This week is all about Shared Device Mode for iOS (and iPadOS) devices. Shared Device Mode is based on Azure AD and is the Microsoft solution for shared iOS devices. Those shared iOS devices are company-owned multi-user devices. Shared Device Mode is provided for iOS (and iPadOS) 13 and later devices and enables multiple users to use the same Apple device and to sign in and out of apps by using an Azure AD account. When those apps support Shared Device Mode, those apps provide the global sign in and global sign out functionality. That enables a user to sign in to an app, at the start of a shift, and automatically be globally signed in to all apps that support Shared Device Mode. That’s also applicable to the the sign out of an app at the end of a shift. The user will automatically be globally signed out of all apps that support Shared Device Mode, which enables multiple users to easily and securely share an iOS device. This post will go through the different configurations that are required for setting up Shared Device Mode.
- Creating an enrollment profile for iOS devices with Shared Device Mode
- Creating a filter for iOS devices with Shared Device Mode
- Configuring the Microsoft Enterprise SSO plug-in for iOS devices with Shared Device Mode
- Configuring the Microsoft Authenticator app for iOS devices with Shared Device Mode
- Getting an iOS device up-and-running in Shared Device Mode
Important: At the moment of writing, Shared Device Mode is still an Azure AD preview feature. That means that the feature is provided without a service level agreement. Also, the usage of the feature is not recommended for production environments.
Recommendation: Unless an organization needs cellphone capabilities, or needs to use iOS devices, Shared iPad is the recommended shared device solution for Microsoft 365 on iPadOS devices.
Note: A big thank you to Tobias Almen for confirming the current behavior of Shared Device Mode.
Creating an enrollment profile for iOS devices with Shared Device Mode
The configuration of Shared Device Mode already starts at the enrollment of an iOS device, as the device should be configured as a company-owned device without user affinity. That can be achieved by using an enrollment profile for iOS devices that are available via Apple Business Manager (ABM). The following six steps walk through the creation of that enrollment profile. After the creation of that enrollment profile, it can be assigned like any other enrollment profile.
- Open the Microsoft Endpoint Manager admin center portal and navigate Devices > iOS/iPadOS > iOS/iPadOS enrollment > Enrollment program tokens > {YourEnrollmentToken} > Profiles
- On the {YourEnrollmentToken} | Profiles page, click Create profile > iOS/iPadOS to open the Create profile wizard
- On the Basics page, provide the following information and click Next
- Name: Provide a name for the profile to distinguish it from other similar profiles
- Description: (Optional) Provide a description for the profile to further differentiate profiles
- Platform: iOS/iPadOS is preconfigured based on the initial start of the wizard
- On the Management Settings page, provide at least the following information and click Next
- User affinity: Select Enroll without User Affinity as value, as a shared device can’t have user affinity
- Supervised: Select Yes as value, as a shared device must be supervised
- Locked enrollment: Select Yes as value, to make sure that the enrollment is locked on the device
- Sync with computers: Select Allow All as value, to allow the shared device to sync with computers
- Apply device name template (supervised devices only): Select Yes as value to easily identify shared devices
- Device Name Template: Specify a device name template to easily identify shared devices
- On the Setup Assistant page, provide at least the following information and click Next
- Department: Specify the department name that should be displayed in the Setup Assistant
- Department Phone: Specify the department phone number that should be displayed in the Setup Assistant
- Setup Assistant Screens: Click Toggle All to hide all the screens in the Setup Assistant
- On the Review + create page, verify the configuration and click Create
Creating a filter for iOS devices with Shared Device Mode
The targeting of policies, profiles and apps for iOS devices with Shared Device Mode, can be simplified by using a filter. That filter can be used to filter all the devices that are enrolled by using the earlier created enrollment profile. The following six steps walk through the creation of that filter.
Important: At the moment of writing not all required configurations support filters. Those configurations might still require a dynamic Azure AD device group and that device group can be configured with the same membership rule.
