This week is all about controlled folder access. Not something particular new, but something important to be familiar with. Controlled folder access is a great addition to further minimize the attack surface of Windows devices. It helps protect the data in the controlled folders from malicious apps and threats, by checking apps against a list of known, trusted apps. That makes it a perfect addition to further protect the (corporate) data on Windows devices. That also makes it mainly a local security feature. To get detailed reporting information, it can be used with Microsoft Defender for Endpoint. This post will mainly focus on the local configuration of controlled folder access and the user experience.
Introducing controlled folder access
Controlled folder access is a great method for further protecting data from malicious apps and threats. It works by only allowing trusted apps to access the folders that are protected with controlled folder access. Those folders are protected folders. Protected folders are specified within the controlled folder access configuration. That configuration can be done by using Microsoft Intune. By default, the public and user folders of Documents, Pictures, Videos, Music, and Favorites and the Windows system folders, are included in the list of protected folders.
Note: It’s not possible to remove the Windows system folders from the list of folders that are protected by default.
Besides that list of protected folders, there is also the list of trusted apps. That list is used to allow trusted apps access to the protected folders. And that list can also be configured within the controlled folder access configuration. By default, most apps will be allowed access to protected folders, without the need to specifically specify those apps, as apps are alowed based on their prevalence and reputation. Those apps will work as expected. Other non-listed apps will be prevented from making changes to files inside the protected folders.
Important: Scripting engines are not trusted and cannot be allowed access to protected folders.
To evaluate controlled folder access, use Microsoft Intune to enable audit mode. For a single device that can also be achieved by using PowerShell via Set-MpPreference -EnableControlledFolderAccess AuditMode.
Configuring controlled folder access
When looking at the configuration of controlled folder access, that can be achieved by using an Attack Surface Reduction Rules profile or by using a Settings Catalog profile. Within the first profile type it’s basically part of a template that contains all the different attack surface reducation options and within the second profile types it’s simply possible to create a custom collection of settings that only contains the required settings. The settings in those profiles for controlled folder access are ADMX-backed settings and are available via WindowsDefender.admx. The following eight steps walk through an example configuration that relies on the Attack Surface Reduction Rules profile.
- Open the Microsoft Endpoint Manager admin center portal navigate to Endpoint security > Attack surface reduction
- On the Endpoint security | Attack surface reduction blade, click Create Profile
- On the Create a profile page, provide the following information and click Create
- Platform: Select Windows 10 or later as value
- Profile: Select Attack Surface Reducation Rules as value
- On the Basics page, provide a unique Name to easy distinguish the profile and click Next
- On the Configuration settings page, configure at least the folllowing settings (as shown in Figure 1) and click Next
- Enable Controlled Folder Access: Select Enabled as value to enforce controlled folder access
- Controlled Folder Access Protected Folder: Specify additional folder locations to complement the system defined folders and when adding multiple folders use | as separator of the different values
- Controlled Folder Access Allowed Applications: Specify additional apps that are allowed to modify or delete files in the protected folders and when adding multiple apps use | as separator of the different values
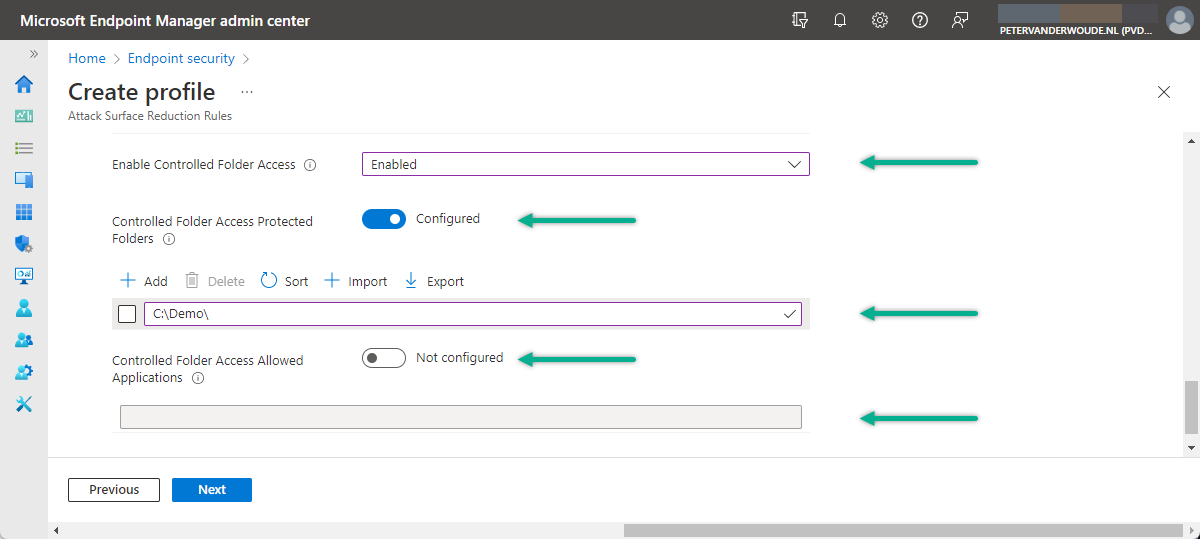
Note: This example adds the additional protected folder of C:\Demo that will be used for testing the functionality.
