This week is all about multi-app kiosk mode on Windows 11 devices. Kiosk mode on itself is nothing new, nor is the configuration of kiosk mode. However, until a few months ago, it was not possible to configure multi-app kiosk mode on Windows 11. That’s possible now, except the configuration options via Microsoft Intune are not that straight forward yet. As in, it’s not available via a standardized configuration profile yet. It is, however, already possible to configure multi-app kiosk mode via the MDM WMI Bridge Provider. That provider relies on configuration capabilities within the MDM channel, which means that the configuration can also be achieved directly via Microsoft Intune. Multi-app kiosk mode relies on assigned access to run one or more apps from the desktop. This blog post will mainly focus on applying the multi-app kiosk mode on Windows 11 devices, by using Microsoft Intune. Besides that, it will describe the main configurations for creating the multi-app kiosk mode configuration. This post will end by showing the user experience with the applied multi-app kiosk mode configuration.
Note: The configuration option described in this post, relies on a custom configuration XML-file. That provides a lot of flexibility, but also relies on some more detailed knowledge. Make sure to be familiar with the required technology.
Creating the custom multi-app kiosk mode configuration
When looking at configuring multi-app kiosk mode, by relying on a custom configuration, it starts with the creation of the XML-file that describes the configuration. That XML-file can be used to apply the multi-app kiosk mode on Windows 11 devices. The configuration of that XML-file is still pretty similar to what it was for Windows 10. Just with some minor tweaks. The basic structure of the XML-file contains basically two sections. The first section is the profiles section, which contains a unique profile id and describes the applications that are allowed to run, the Start layout configuration, and the taskbar configuration. There can be multiple profiles within that section, each with their own unique profile id. Besides that, there is the config section. That section associates a non-admin user account to a profile. There can also be multiple configurations within that section. All focused on connecting a profile to an account. Now let’s briefly walk through the those different sections in a bit more detail.
Profile id
The first section, within the profiles section, is the profile id section. That id is a GUID that is used to uniquely identify the profile. That GUID just needs to be unique within the XML-file. Within that section the configuration that belongs to that id is described. Any additional profile requires their own unique id. Below is an example of the profile id section.
<Profiles>
<Profile Id="{9A2A490F-10F6-4764-974A-53B19E722C23}">
</Profile>
</Profiles>AllowedApps
The next section, within the profile section, is actually the AllAppList section. That section, however, only contains the AllowedApps section. The AllowedApps section contains the apps that are allowed to run on the device. By default, the multi-app kiosk mode configuration applies AppLocker configurations to only allow the specified apps. That can be both, UWP apps and desktop apps. Below is an example of the AllowedApps section that contains Calculator, Notepad, Paint, Photos, and Settings.
<AllAppsList>
<AllowedApps>
<App AppUserModelId="Microsoft.WindowsCalculator_8wekyb3d8bbwe!App" />
<App AppUserModelId="Microsoft.WindowsNotepad_8wekyb3d8bbwe!App" />
<App AppUserModelId="Microsoft.Paint_8wekyb3d8bbwe!App" />
<App AppUserModelId="Microsoft.Windows.Photos_8wekyb3d8bbwe!App" />
<App AppUserModelId="windows.immersivecontrolpanel_cw5n1h2txyewy!microsoft.windows.immersivecontrolpanel" />
</AllowedApps>
</AllAppsList> Note: When allowing the Settings app, make sure to scope the available functionality to only what’s really needed.
StartPins
The next section, within the profile section, is the StartPins section. That section configures the apps that should be pinned to the Start layout. This section should be in line with the previous section. Mainly because apps in the Start layout must be allowed to run, for the user to be able to start those apps. Below is an example of the StartPins section that also contains Calculator, Notepad, Paint, Photos, and Settings.
<win11:StartPins>
<![CDATA[
{ "pinnedList":[
{"packagedAppId":"Microsoft.WindowsCalculator_8wekyb3d8bbwe!App"},
{"packagedAppId":"Microsoft.WindowsNotepad_8wekyb3d8bbwe!App"},
{"packagedAppId":"Microsoft.Paint_8wekyb3d8bbwe!App"},
{"packagedAppId":"Microsoft.Windows.Photos_8wekyb3d8bbwe!App"},
{"packagedAppId":"windows.immersivecontrolpanel_cw5n1h2txyewy!microsoft.windows.immersivecontrolpanel"}
] }
]]>
</win11:StartPins>ShowTaskbar
The last section, within the profile section, is the ShowTaskbar section. That section configures whether the taskbar should be visible. Below is an example of the ShowTaskbar section that configures the taskbar as visible.
