Troubleshooting MAM for Windows
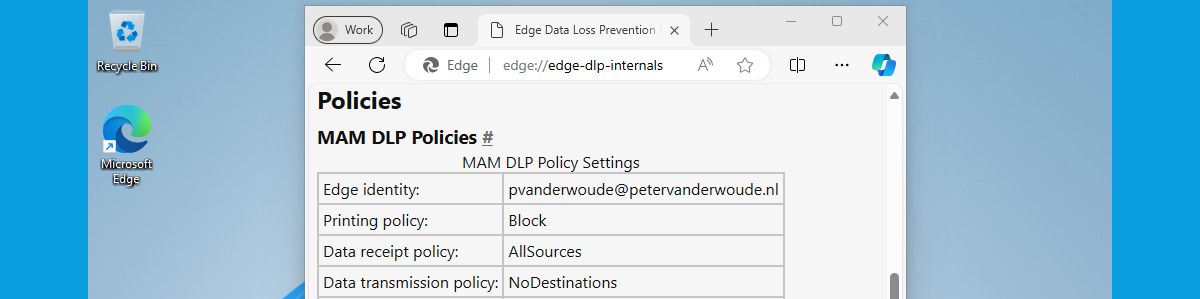
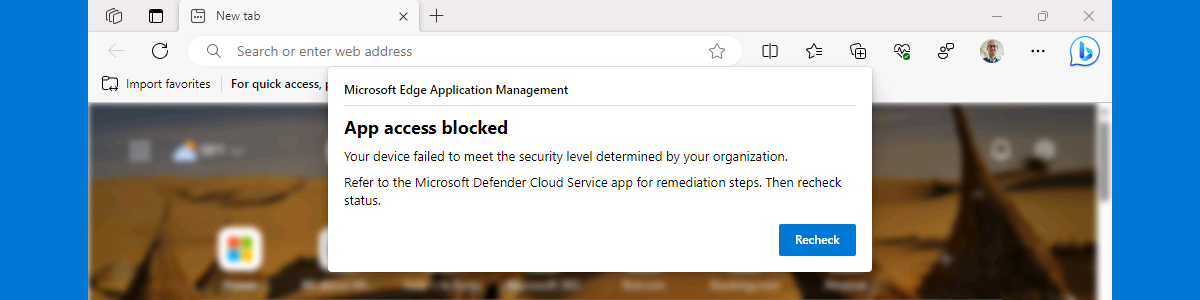
This week is a short follow-up on a post of a few months ago about getting started with Mobile Application Management (MAM) for Windows. That post was really focused on getting started with MAM for Windows, while this post will be more focused on what’s coming after that. The concept and the basic configuration of MAM for Windows is pretty straight forward, once being familiar with the available configuration options. However, it gets more challenging when verifying the configuration and the behavior. Especially when there is not that much information available. The (location of the) log file is not really well documented, as is the process to verify the applied configuration. This post will provide answers to those questions. It will described were to find …