This week is all about federated authentication for Managed Apple IDs. When using Microsoft Intune for managing Apple devices, the use of Managed Apple IDs is adding more and more value to the solution. That value gets even more when those Managed Apple IDs are federated with Azure AD. That would provide the user with a single account to remember and to use. Together that brings a very nice experience to Apple devices that are using federated Managed Apple IDs and are managed with Microsoft Intune. In this post I’ll discuss and describe the following information regarding Managed Apple IDs:
- What are Managed Apple IDs and why using them?
- Federated authentication for Managed Apple IDs
- Automatically provisioned users from Azure AD
- Provisioned user with federated authentication in Apple Business Manager
What are Managed Apple IDs and why using them?
Managed Apple IDs are the business versions of personal Apple IDs and are the solution to prevent the use of personal Apple IDs for work. Managed Apple IDs are also unique to an organization and are owned and managed by that organization. That also means that that organization is responsible for everything around managing that account and its password. Apple Business Manager (ABM) can be used for managing everything around Managed Apple IDs.
Within Microsoft Intune, Managed Apple IDs are required for shared iPad devices and for user enrollment. In the first scenario a Managed Apple ID is used to actually sign in to the device, and in the second scenario a Managed Apple ID is used to differentiate between personal and work data and apps. The latter experience is similar to what might be known from a Work Profile on an Android device. The integration is just a bit prettier for the user, but more about that is for another post.
Besides the Microsoft Intune specific scenarios, in which Managed Apple IDs are required, Managed Apple IDs can also be used to sign in to devices and to access Apple services. That experience is similar to the use of personal Apple IDs. However, there is a big difference. The available services and features are limited to what is useful for businesses. That means that signing in to iCloud (including 5GB of storage) and collaborating in iWork and Notes is available, but other features like Apple Pay, Find My and Apple Homekit are not available. For a complete list of available features refer to the Apple docs.
Federated authentication for Managed Apple IDs
Managed Apple IDs can be created and associated with basically any email address. That includes the personal Apple ID of users. However, it might be a lot easier to create Managed Apple IDs based on the work email address, or, even better, automatically create them. To achieve that, organizations can use a federation with Azure AD for Managed Apple IDs, and automatically provision those Manage Apple IDs from Azure AD.
The first step in that process is to create the federation with Azure AD. That will enable users to also use their Azure AD work account for business purposes on their Apple devices. A single account for all business purposes in the Microsoft world and the Apple world. A very pleasant experience. To create that experience, an organization should to link their Apple Business Manager to their Azure AD tenant. That link will make Azure AD the identity provider that authenticates the users for Apple Business Manager.
Important: Apple Business Manager can only be linked to a single Azure AD tenant.
The following 11 steps walk through the different stages of configuring Azure AD as the identity provider for the Managed Apple IDs. During the configuration an Enterprise application – with the name Apple Business Manager – will be created in Azure AD. Keep that in mind for any Conditional Access policies.
- Open Apple Business Manager and navigate to Settings > Accounts
Note: The account that is used should have the role of Administrator or People Manager.
- In the Domains section, click Edit > Add Domain, add the required domain and click Continue (and the result is shown below in Figure 1)
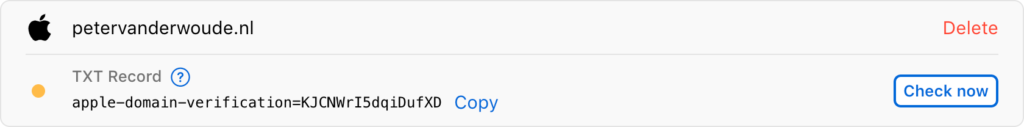
- Back in the Domains section, click Verify next to the added domain, copy the information for the TXT record and create a TXT record in the public DNS (and the result is shown below in Figure 2)
- Back in the Domains section, after the TXT record has been added, click Check Now next to the added domain (and the result is shown below in Figure 3)
- In the Federated Authentication section, click Edit > Connect
- On the Connect to your Identity Provider dialog box, click Sign in to Microsoft Azure Active Directory Portal… and sign in with an account of the Azure AD tenant
Note: The account that is used should have the role of Global administrator, Application administrator, or Cloud application administrator.
- On the Permissions requested dialog box, verify the information about the Apple Business Manager app and the requested permissions and click Accept
- Back on the Connect to your Identity Provider dialog box, click Done (and the result is shown below in Figure 4)
Note: Once the federation is configured, the configuration cannot be undone via Apple Business Manager and requires contact with Apple.
