This week is all around Shared iPad devices with Microsoft Intune. Shared iPad is an iPadOS configuration that easily lets multiple user share the same iPad. That configuration enables a personal experience for a user, on a device that is shared between multiple users. That personal experience enables users to be more productive, as users can simply pick-up where they left off previously. This post will start with a short introduction to Shared iPad devices, followed with the configuration steps for those devices. This post will end by describing and showing the user experience with Shared iPad devices.
Introduction to Shared iPad devices
With shared devices, this post is referring to company-owned multi-user devices that can be used – depending on the use case – as single-purpose or multi-purpose devices. Familiar use cases are frontline workers and students. When looking at iOS/iPadOS devices, there are actually two different methods for addressing shared multi-user devices. That is without considering kiosk mode.
- Shared iPad – Shared iPad functionality is provided by Apple with iPadOS 13.4 and later. This functionality enables multiple users to sign in to the same iPad by using a Managed Apple ID. Based on that Managed Apple ID, the user receives access to the different Apple apps, data and resources on the Shared iPad. Besides users with a Managed Apple ID, it’s also possible to provide temporary access for users without an account, by using a guest account. Shared iPad also provides builtin functionality to automatically clean up cached user accounts, depending on the available storage on the device. Microsoft Intune can enable the Shared iPad functionality, by integrating with Apple Business Manager (ABM), and adds on to that functionality by configuring policies and distributing additional apps.
- Shared Device Mode – Shared Device Mode functionality is provided by Microsoft for iOS/iPadOS 13 and later. This functionality enables multiple users to sign in to the same Apple device by using an Azure AD account. Based on that Azure AD account, the user will be automatically signed in to any supported app. Microsoft Intune can enable Shared Device Mode, by using the Microsoft Enterprise SSO plug-in, and adds on to that functionality by configuring policies and distributing additional apps.
Unless an organization needs cellphone capabilities, or needs to use iOS devices, Shared iPad is the recommended shared device solution for Microsoft 365 on iPadOS devices. Shared iPad is also the focus of this post and before looking at the configuration in more detail, it’s important to be aware of a few unsupported scenarios. According to the documentation, app-based and device-based conditional access, app protection policies and device compliance policies are currently not supported.
Note: During my initial testing, I could successfully use app-based conditional access policies and apply app protection policies in combination with Shared iPad devices.
Configuration of Shared iPad devices
The configuration of Shared iPad devices contains of a few important configurations that should be in place and that are described below as prerequisites. Besides that, the main configuration of Shared iPad devices consists of the configuration and assignment of an enrollment profile for iPadOS devices.
Requirements and prerequisites for configuring Shared iPad devices
The Shared iPad functionality has the following requirements on the iPad device.
- iPad Pro, iPad (5th generation or later), iPad Air 2 (or later), iPad mini (4th generation or later)
- iPadOS 13.4 or later as platform
- 32GB or more as storage
Note: Not enough storage space can be a reason why the configuration of the iPad will hang during the remote configuration, with the message of “Awaiting final configuration from company“.
The described configuration of Shared iPad devices assumes that the following configurations are in place.
- Federated authentication and user provisioning with Azure AD, to make sure that the IT administrator has the best experience for managing accounts and that the user has the best experience for initially signing in to the Shared iPad device
- Automated Device Enrollment with Apple Business Manager, to make sure that the Apple device can be turned in to a Shared iPad device
Configuration steps for Shared iPad devices
The actual configuration of Shared iPad devices is achieved by using an enrollment profile for corporate-owned iPadOS devices that synchronized via ABM. That enrollment profile will make sure that those iPadOS devices apply the correct enrollment configuration to bring those iPadOS devices in the correct mode. The following six steps walk through the steps to create an enrollment profile for Shared iPad devices.
