This week is all about one of the new Intune Suite add-on capabilities. The capability of focus is Microsoft Tunnel for Mobile Application Management (Tunnel for MAM) for iOS/iPadOS devices. The Intune Suite add-ons were released at the beginning of March, including a new licensing model, and including Tunnel for MAM. That capability on itself, is available as part of the new Microsoft Intune Plan 2 license. Tunnel for MAM makes it possible to provide access to on-premises resources, on unmanaged devices. Often unmanaged devices are equal to personal-owned devices. So, that provides IT with the flexibility to make that app, with on-premises interaction, available on personal-owned devices. Without requiring the user to enroll that specific device, but still enforcing secure access and guaranteeing full privacy. It provides all the strong capabilities that were already available via Microsoft Tunnel, like modern authentication, single sign-on, and conditional access, to access on-premises apps and resources on unmanaged devices. This post will zoom-in on using Microsoft Edge for accessing an on-premises hosted website. Mainly focused on enabling that functionality, and not focused on using Tunnel for MAM versus using the Azure AD Application Proxy. This post will end by showing the user experience with Tunnel for MAM for iOS/iPadOS devices.
Important: This post assumes that Microsoft Tunnel is already up-and-running. To get started, refer to this post.
Note: The VPN-functionality is provided via the Tunnel for MAM SDK for iOS integration. That also brings VPN-functionality to LOB apps, but does require an additional app registration in Azure AD that is out-of-scope for this post.
To configure Tunnel for MAM for iOS/iPadOS devices, and use Microsoft Edge for accessing on-premises resources, the following profiles and policies can be used, each with their own purpose (including a link to more details in this post):
- App protection policy: Used for protecting the data and creating the MAM channel.
- Trusted certificate profile: Used for creating a chain of trust for resource protected with an internal SSL/TLS certificate
- App configuration policy: Used for configuring Microsoft Tunnel settings for Microsoft Edge
Configuring an app protection policy for Microsoft Edge
When looking at applying the app configuration policy, it all starts with an app protection policy. That policy is used for providing the required data protection for any corporate data, but also, even more important in this scenario, it establishes a path for delivering the app configuration policy to an unmanaged device. It basically creates the MAM channel that can then also be used for applying an app configuration policy. The following ten steps walk through the basics of creating an app protection policy for Microsoft Edge on unmanaged iOS/iPadOS devices.
- Open the Microsoft Intune admin center portal navigate to Apps > App protection profiles
- On the Apps | App protection policies blade, click Create policy > iOS/iPadOS
- On the Basics page, specify a valid name to distinguish the profile from other similar profiles and click Next
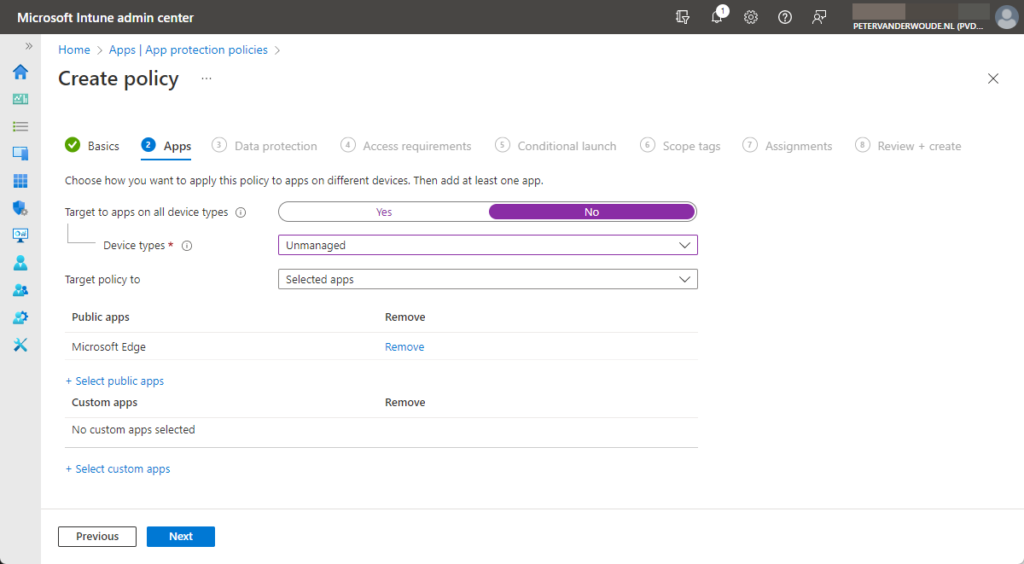
- On the Apps page, as shown below in Figure 1, provide at least the following information and click Next