- Back in the Domains section, click Verify next to the added domain
- On the Federated Domain dialog box, click Sign in to Microsoft Azure Active Directory Portal… and sign in with an account of the Azure AD tenant
Note: The account that is used should have the role of Global administrator, Application administrator, or Cloud application administrator and should have a UPN of the verified domain.
- Back on the Federated Domain dialog box, click Done (and the result is shown below in Figure 5)
Important: When automatically provisioning of the Managed Apple IDs should also be configured, do not yet enabled the federation.
Note: Once the federation is tested, Apple will verify that no existing Apple IDs are using the verified domain name.
Automatically provisioned users from Azure AD
After creating the federation with Azure AD, the second step is to automatically provision the user in Apple Business Manager. That enables an organization to have a single place to maintain the identity of the users. Users created in Azure AD (or AD) are automatically created in Apple Business Manager, after the next synchronization. The same is applicable for disabling and removing accounts in Azure AD. After the next synchronization, the Managed Apple IDs will be updated in Apple Business Manager.
Note: When an account is disabled or removed in Azure AD, it will be deactivated in Apple Business Manager and it will be removed after 30 days.
There are also alternatives to automatically provisioning users from Azure AD. An alternative is manually creating Managed Apple IDs and another alternative is letting Apple Business Manager automatically create Managed Apple IDs once their used for the first tine. However, in both cases there is administrative effort required for managing those Managed Apple IDs in Apple Business Manager. If possible, use automatic provisioning of users from Azure AD.
To facilitate the automatic provisioning of users from Azure AD in Apple Business Manager, Azure AD and Apple Business Manager can rely on System for Cross-Domain Identity Management (SCIM). SCIM is an open standard for automating the exchange of user identity information between identity domains and IT systems. That standard is focused on exchanging user and group information. However, Apple Business Manager doesn’t know the concept of groups and is only focused on user information. The following number of steps walk through the different stages of configuring a SCIM synchronization between Azure AD and Apple Business Manager.
- Open Apple Business Manager and navigate to Settings > Data Source
- In the SCIM section, click Connect, copy the Token and click Close
- Open the Azure portal and navigate to Azure Active Directory > Enterprise applications > Apple Business Manager
Note: The Apple Business Manager app is created during the configuration of de federation.
- Select the Provisioning tab, click Get started and set Provisioning Mode to Automatic
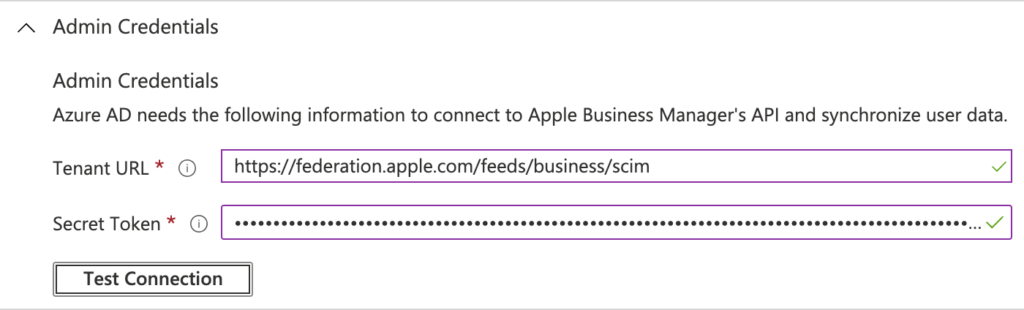
- In the Admin Credentials section, specify the following information (as shown below in Figure 6) and click Test Connection
- Tenant URL: Specify https://federation.apple.com/feeds/business/scim as value
- Secret Token: Specify the earlier copied Token as value
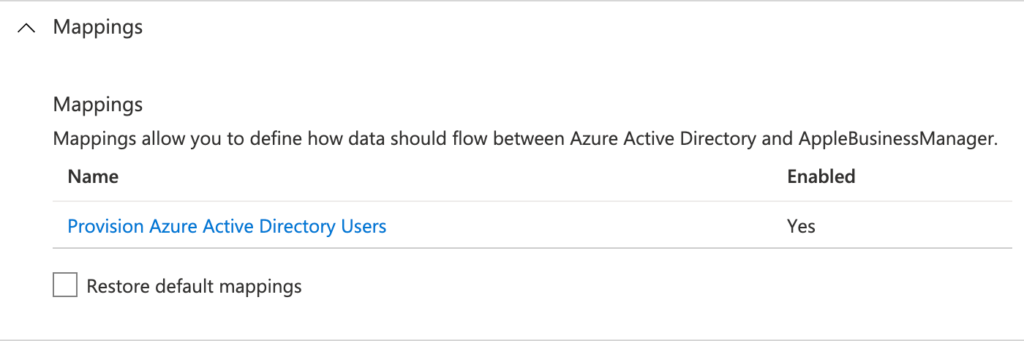
- In the Mappings section, specify any additional (or adjust any default) Azure AD attributes that should be mapped with Apple Business Manager attributes (as shown below in Figure 7)
Important: Only use the Apple Business Manager attributes as documented here, or the SCIM synchronization will break.
