This week is all about managing the updates channels for the different Microsoft Defender Antivirus update types. On one hand to create some awareness for the different update types, and on the other hand to show the latest configurations options for managing the updates channels for those different update types. Microsoft Defender Antivirus contains three different update types and up to six updates channel configuration options. That provides IT administrators with quite some configuration options for the devices within the environment. And starting with the latest service release of Microsoft Intune (2302), the update channel configurations becomes easily configurable via a specific configuration profile. That enables IT administrators to also use different update channels throughout the environment to gradually rollout the different updates of Microsoft Defender Antivirus. This post will start with an introduction to the update types and updates channels, followed with the configuration options in Microsoft Intune. This post will end with experiencing the applied configuration.
Introducing Microsoft Defender Antivirus updates channels
When looking at managing the Microsoft Defender Antivirus updates channels, it starts by being familiar with the different updates types that are available. The updates for Microsoft Defender Antivirus are separated into three different update types that also all have a different update cadence. The table below provides an overview of those update types.
| Update type | Cadence | Description |
|---|---|---|
| Engine updates | Monthly | This update type contains new engine updates that are provided with the security intelligence updates. |
| Platform updates | Monthly | This update type contains new platform updates that are provided via KB4052623. |
| Security intelligence updates | Daily (multiple) | This update type contains new security intelligence updates (defenitions) that are provided via KB2267602. |
For a gradual rollout of the different update types, there are multiple updates channels available. The number of available updates channels, is related to the update cadence. The monthly updates provide relatively many update channels, to gradually rollout those updates throughout the environment. The daily updates provide lesser available update channels. Simply because of the importance of those updates and the quick turnaround time of those updates. Out-of-the-box Microsoft already utilizes a monthly gradual release cycle that contains three stages and differentiates between between beta, preview, and the rest. For enterprise environments that can create different behavior across devices. To get that under more control, IT administrators can manage the updates channel of the devices in the environment. The table below provides an overview of the updates channels and the relation with the different update types.
| Updates channel | Value | Update type | Description |
|---|---|---|---|
| Not configured (Default). | 0 | Engine updates, platform updates, security intelligence updates | This update channel configuration is used for devices to stay up to date automatically during the gradual release cycle. |
| Beta Channel | 2 | Engine updates, platform updates | This update channel configuration is used for devices that will be the first to receive new updates and is used for identifying and reporting issues to Microsoft. Devices in the Windows Insider Program are subscribed to this channel by default. |
| Current Channel (Preview) | 3 | Engine updates, platform updates | This update channel configuration is used for devices that will be offered updates earliest during the monthly gradual release cycle. |
| Current Channel (Staged) | 4 | Engine updates, platform updates, security intelligence updates | This update channel configuration is used for devices that will be offered updates after the monthly gradual release cycle. |
| Current Channel (Broad) | 5 | Engine updates, platform updates, security intelligence updates | This update channel configuration is used for devices that will be offered updates only after the gradual release cycle completes. |
| Critical – Time delay | 6 | Engine updates, platform updates | This update channel configuration is used for devices that will be offered updates with a 48-hour delay. |
Configuring Microsoft Defender Antivirus updates channels
When looking at the configuration of the Microsoft Defender Antivirus updates channels, it all starts with the Antivirus policies. Those policies now also include the Defender Update controls profile. That profile can be used to easily configure the Microsoft Defender Antivirus updates channels. The settings within that profile rely on the Defender CSP and are now also available via the Settings Catalog. The following eight steps walk through the configuration by using the new Defender Update controls profile.
