This week is sort of another follow-up on the earlier posts about new Microsoft Intune Suite add-on capabilities. This time it’s all about the latest addition, Microsoft Cloud PKI (Cloud PKI). Cloud PKI provides organizations with a cloud-based service that simplifies and automates the certificate lifecycle management for Intune managed devices. It literally provides a public key infrastructure (PKI) from the cloud. That PKI environment can be built within a few minutes, by simply going through a couple of wizards. Even when relying on at least a two-tier hierarchy, with a root certificate authority (CA) and an issuing CA. There is no longer a need to maintain on-premises servers, connectors, or hardware. Cloud PKI handles the certificate issuance, renewal, and revocation for Intune managed devices. The latter is also something to keep in mind. Cloud PKI makes a lot of certificate scenarios a whole lot easier. Just not for non-Intune managed devices. This post will go through the steps for creating a two-tier hierarchy and using that environment for deploying certificates to the Intune managed devices.
Important: Keep in mind that during trial licenses, the CAs are created using software-backed keys, instead of HSM-backed keys. Those CAs can still be used when purchasing an actual license, but the keys remain software-backed.
Note: For more information around the PKI hierarchy that should be used, please refer to the Microsoft docs.
Creating the root CA
When looking at the creation of a two-tier hierarchy, it all starts with the root CA. The good thing is that Cloud PKI provides a lot of flexibility in that area. An organization can either create their root CA within Cloud PKI, or use the concept of bring your own certificate authority (BYOCA). The latter basically means that it’s possible to rely on any existing PKI infrastructure within the (on-premises) environment. The following six steps walk through the process of creating a root CA within Cloud PKI. A really straight forward process that directly shows the simplicity of Cloud PKI.