Note: By default the following Azure AD attributes are mapped to Apple Business Manager attributes – with the target object actions of Create, Update and Delete – userPrincipalName, Not([IsSoftDeleted]), givenName, surname, objectId, department and employeeId.
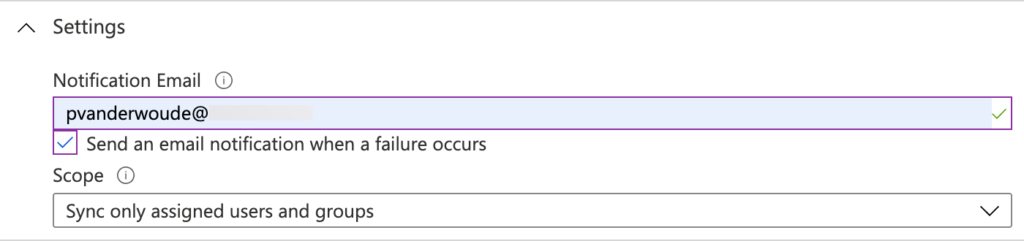
- In the Settings section, specify the following information (as shown below in Figure 8) and click Save
- Notification Email: Specify the email address of an administrator that should be notified for synchronization failures (when Send an email notification when a failure occurs is also checken)
- Scope: Select Sync only assigned users and groups as value
Note: This configured scope will make sure that the provisioning can be scoped to specific users accounts.
- Select the Users and groups tab and click Add user/group to specify the users that should be part of the automatic provisioning in to Apple Business Manager
Note: This assignment doesn’t allow an administrator to configure a default assigned role yet. Every synchronized user account will created in Apple Business Manager with the role Staff.
- Back in Apple Business Manager, navigate to Settings > Accounts
- In the Domains section, click Edit and move the slider to enable federation with the added domain (and the result is shown below in Figure 9)
Note: After enabling the federation, the user accounts will start coming to Apple Business Manager.
Provisioned user with federated authentication in Apple Business Manager
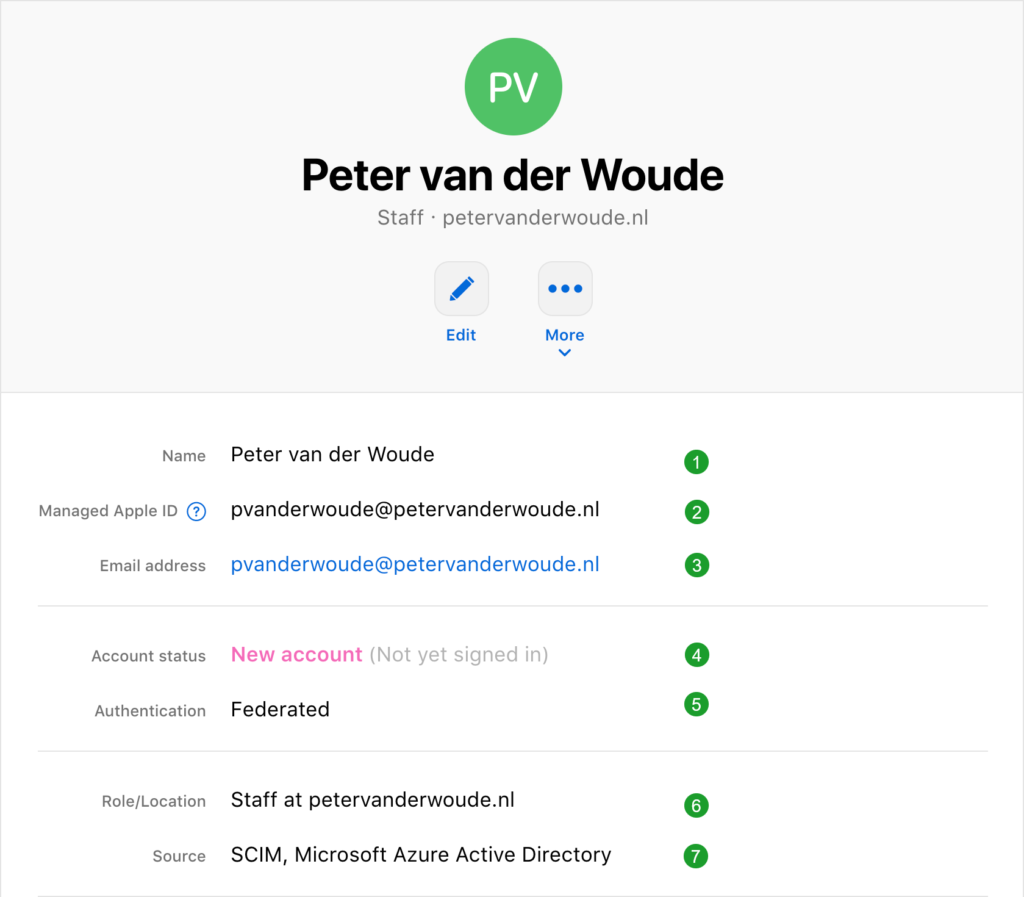
There are many places to look for a successful configuration of the SCIM synchronization and the federation of Managed Apple IDs. The Provisioning tab, of the Apple Business Manager app in Azure AD, provides a nice status overview and the provisioning interval (by default every 40 minutes), and the Provisioning logs tab, of the Apple Business Manager app in Azure AD, provides a nice overview of the actions that are performed during the synchronization. However, a successfully synchronized user is the best example. Below, in Figure 10, is an example of a synchronized user account with a snippet and short description of the most important information of that user account.
- Name: Based on the givenName attribute is Azure AD
- Managed Apple ID: Based on the userPrincipleName attribute in Azure AD
- Email address: Also based on the userPrincipleName attribute in Azure AD
Note: As both, the Managed Apple ID and the email address, are based on the UPN in Azure AD, it’s important that the email address and the UPN are the same.
- Account status: Based on the status and the usage of the user account and will change when the user account is used to log in, or when the user account is disabled or removed in Azure AD
- Authentication: Based on the identity provider of the user account and is set to Federated for synchronized and federated user accounts