- Open the Microsoft Endpoint Manager admin center portal and navigate Devices > iOS/iPadOS > iOS/iPadOS enrollment > Enrollment program tokens > {YourEnrollmentToken} > Profiles to open the {YourEnrollmentToken} | Profiles page
- On the {YourEnrollmentToken} | Profiles page, click Create profile > iOS/iPadOS to open the Create profile wizard
- On the Basics page, provide the following information and click Next
- Name: Provide a name for the profile to distinguish it from other similar profiles
- Description: (Optional) Provide a description for the profile to further differentiate profiles
- Platform: iOS/iPadOS is preconfigured based on the initial start of the wizard
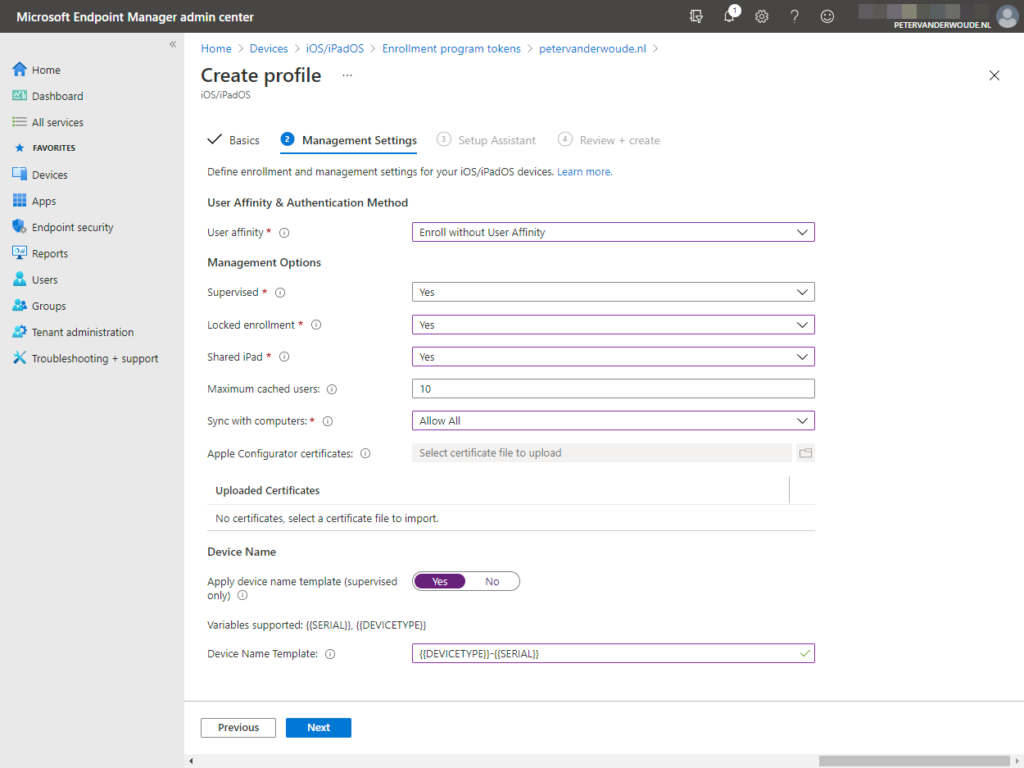
- On the Management Settings page (as shown in Figure 1), provide at least the following information and click Next
- User affinity: Select Enroll without User Affinity as value, as a Shared iPad can’t have user affinity
- Supervised: Select Yes as value, as a Shared iPad must be supervised
- Locked enrollment: Select Yes as value, to make sure that the enrollment is locked on the device
- Shared iPad: Select Yes, to enable the Shared iPad configuration
- Maximum cached users: Specify a number of users that should be cached on the device
Note: A maximum of 24 users can be cached on a device with 32GB, or 64GB. Make sure to match this number with the number of user of the device. A too low number can mean that users have to wait longer to be productive and a too high number can mean that the device is running out of space.
- Sync with computers: Choose between Allow All, Deny All and Allow Apple Configurator by certificate, to specify if the device is allowed to sync with computers
Note: When choosing Deny All, the port will be limited to charging only.
- Apple Configurator certificates: Specify a certificate when the requirement (and previous configuration) is to only allow Apple Configurator by certificate
Note: It’s important to have local copy of the certificate, as it’s not possible to make changes to the uploaded copy.
- Apply device name template (supervised devices only): Choose between Yes and No, to specify if the device should follow a specific naming standard
- Device Name Template: Specify a device name template when the requirement (and previous configuration) is to apply a device name template
Note: The variable {{SERIAL}} can be used as serial number in the device name and the variable {{DEVICETYPE}} can be used as the device type in the device name.
