This week is another short follow-up on the last couple of weeks. While the last couple of weeks were all about configuring the authentication on Azure file shares and on mapping Azure file shares, this week is all about the exclusion for multi-factor authentication (MFA). During the initial post, about using Azure AD Kerberos authentication for Azure file shares, it was mentioned that Azure AD Kerberos doesn’t support using MFA for accessing Azure file shares. The steps to prevent that, just weren’t described. And based on comments and feedback, it’s good to still walk through the steps for configuring that exclusion. This post will briefly discus the challenge, followed with the steps to create the exclusion for Azure file shares. This post will end with the user experience.
Note: Keep in mind that this post is only applicable when using Azure AD Kerberos authentication for Azure file shares. For more information, have a look at this post about configuring Azure AD Kerberos authentication.
Configuring the exclusion for Azure file shares
When looking at the not supported MFA configuration, the focus is all on Conditional Access policies. More specifically, Conditional Access policies that are assigned to all cloud apps. When looking at an Azure file share that relies on Azure AD Kerberos authentication, there will be an Azure AD app representing the storage account. That app registration is also targeted by Conditional Access policies that are assigned to all cloud apps. Those Conditional Access policies can be used to require specific access controls, including requiring MFA for access. The challenge with requiring MFA is that it’s not supported by Azure AD Kerberos.
For actually making sure that the Azure file shares are not assigned with Conditional Access policies that require MFA, the Azure AD app representing the storage account, that contains the file shares, can be excluded from the different Conditional Access policies. The following three steps walk through the process of creating that configuration.
- Open the Microsoft Endpoint Manager admin center portal navigate to Endpoint security > Conditional Access – or open the Azure portal and navigate to Azure Active Directory > Security > Conditional Access
- On the Conditional Access | Policies blade, select the Conditional Access policy that requires MFA on all cloud apps
- On the Assignments section, as shown below in Figure 1, configure at least the following and click Save
- Cloud apps or actions: Select the Exclude tab and use the Select excluded cloud apps configuration to select the Azure AD app representing the storage account
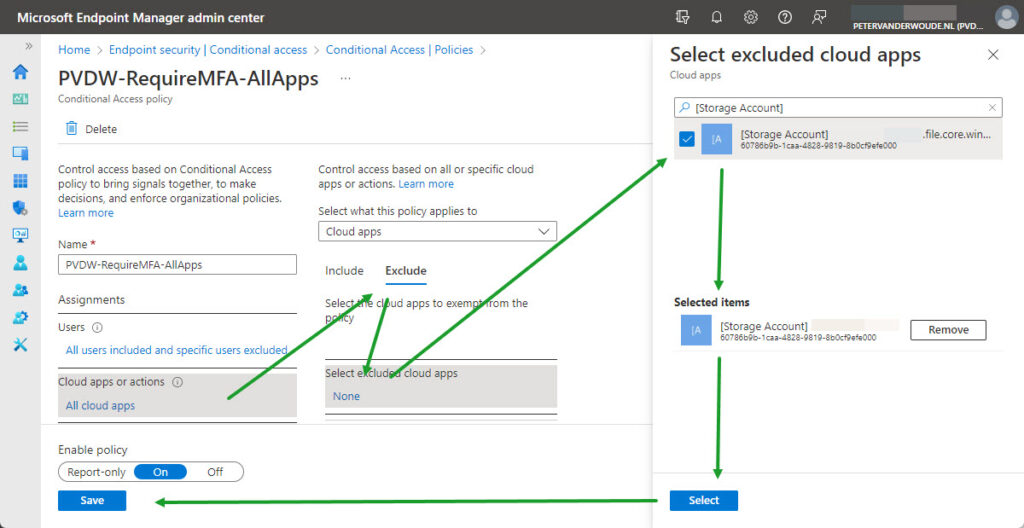
Note: The provided steps can be used for any Conditional Access policy that might be problematic and for any storage account that might need to be excluded.