- Open the Microsoft Intune admin center portal and navigate to Tenant admin > Cloud PKI
- On the Tenant admin | Cloud PKI page, click Create
- On the Basics page, provide a valid name certification authority and click Next
- On the Configuration settings page, as shown in Figure 1 and Figure 2, provide the following information and click Next
- CA type (1): Select Root CA to create a new root CA
- Validity period (2): Select the validity period for that root CA by choosing between 5, 10, 15, 20, or 25 years
- Extended Key Usages (3): Select the purpose of the root CA by selecting the required key usage types
- Subject attributes (4): Specify at least the Common name (CN) that helps to identify the CA
- Encryption (5): Select the key size and algorithm that should be used for the CA by choosing between RSA-2048 and SHA-256, RSA-3096 and SHA-384, and RSA-4096 and SHA-512
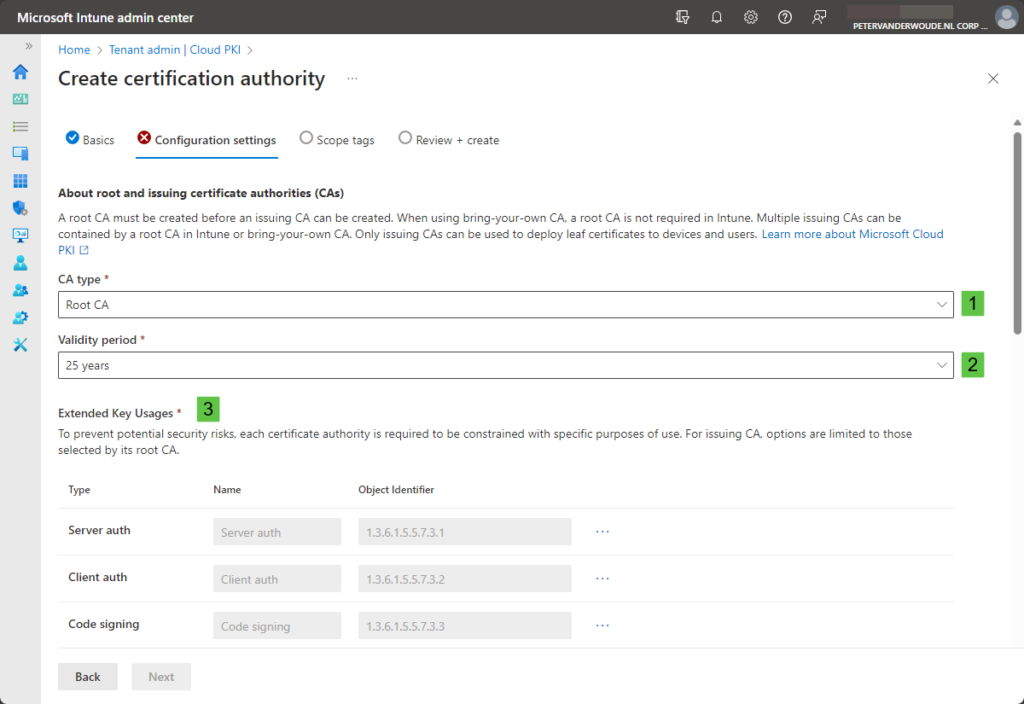
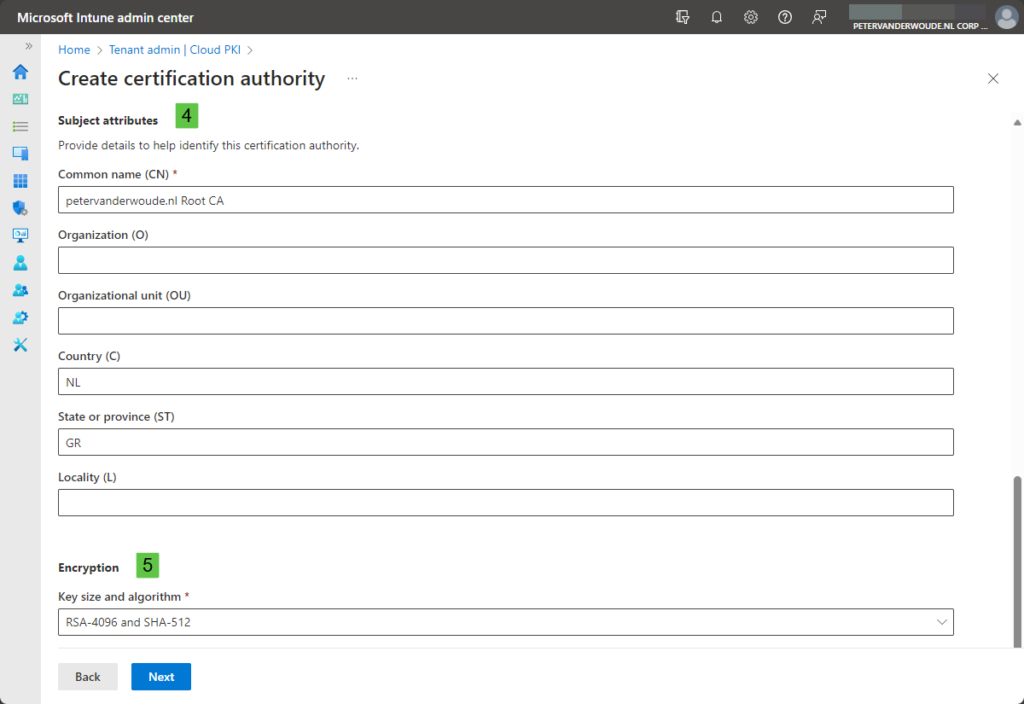
Important: The purpose of the root CA cannot be adjusted after the initial configuration of the root CA and the purpose of any issuing CA will be limited to the purpose of the related root CA.
Note: Additional purposes can be added by simply using the related object identifier of the extended key usage.
- On the Scope tags page, add any required scope tags and click Next
- On the Review + create page, verify the configuration and click Next
Creating the issuing CA
When the root CA is available, either by creating a root CA in Cloud PKI or BYOCA, it’s time to create the issuing CA. The issuing CA will be responsible for issuing the certificates for Intune managed devices. During the creation of that issuing CA, Cloud PKI automatically provides the Simple Certificate Enrollment Protocol (SCEP) service that is used to request certificates from the issuing CA on behalf of the Intune managed devices. The following six steps walk through the process of creating that issuing CA within Cloud PKI. A really straight forward process that further shows the simplicity of Cloud PKI.