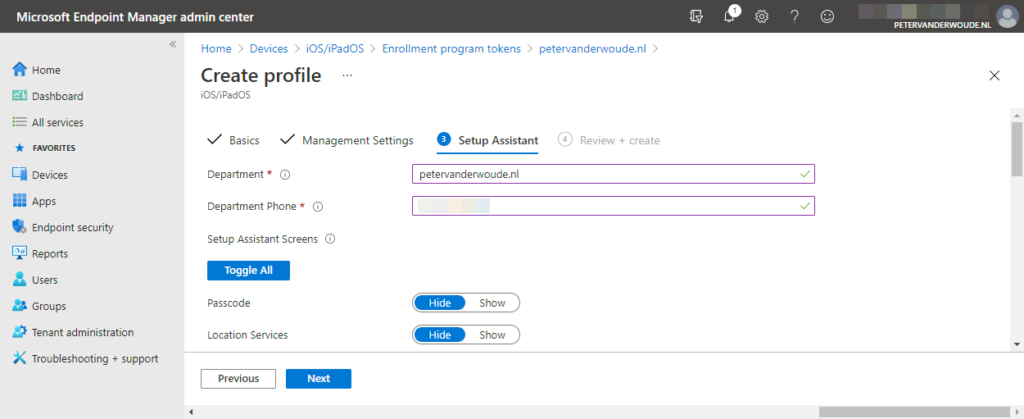
- On the Setup Assistant page (as shown in Figure 2), provide at least the following information and click Next
- Department: Specify the department name that should be displayed in the Setup Assistant during the setup of the Shared iPad
- Department Phone: Specify the department phone number that should be displayed in the Setup Assistant during the device setup of the Shared iPad
- Setup Assistant Screens: Specify the screens that should be displayed in the Setup Assistant during the device setup of the Shared iPad
- On the Review + create page, verify the configuration and click Create
Once the enrollment profile for Shared iPad devices is created, it can be assigned to devices that are synchronized via ABM. That assignment can be achieved by using one of the following methods.
- Default profile – Navigate to Devices > iOS/iPadOS > iOS/iPadOS enrollment > Enrollment program tokens > {YourEnrollmentToken} > Profiles and use Set default profile to configure the default profile that is automatically assigned to all synchronized iOS/iPadOS devices for that specific enrollment token.
- Assign profile – Navigate to Devices > iOS/iPadOS > iOS/iPadOS enrollment > Enrollment program tokens > {YourEnrollmentToken} > Devices and use Assign profile to manually configure the profile that is assigned to the specifically selected iOS/iPadOS devices that are synchronized for that specific enrollment token
Configuration suggestions for Shared iPad devices
Once an iPad is configured as a Shared iPad, it’s possible to do additional configuration and to distribute apps. Below are a few suggestions to use and to keep in mind for further configuring Shared iPad devices.
- Assign apps and policies to device groups, as user assigned apps and policies will not apply on Shared iPad devices.
- Assign apps as required to device groups, as available apps (and the Company Portal app and website) are not supported on Shared iPad devices.
- Only Apple VPP apps, line-of-business apps and weblinks can be distributed to Shared iPad devices, as the App Store can not be used.
- Disable the App Store via a device configuration profile (setting: Block App store), as the App Store is available on Shared iPad devices but the app installations are disabled.
- Block guest sign in via a device configuration profile (setting: Block Shared iPad temporary sessions), to prevent temporary sessions and public access to the Shared iPad devices
User experience with Shared iPad devices
Once all the required configurations are in place and the enrollment profile is assigned to an iPad, it’s time to have a look at the user experience. The enrollment is actually really simple and leaves little room for error. The IT administrator (or an user) turns on the iPad, selects the language and the location of the iPad, and connects the iPad to the Wi-Fi. The iPad will activate and will find the remote management configuration after connecting to ABM. That will trigger the Shared iPad configuration. The iPad will restart and the configuration of the iPad will start. Once the configuration is completed, the Shared iPad sign-in screen shown.
Now the user can sign in with a Managed Apple ID and the profile will be created and cached locally on the Shared iPad. When it’s the first time of the user with a Shared iPad, the user should configure a language and location. Also, and this is were Shared iPad is a bit tricky from a user perspective, when it’s the first time using a Shared iPad, the user should configure an iPad passcode. All of these configurations are not iPad specific, but Shared iPad specific. The user can now sign in with a Managed Apple ID and the iPad passcode, on any Shared iPad device. That means that from this point, the user has a separate passcode for Shared iPad devices.