- Role/location: Set to a default value and can be edited in Apple Business Manager
- Source: Based on how the user account was created
More information
For more information about the federated authentication and Managed Apple IDs, refer to the following docs.





Hi Peter,
awesome article as always !
I’ve been thinking to take ownership of our domain in ABM for some time now but the team that is responsible of deploying phones in our organization created apple IDs for our users for years now.
Some users have been using personnaly these “corporate” apple IDs and bought applications over the year and my understanding is that all of their purchases will not be theirs anymore once we take the domain’s ownership.
That being said, the technical aspect of this feature is not really complicated to configure as compare to some possible impacts of taking the domain’s ownership.
Hi Jonathan,
I haven’t specifically tested that, but, to my knowledge, taking ownership of the domain doesn’t do anything thing yet to those accounts.
Regards, Peter
I have had an open ticket with Apple for 4 weeks now. We have a problem with third-party Microsoft federated domains. We use a third-party single sign-on for M365 and it does not work with iOS. It was working prior to iOS 14. Do you have any insight?
Sorry George, I haven’t had to deal with that scenario yet. Only with MFA an the Setup Assistant, which can be worked around by using the Company Portal app.
Regards, Peter
How does this work with Shared iPads with generic accounts? Is there a way to bypass mfa without being prompted?
Hi John,
What do you mean? Are you seeing issues with federated accounts when MFA is enabled (with or without CA)?
Regards, Peter
Great article Peter. What happens when a user already has created an Apple ID on his business mail address ? When adding domain Apple does a check but what happens or can we do/choose (in Docs i read the account is “transfered” as managed Apple ID but what impact does this have? Thanks!
Have a look at the reply of Joey, Rkast. That should get you started.
Regards, Peter
Hi Jonathan,
I recently did a migration within a company with over 1000 Apple ID’s that used their company mail for their Apple ID account. Here’s what happens: if you claim the ownership of the domain the users have 60 days to change their Apple ID mailadres at appleid.apple.com. After these 60 days their Apple ID will change automatically from frist.lastname@company.com to first.lastname@company.appleid.com the password keeps the same. This wont happen if the user changed their Apple ID. Also if you start claim the domain the users receive push notifications and mails from Apple that they need to change their Apple ID.
This means that the accounts will not be removed. They only will be renamed. All the purchases will be kept in the account.