- Open the Microsoft Intune admin center portal and navigate to Tenant admin > Cloud PKI
- On the Tenant admin | Cloud PKI page, click Create
- On the Basics page, provide a valid name certification authority and click Next
- On the Configuration settings page, as shown in Figure 3 and Figure 4, provide the following information and click Next
- CA type (1): Select Issuing CA to create a new issuing CA
- Root CA source: Select Intune to be able to select the earlier created root CA
- Root CA: Select the earlier created root CA
- Validity period (2): Select the validity period for that issuing CA by choosing between 2, 4, 6, 8, or 10 years
- Extended Key Usages (3): Select the purpose of the issuing CA by selecting the required key usage types
- Subject attributes (4): Specify at least the Common name (CN) that helps to identify the CA
- Encryption (5): The key size and algorithm is preconfigured based on the configuration of the root CA
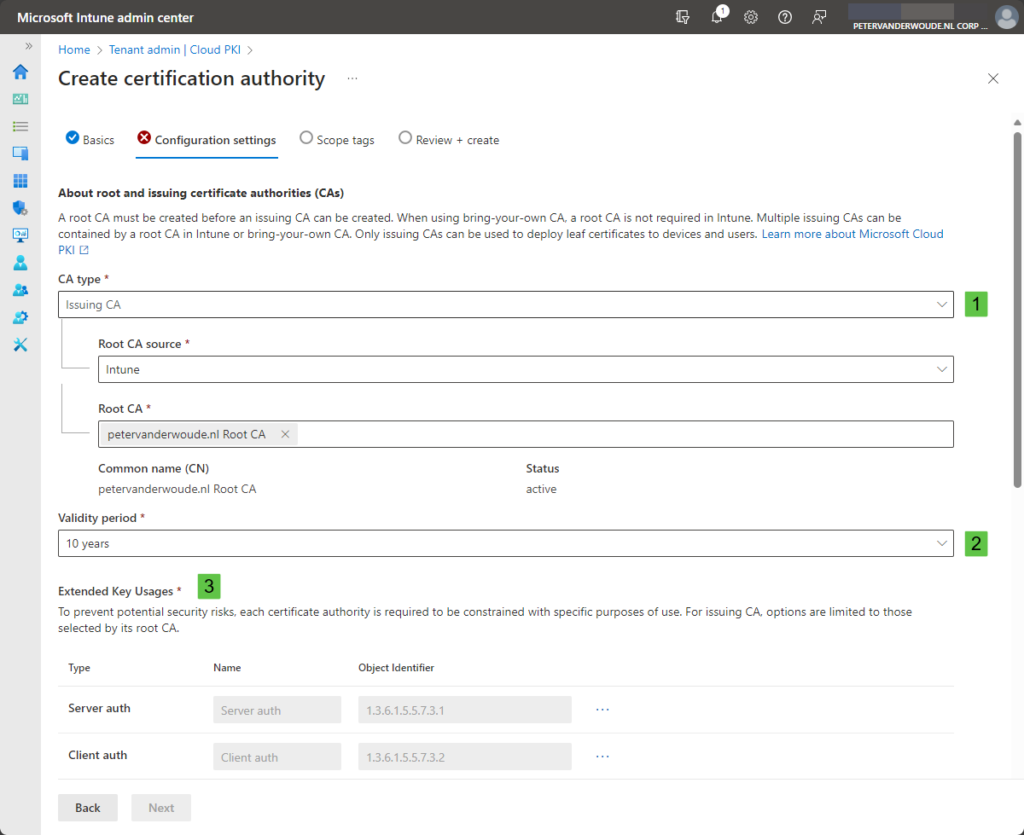
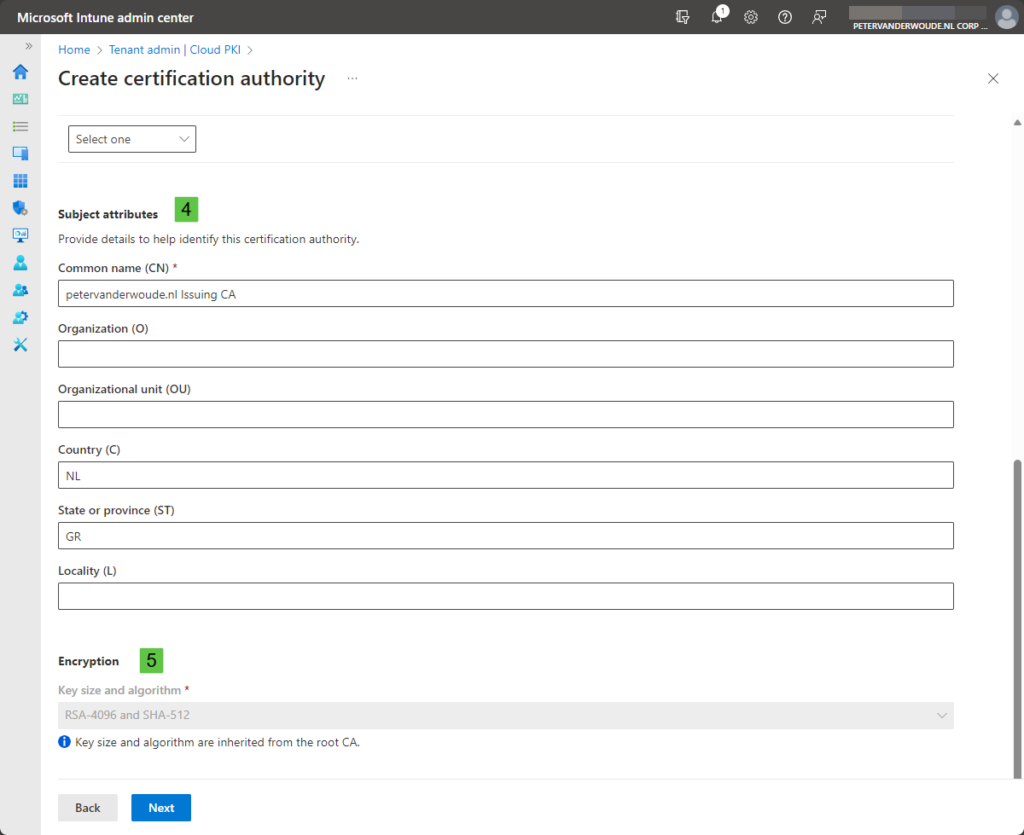
- On the Scope tags page, add any required scope tags and click Next
- On the Review + create page, verify the configuration and click Next
Distributing the trusted certificates
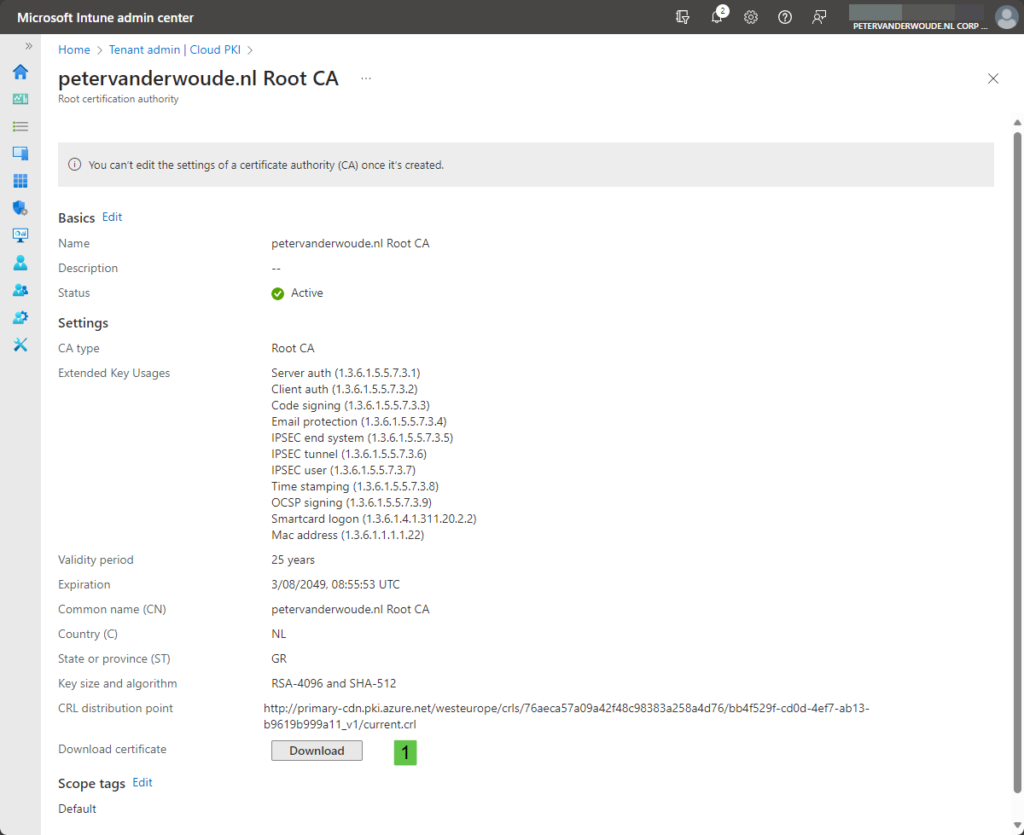
After creating the two-tier hierarchy, it’s time to distribute the public keys of the root CA and the issuing CA to make them trusted by the client devices. That can be achieved by downloading the related certificates and distributing those certificates to the client devices. Those certificates can be downloaded at the following places.