<Taskbar ShowTaskbar="true"/>Note: Besides this it’s now also possible to add a TaskbarLayout section to pin specific apps to the taskbar.
Config
The config section connects a profile to a user account. That account can actually be a group or an individual account. In both cases that can be something local, something from Active Directory, or something from Entra ID. Besides that, it can also be used to configure an auto logon account. Below is an example of the Config section that connects the user MultiAppKioskUser to the created profile.
<Config>
<Account>MultiAppKioskUser</Account>
<DefaultProfile Id="{9A2A490F-10F6-4764-974A-53B19E722C23}"/>
</Config>Important: When using a local account that account must already exist before applying the configuration.
Note: Keep in mind that a profile has no effect when it’s not associated to an account in the config section.
Complete configuration overview
Putting all the different sections together, brings the complete picture of the multi-app kiosk mode configuration. Below is an example that brings all the pieces together that are briefly described in this post.
<?xml version="1.0" encoding="utf-8" ?>
<AssignedAccessConfiguration
xmlns="http://schemas.microsoft.com/AssignedAccess/2017/config" xmlns:win11="http://schemas.microsoft.com/AssignedAccess/2022/config">
<Profiles>
<Profile Id="{9A2A490F-10F6-4764-974A-53B19E722C23}">
<AllAppsList>
<AllowedApps>
<App AppUserModelId="Microsoft.WindowsCalculator_8wekyb3d8bbwe!App" />
<App AppUserModelId="Microsoft.WindowsNotepad_8wekyb3d8bbwe!App" />
<App AppUserModelId="Microsoft.Paint_8wekyb3d8bbwe!App" />
<App AppUserModelId="Microsoft.Windows.Photos_8wekyb3d8bbwe!App" />
<App AppUserModelId="windows.immersivecontrolpanel_cw5n1h2txyewy!microsoft.windows.immersivecontrolpanel" />
</AllowedApps>
</AllAppsList>
<win11:StartPins>
<![CDATA[
{ "pinnedList":[
{"packagedAppId":"Microsoft.WindowsCalculator_8wekyb3d8bbwe!App"},
{"packagedAppId":"Microsoft.WindowsNotepad_8wekyb3d8bbwe!App"},
{"packagedAppId":"Microsoft.Paint_8wekyb3d8bbwe!App"},
{"packagedAppId":"Microsoft.Windows.Photos_8wekyb3d8bbwe!App"},
{"packagedAppId":"windows.immersivecontrolpanel_cw5n1h2txyewy!microsoft.windows.immersivecontrolpanel"}
] }
]]>
</win11:StartPins>
<Taskbar ShowTaskbar="true"/>
</Profile>
</Profiles>
<Configs>
<Config>
<Account>MultiAppKioskUser</Account>
<DefaultProfile Id="{9A2A490F-10F6-4764-974A-53B19E722C23}"/>
</Config>
</Configs>
</AssignedAccessConfiguration>Applying multi-app kiosk mode configuration
When looking at applying the multi-app kiosk mode configuration, all roads point to the AssignedAccess CSP. That CSP can be used to configure a Windows device to run in (multi-app) kiosk mode. Once the CSP has been executed, the next user login that is associated with the (multi-app) kiosk mode puts the device into the specified kiosk mode. That CSP is the same that is also already used in the examples, provided by Microsoft, to configure the multi-app kiosk mode via the MDM WMI Bridge Provider. Within Microsoft Intune a Custom profile can be used to apply a custom multi-app kiosk mode configuration via the AssignedAccess CSP. The following nine steps walk through applying the custom multi-app kiosk mode configuration by using the configuration node of the AssignedAccess CSP.