- Target to apps on all device types: Select No to enable targeting to specific device types
- Device types: Select Unmanaged to target this policy only to unmanaged devices
- Target policy to: Select Selected apps to make it possible to select a specific app
- Public apps: Select Select public apps > Microsoft Edge as the app to protect
- On the Data protection page, configure the required data protection settings and click Next
- On the Access requirements page, configure the required access requirements and click Next
- On the Conditional launch page, configure the required app conditions and device conditions and click Next
- On the Scope tags page, configure the required scope tags and click Next
- On the Assignments page, configure the required assignment by selecting the applicable user group and click Next
- On the Review + create page, review the configuration and click Create
Configurating a trusted certificate profile
When looking at providing access through Tunnel for MAM to resources that are protected by an SSL/TLS certificate, it’s important to establish a chain of trust. That’s not a problem when the certificate is issued by a public certificate authority, but becomes challenging when the certificate is issued by an on-premises certificate authority. In that case it’s required to make sure that the device trusts the certificate that was issued. That can be achieved by using a trusted certificate profile. This profile, however, doesn’t need to be assigned to the users or their devices. Only the public-key certificate payload of that profile is used by Tunnel for MAM. So, simply selecting any trusted certificate profile for that certificate chain will be sufficient. When no such profile is available yet, the following eight steps walk through the creation of a trusted certificate profile.
- Open the Microsoft Intune admin center portal navigate to Devices > Configuration profiles
- On the Devices | Configuration profiles blade, click Create profile
- On the Create a profile page, provide the following information and click Create
- Platform: Select iOS/iPadOS as value, but this can basically be any platform
- Profile: Select Templates > Trusted certificate as value, to start with the creation of the required profile
- On the Basics page, specify a valid name to distinguish the profile from other similar profiles and click Next
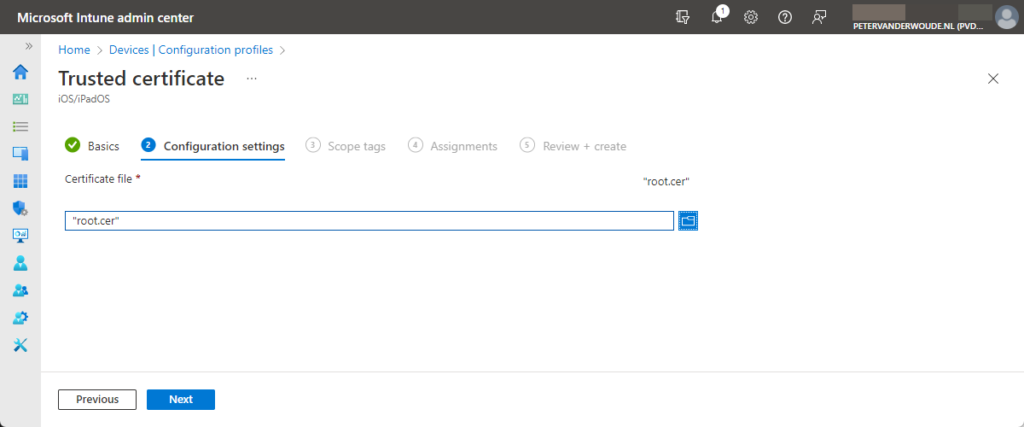
- On the Configuration settings page, as shown below in Figure 2, select the root certificate and click Next
- On the Scope tags page, configure the required scope tags and click Next
- On the Assignments page, configure any assignments (which is not required for this purpose) and click Next
- On the Review + create page, review the configuration and click Create
Configuring an app configuration policy for Microsoft Edge
When looking at providing Tunnel for MAM functionality, it all starts with an app configuration policy. That policy is used for configuring Microsoft Edge to enable Tunnel for MAM. Besides that, it’s also possible to implement the identity switch functionality, to make sure that the connection is not available for the personal account of the user. That behavior can be achieved by using the following new key value pair.