- Open Microsoft Intune admin center navigate to Endpoint security > Antivirus
- On the Endpoint security | Antivirus blade, click Create policy
- On the Create a profile page, provide the following information and click Create
- Platform: Select Windows 10 and later as value
- Profile: Select Defender Update controls as value
- On the Basics page, provide a unique Name to distinguish the profile from other similar profiles and click Next
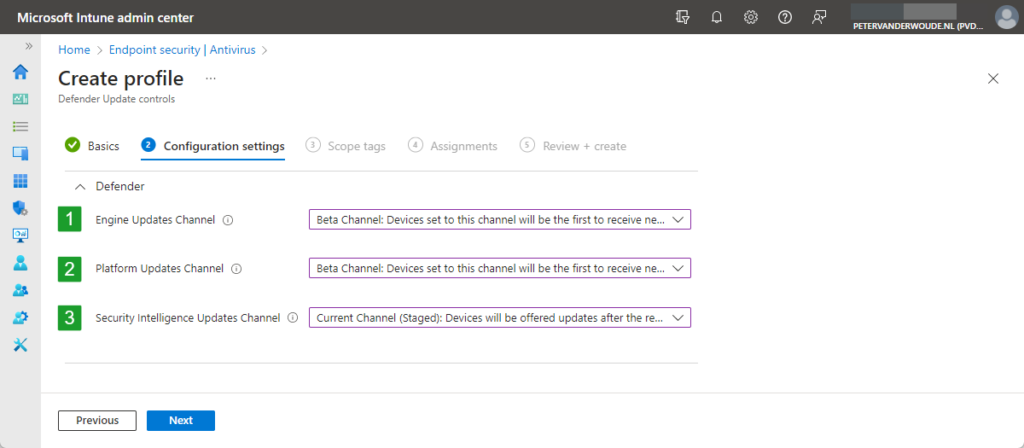
- On the Configuration settings page, as shown in Figure 1, configure the following settings and click Next
- Engine Updates Channel (1): Select the channel for the engine updates that is needed for the assigned devices, by choosing from the available channels as described in the table above
- Platform Updates Channel (2): Select the channel for the platform updates that is needed for the assigned devices, by choosing from the available channels as described in the table above
- Security Intelligence Updates Channel (3): Select the channel for the security intelligence updates that is needed for the assigned devices, by choosing from the available channels as described in the table above
- On the Scope tags page, configure the required scope tags click Next
- On the Assignments page, configure the assignment to the required users and/or devices and click Next
- On the Review + create page, verify the configuration and click Create
Experiencing configured Antivirus updates channels
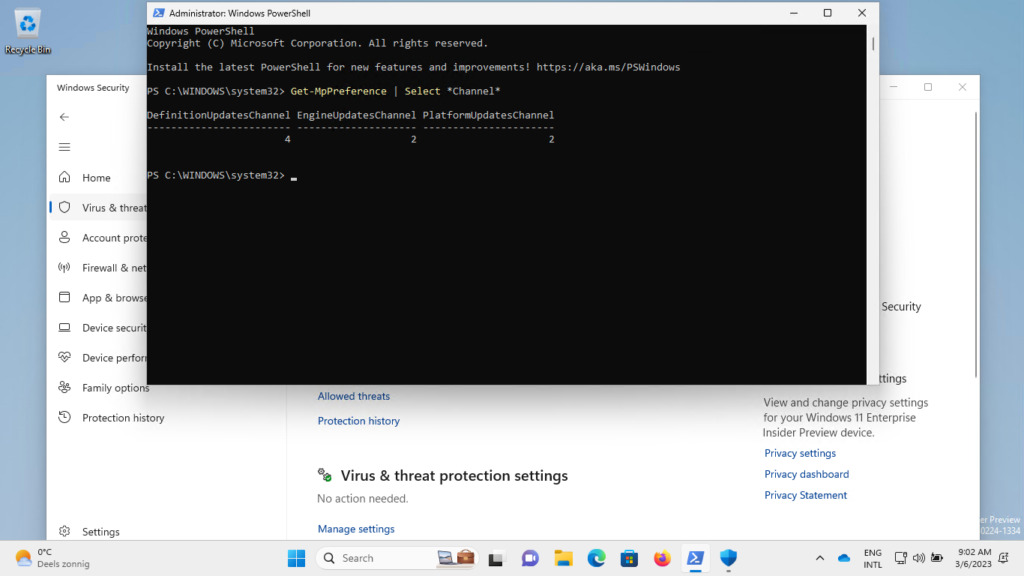
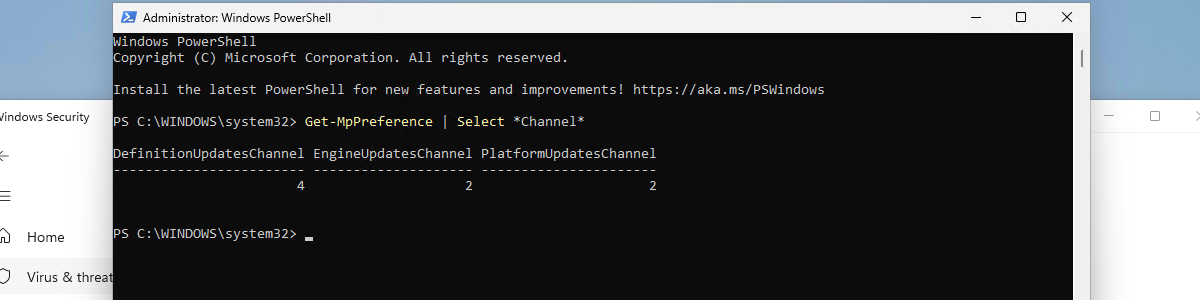
When looking at experiencing the applied Microsoft Defender Antivirus updates channels, it’s all about PowerShell. PowerShell can be used to retrieve the applied configuration, as the Windows Security app doesn’t seem to display that information. The Get-MpPreference cmdlet can be used to get the preferences for the Defender scans and updates, as shown below in Figure 2.
More information
For more information about the new settings to configure Antivirus updates channels, refer to the following docs.
- Defender CSP – Windows Client Management | Microsoft Learn
- Manage antivirus settings with endpoint security policies in Microsoft Intune | Microsoft Learn
- Manage the gradual rollout process for Microsoft Defender updates | Microsoft Learn
- Create a custom gradual rollout process for Microsoft Defender updates | Microsoft Learn
