This week is all about Microsoft Defender Application Guard (Application Guard) for Office. It’s a follow up on this post of almost 2 years ago. That time the focus was simply on getting started with Application Guard and it slightly missed out on Application Guard for Office. This time Application Guard for Office will be the main focus. Application Guard for Office uses hardware isolation to isolate untrusted Office files, by running the Office application in an isolated Hyper-V container. That isolation makes sure that anything potentially harmful in those untrusted Office files, happens within that isolated Hyper-V container and is isolated from the host operating system. That isolation provides a nice, but resource intensive, additional security layer. This post will start with a quick introduction about Application Guard for Office, followed with the steps to configure Application Guard for Office. This post will end with the user experience with Application Guard for Office.
Introducing Microsoft Defender Application Guard for Office
Application Guard for Office helps with preventing untrusted Office files, of Word, PowerPoint and Excel, from accessing trusted resources. That might sounds similar to the functionality that is already provided by Protected View. The main difference, however, is that Protected View is mainly a read-only mode and most editing functionalities are disabled. Application Guard for Office, on the other hand, is more a restricted mode that allows limited editing and printing functionalities while minimizing the risk by opening untrusted Office files in an isolated container. That brings enhanced security combined with enhanced productivity, to the user.
An Office file is considered untrusted when it originates from the internet, when it’s located in a potentially unsafe location, or when it’s blocked by the File Block functionality. Once the user opens an untrusted file, Application Guard will make sure that the file will open in the corresponding Office app in an isolated Hyper-V container. That will make sure that when that file was malicious, the local device is not affected. It stays contained in the isolated Hyper-V container. In general, Application Guard is a perfect fit in the assume breach strategy, as that strategy also means that the next best thing is to contain the damage by protecting the corporate resources and data. It can contain further damage within the isolated Hyper-V container.
Note: When used in combination with Safe Documents, the Office file will be verified against the Microsoft Defender for Endpoint service to determine if it’s malicious before it’s opened outside of Application Guard for Office.
The minor detail is that Application Guard for Office is quite heavy on the requirements. The following are minimally required for using Application Guard for Office:
- License requirement: Microsoft 365 E5 or Microsoft 365 E5 Security
- Hardware requirement: 64-bit process with 4 cores and virtualization extensions, 8GB memory, and 10GB free space
- Platform requirement: Windows 10 Enterprise, version 2004 or later, or any version of Windows 11
- Office requirement: Microsoft 365 apps for enterprise, version 16.0.13530.10000 or later
Note: Keep in mind that Application Guard is officially not supported on VMs and VDI environments.
Creating attack surface reduction policy for app and browser isolation
When looking at the configuration of Application Guard for Office, it all starts with the attack surface reduction policies. The attack surface reduction policies, include the Apps and browser isolation profile. That profile can be used to relatively easy enable Application Guard for Office, as it contains the option to enable Application Guard for isolated Windows environments. That option includes Application Guard for Office. The following eight steps walk through the required steps for configuring Application Guard for Office, including some context with the configuration options.
Important: Make sure to enable the hypervisor before enabling Application Guard, to prevent failures.
- Open Microsoft Endpoint Manager admin center navigate to Endpoint security > Attack surface reduction
- On the Endpoint security | Attack surface reduction blade, click Create profile
- On the Create a profile page, provide the following information and click Create
- Platform: Select Windows 10 and later as value
- Profile: Select Apps and browser isolation as value
- On the Basics page, provide a unique Name to distinguish the profile from other similar profiles and click Next
- On the Configuration settings page, as shown in Figure 1, configure the following settings and click Next
- Turn on Application Guard (1): Select Enabled for isolated Windows environments as value, to turn on Application Guard for Office
- Application Guard allow use of Root Certificate Authorities from the user’s device (2): Specify any required certificate thumbprints to automatically transfer the matching root certificate to the virtual environment
- Application Guard allow print to local printers (3): Select Yes to allow print to local printers in the virtual environment
- Application Guard allow print to network printers (4): Select Yes to allow print to network printers in the virtual environment
- Application Guard allow print to PDF (5): Select Yes to allow print to PDF in the virtual environment
- Application Guard allow print to XPS (6): Select Yes to allow print to XPS in the virtual environment
- Windows network isolation policy (7): Select Configure to define any trusted locations by specifying IP ranges, cloud resources, network domains, (internal) proxy servers, or neutral resources.

Note: The last setting can be used to define which locations are automatically trusted by Application Guard for Office. Exvery location that is not defined, will automatically be untrusted.
- On the Scope tags page, configure the required scope tags click Next
- On the Assignments page, configure the assignment to the required users and/or devices and click Next
- On the Review + create page, verify the configuration and click Create
Experiencing Microsoft Defender Application Guard for Office
Tip: When using a VM for testing Application Guard for Office, make sure to configure nested virtualization. Also, make sure that the VM meets the minimal requirements, or, when needed, to bypass the hardware requirements by using the documented registry keys.
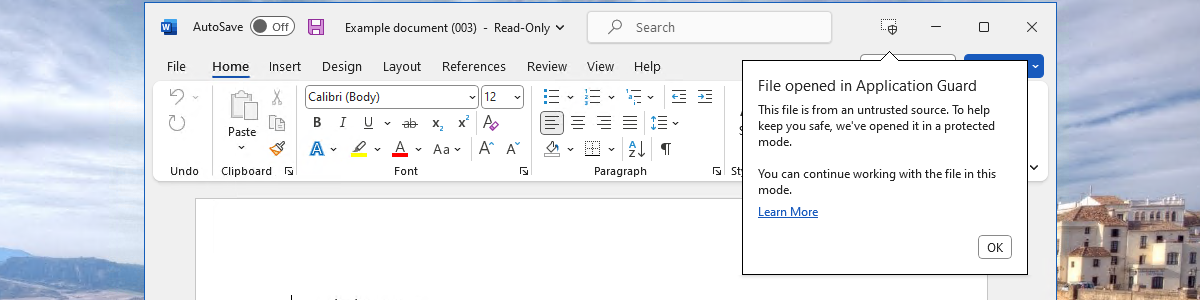
Experiencing the configuration of Application Guard for Office is actually pretty simple. Just open an untrusted Office file and see what happens. In the example shown below in Figure 2, the untrusted Office file is a Word document that was received via email. When opening that document, Word will take a bit longer to start and will show the message: To keep you safe, we’re opening this document in Application Guard. Once Word has opened the document, the user can see that the document is opened in Application Guard, by looking at the shield icon on the top of the window (shown with number 1) and by looking at the shield icon with the Word application in the taskbar (shown with number 2).

When Word is running in Application Guard, certain capabilities will not be available. That includes no access to the identity of the user (see the missing signed-in user), documents that are protected with IRM can’t be opened, and all capabilities that extend the capabilities of Word (like add-ins and macro’s) are not available.
More information
For more information about Microsoft Defender Application Guard for Office, refer to the following docs.
I’m curious about your note: “Important: Make sure to enable the hypervisor before enabling Application Guard, to prevent failures.” Does that mean that the hyper-v feature needs to be enabled via a separate powershell script in Intune (Enable-WindowsOptionalFeature -Online -FeatureName Microsoft-Hyper-V -All)? The ms doco doesn’t state that, but I can’t get application guard to enable via Intune ASR policy without doing it.
Hi Jeremy,
At that time that was indeed my experience. The docs don’t mention it anymore and even implies that PowerShell does it all at once (see: https://learn.microsoft.com/en-us/windows/security/threat-protection/microsoft-defender-application-guard/install-md-app-guard).
Regards, Peter