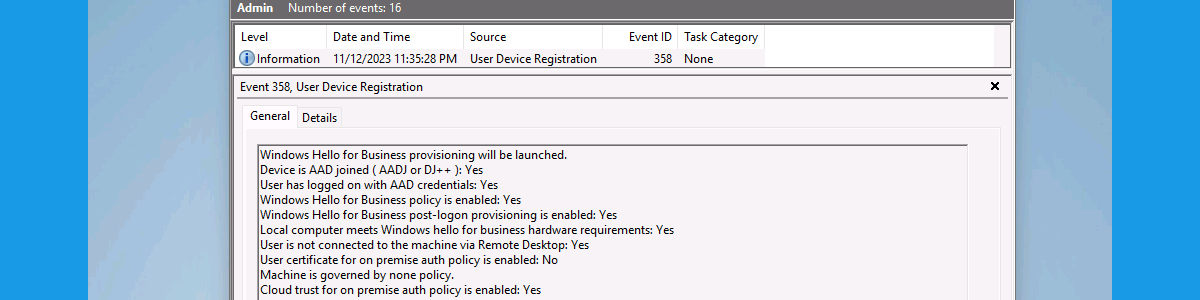
Discouraging data leakage on Windows 365
This week is all about a few newly introduced features to discourage data leakage specifically for Windows 365. Within the Microsoft 365 solution there are many different options for protecting data. On the data itself as well as platform specific options. Windows 365 is the latest platform that can be added to that list with platform specific solutions. Windows 365 recently introduced screen capture protection that can be used to discourage leaking data by preventing it from being captured. Besides that, it also introduced watermarking that can be used to discourage leaking data by adding a watermark to the desktop that can be traced to the session or desktop of the user. Different solutions, for different scenarios. This post will start by briefly introducing both …