- key: com.microsoft.intune.mam.managedbrowser.TunnelAvailable.IntuneMAMOnly
- value: True
The configuration of that app configuration policy for Microsoft Edge, is pretty straight forward. The following seven steps will walk through the process of creating that policy, including adding that new key-value pair.
- Open the Microsoft Intune admin center portal navigate to Apps > App configuration policies
- On the Apps | App configuration policies blade, click Add > Managed apps
- On the Basics page, provide the following information and click Next
- Name: Provide a valid name to distinguish the policy from other similar policies
- Description: (Optional) Provide a valid name to further distinguish the policy from other similar policies
- Device enrollment type: (Grayed out) Managed apps
- Target policy to: Select Selected apps to make it possible to select a specific app
- Public apps: Select Select public apps > Microsoft Edge as the app to configure
- On the Settings page, provide at least the following information and click Next
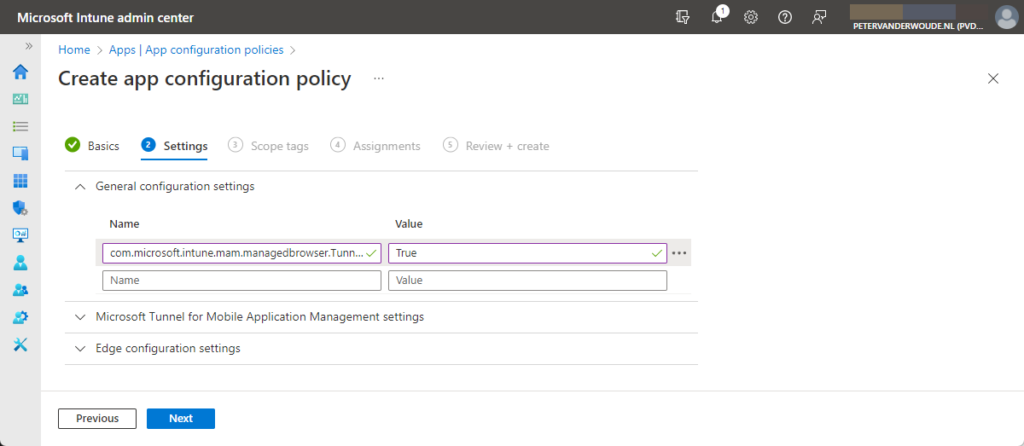
- In the General configuration settings section, as shown below in Figure 3, configure
- Specify com.microsoft.intune.mam.managedbrowser.TunnelAvailable.IntuneMAMOnly as Name and True as Value to enable the identity switch support to Microsoft Edge
- In the Microsoft Tunnel for Mobile Application Management settings section, as shown below in Figure 4, configure
- Use Microsoft Tunnel for MAM: Select Yes to use Microsoft Tunnel for MAM