- Open the Microsoft Intune admin center portal and navigate to Tenant admin > Cloud PKI
- Select the root CA, as shown in Figure 5, navigate to Download certificate and click Download (1)
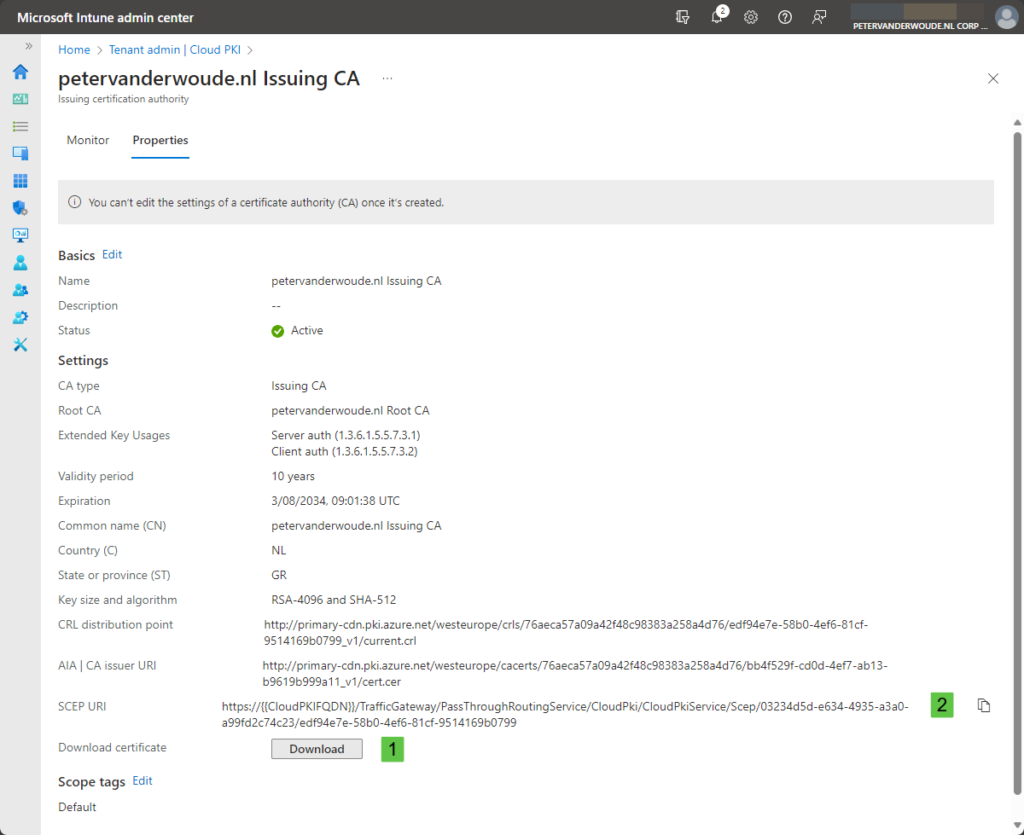
- Select the issuing CA, as shown in Figure 6, navigate to Properties > Download certificate and click Download (1)
After downloading those certificates, the process for making them trusted is pretty straight forward. That can be achieved by using a trusted certificate profile. That profile can be used to add those certificates to a specific store locally on the device. The following eight steps can be used to distribute those certificates to the Trusted Root Certification Authorities store.
- Open the Microsoft Intune admin center portal navigate to Devices > Configuration
- On the Devices | Configuration page, select, click Create > New policy
- On the Create a profile page, provide the following information and click Create
- Platform: Select Windows 10 and later as value
- Profile type: Select Templates as value
- Template name: Select Trusted certificate as value
- On the Basics page, provide a unique Name to distinguish it from other trusted certificate profiles and click Next
- On the Configuration settings page, provide the following information and click Next
- Certificate file: Select the just downloaded certificate file
- Destination store: Select Computer certificate store – Root for the selected certificate file
- On the Assignments page, configure the assignment and click Next
- On the Applicability rules page, configure the applicability rules and click Next
- On the Review + create page, verify the configuration and click Create
Note: These steps can be used for distributing the download certificates for the root CA and the issuing CA.
Delivering the client authentication certificate
When the different public keys are trusted, it’s time to actually distribute the client authentication certificate. That is the certificate that will be of an actual use for the user, as it can be used for authenticating on something like Wi-Fi, or VPN. However, before looking at the creation of a profile for that purpose, it’s important to first gather the last piece of information. That piece of information is the URL of the SCEP endpoint. That endpoint can be found at the following location.
- Open the Microsoft Intune admin center portal navigate to Tenant admin > Cloud PKI
- Select the issuing CA, as shown above in Figure 6, navigate to Properties > SCEP URI and click Copy
When the SCEP endpoint is available, it’s time to start distributing client authentication certificates to Intune managed devices. That can be achieved by using the SCEP certificate profile. That profile is used by the client to create a certificate request with the issuing CA, via the SCEP service. That request will be evaluated and eventually the SCEP service will provide the device with a signed certificate. The following eight steps walk through the process of creating that SCEP certificate profile.