- Open the Microsoft Endpoint Manager admin center portal and navigate Devices > Filters (alternative roads to the same configuration are Apps > Filters or Tenant admin > Filters)
- On the Devices | Overview page, click Create to open the Create Filter wizard
- On the Basics page, provide the following information and click Next
- Filter name: Specify a unique name to distinguish the filter from other filters
- Description: (Optional) Specify a description to further explain the usage of the filter
- Platform: Select iOS/iPadOS as value
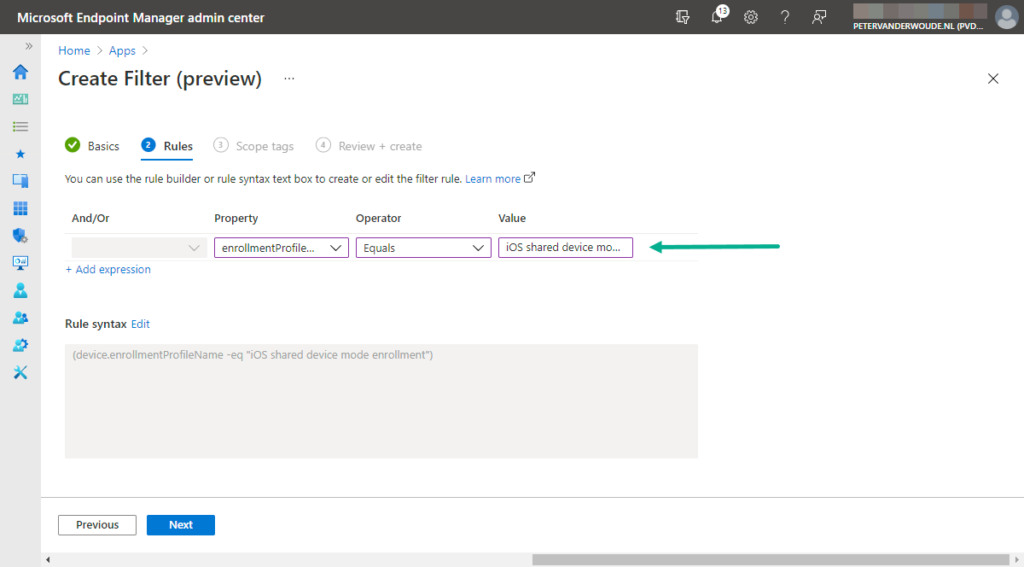
- On the Rules page, as shown below in Figure 1, create the following configuration and click Next
- Expression 1 – This expressions is used to filter devices based on the enrollment profile that is used
- And/Or: Not applicable
- Property: Select enrollmentProfileName as value to filter devices based on the enrollment profile that is used
- Operator: Select Equals as value to filter devices based on a specifically matched value
- Value: Specify the name of the just created enrollment profile as value to filter on that enrollment profile
Note: When creating this filter, or a dynamic Azure AD device group, a rule syntax like this (device.enrollmentProfileName -eq “{enrollmentProfileName}”) can be used.
- On the Scope tags page, configure the required scope tags and click Next
- On the Review + create page, verify the configuration and click Create
Configuring the Microsoft Enterprise SSO plug-in for iOS devices with Shared Device Mode
The single sign-on experience, for the supported apps, is provided via the Microsoft Enterprise SSO plug-in for Apple devices. That plug-in relies on the Microsoft Authenticator app and requires the Microsoft Authenticator app to be installed to provide that single sign-on experience. The following eight steps walk through the configuration of the Microsoft Enterprise SSO plug-in and the assignment of that configuration to the filtered devices.
Important: As the device is a company-owned device without user affinity, make sure to deploy the Microsoft Authenticator app by using the Apple Volume Purchases Program (Apple VPP) and to use a device license type.