Thank you for sharing your experience Joey!
Thanks for sharing!
Will the same happen if the users already have a manually created Managed Apple ID with the company mail? Or will there be kind of a merge ?
regards,
Kudi
Great article. In my experience even though SCIM is setup it’s not always clear when the users will be synchronized (even though membership in AAD is established for a user and the SCIM connection is green and tested (both in AAD and in ABM). Even when there is no conflict. I’m not sure if Apple have any other timer except the SCIM-sync one which clocks at every 40 min as per default?
Another experience I’ve encountered is that even if a user’s primary email on it’s apple ID is a private one, if there is another mailconnection added (later sometime) to the domain which you want to obtain ownership against, Apple will count that as a conflict until that connection is gone or if 60 days pass and as Joey stated, the domain-name will change to @company.appleid.com
Hi Twilight Imperium,
The default synchronization interval is once every 40 minutes and it seems to be doing okay in my environment. Do keep in mind however, that the provisioning connector in Azure AD is still preview functionality (according to the UI).
Regards, Peter
Hey,
We are using federated managed apple IDs but the iPhones are popping up asking for the apple account to be re-verified. This is happening at least once every 24 hours? Has anyone else had a similar issue?
I haven’t noticed that behavior yet Jack. I’ll pay some attention to it.
Regards, Peter
I’m having the same issue, but it’s 1 hour for us. This seems to be tied to a session token expiring.
When signing into a federated account, it uses a Microsoft login page. This works as it should, it authenticates with the user’s password from Azure AD. The issue that I’ve run into is the session token for this expires after 1 hour. So after an hour, the phone starts asking for an Apple ID login. Is there any way to stop this? The only thing I’ve found is Conditional Access policies, but this requires a premium license. This also only allows expanding it out to 90 days.
Checking “Stay signed-in” doesn’t seem to work. The login details in Azure show that the box wasn’t checked. It also shows this as being a Safari agent, so it’s like a browser not saving cookies (loosely). Even if it did work, I don’t think this is a permanent solution. I think this persistent browser token expires after 30 days.
Any help with this would be greatly appreciated. I really don’t want to have to manually manage ABM accounts.
Hi Eric,
Are you also using Microsoft Intune and/or the Microsoft Authenticator?
Regards, Peter
Great article. We have setup federation with Azure and working as expected. All our devices are managed, pushed to intune, and ready to enroll by users. With testing policies, we are now prompting the user for Apple IDs. When I put my corporate email address, apple knows it is federated and the M365 login is triggered. All working well. Now, how, if possible, Can we prevent the phone (as it is managed) from accepting other AppleIDs (Personals). I have tried different scenarios with no success. Can this be accomplished with Enrollment types?
thanks
Hi MMog,
The enrollment types are focused on personal devices. That means that the main strength is in the combination of a personal and managed Apple ID.
Regards, Peter
What about the possibility of allowing the use only managed appleIDs on managed devices?
Not sure if that’s completely possible, but I haven’t checked the Apple Configurator. You can at least make it nearly impossible with a combination of not showing the screens during ADE and removing access via a configuration policy.
Regards, Peter
What do you mean by managed devices. Are those devices managed via Apple DEP/Apple Business Manager. You can use Managed Apple ID’s for the User Enrollment method with managed for business apps only. But this option is not available when you use an iPhone managed via Apple DEP/Apple Business Manager but only for BYOD iPhones.
To prevent installing apps from the App Store you can disable the App Store (only with DEP). You can use Apple VPP to serve apps via the Company Portal. You can also disable the possibility to backup managed apps to iCloud. This way prevents users to upload company data to iCloud.
You can’t get your result with Enrollment Options, but you can try the options i mentioned above.
Hey Joey, thanks for the tips. Yes our devices are managed via DEP/ABM. We do have the apple store disabled by policies, as well as VPP. Our phones are pretty well locked down to the point to not permit the use of Apple IDs. After doing federation, we have tested enabling the use of apple IDs and successfully login with a Federated account. My problem is not configuration, as we also push all apps via CP. But, enabling the use of apple ids, there is nothing preventing me to use my personal Apple ID, even though I won’t be able to download apps, or use any other features like icloud backups, the user can still register their phone with their personal apple ID. We have even disabled the activation lock, but we just want to prevent users to use personal IDs. We can tell end users, here is your corporate apple ID, use it, it is using SSO, but they will put their own.
Having Managed Apple IDs for managed devices is a plus, as it enables imessage and other nice features like pushing an active sync profile for contact synchronization (knowing that the sync between outlook and native app is one way only). But not having an option not to be able to use personal apple IDs, opens a door for end-users to use their own.
hope you understand,
Great article! Very helpful!