- On the Scope tags page, configure the applicable scopes for the profile and click Next
- On the Assignments page, configure the assignment for the profile and click Next
- On the Review + create page, verify the configuration and click Create
Important: Controlled folder access requires enabling Microsoft Defender Antivirus real-time.
User experience with controlled folder access
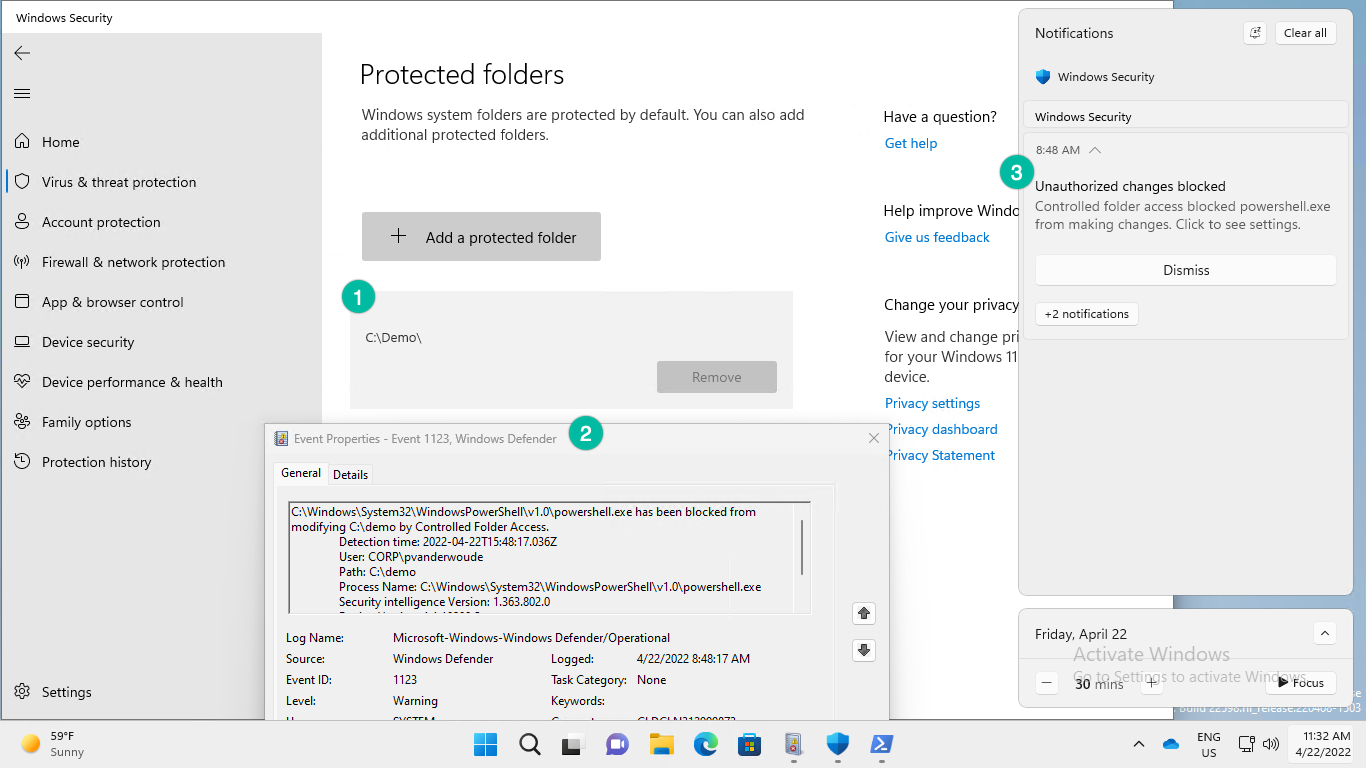
The best method to experience controlled folder access, is by using an example from the Microsoft Defender Testground. That example contains a fake ransomware file that will try to encrypt an specific folder. Make sure that the folder is a protected folder and the controlled folder access functionality will be triggered when the fake ransomware file is used. Fun part is that in this case controlled folder access was already triggered by running the PowerShell script that can be used to prepare the demo. That behavior is shown below in Figure 2, with the following points of attention.
- The Windows Security app provides an overview of the applied configuration. In this case it shows the additional added folder and also that it can’t be removed by the users.
- The Event Viewer message provides information about the blocked action. In this case it shows that PowerShell was blocked from modifying the additional folder by controlled folder access.
- The Notification message provides the user with a notification about the blocked action. In this case it shows the PowerShell was blocked from making changes.
More information
For more information about controlled folder access, refer to the following docs.
- Protect important folders from ransomware from encrypting your files with controlled folder access | Microsoft Docs
- Evaluate controlled folder access | Microsoft Docs
- Enable controlled folder access | Microsoft Docs
- Customize controlled folder access | Microsoft Docs
- Policy CSP – Defender – Windows Client Management | Microsoft Docs
- Home – Microsoft Defender Testground
How does controller folder access work with OneDrive folder Redirection enabled for Desktop, Docs and Pictures?
Hi Adam,
It protects the access to the specified folders.
Regards, Peter
Hey Peter
How to unblock PowerShell from Controlled Folder Access?
Hi Tayyab,
According to the note here, you can’t: https://learn.microsoft.com/en-us/microsoft-365/security/defender-endpoint/customize-controlled-folders?view=o365-worldwide#allow-signed-executable-files-to-access-protected-folders
Regards, Peter