- Open the Microsoft Endpoint Manager admin center portal navigate to Devices > Configuration profiles
- On the Devices | Configuration profiles blade, select Create profile
- On the Create a profile page, provide the following information and click Create
- Platform: Select iOS/iPadOS as value
- Profile: Select Device features as value
- On the Basics page, provide the following information and click Next
- Name: Specify a unique name to distinguish the device features profile from other device features profiles
- Description: (Optional) Specify a description to further explain the usage of the device features profile
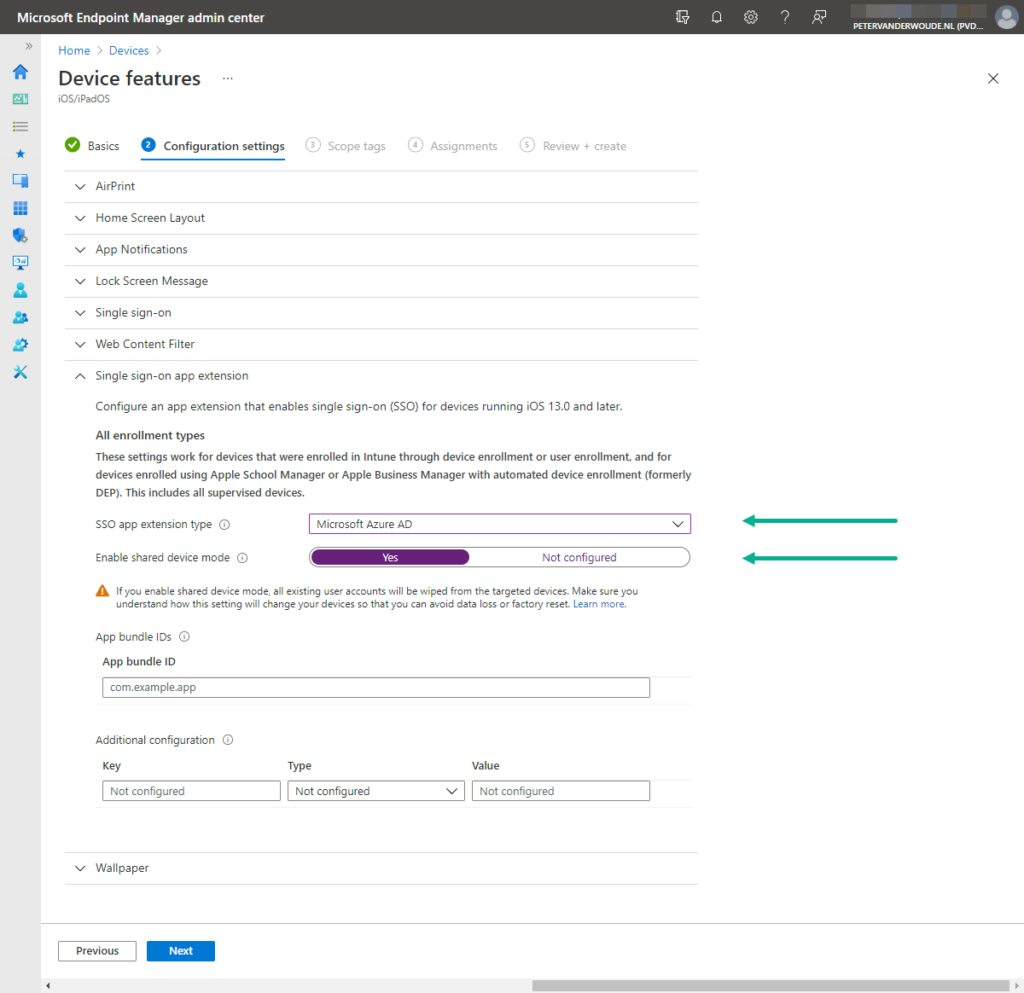
- On the Configuration settings page, as shown below in Figure 2, configure at least the Single sign-on app extension section by providing the following information and click Next
- SSO app extension type: Select Microsoft Azure AD as value to configure the extension type for Azure AD
- Enable shared device mode: Select Yes as value to change how the device works with apps
- On the Scope tags page, configure the required scope tags click Next
- On the Assignments page, configure the assignment to all devices with an include for the earlier created filter and click Next
- On the Review + create page, verify the configuration and click Create
Note: The include of the earlier created filter makes sure that the assignment is only applicable on the filtered devices.
Configuring the Microsoft Authenticator app for iOS devices with Shared Device Mode
The configuration of Shared Device Mode also requires a specific app configuration for the Microsoft Authenticator app. That app configuration will makes sure that the Microsoft Authenticator app will run in a specific Shared Device Mode. The following seven steps will walk through the configuration of the Microsoft Authenticator app for the Shared Device Mode.
Important: As the device is a company-owned device without user affinity, make sure to deploy the Microsoft Authenticator app by using the Apple Volume Purchases Program (Apple VPP) and use a device license type.