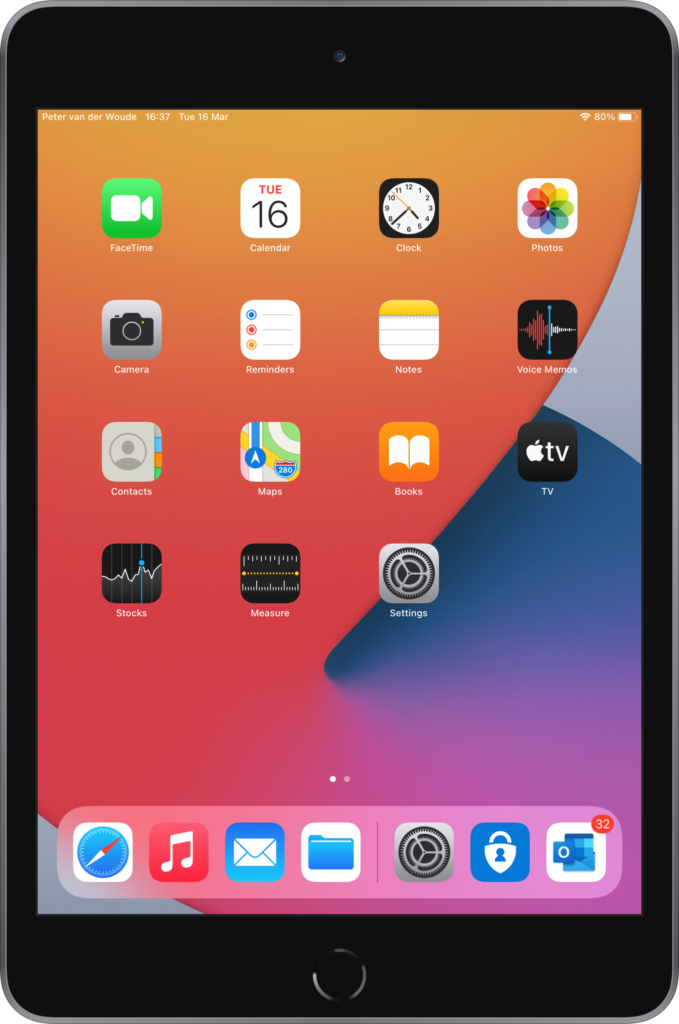
Once the user is signed in to a Shared iPad, the name of the user will be visible in the top left corner of every screen (as shown below in Figure 3 and Figure 4). To sign-out of the device, the user can swipe down to get a Sign Out button in the bottom right corner of the screen (as shown below in Figure 4). When the user is signed out, the device will show Recent Users (middle) and Other User (bottom left corner) as options to sign in to the device again. And when guest access is allowed, this screen will also show Guest (bottom right corner) as option to sign in.
When working with Shared iPad devices, there are also a few practical things to keep in mind.
- Only a limited number of settings and system apps are available on Shared iPad devices.
- The passcode complexity for Shared iPad devices is complex 8 character alphanumeric.
- ABM should be used to reset the passcode of a user for a Shared iPad device.
- The cached user data is removed after a passcode reset of that user for a Shared iPad device.
More information
For more information about Shared iPad devices and Microsoft Intune, refer to the following docs.

Thanks for this Peter, I’ve been struggeling a while now to configure a bunch of shared iPads. This guide helped me setting up our devices for this particular use.
Also one additional comment: MS states that wallpaper is not supported on shared iPad. I tried it with a device feature policy and it worked in my case. Did you try this?
Hi Jonas,
The thing is mainly that the behavior can be unexpected (see also: https://docs.microsoft.com/en-us/mem/intune/configuration/ios-device-features-settings#wallpaper).
Regards, Peter
Hello Peter,
any luck to set an VPN client on such device authentication via device certificate? (Pulse Secure)
Thanks for the article
Cheers
Jan
Hi Jan,
I haven’t tried that configuration yet. From the Microsoft docs, it appears that it should be possible. The Apple docs, however, make it a bit confusing: https://support.apple.com/en-gb/guide/mdm/mdm9992c9a34/web
Regards, Peter
Sadly, you were right. It is not possible as the VPN setting or the application do not have access to the certificates stored on shared iPad. Even thought they are present and may be used for wifi setting. Another bumper is that Shared iPAD is not supporting any kind of data connection via SIM card. 🙁
Maybe this will save some time for the others. 😀
Cheers
Jan
Thank you for the information Jan!
Hi Peter, this was very helpful! Do you have any recommendations about how (or to you know whether it’s even possible) to remove preinstalled apps such as TV or Podcasts? Thanks!
Hi Tamara,
You could have a look at the option to show or hide apps in a device restrictions policy: https://docs.microsoft.com/en-us/mem/intune/configuration/device-restrictions-ios#show-or-hide-apps
Regards, Peter
Hi Peter,
Great post.
Did you also tested a cellular data connection?