- Open the Microsoft Intune admin center navigate to Devices > Windows > Configuration profiles
- On the Windows | Configuration profiles blade, click Create > New policy to open the Create a profile page
- On the Create a profile page, provide the following information and click Create
- Platform: Select Windows 10 and later as value
- Profile type: Select Templates as value
- Template name: Select Custom as value
- On the Basics page, provide a unique Name to distinguish the profile from other custom profiles and click Next
- On the Configuration settings page, as shown below in Figure 1, click Add to add rows for the following custom settings and click Next
- OMA-URI setting – This setting is used to configure multi-app kiosk mode on Windows 11
- Name (1): Provide a name for the OMA-URI setting to distinguish it from other similar settings
- Description (2): (Optional) Provide a description for the OMA-URI setting to further differentiate settings
- OMA-URI (3): Specify ./Vendor/MSFT/AssignedAccess/Configuration as value to configure multi-app kiosk mode
- Data type (4): Select String as value
- Value (5): Specify the created XML-file as value to set the required multi-app kiosk mode configuration
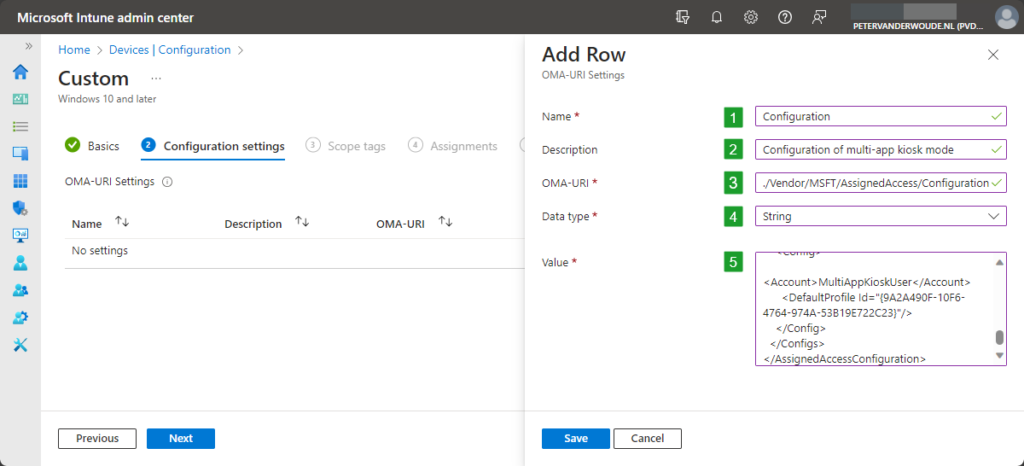
- On the Scope tags page, configure the applicable scopes and click Next
- On the Assignments page, configure the assignment and click Next
- On the Applicability rules page, configure the applicability rules and click Next
- On the Review + create page, verify the configuration and click Create
Note: At some point in time this setting might become directly available within Microsoft Intune.
Experiencing multi-app kiosk mode on Windows 11
When the configuration of the multi-app kiosk mode is applied, it’s relatively easy to very the configuration. Simply sign in with a user account that has the multi-kiosk mode configured and see what happens. In this case there are a few things that are easily visible within a screenshot. With the configuration created throughout this post a few obvious items are configured and shown below in Figure 2. That shows the user account that is used with number 1, the pinned items in the Start layout with number 2, and the available taskbar with number 3. Besides that, when testing this configuration also try starting apps that are not allowed. Simply to verify the assigned access that comes with the multi-app kiosk mode.
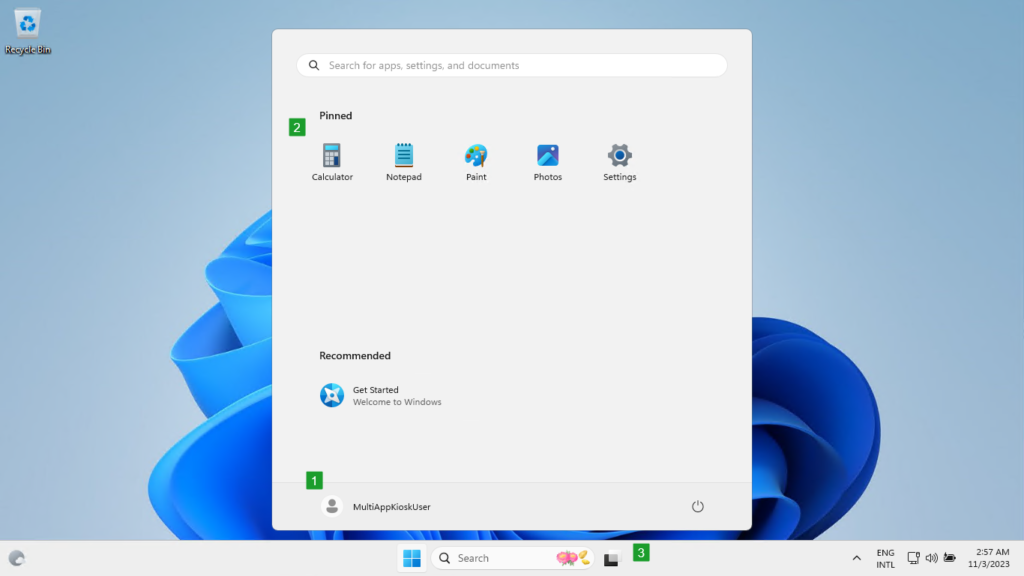
More information
For more information about multi-kiosk mode on Windows 11 devices, refer to the following docs.