Since ABM (and every domain verified in it) can only be Federated with a single Azure AD, it appears that the only way to test in a UAT/TEST (non-prod) Azure AD environment would be to create a second ABM instance and federated the second ABM with the non-prod Azure AD. Am I understanding this correctly? Any options to avoid a second ABM environment?
Hi Manoj,
That is correct. At this moment ABM can only do federated authentication with a single Azure AD tenant.
Regards, Peter
Hi Peter,
Great article here.
I’m just going through the motions of enabling SCIM. We have a profile within Intune that has previously been applied via Apple Configurator 2. Now that we are no longer using Apple Configurator, I’d like to apply that same profile or create a new version of it and apply it through Apple Business Manager.
Are you able to share how I go about doing that?
Thanks,
Ad
Hi Adam,
That depends a bit on the type of settings. Many settings are available via the different policies and profiles within Intune already. An alternative could always be to create a custom configuration profile and providing the .mobileconfig file.
Regards, Peter
we would like to block the use of personal ids in apple icloud account.
we just want that they should be using their WORK account id’s . is that can be achievable through APPLE ade enrollment ?
Not sure if there is a setting that does specifically that. You can make it difficult for the user to use a personal account.
Regards, Peter
Hi,
Awesome article!
Is federation required for Azure AD join? We have enrolled iPhones in ABM (using Apple Configurator) without federation and Intune MDM, but they show up in Azure AD as registered.
Thank you,
Liza
Hi Liza,
An iOS device cannot be Azure AD joined. Those devices are always registered.
Regards, Peter
Hi. Thank you for the great article. I have to setup the scenario you described above. After Step 11 you write “Important: When automatically provisioning of the Managed Apple IDs should also be configured, do not yet enabled the federation.”
When I was at this point, the Federation was already enabled. This was done by another administrator in the past, I was told. Together with initial domain verification.
I configured all the other steps without error but I can’t see any new accounts. What can I do to ‘reset’ this situation or to let the accounts come in?
The sync status of the enterprise app ‘Apple school manager’ says: “Incremental cycle completed., 100% complete”. A scoping filter is not set. I assume that all accounts from AAD should be synchronized. But under “Provisioning Logs” no data comes: “No results found. Please review the filters above.” Not even when I turn off all filters and set the date to ‘last 30 days’.
Do you have any idea what is going wrong?
Hi Robert,
Please have a look at the information as provided in the automatically provisioned users from Azure AD section.
Regards, Peter
Thanks for the tip. I didn’t realize that ‘Users & Groups’ at point 8 meant the ‘Users & Groups’ section of the Enterprise App.
Clarification question on devices in inTune. After federation, can users still enroll personal devices tied to personal Apple IDs in Intune MDM using the Intune company portal process? Thanks.
Hi Richard,
That should not be a problem. Just make sure that users are not using their corporate-account as a “personal” Apple ID.
Regards, Peter
Hi Peter,
Imagine the following use case, you’ve configured an AppleID based upon an alias of a shared mailbox which you use for Apple MDM certificate or ABM account.
When you’ve configured the federated authentication in ABM, you won’t be able to logon with these accounts anymore as the federation points you to Azure AD for authentication but these is no real user for the shared mailbox …
Any idea’s how to resolve this, other then creating a user account based upon that email address?
Sorry Bart, but I don’t have any other suggestions at this moment.
Regards, Peter
So I have setup federation, and I can login to appleid.apple.com with my managed appleid. I can’t seem to get that ID to work for logging into my managed macbook air? I even tried signing out of the existing appleID and signing in with the managed one ( successfully ), but when I login to the machine it still wants to authenticate to the local admin user ( and won’t try the managed one ). What am I doing wrong?
Hi Jon,
To my knowledge that is the functionality currently provided by Apple (see also: https://support.apple.com/en-gb/guide/deployment/depa85a35cf2/web)
Regards, Peter
Hello Peter,
Great helpful articles….
I have a question. Is see al lot of articles describing creating a federation between ABM en AAD.
But almost nothing about disconnecting and/or deleting of a federated connection and the impact it had on federated users.
In our case Apple Support advised use to delete the current broken AAD federation (which was a crappy one, created by an old IT supplier of our customer) in order to create a new one, and unlock the full power of the planned Shared Ipad setup. We cannot find any articles on the web in which is explained what will happen with the created federated Apple ID (managed, new and SCIM created) when de federation is deleted/disconnected.
