not every local group membership configuration has to be a different profile.
Experiencing the Remote Desktop configuration
When all the configurations are in place, it’s easy to experience a successful configuration. Simply open the Remote Desktop Connection app (mstsc.exe), navigate to the Advanced tab and select Use a web account to sign in to the remote computer. Now provide the required credential information and everything should be working. Also good to know is that when using a custom connection file, the RDP property enablerdsaadauth can be used.
Important: When connecting, the name of the remote device must be specified. That name must match the hostname of the remote device in Azure AD and must be network addressable, resolving to the IP address of that device.
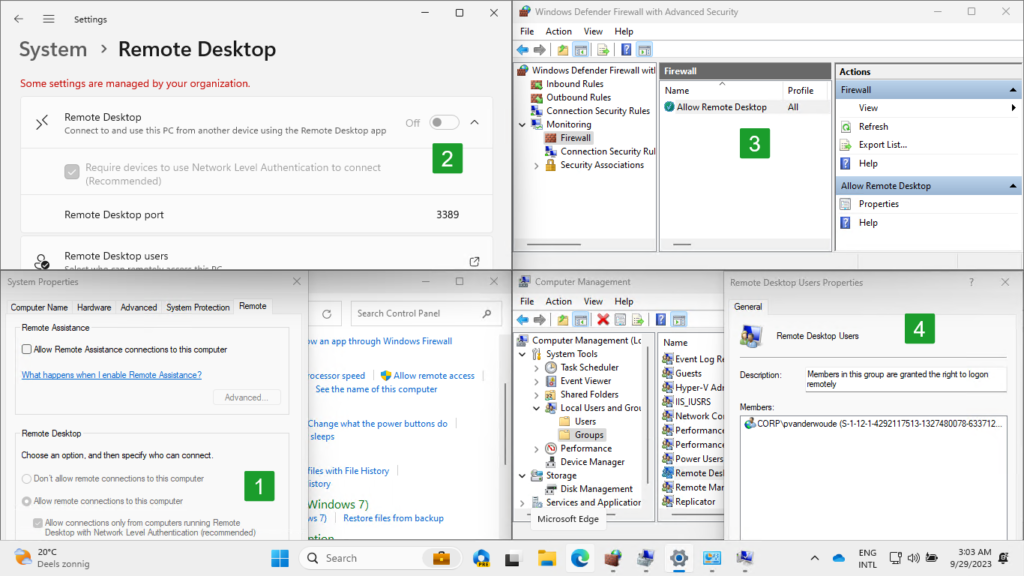
Besides that, in this case it’s also good to have a brief look at the applied configuration on the remote device. Basically all configurations are shown below in Figure 4. Especially the configuration of allowing remote connections. Mainly because the correct information is shown in the System properties via the Control Panel (see number 1) and the wrong information is shown in the Settings app (see number 2). Besides that, the Firewall rule can be found in the Monitoring section of the Windows Defender Firewall with Advanced Security (see number 3) and the Remote Desktop Users can be found in the Local Users and Groups section of Computer Management (see number 4).
More information
For more information about the Remote Desktop configuration options, refer to the following docs.
- Connect to remote Azure Active Directory joined device – Windows Client Management | Microsoft Learn
- RemoteDesktopServices Policy CSP – Windows Client Management | Microsoft Learn
- Firewall CSP – Windows Client Management | Microsoft Learn
- LocalUsersAndGroups Policy CSP – Windows Client Management | Microsoft Learn
hi,
Do you have any tip how to add the MFA to user login ?
thank you
Hi Wichur,
As it relies on web sign-in, it also includes Conditional Access in the flow. That enables you to require MFA.
Regards, Peter
Hi! Thank you!
It is working with my AD username (that is in localadmins group), but with simple user accounts not working the rdp connection.
After I gave the correct password: “The connection was denied because the user account is not authorized for remote login”
I think something is missing by me in this section: “Adding specific users to the Remote Desktop Users” Should I put in Assignments something? Users or device? Or both? (I tried, but not working)
Can you please help?
Hi Istvan,
That is an important step, as that provides the user with the permissions to do a RDP session to that device. As it’s a device specific configuration, I would assign it to devices.
Regards, Peter
Hi, any way of forcing the requirement for AAD signin? If the user ticks the box of web auth in a hybrid scenario it falls back to AD without MFA
Hi Arjan,
Not really. I would look at making the other route impossible.
Regards, Peter
Hi there,
We are assigning Remote Desktop Users via an Entra ID group but we also are getting the “The connection was denied because the user account is not authorized for remote login” error. When we assign user by user, it works fine.
Any thoughts of assigning Entra ID groups to Remote Desktop Users?
Hi Nigel,
Are you using the SID of the Entra groups? If so, are the users already in the group, or do you have a mechanism for adding those users?
Regards, Peter