This doesn’t mean, however, that Conditional Access policies that require MFA are always problematic. When a token is already available on the device that contains a claim that satisfies the MFA requirement, the mapping of the Azure file share will also be successful. In that case, it simply uses the existing token. The main challenge is when no such token is available on the device, when mapping the Azure file share.
Experiencing before the exclusion for Azure file shares
When looking at the user experience, the best method for experiencing the behavior is before the exclusion of the Azure file shares. Simply because that shows the error that users will experience. That behavior is shown below in Figure 2. It shows the message that the user will receive when trying to connect the Azure file share, while a Conditional Access policy is applied that requires MFA. That provides the user with the message that account restrictions are preventing the sign-in.
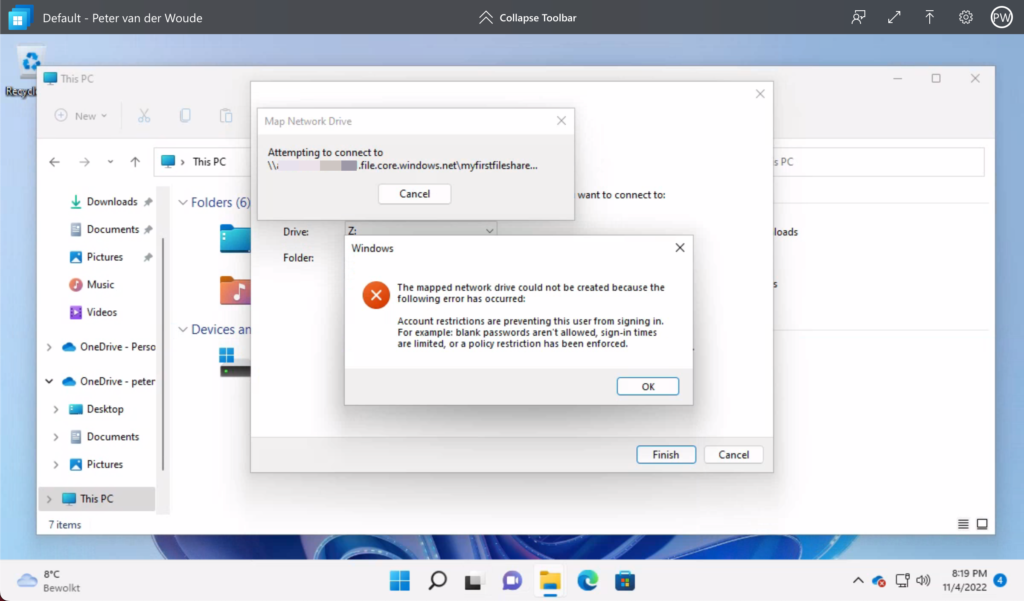
Note: As mentioned before, this doesn’t mean that it won’t work at all. When a token is already available that contains a claim that satisfies the MFA requirement, the sign-in will still be successful.
More information
For more information about Azure File shares and authentication, refer to the following docs.
Hi, can the other policies (e.g., Device Compliant) be applied on the storage account?
I would like to try using it to transfer some data from my local file server to Azure Files (leaving it read-only).
I would like to access it via a desktop shortcut via \\test.filecore.windows.net\test
Hi Michelle,
Yes, that should be possible.
Regards, Peter
HI there – when I try to do this so we can use FSLogix, I get an Invalid Session Control error when I try to Save. Our blanket MFA policy at the moment has Sign in Frequency set to x days and Persistent Browser Session set to Always. Is there a way round this as I can’t get FSLogix working until the file share app is excluded from MFA.
Hi Simon,
I’m afraid not, as the documentation explicitly mentions that behavior: https://learn.microsoft.com/en-us/azure/storage/files/storage-files-identity-auth-hybrid-identities-enable?WT.mc_id=EM-MVP-5001447&tabs=azure-portal#disable-multifactor-authentication-on-the-storage-account
Regards, Peter