Combining the different layers of data security on personal Windows devices
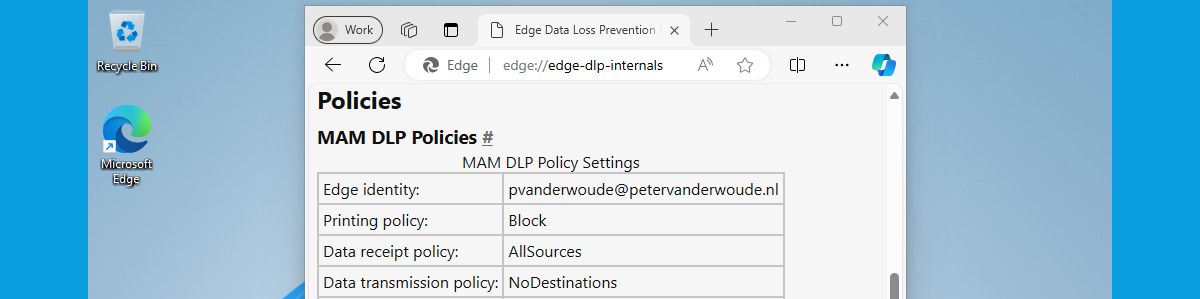
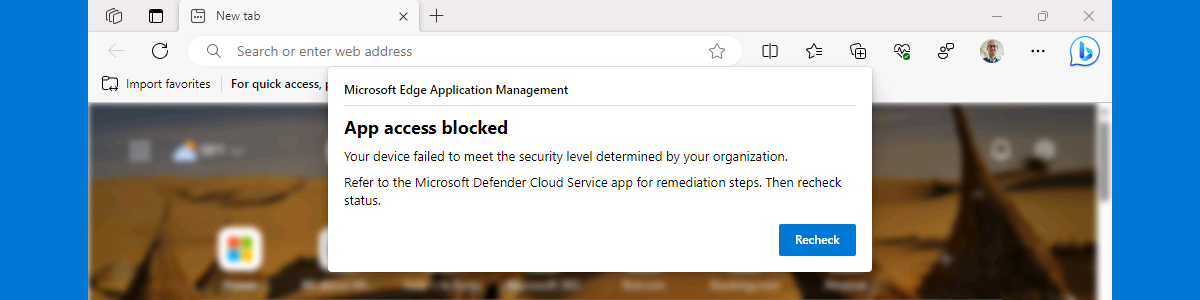
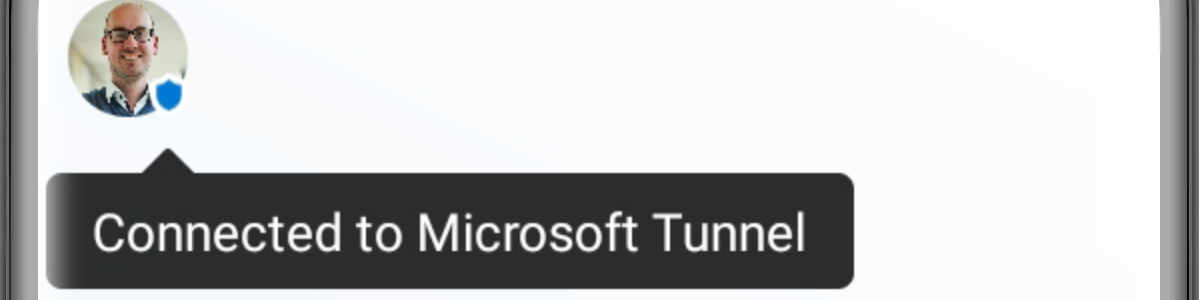
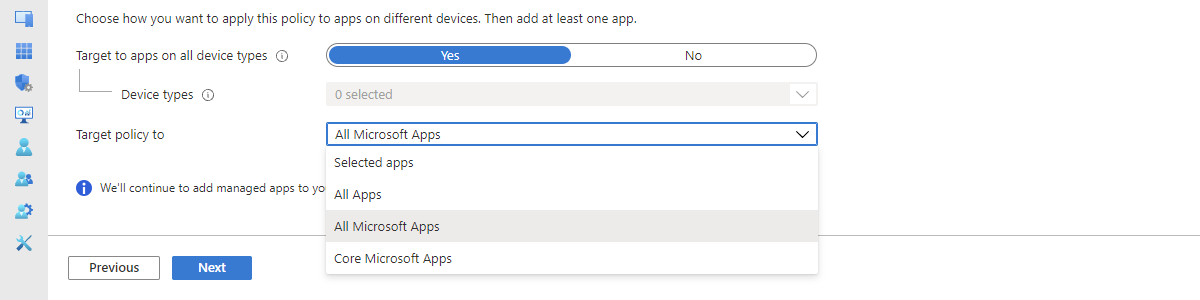
This week is a continuation of my previous blog post about working with personal Windows devices. That post was focussed on the different options available for providing secure access to corporate data on personal Windows devices. This post is focussed on providing more details around using those different options actually as different layers in a single solution. All with the focus on providing secure access to corporate data on personal Windows devices, while still providing the user with as much flexibility and options to be productive. Besides that, using different layers of data security also enables the IT administrators to add more granularity to the solution. That makes the total solution less black-and-white. So, for example, not just block the ability of the user to …