This week is all about another new Windows 11 features and that feature is Dev Drive. Dev Drive is a new form of a storage volume that is aimed at improving performance for key developer workloads. It enables users to create a separate volume on their device that will improve the performance for disk-bound operations such as cloning, building, copying files, and package restore. To gain that performance, Dev Drive builds on ReFS technology. That technology provides file system optimizations and more control over storage volume settings and security. That includes trust designation, antivirus configuration, and administrative control over what filters are attached. All of that, could also be a reason to make sure that some security-minded Dev Drive configurations are in place. To make sure that a certain minimal level of security is available and also can’t be removed. This post will provide a closer look at the available management options for Dev Drive, followed with the experience with the applied configuration.
Note: Keep in mind that Dev Drive is mainly intended for source code repositories and project files, for package caches, and to build output and intermediate files. And not to store developer tools.
Introducing Dev Drive
Dev Drive is a new appearance of a storage volume that is optimized for developer workflows. A storage volume on itself is nothing new, it specifies how data is stored on the file system in a particular format. For most system drives and other non-removable drives, Windows uses NTFS as the format. Besides that, Microsoft introduced the newer file system format Resilient File System (ReFS). ReFS is designed to maximized data availability, scale efficiently to large data sets across diverse workloads, and provide data integrity with resiliency to corruption. That format is also what is utilized by Dev Drive. It enables Dev Drive to achieve that better performance for developer workloads and customizable settings that are optimized for developer scenarios.
When mentioning performance, there is often a tradeoff between performance and security. However, when using a Dev Drive that places control, over the balance between performance and security, in the hands of developers and IT administrators. Those users can choose which filters are attached and what is configured in the antivirus scans. Well, initially the IT administrator determines what is allowed and the developer can work within the provided boundaries. When nothing is configured by the IT administrator, the developer can basically determine the configuration. Good thing is that by default the antivirus filters are attached to a Dev Drive. So, when nothing is enforced by the IT administrator, it must be a deliberate action to remove those filters. Maybe even better, Microsoft Defender Antivirus now includes a performance mode that is specifically designed for Dev Drive. Performance mode reduces the performance impact of scans for files stored on the Dev Drive. The goal of performance mode is to improve functional performance for developers.
Note: Any product or feature that requires additional filters, will not work unless the filter is added to Dev Drive.
Configuring security policies for Dev Drive
When looking at configuring security policies for Dev Drive, it starts with the available management capabilities. Those management capabilities start with filters, as any product or features requiring additional filters will not work unless that filter is added to the Dev Drive, including antivirus products. Luckily, there is a new node (FileSystem) available within the Policy CSP that contains settings that can be used for this purpose. That CSP contains the EnableDevDrive policy setting that can be used to enable Dev Drive. When that setting is not configured any local administrator can choose not to attach the antivirus filter. Besides that, it also contains the DevDriveAttachPolicy policy setting that can be used to list filters that are allowed to attach to the Dev Drive. Both settings are ADMX-backed via filtermanager.admx and are available via the Settings Catalog. The following eight steps walk through the creation of a Settings Catalog profile that contains the required settings for Dev Drive.
- Open the Microsoft Intune admin center portal and navigate to Devices > Windows > Configuration profiles
- On the Windows | Configuration profiles blade, click Create > New Policy
- On the Create a profile blade, provide the following information and click Create
- Platform: Select Windows 10 and later to create a profile for Windows 10 devices
- Profile: Select Settings catalog to select the required setting from the catalog
- On the Basics page, provide the following information and click Next
- Name: Provide a name for the profile to distinguish it from other similar profiles
- Description: (Optional) Provide a description for the profile to further differentiate profiles
- Platform: (Greyed out) Windows 10 and later
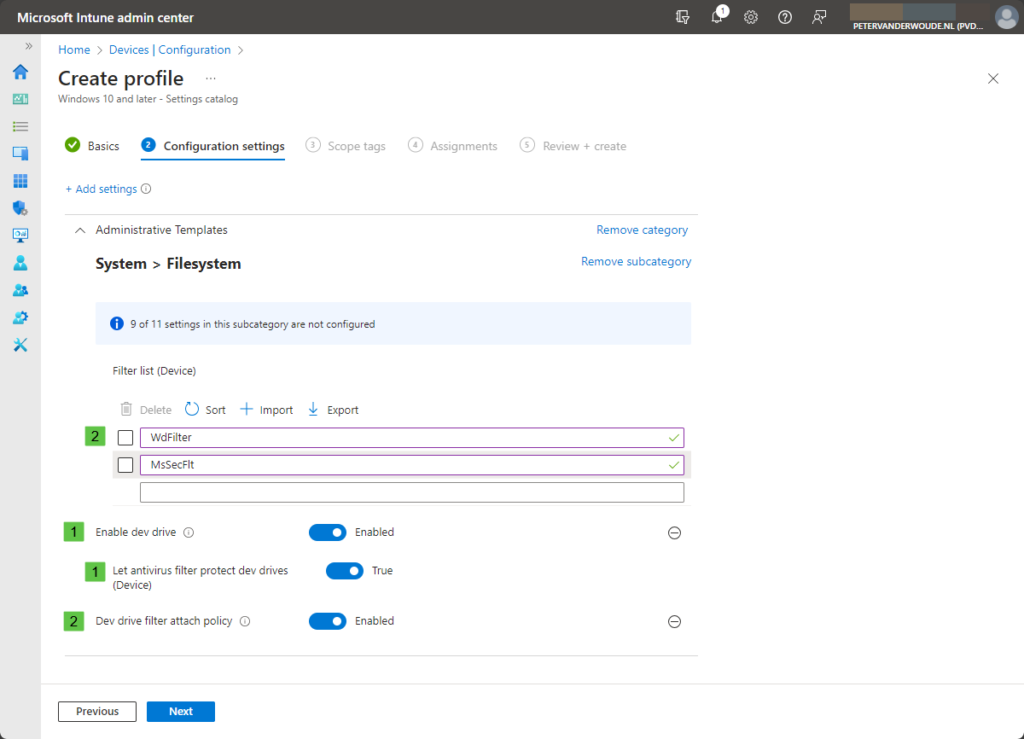
- On the Configuration settings page, as shown below in Figure 1, perform the following actions
- Click Add settings and perform the following in Settings picker
- Select Administrative Templates > System > FileSystem as category
- Select Enable dev drive and Dev drive filter attach policy as setting
- Switch the slider with Enable dev drive (1) to Enabled and after that do the same for Let antivirus filter protect dev drives (1)
- Switch the slider with Dev drive filter attach policy (2) to Enabled, specify the required filters (2) with Filter list and click Next
- On the Scope tags page, configure the required scope tags and click Next
- On the Assignments page, configure the assignment and click Next
- On the Review + create page, verify the configuration and click Create
Note: The order of the settings looks indeed really funny when enabling the different sliders.