- Open the Microsoft Endpoint Manager admin center portal navigate to Apps > App configuration profiles
- On the Apps | App configuration policies blade, click Add > Managed devices to open the Create app configuration policy wizard
- On the Basics page, provide the following information and click Next
- Name: Specify a unique name to distinguish the app configuration policy from other app configuration policies
- Description: (Optional) Specify a description to further explain the usage of the app configuration policy
- Device enrollment type: (Grayed out) Managed devices
- Platform: Select iOS/iPadOS as value
- Targeted app: Select Microsoft Authenticator as value
- On the Settings page, as shown below in Figure 3, provide at least the following configuration and click Next
- Configuration settings format: Select Use configuration designer as value
- Click Add to add the sharedDeviceMode configuration key and set the configuration value for the boolean to true
- On the Scope tags page, configure the applicable scope tags and click Next
- On the Assignments page, configure the assignment by selecting the applicable group and click Next
- On the Review + create page, review the configuration and click Create
Important: At the moment of writing an app configuration policy is one of the configurations without support for filters.
Getting an iOS device up-and-running in Shared Device Mode
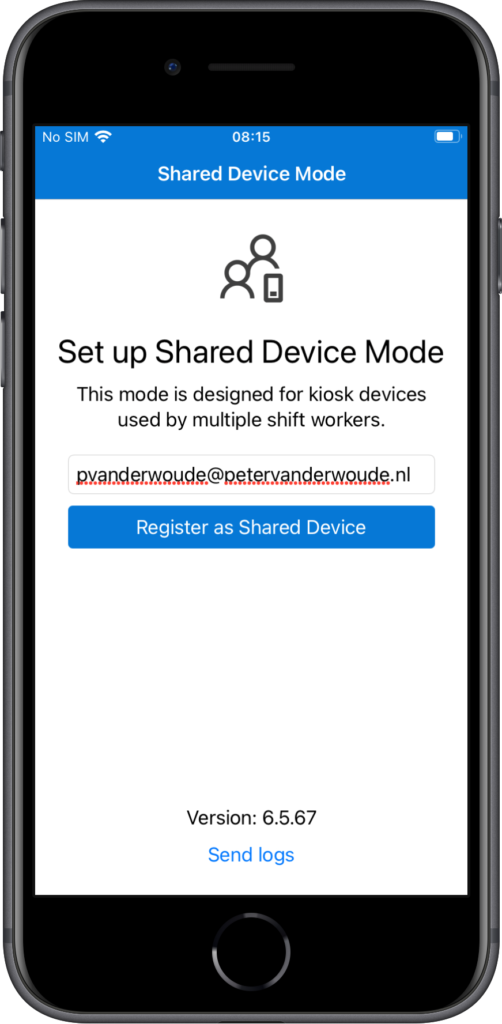
With creating and configuring the different components for Shared Device Mode for iOS devices, the most important work is done and the device enrollment will be automatically. The IT administrator will turn on the device and walk through the Setup Assistant. After completing the Setup Assistant the device will automatically enroll in Microsoft Intune and the Microsoft Authenticator app will be installed. Once the Microsoft Authenticator app is installed, the IT administrator must set up Shared Device Mode. That can be achieved by providing an organization email and clicking Register device as Shared Device, as shown below in Figure 4.
Important: The IT administrator that is setting up Shared Device Mode, must have the Cloud Device Administrator role.
Note: According to the docs, the manually action in the Microsoft Authenticator app is only required during the preview.
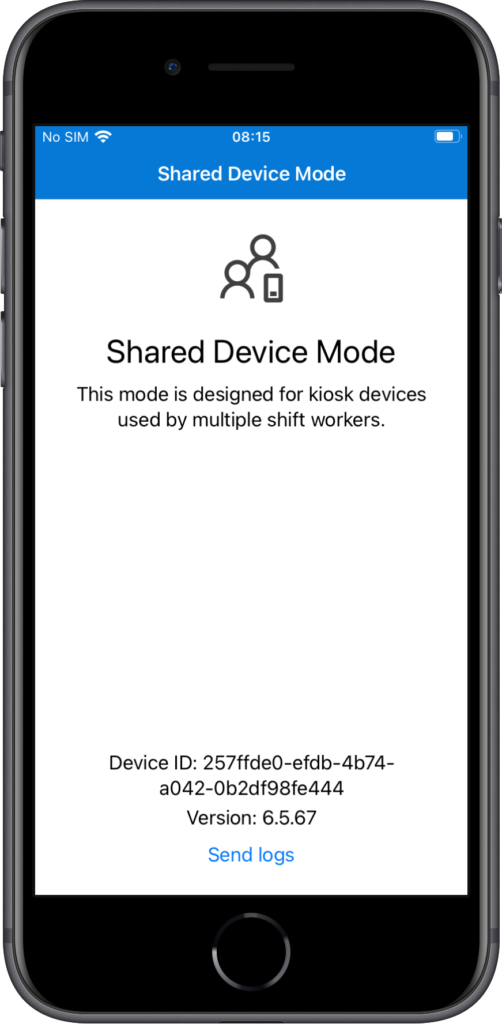
After that the iOS device is up-and-running in Shared Device Mode, as shown below in Figure 5. To further test the behavior, Microsoft provides an example frontline worker app. That app is available here. Besides that app, there are, at the moment of writing, no apps available for iOS that support Shared Device Mode.
