Easily managing Microsoft Defender Antivirus updates channels
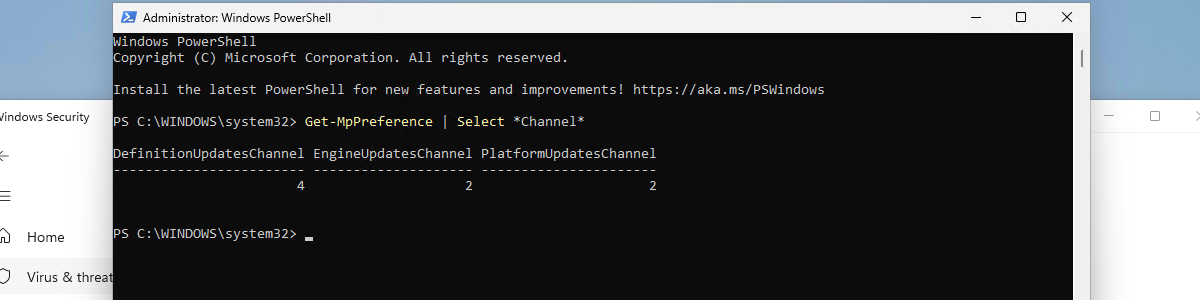
This week is all about managing the updates channels for the different Microsoft Defender Antivirus update types. On one hand to create some awareness for the different update types, and on the other hand to show the latest configurations options for managing the updates channels for those different update types. Microsoft Defender Antivirus contains three different update types and up to six updates channel configuration options. That provides IT administrators with quite some configuration options for the devices within the environment. And starting with the latest service release of Microsoft Intune (2302), the update channel configurations becomes easily configurable via a specific configuration profile. That enables IT administrators to also use different update channels throughout the environment to gradually rollout the different updates of Microsoft …