- Open the Microsoft Intune admin center portal navigate to Devices > Configuration
- On the Devices | Configuration page, select, click Create > New policy
- On the Create a profile page, provide the following information and click Create
- Platform: Select Windows 10 and later as value
- Profile type: Select Templates as value
- Template name: Select SCEP certificate as value
- On the Basics page, provide a unique Name to distinguish it from other SCEP certificate profiles and click Next
- On the Configuration settings page, provide the following information and click Next
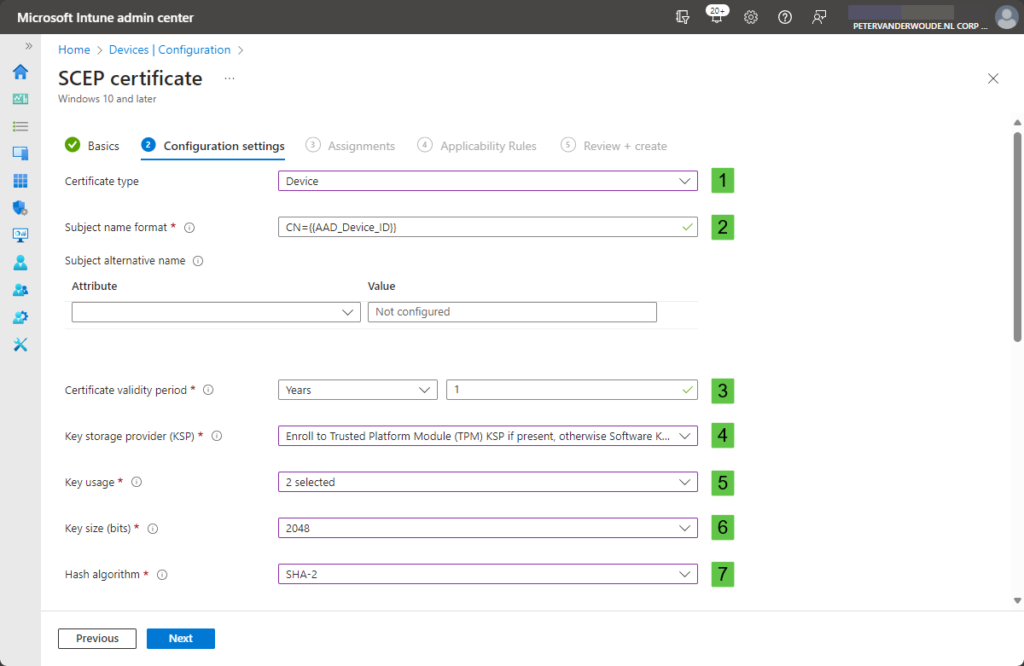
- Certificate type (1): Select the certificate type by choosing between User and Device
- Subject name format (2): Specify how to automatically create the subject name in the certificate request by specifying the required variable (as documented here) that corresponds to the use case
- Subject alternative name (-): If needed, specify an alternative name in the certificate request
- Certificate validity period (3): Specify how long the certificate will be valid
- Key storage provider (KSP) (4): Specify where the key to the certificate is stored by choosing between Enroll to Trusted Platform Module (TPM) KSP if present, otherwise Software KSP, Enroll to Trusted Platform Module (TPM) KSP, otherwise fail, Enroll to Windows Hello for Business, otherwise fail (Windows 10 and later), and Enroll to Software KSP
- Key usage (5): Select the key usage options for the certificate by choosing between Digital signature and Key encipherment
- Key size (bits) (6): Select the number of bits contained in the key by choosing between Not configured, 1024, 2048, and 4096
- Hash algorithm (7): Select the hash algorithm type for the certificate by choosing between SHA-1 and SHA-2
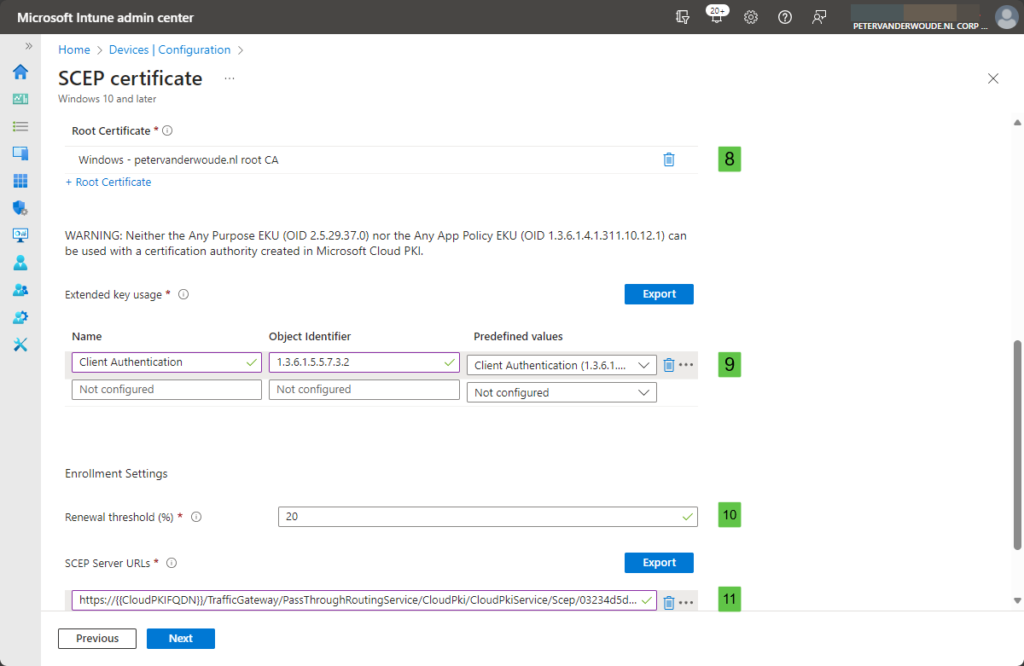
- Root certificate (8): Select the root CA certificate that the issuing CA is anchored to in the hierarchy