More information
For more information about Shared Device Mode and Microsoft Intune, refer to the following docs.


I’ve setup as per the blog, but my devices are just getting “Request Timed Out” when trying to enroll, any ideas?
Hi Nick,
Are you referring to the registration in the Authenticator app? If so, make sure that the user is member of the Cloud Device Administrator role.
Regards, Peter
Thank you for writing this. There’s not a lot of information on this topic. I have a few questions about Best Practices and assignments… How do we assign an App Configuration Policy without the use of filters? Do we need to create a Dynamic Group based on Enrollment Profiles instead of using Filters? And if so, what’s the point of using Filters instead of keeping assignments consistent by using Dynamic Groups?
Hi Corey,
That’s just time. In time it will be possible to use filters for all objects. At this moment it’s still a bit in between, looking at the fact that not every object supports filters yet. It will come.
Regards, Peter
(I’ve struggled with multiple comments here, sorry for that. This one is the complete one 😀 )
Hi Peter,
applause for this article. Do you know if there’s a docs article out there where is outlined if there are any apps that supports this mode in the meanwhile? (I’M looking for Teams, Outlook, OneDrive, etc. (the most used MS aapps). Otherwise this mode is kinda useless for most of us, yet. 🙁 (Most customers don’t program their apps themselve.)
Thanks in advance!
By the way: There’s still no possibility to use filters for app configuration.
Is this process working with a dynamic group for the app configuration itself or would this break the enrollment process? (I can’t see any other possibility, yet.)
Hi Patrick,
1) For iOS, that’s currently Microsoft Teams only. There is a doc on the Tech Community and that’s about it. Android is getting some nice improvements, but that doesn’t help you now..
2) What do you mean with break the enrollment? What is the problem that you’re seeing?
Regards, Peter
Hi Peter,
as long as at least the standard microsoft apps are not supported, it is not worth it yet, i guess.
Because App configuration doesn’t support the use of filters. Therefore i need to use dynamic groups.
Because of the slowlyness of dynamic groups i think about that the deployment would not work, because when running though the enrollment the device does not know about the app configuration, yet. (Didn’t tested it)
Patrick
Hi Patrick,
Yes, the challenge with dynamic groups is that you have little control over the update of the membership..
Regards, Peter
Not having any luck here. On enrollment profile, does Shared iPad need to be Yes or No? I have seen it both ways about the very few sites talking about shared device mode. I just want to login as guest and people use Teams. Have iPads enrolled with Shared iPads set to No on enrollment profile, MS Authenticator configured as shared mode and logged into it and it’s enrolled as shared device mode, SSO is configured. But get no Guest or anything at lock screen. Does Shared iPad need to be Yes and if so then Federated accounts are needed as well. But I didn’t think that was needed with Shared Device Mode. Not sure what the issue is?
Hi Dan,
You need Shared iPad to be Yes. That will give you the actual SHared iPad configuration.
Regards, Peter
Hi Peter,
Thanks for the article!
One thing I don’t understand. You are registering the device as Cloud Device Administrator. Is this required for registration only and once it’s registered and the Cloud Device Administrator signed out then other users can sign in as well? Or it is only for users with Cloud Device Administrator role?
Hi Gordon,
That is only required to join the device and only during the public preview (which is still the case).
Regards, Peter
Based on the comments here, is Teams the only app that would be available to the end user when they login to an iOS device in shared mode or is Teams the only app that auto logs them in? Will the other installed apps display?
The apps that you make available, will be shown. It’s mainly about the sign-on and sign-off experience.