We recognized that no LTE Mobile Data Connection is possible (only edge which is almost equal as no internet).
It seems only possible while setting the device up but after a while no LTE Connection can be established anymore
which would make the ipad almost not usable when no Wifi is available.
thanks
Regards
Stefan
Hi Stefan,
Based on the docs, I would say that it’s expected behavior: https://support.apple.com/en-gb/guide/deployment/depc3485c493/1/web/1.0
Regards, Peter
Why is it expected behaviour?
Fair question. Reading that link better, the settings are only disabled and not the services. So, theoretically you might be able to get a signal, you just can’t configure it.
Regards, Peter
My company is looking to procure 6 new iPad Air cellular models, are you saying that LTE or 5g won’t work with shared IPAD profile
You won’t be able to make configuration changes.
Regards, Peter
Can we save data in icloud in shared ipad
Hi shaheen,
At least for managed Apple IDs you should be able to use iCloud.
Regards, Peter
Hi Peter,
Is it possible to wipe shared ipad device as in settings there is no option for erasing shared ipad can we able to wipe shared ipad from intune.Please suggest possible options.
Hi Shaheen,
You can use the remote actions in Microsoft Intune to send a Wipe action.
Regards, Peter
I am having problems setting 6 or 4-digit passcode on the shared iPads. They are enrolled through ABM, and I log on with federated users. I still have to use the full password tied to the Managed Apple ID user.
How can I change this so that the iPad accepts a passcode?
Hi Kjetil,
Are they enrolled as Shared iPads? If so, the initial sign-in will automatically require the user to set a passcode.
Regards, Peter
I have setup Shared iPads as Guest only login and have hidden all applications except a few which includes teams. User identities are not federated with ABM. When users login to teams they get sign was successful but does not meet the criteria message because of the conditional access policy.
The users can access teams and join meetings only as a guest and with the meeting I’d but, We want to allow user to sign in with their credentials to Teams. What is the best possible solution?
Hi Ajay,
What are you requiring from the device/app via CA?
Regards, Peter
Hello Peter,
Thank you for the response. Today we have a block access CA with exclusion of filtered devices = compliant (iPhones and Androids). I have read through the MS documentation, and it states though the device is compliant it is actually not. It also states conditional access policy is not supported fro Shared iPads. I guess I am asking how to exclude the Shared iPad from the condition access policy that is blocking Teams login. I have used device filters: exclude enrollmentprofilename = “the profile name” but it doesn’t work.
Hi Ajay,
I’m afraid that there is no magic switch yet to exclude those device. You have to find something that makes them unique within your environment.
Regards, Peter
Thank you for getting back. I will explore options to mark the device as unique so that I can include those in the CA
Hi Peter,
thanks for the great content!
Do you have any experience with SSO?
When user signs in to Shared iPad and opens any Microsoft application (Teams) it asks for username + password.
Would be great to use sign-in information for this.
Thanks,
Christian
That SSO experience is probably better when using the Azure AD Shared Device Mode (but that has it’s own challenges).
Regards, Peter
Hi Peter,
Great writeup. What is the best way to remove a user from a Shared iPad? In Intune we do not see a Users section listed under the device details as the documentation describes.
Hi Rogér,
Not sure you have an option like that. Eventually, unused accounts will be removed automatically.
Regards, Peter
Hello Peter,
I am trying to create a shared ipad for 2 users that i have synced. A teacher account and a student account. I wanted to display a set of app for the teacher and a set for the students. I have all apps assigned to the device as required.
I created a device features config profile to set a homescreen layout for the student, assigned to the student group, but it doesn’t seem to be picked up. I also tried show/hide in device restrictions. Doesn’t seem to apply either.
Basically i want that when a student logs in it only shows the apps that are pushed to the device. No built-in apps or as little as possible.
And a teacher should have some additional apps.
Hi Jorin,
Keep in mind that user-assigned policies require federated Azure AD accounts, as mentioned here: https://learn.microsoft.com/en-us/mem/intune/enrollment/device-enrollment-shared-ipad?WT.mc_id=EM-MVP-5001447#configure-settings-for-shared-ipads
Regards, Peter
Yes I know, I am using azureAD accounts that are synced with asm
Hi Jorin,
Just to fully understand your response: are those accounts only synced or also federated (as in: initial authentication via Azure AD)?
Regards, Peter
Hi Peter,
I have just setup 25 iPad 64Gb 9gen, as Shared iPads. Everything works perfectly, I only have one serious problem. When I look in Setting, Gerneral, About, the capacity states 12GB, leaving very little room for apps. Have you any idea what is wrong ?