- Extended key usage (9): Specify the values for the intended purpose of the certificate
- Renewal threshold (10): Specify the percentage of the certificate lifetime that remains before renewal request
- SCEP Server URLs (11): Specify the SCEP URI that was copied at the beginning of the process
Note: Keep in mind that 4096-bit key storage is only supported in the Software Key Storage Provider.
- On the Assignments page, configure the assignment and click Next
- On the Applicability rules page, configure the applicability rules and click Next
- On the Review + create page, verify the configuration and click Create
Verifying the delivered certificates
When the configuration of the Cloud PKI is in place and the required certificate profiles are created, it’s time to verify the delivered certificates. There are actually multiple locations that provide a quick overview of the successful delivery of the client authentication certificate and the certification path. One location is locally on the device and the other location is in the Microsoft Intune admin center portal. Locally on the device, the Event Viewer provides an overview of the certificate request in the Microsoft-Windows-DeviceManagement-Enterprise-Diagnostics-Provider/Admin log. Especially Event ID 36, as shown below in Figure 9, provides interesting details about the success. Besides that, of course the client authentication certificate itself. That immediately indicates the success. Below in Figure 9 is also an brief overview of that distributed certificate including its certificate path.
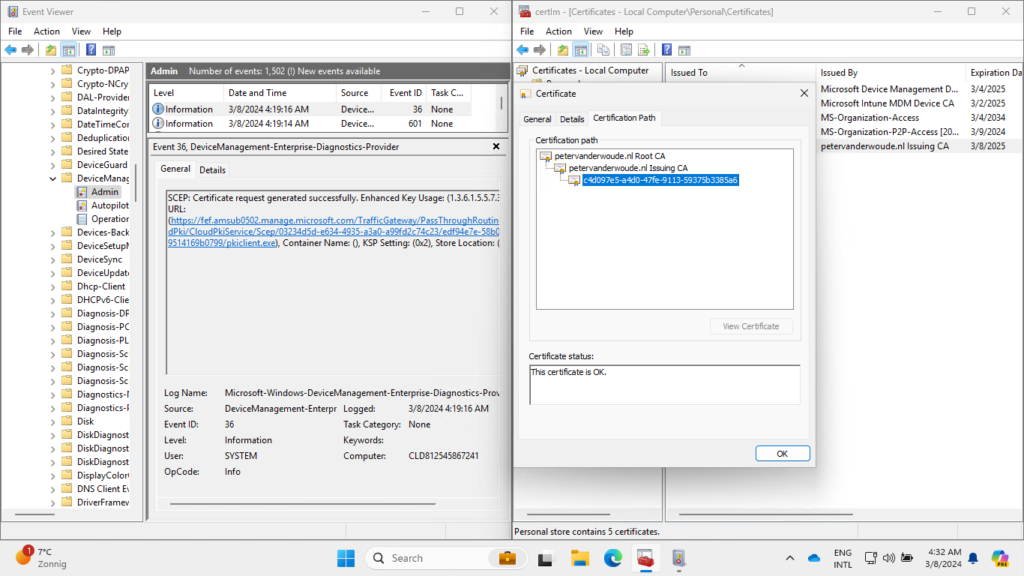
The other location also provides a pretty clear overview. Within the Microsoft Intune admin center portal there is an overview of the delivered client authentication certificates. That overview, as shown below in Figure 10, can be found by navigating to Tenant admin > Cloud PKI > [issuing CA] > View all certificates. Besides that, that location can also be used to Revoke certificates.