- Connection name: Specify a valid name for the connection that will show on the device
- Microsoft Tunnel site: Select Select a Site and select the Tunnel site that should be used
- Root Certificate: (Optional) Select Root certificate and select the trusted certificate profile that should be used
- Automatic configuration script: (Optional) Specify an url for the proxy auto-config (PAC) file
- Address: (Optional) Specify the address of a proxy that the traffic should be routed through
- Port Number: (Optional) Specify the port number that relates to the proxy address

- In the Edge configuration settings section configure any Microsoft Edge specific configurations not related to Tunnel
- On the Scope tags page, configure the applicable scope tags and click Next
- On the Assignments page, configure the required assignment by selecting the applicable user group and click Next
- On the Review + create page, review the configuration and click Create
Experiencing Microsoft Tunnel for Mobile Application Management with Microsoft Edge
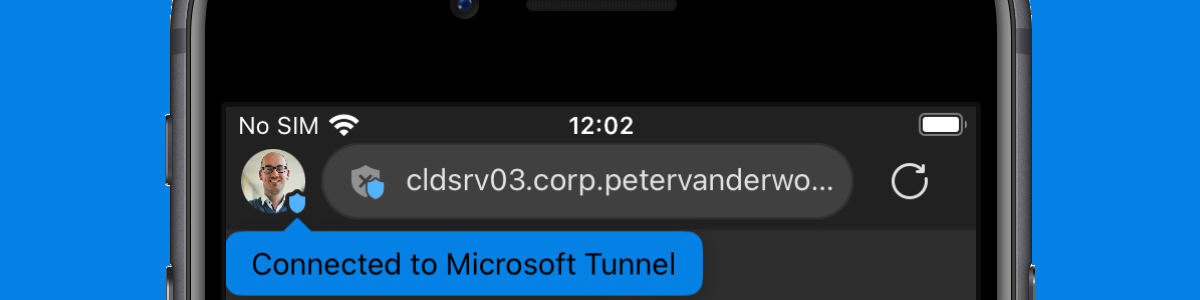
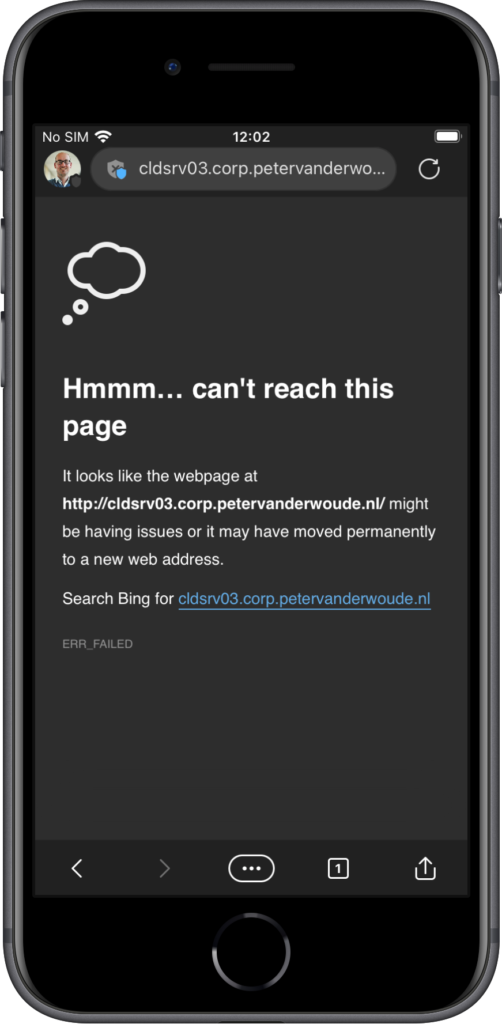
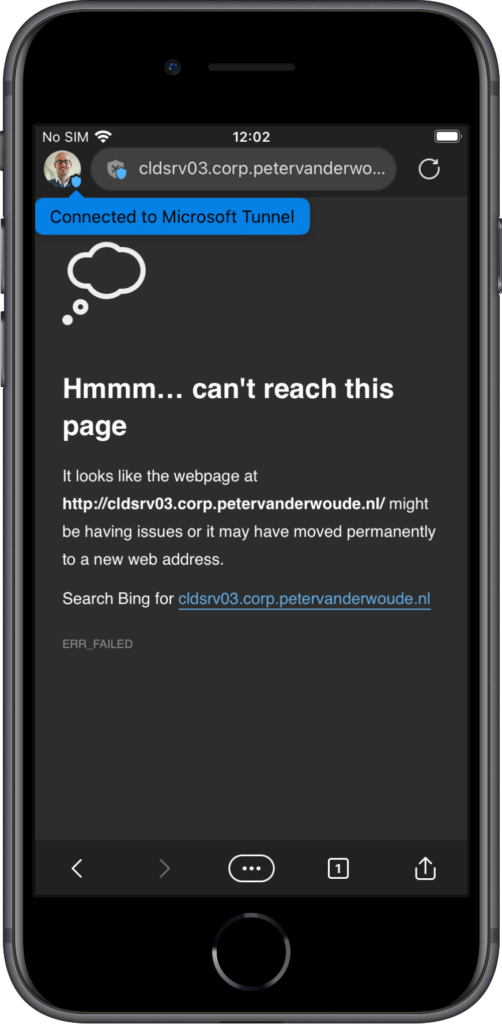
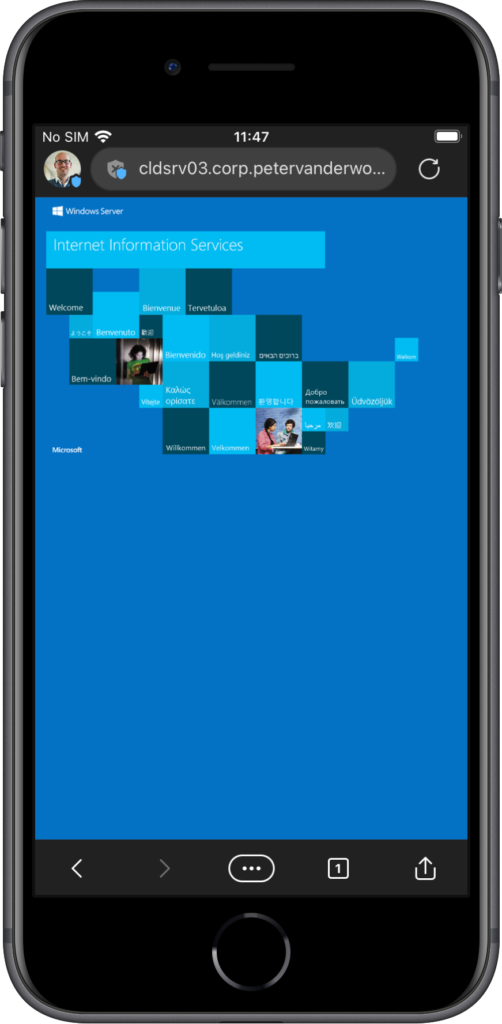
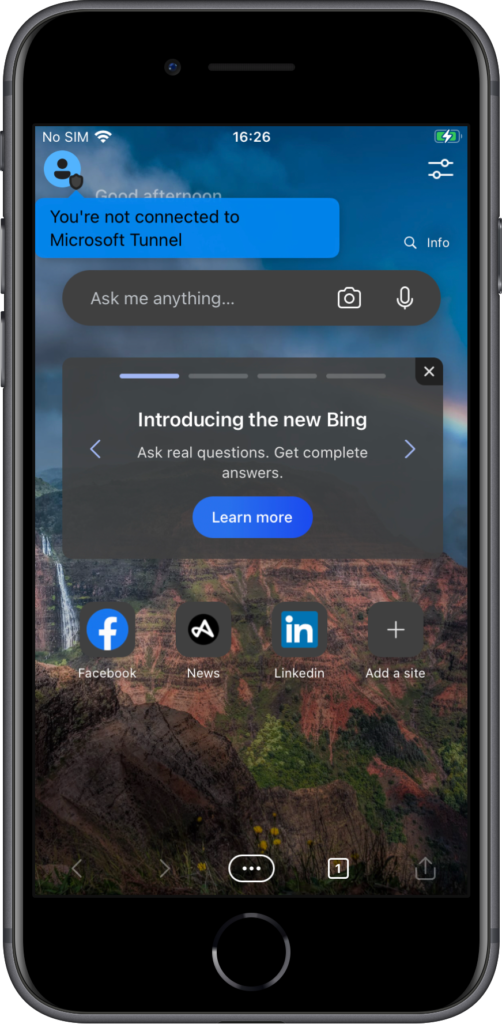
After applying the different parts of the configuration, the behavior and the experience will change for the user in Microsoft Edge. And there aren’t any requirements that have to be in place, except for the Microsoft Edge app itself. Every piece of intelligence that is needed, is available within that app. Only when requiring multi-factor authentication, via Conditional Access, the Microsoft Authenticator app will be required. The change to the user experience is all in the details. The small details make it clear for the user when Tunnel for MAM is connected. At least, when knowing what to look for. When the user initially opens Microsoft Edge, Tunnel for MAM will not be connected and the internal resources will not be available (as shown below in Figure 5). In a few seconds Microsoft Tunnel will connect, notify the user and makes the shield with the user icon blue (as shown below in Figure 6). Once connected the user can connect to internal apps and resources (as shown below in Figure 7 with a basic IIS page). The grey shield with the cross indicates that it’s an HTTP site.
When the connection is secured with a SSL/TLS certificate, and the public-key certificate payload was provided in the configuration, the grey shield will change to grey informational round (as shown below in Figure 8). The best part of all of this, is that it’s also connected to the profile of the user when the identity switch is configured. As soon as the user switches to a personal profile, Tunnel for MAM will automatically disconnect and notify the user (as shown below in Figure 9).
More information
For more information about Tunnel for MAM for iOS/iPadOS devices, refer to the following docs.
2 thoughts on “Getting started with Microsoft Tunnel for Mobile Application Management for iOS/iPadOS”