Experiencing security policies for Dev Drive
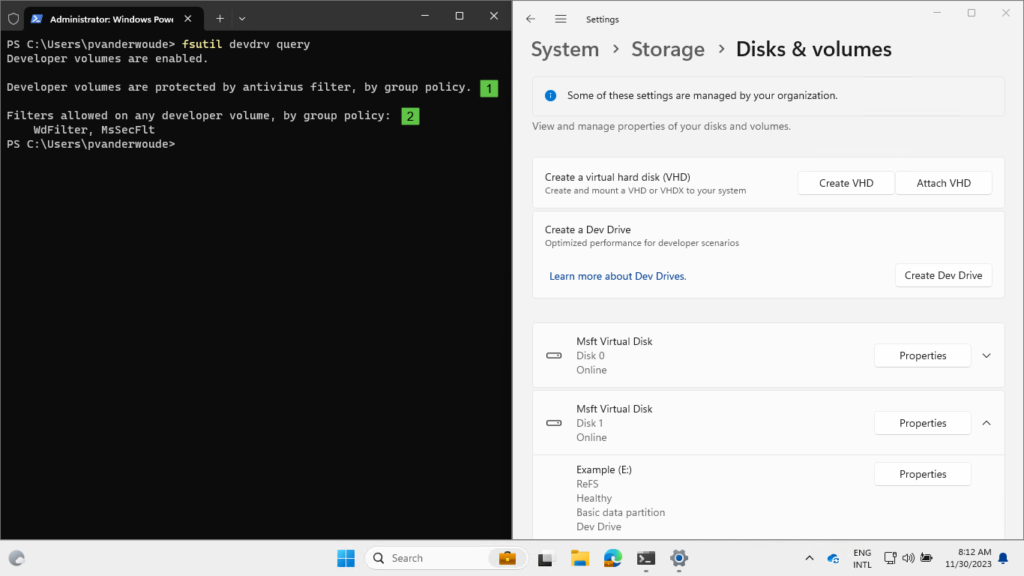
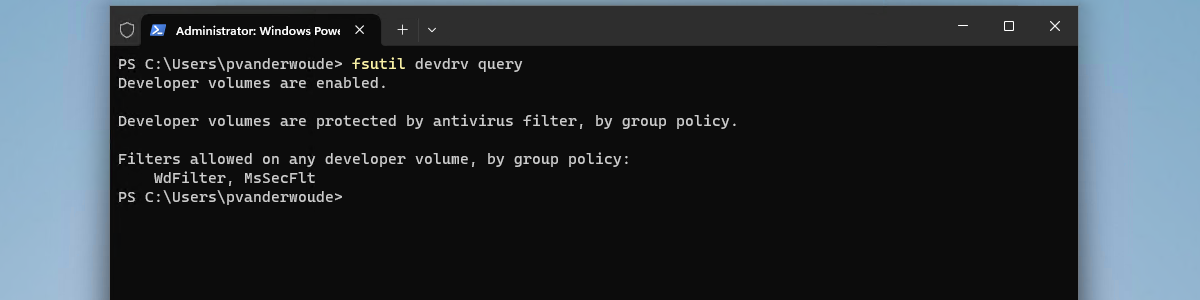
When looking at the applied configuration for Dev Drive, there are a few common places to look. The most obvious place is within the Settings app at the Disks & volumes section. When Dev Drive is enabled that section should provide the option Create Dev Drive. Another good place to look is fsutil. That tool can be used to query the disks and volumes, including the Dev Drive configuration. That provides an overview of the protection of the volumes with antivirus (1) and the allowed filters (2). Both of these should match the applied configuration.
More information
For more information about Dev Drive on Windows 11, refer to the following docs.
- Dev Drive for Performance Improvements in Visual Studio and Dev Boxes! – Visual Studio Blog (microsoft.com)
- Set up a Dev Drive on Windows 11 | Microsoft Learn
- Configure Dev Drive policy for enterprise business devices | Microsoft Learn
- Protect Dev Drive using performance mode | Microsoft Learn
- FileSystem Policy CSP – Windows Client Management | Microsoft Learn
- Resilient File System (ReFS) overview | Microsoft Learn
Hi Peter, Thank you for the detailed post. As, Dev Drives are automatically designated as trusted flag. I couldnt find any in Intune, Is there any policy to enforce disabling the the performance mode (asynchronous mode) for Dev Drive.
Hi!,
I haven’t tried it yet, but this setting should do just that: https://learn.microsoft.com/en-us/windows/client-management/mdm/defender-csp#configurationperformancemodestatus
Regards, Peter