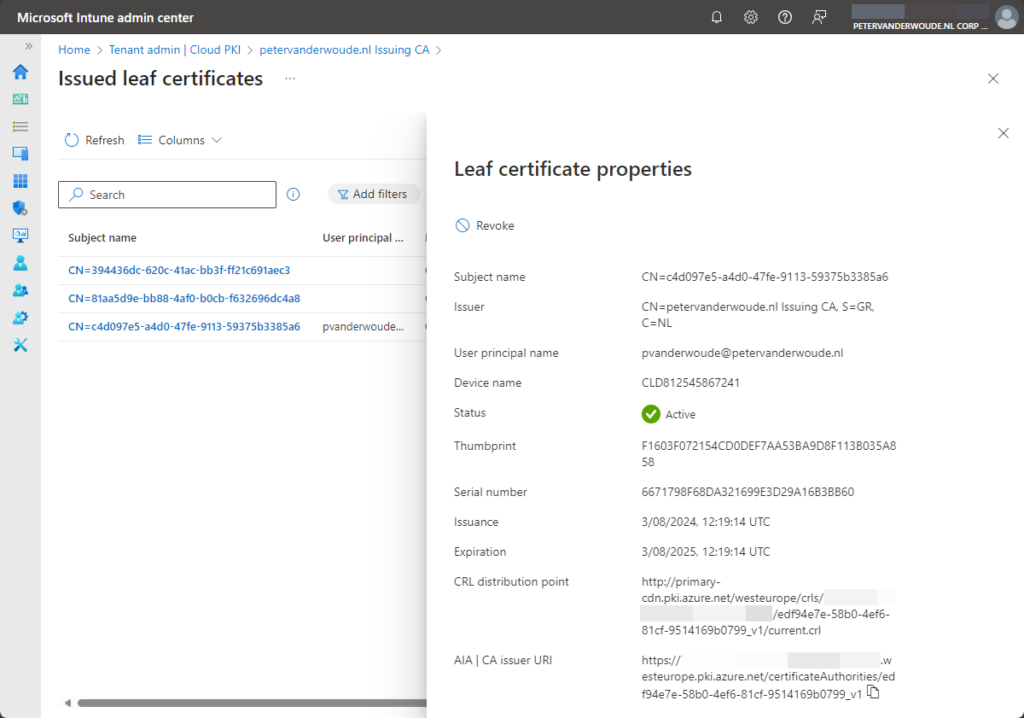
Now this certificate can basically be used for anything within the purpose of the certificate.
More information
For more information about the Intune Suite add-on capabilities and Microsoft Cloud PKI, refer to the following docs.
- Use Intune Suite add-on capabilities – Microsoft Intune | Microsoft Learn
- Microsoft Cloud PKI for Microsoft Intune – Microsoft Intune | Microsoft Learn
- Deployment models for Microsoft Intune cloud PKI – Microsoft Intune | Microsoft Learn
- Monitor issued PKI certificates with Microsoft Intune – Microsoft Intune | Microsoft Learn
- Audit logs for Microsoft Intune cloud PKI – Microsoft Intune | Microsoft Learn
This this work with Hybrid-Joined Intune Devices, or AAD Only? And, this wouldn’t work for on-prem servers since they aren’t able to be Intune Managed I suspect.
Hi Jamie,
Currently, Cloud PKI works only for Intune managed devices. It doesn’t matter if those devices are Entra joined or hybrid Entra joined.
Regards, Peter
Now you have my attention with hybrid Entra joined devices being supported. Another question, how does licensing work? I see that it’s $2.40 USD/license. Does each device need to be licensed? Meaning, if we have 100 devices, we’d be paying $240 monthly? Or, is it simply a license to manage the cloud PKI per “operator?”
Hi Jamie,
As far as I know, it’s a per user license, just like with regular Intune licenses.
Regards, Peter