Regards, Peter
So can we use the same apps we are using today? We are trying to find the best process for getting our frontline workers signed into Teams besides adding it as another manual login to their existing process. Today, they pickup an iPhone that we manage in Airwatch with a profile configured for their job role (not per user), it has access to only the apps they need, they don’t login to the device, they just login to those apps.
I guess my question is, do the apps need to be developed for shared device mode or does it really just allows us to have the user sign onto the device and log them into Teams, then they manually login to the other apps?
Hi Matt,
Well, the app needs to be developed to support the shared device mode functionality that takes care of the sign-on and sign-off behavior. On Android device, there is something that at least works around the sign-off behavior (https://techcommunity.microsoft.com/t5/intune-customer-success/endpoint-manager-supports-sign-out-for-apps-not-optimized-with/ba-p/3034398), but to my knowledge not on iOS devices.
Regards, Peter
We are trying to configure Shared iPad and after device registration in Microsoft Authenticator App on an successfully enrolled Shared iPad we get this error “The SSO extension is not in shared device mode. Please refer to the error code SSO_EXTENSION_CONFIG_MISSING_SHARED_FLAG in the troubleshooting section of provided documentation”.
We use VMware Workspace ONE UEM.
We have deployed user context SSO Extension payload configured as per Microsoft documentation with custom XML to enable Shared Device Mode for the SSO Extension. Content of custom XML below.
sharedDeviceMode
Microsoft Authenticator is deployed with Application configuration as below:
Configuration Key = sharedDeviceMode
value Type = Boolean
Configuration value = true
Device registration is successful (banner appears at the top) but we get error as mentioned. We are registering device using a account with cloud device administrator role.
Any link to troubleshooting document or guidance on how to move ahead is much appreciated
Hi Makesh,
Are you saying that you’re also using the Microsoft Enterprise SSO extension?
Regards, Peter
Thanks for the write up. The Azure AD SSO extension is still in preview, but has matured a bit (enough that getting the right info from various areas of MS documentation can point you in different directions). Question I have is whether this supports iPhones. It states iOS devices (rather than the prior Shared iPad only option), so seems like it should, but I’ve yet to get this working on one. I can get as far now as having the Authenticator App allow a cloud admin account register the device, but there is never any opportunity to get the device in a mode that would allow any sort of login prompt to authenticate with an Azure AD account.
Thanks in advance!
Hi Jey,
The example shown in the post is also of an iPhone. So, yes, it should work. It’s also documented as the shared device solution for those devices here: https://learn.microsoft.com/en-us/mem/intune/enrollment/device-enrollment-shared-ios?WT.mc_id=EM-MVP-5001447
Regards, Peter
Hi Peter, did you already tested the differences between those two:
Case 1: As in your article: Enrollment profile = Enroll without user affinity, in addition the sso plug-in, assignment of the device licensed Authenticator App via VPP, with App configuration
Case 2: Enrollment Profile = Enroll with Azure AD shared mode
As mentioned in this article from ms (https://learn.microsoft.com/en-gb/mem/intune/enrollment/automated-device-enrollment-shared-device-mode#step-1-create-an-apple-enrollment-profile) they aren’t using an app configuration for the authenticator app, but a device configuration profile of type “Device features”.
Do you already know why and what are the differences?
Hi Patrick,
I think that’s a simple case of evolution. When I wrote that post, the functionality was still in the early stages of the public preview. Now, less manual actions are required to eventually reach the same goal.
Regards, Peter
Hello Peter
I configured everything like you mentioned in this article. So far so good and everything looks like expected.
But now my question is, when i open the Authenticator App i see the Title Set up Shared Device Mode and i have to provide an email adress…if i enter my Work Adress it does not work (our MFA pops up and i can approve with authenticator app in my other Phone) but then after i get Device Registration server error Message.
So do an Cloud Admin User need to first sign in in Authenticator App to get work, or is something else wrong?
thanks and regards
Kaya
Hi Kaya,
During the preview, the IT administrator that is setting up Shared Device Mode, must have the Cloud Device Administrator role.
Regards, Peter
Hi Peter,
I configured everything like you mentioned.
Is it right, that i need to log-in to the Authenticator App with a cloud device admin role account first, when a new AAD-User is using the ipad?
Hi Ivan,
During the preview, the IT administrator that is setting up Shared Device Mode, must have the Cloud Device Administrator role.
Regards, Peter
Hi Peter
Thanks for your article. i have setup shared iOs Device like your example and it works fine so far.