- Microsoft Defender Antivirus security intelligence and product updates | Microsoft Learn
Hi
Can i disable all Microsoft Defender Antivirus updates via Intune?
I tried to pause update rings policy but device will still download and install Security Intelligence Update for Microsoft defender AntiVirus in background
Thanks.
Hi AS,
Why would you want to disable those updates?
Regards, Peter
I don’t know how to handle the signatures updates with device in co-management and endpoint protection switched to intune. Could you help me?
Hi Denis,
What issues are you running into?
Regards, Peter
I have devices in co-management and endpoint protection switched to intune.
I don’t know if configuring the “SignatureUpdateFallbackOrder” policy works with devices in co-management.
In addition i can’t find any clear indications in microsoft documentation about that, what is the best practice? How can I eventually distribute the signatures updates via configuration manager?
And what about the Windows updates workload?
Regards, Peter
I have configured the “signatureupdatefallbackorder” option in Endpoint Security configuration in Intune, devices are in co-management with endpoint protection workload switched to intune pilot. When we check the report in Intune the policy fails with error 65000.
Microsoft confirmed us that endpoint protection workload include signature updates management.
In configuration manager the windows update workload is switched to configuration manager, because we distribute updates.
Hi Denis,
The setting SignatureUpdateFallbackOrder is part of the Defender CSP. So, with the switched workload and that statement of Microsoft, I would expect it to be applicable. What are you seeing in the Event Log when that settings is applied?
Regards, Peter
I need to check the event log, but.. settings to option to “not configured” the warning doesn’t appeair, when I do a manual update of the signatures from the Intune fails.
is there a particular configuration to do in co-management scenario?
because I have a similar problem configuring the windows firewall client and rules.
Hi Denis,
In general, it’s all about switching the applicable workloads. When those workloads are switched the management authority for the related settings will switch. Did you check to see if the workloads are actually switched on the client?
Regards, Peter