Can you tell us something about this. We need to know what the impact will be on de current shared iPad, cause they are used in a production environment.
(give my regards to your father. I work with him for a few years)
Hi Douwe,
The impact on existing Shared iPads can’t be big, because the federation is only used initially to authenticate. After that you’ve got to set a PIN that’s managed within ABM. So, at that point you’re not relying on the federation anymore.
Regards, Peter
H Peter,
Thanks for your reply.
So as I understand is that when we delete the federation nothing BIG happens with the Ipads and Iphones? (no wipe or lost mode….or??) Our main concern is the people lose data in any way and cannot work with the Ipad/Iphone during the delete/create proces.
Maybe for your information and better judgement, is that Apple advises us to delete the current federation between ABM and AAD (because the current setup maybe broken….”during enrollment of a new federated user on a shared Ipad” does not let us to create the PIN that you described. Only manual enrollment works).
We should reinstate a federation tot the same tenant and domain after successful delete, in the hope the error resolves. Do we have to create new passwords when the tenant federation is deleted ?
Ah, okay. So, it’s more than just Shared iPads. From what I recall, the accounts won’t break, but the authentication will.
Regards, Peter
Hello Peter
I want to remove initial tested federation to different Azure AD domain. However in Federated Authentication i still see Microsoft Azure Active Directory Configured and no way how this can be removed/disconnected.
Any advice? Or do I need to request 2nd ABM instance?
Hi Tomas,
There are some parts of the configuration that would still require work from Apple support. So, contact Apple and ask them to remove it.
Regards, Peter
At this point in the tutorial you say “another alternative is letting Apple Business Manager automatically create Managed Apple IDs once their used for the first tine”. I understand that there is no need to federate, as it will create a managed ID for everyone. I want him to create the IDs only according to the use, if the user is to register he creates it, otherwise not. How would you do ?
Hi Marcel,
You would still need the federation for the authentication, you just don’t need the provisioning with that.
Regards, Peter
Hi Peter,
I have an issue, we have added multiple iPhones through the Enrollment program tokens with domain federated Apple ID’s. After enrolling, when we log into the Apple Store with our federated Apple ID’s all app-downloads are greyed out. I haven’t blocked the App Store in MEM so is this something that can be fixed? In an ideal situation we would auto-publish the device configuration and certain apps, but also allow people to download extra apps on their own.
Hi Stein,
That’s standard behavior: https://support.apple.com/en-gb/guide/apple-business-manager/axm78b477c81/web
Regards, Peter
Hi Peter, great article.
Is SCIM separate from Federation or does SCIM require federation? My understanding is SCIM does require federation, but federation does not require SCIM. How do they differ exactly? I am having troubles understanding this piece
You mention a big strength to managed apple ID’s is the ability to use both managed apple ID along with personal. How does this work? Can a user enroll a corporate-provided device with their personal Apple ID so they retain all personal apple ID functionality (app store, apple pay, etc) and also have that device associated with a managed apple ID as well? How does that work with management from an MDM like Intune?
Can you manually create managed apple ID’s and just use as one-off scenarios for for something like shared iPads, or does that require creating said managed apple id accounts via federation?
Can you enroll a device via managed/federated apple ID then later add a personal account to access app store etc on a single device?
I’m in a scenario where I’m trying to have it both ways (have the user be able to log in to an iOS device via azure AD credentials but also still be able to use their device as if it was a personal account). Also interested in potentially skipping federation entirely, if possible, to create a working shared device workflow, since there are tons of existing apple ID account conflicts.
Hi Anon,
That’s a lot of question. If I miss a few, my apologies. SCIM is used for importing user accounts into ABM and federation is used for authenticating users. You indeed need to have the federation configured, before you can configure SCIM. However, you don’t need SCIM. You could also manually create user accounts, or let ABM create user accounts.
Usign the combination of personal and managed Apple IDs, us currently only really applicable to the User Enrollment scenario. That’s creates a (possible) separation between personal and corporate data.
Regards, Peter
Hi Peter,
Thanks so much for your helpful weblog. I wanted to ask about your mention of conditional access in this post. Over the past year, I’ve seen users being asked to re-authenticate to iCloud with Managed Apple ID in their iPad settings roughly every 90 days. My users are asking for an experience closer to what they had prior to federation, where Apple wouldn’t require re-authorization too frequently. In my reading I’ve landed on the rolling 90 day authentication window as a possible cause, and Conditional Access for the Apple Business Manager app in Azure as a possible solution.