What iam missinng is how or where can i configure a User AAD Account sign in on iPad/iPhone?
Currently we have no sign in when starting os and so if User A signs in to Teams, he has to log out from Teams before hands over the device to User B, otherwise User B would have access to User B Teams and Files.
Thanks and regards
Kaya
Hi Kaya,
As far as I know, on Apple devices, only by using Shared iPad.
Regards, Peter
Hi Peter,
Thank you for writing this guide. I have read this page as well as the Microsoft Learn article, and while I seem to have got the solution working insofar as the Authenticator app will display a message reading “This device is now set up in Shared Device Mode. You can return to the application and sign in”, the end user experience is not quite there yet.
As you have already said yourself in the comments, it seems Microsoft have evolved the setup process here, and it’s no longer necessary to create the app configuration profile for the Authenticator app – it’s my understanding that a pre-existing Authenticator app profile which is deploying the app to all iOS devices should be sufficient now, is that also your understanding?
In my proof of concept iPhone, I found that I could log into Outlook, and OneDrive and Teams would automatically log in; not bad. Unfortunately, Office apps like Word, Excel and PowerPoint stubbornly refused to log in by themselves. To make matters worse, logging out of Outlook was not successful in logging out any other apps.
This makes me think I have missed something.
In your example, you recommend creating the SSO app extension by configuring only the extension type (Microsoft Azure AD) and the enable shared device toggle (Yes).
In Microsoft’s documentation (https://learn.microsoft.com/en-us/mem/intune/enrollment/automated-device-enrollment-shared-device-mode) they recommend configuring a key called device_registration, which I did, but didn’t seem to get things going.
On another MS page on this topic (https://learn.microsoft.com/en-us/entra/identity-platform/msal-ios-shared-devices#use-intune-to-enable-shared-device-mode–sso-extension) they discuss the need to configure the same, and link to a further page (https://learn.microsoft.com/en-us/entra/identity-platform/apple-sso-plugin) which describes a different configuration again, this time including keys called AppPrefixAllowList and browser_sso_interaction_enabled.
Naturally, I configured all 3 keys described across the 2 pages in my config, and that has got me to the state I described at the beginning, where it seems to be configured correctly but doesn’t quite work.
The only things I did differently from you was re-using a pre-existing Authenticator app deployment and scoping my SSO app extension policy to a dynamic group (based on deployment profile) – I obediently created the filter as instructed, but didn’t use it at any point.
If you’ve made it to the end of this missive, and understood it all, I wonder if you can spot anything I’ve done wrong that would cause the solution not to work?
Microsoft haven’t made it very easy, because there doesn’t seem to be a list of their apps which support this method, so I’ve no idea if the Office apps are supposed to work or not.
Robert
Hi Robert,
That was a lot of information. I think it all starts with the apps that support this functionality. So far, only Microsoft apps that I know of. And at this moment only these apps: https://learn.microsoft.com/en-us/entra/identity-platform/msal-ios-shared-devices#microsoft-applications-that-support-shared-device-mode
Regards, Peter
Thanks for the reply Peter, and for that link – extremely useful! I searched in vain for something like that without success, so this explains why I’ve had such limited success in my testing.
To your knowledge, is there a signing out process yet? Again, this isn’t something I’ve had any luck in finding any documentation around, but testing has shown that logging out of any one app has no effect on the others.
I did hope that signing into the Authenticator app with a different account would simply log that account into the other supported apps in place of the previous one, but all it did was produce errors.
I’m not sure how Microsoft consider the solution viable in the real world if this is the case?
Don’t get me wrong, it seems like a great feature, but not match-fit from my perspective, not yet.
Regards,
Robert
Hi Robert,
I haven’t used this and/or tested this recently. From what I’ve seen and heard, it should now be the case that all supported apps automatically sign-out. If that’s not the behavior that you’re experiencing, I would suggest to raise a support case with Microsoft.
Regards, Peter
Hi Peter!
I have an ipad with this solution but i am having some trouble.
1. I get an error saying “SSO_EXTENSION_NOT_ACTIVE” i have followed your guide and created an app config policy but i still get this error
2. i dont understand how this works, is it like android shared device mode for dedicated devices where the users log into managed home screen(or another app) with their entra id user? and that session is theirs?
Hi Michael,
That sounds like the configuration to enable the SSO extension has not been applied yet.
Regards, Peter