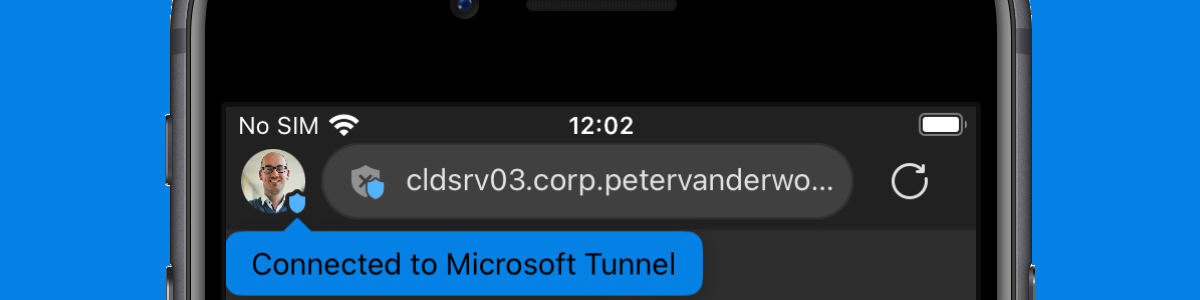
Getting started with Microsoft Tunnel for Mobile Application Management for iOS/iPadOS
This week is all about one of the new Intune Suite add-on capabilities. The capability of focus is Microsoft Tunnel for Mobile Application Management (Tunnel for MAM) for iOS/iPadOS devices. The Intune Suite add-ons were released at the beginning of March, including a new licensing model, and including Tunnel for MAM. That capability on itself, is available as part of the new Microsoft Intune Plan 2 license. Tunnel for MAM makes it possible to provide access to on-premises resources, on unmanaged devices. Often unmanaged devices are equal to personal-owned devices. So, that provides IT with the flexibility to make that app, with on-premises interaction, available on personal-owned devices. Without requiring the user to enroll that specific device, but still enforcing secure access and guaranteeing full …