We don’t have any conditional access policies in place now, but I was hoping you could tell me what impact setting conditional access sign-in frequency to 365 days would have on this scenario. Will it allow my users to stay logged in to iCloud for a full year? I’ve tried setting it down to a week or so for a few users as a test, but it doesn’t seem to force them to re-authenticate so I’m not sure if it’s having any impact at all. Perhaps I’m just confused. Can you offer any advice?
Hi Alas,
It all depends on the different apps that will be targeted and how it is scoped. Otherwise the impact will be bigger than expected..
Regards, Peter
Great blog thanks! What is the impact on devices? Let’s say a user has an Apple ID on a corporate mail address (martijn@contoso.com) and we federate contoso.com The user will get a mail to change his Apple ID mail address but will this mail address also be his login name for his Apple ID and will the device prompt to change the Apple ID? I’m confused.
Hi Martijn,
The personal Apple ID will change and the managed Apple ID will be on the corporate address.
Regards, Peter
Peter, but what happens when the user is logged in on his ipad before the domain claim? Will it get a notification on the device to sign out and sign in with his new mail address?
Hi Martijn,
Please have a look at the earlier response by Joey.
Regards, Peter
Hello Peter, great article!
I have the same situation as Joey described, need to enable Azure AD federation in company where around 300 users already use personal Apple IDs with company’s domain.
Just to confirm the flow of a couple steps:
As far as I can see in this video, I will be able to see the number of conflicts before federation is enabled by moving slider to the right:
https://youtu.be/4hPCJYXsnng?t=1305
At the end, when I enable federation by moving slider to the right I have to click “Send notifications” button to send emails to users with conflict.
Then, in the next step, all users with conflict will start receiving emails to create another Apple ID?
And as you mentioned – user accounts will start coming to Apple Business Manager.
Thanks
Hi Djordje,
It’s as explained by Joey. Once you claim the domain, users will have 60 days and receive a notification about what’s happening.
Regards, Peter
Hi Peter,
Thanks for the article, super useful to our org.
May I ask, is there any way to exclude particular users from federation? I need to create an Apple ID using the company domain, as a test analyst requires a specific app that leverages the logged in system ID/Apple ID, but I don’t want that account to be a managed Apple ID and all the restrictions that go along with that.
Is there any way around this?
Hi Tom,
Can’t you just manually add a managed Apple ID to ABM?
Regards, Peter
Hi Peter,
Appreciated this run down, helped greatly.
Kind of a fringe case but was hoping for some input.
Rather than federate our root domain (office365 upn’s) and create chaos among the user base, I thought it would be a good idea to create a subdomain, ie appleid.contoso.com
From their I added a regex expression in the SCIM provisioning to take the UPN and populate the subdomain suffix that was added.
Problem I’m facing now is the SSO login piece, the sign s expected the subdomain address but these accounts don’t actually exist. I created email aliases in the hope I could update the SAML claim to do the same expression that was done for the SCIM provisioning.
Should be noted that this subdomain is verified in office365 and is routable.
Any thoughts or should I just do the root and listen to some whining?
Hi Thomas,
My first response would indeed be to accept some whining. That being said, I have to be hones that I haven’t tried your work around. But I also can’t really imagine how that would work with the sign-in of the user…
Regards, Peter
Is it possible to use guest sessions on a brand new (supervised) iPad without an apple id login? Use case is for public use and allow guest sessions. Thanks
Hi John,
On Shared iPads that should be possible.
Regards, Peter
Hi Peter, thanks for your clear guide. Is there no way to select a group of AzureAD users to sync? I get the feeling that it will now also sync guest / external / B2B users, or am I wrong in stating that?
Hi Gerard,
Apologies for the late reply, as I was enjoying my vacation. Only the users in the specified group(s) will be synced.
Regards, Peter
Hi Peter, very good article and website.
Maybe you can help me a bit. We are looking at implementing BYOD, but many users have already created AppleID’s based on company email. Trying to avoid this, is there a way to use another domain or enrolment method? When I enrol an iPhone it must connect with company email to Intune, and then it asked to login with the Managed Apple ID, but I can’t change the AppleID;s email address during setup. I can only enter the password. Look at federation I think it will create lots of problems due to the limitations, and the fact that one of the email addresses has been used to crate DEP connection to Jamf, if this changes it will break things… Any way to do the BYOD, but no device enrolment, perhaps another way to do this?
Hi Mark,
So you are looking at BYOD and no device enrollment? If so, you’re quickly looking at user enrollment and that requires Managed Apple IDs.
Regards, Peter