Many thanks 😉 Peter
Hi Peter,
Shared iPads have a standard data allocation, as described here: https://support.apple.com/en-gb/guide/deployment/dep6fa9dd532/web
Regards, Peter
If you are using this for a pure ‘guest’ mode is a passcode enforced and when during the setup process? Intune doc mentions the 8 digit complex passcode is enforced but is that still the case if using ONLY for guest mode? Thanks
Hi Jimmy,
No. That will use a temporary session that also doesn’t require a passcode for unlocking. So it’s important for users to be careful when signing into different web apps.
Regards, Peter
Great Thanks!
Hi Peter,
Thanks for a great article. Can you tell me why Intune policies are not supported with Shared iPad: app-based and device-based conditional access policies, app protection policies, and compliance policies. Is it because they are devices without user affinity? Though Microsoft says its not supported, policies still apply. So is it recommended to use them?
Hi Lalitha,
The main question will be if the behavior is consistent and that might be the challenge.
Regards, Peter
Hi Peter,
We have created app protection policy for unmanaged devices (MAM) and deployed to all users group, we have couple of shared iPad devices that we have enrolled to Intune but we observed that unmanaged devices app protection policy also getting applied to these shared iPad device when user sign in to device. We had not expected this as Microsoft itself says app protection policy not supported on Shared iPad but in real word its the reverse case. Do you know how we can prevent the policy to get applied ?
Regards,
Suraj Malusare
Hi Suraj,
Sadly not supported is not the same as not applied. What you could do is making sure that those apps are considered managed apps on managed devices. In that case, that policy is not applicable.
Regards, Peter
Hi Peter,
Could you elaborate on ‘making sure that those apps are considered managed apps on managed devices’?
I’m running into the same issues as Suraj with MAM policies in my setups. The policies are applied and enforced by CA policies.
What happens is that a Shared iPad device isn’t recognized as a managed device when evaluating CA policies and MAM filters so they can’t exclude them. Currently we’re telling users to run through the securing of apps, but I’m looking into a solution where I can exempt Shared Ipads from such policies aimed at personal devices.
Last month I created a (premium) support ticket at MS but after a long process of making clear what Shared iPads exactly are we were told that they’d be making it available with the new (application) filtering option which didn’t change anything about this. I’m creating a new ticket as of now, but it would be great to hear your insights on this.
Thank you!
Best regards,
Thomas
Hi Thomas,
From a app protection perspective on iOS a device is considered unmanaged by default, unless a specific configuration is done. See also: https://www.petervanderwoude.nl/post/app-protection-policies-and-managed-ios-devices/
Regards, Peter
I have just configured 20 ipads and wax painful as bought from amazon.
I used apple configurator on vm to test and creates a profile just with wifi as thought intune would handle the rest.
In the end due to pull make profile on itune to pull and download intune company app
Working but user signs in with microsoft account then asks for password to be changed ( apple) I changed security measure in apple school manger to 4 digits as young age school.
Works but annoying that can’t just use Microsoft passeord as in shared user environment
I will be enrolling imacs next week any thoughts about this with azure ad and intune ?
Hi Steve,
Sadly, that’s the Shared iPad concept. That requires the separate PIN that must be created.
Regarding the MacOS devices; if it’s also about the authentication of the user, that might be challenging and sounds like platform SSO could be interesting: https://techcommunity.microsoft.com/t5/microsoft-entra-azure-ad-blog/coming-soon-platform-sso-for-macos/ba-p/3902280
Regards, Peter
Thanks a lot for this wonderful article. In shared iPad : For the Guest login “No password security available and it’s an users risk”. But for the Azure user login “Local device passcode setup is possible ?, we are not getting an prompt for the password setup while logging with managed Apple id”.
Hi Govi,
When using Shared iPad configuration for the iPad, and Entra for the account, the user has a managed Apple ID and will automatically be prompted to create a PIN. That is default Shared iPad behavior, created by Apple.
Regards, Peter
Also your suggestion is “Shared iPad is recommended for Multiple Users login in iOS device with M365 Apps ? and Shared Device Mode is not recommended due to limitation of SSO enabled M365 Apps ?. and Shared device mode doesnt required a login in an iPad device ?.
Hi Govi,
Shared Device Mode is a different concept that is created by Microsoft. It completely depends on your scenario if it makes sense. For the full experience. the user should eventually sign in with username-password (or whatever is configured).
Regards, Peter