- Set up a multi-app kiosk on Windows 11 – Configure Windows | Microsoft Learn
- Find the Application User Model ID of an installed app – Configure Windows | Microsoft Learn
- AssignedAccess CSP – Windows Client Management | Microsoft Learn
- Multi-app kiosk mode now available in Windows 11! – Microsoft Community Hub
hello, if we try for example an app, which ist running from userprofile – it will not work
i’ll get in eventlog of applocker following error => error 8004 => %OSDRIVE%\USERS\KIOSKUSER0\APPDATA\LOCAL\WEBEX\CISCOWEBEXSTART.EXE blocked
Hi David,
I haven’t had to deal with those type of apps yet. Can you provide an example of the allowed section of your configuration?
Regards, Peter
I think the Comment system removed your formatted reply. You could try using the contact form.
Regards, Peter
Great article, Peter! Have you ever tried to assign apps in kiosk-mode, which require a username in the app path, such as “%OSDRIVE%\USERS\*\APPDATA\LOCAL\Webex\WebexHost.exe”? Thanks, Klaus
Hi Klaus,
I haven’t had to deal with those type of apps yet. Can you provide an example of the allowed section of your configuration?
Regards, Peter
Never works for me in intunes, all the rest code works just fine if i exclude “start pins”
my current code:
Kiosk111
Hi Min,
Can you provide some more details about what’s not working for you?
Regards, Peter
Hi,
Great article, but what is the best way to create a local user on those kiosk systems.
By using an remediation script or someting else?
Gr,
Nico
Hi Nico,
What ever fits your scenario the best. That can be via the CSP (but that often still requires additional scripting), or directly via script.
Regards, Peter
Hey,
After pushing the exact XML to a Windows 11 device the configurations shows as “error” in Intune with an error code “0x87d1fde8”.
Any idea as to why this could be happening? I’m using your exact configuration.
Hi Dancr,
Make sure that the quotes are all correctly formatted, as that’s often the problem with copy-paste.
Regards, Peter
I did this and it worked for me, however it shows option for All Apps which user can easily go to select other Apps. It also shows Apps shortcut installed on Desktop.
Actually what I want to achieve is a single app and not multi app. I have used this code below but not sure about the OMA-URI
Test
Two questions,
– is this xml the correct format for kiosk mode?
– what will be the OMA-URI in this instance?
Thanks very much for your help
Hi Dave,
You can use the available Kiosk profile for that in Intune. Just as for Windows 10.
Regards, Peter
Hi Peter,
Thanks for this but I am unable to get it working even with your xml. I have entered the quotations manually just incase I have the copy issue. But I am still unable to get this working.
Error code is:
-2016281112
Any ideas?
Hi Aran,
That often implies that something is wrong with the XML. You could check locally on the device for some more details.
Regards, Peter
Hi Peter,
Thanks for the article!
I’m just wondering if it’s possible to have the allowed apps using a tiled layout like in the Windows 10 kiosk? As I’m not a fan of the pinned list.
Win10 code looks like the below.
Also, how do we allow USB and access to the downloads folder, is it still like the below?
Thanks!
Hi Shawn,
The Windows 11 multi-app kiosk mode no longer leverages the Tablet UI that was used on Windows 10.
Regards, Peter
Hi Peter,
I’ve tried to implement a kiosk profile with your configuration but I keep getting error codes in intune:
ERROR CODE
0x87d1fde8
SETTING
Configuration [./Vendor/MSFT/AssignedAccess/Configuration]
STATE
Error
Perhaps I need to change something within the XML file.
Can you help me?
Hi Aflew,
I would expect something to be wrong with the XML. Did you copy-paste it from my blog? If so, you might want to check the formatting of the quotes.
Regards, Peter
I did copy and paste from your blog and got the same error.
MultiAppKioskUser
Hi Brandon,
I don’t see any error, but as you’re referencing that account; is that account already available on that device?
Regards, Peter
Hi Peter,
Thank you for the blog, it was very useful. Perhaps a small add-on: the requirement of Windows 11 version 22H2. It took me a while before I figured out why my policy didn’t apply and this was because my test device was still on 21H2.
https://learn.microsoft.com/en-us/windows/client-management/mdm/assignedaccess-csp#configuration
Regards
Bjorn
You are absolutely correct, Bjorn
Regards, Peter
Hi Peter,
The recycle bin being on the desktop is a hole for the non-admin kiosk user to be able to interact with the filesystem. Even though file explorer is not put in the AllowedApps section, it can still be opened and interacted with. Microsoft Edge is another example of an application somehow being allowed while not being included in the AllowedApps section of the XML.
This was not the case in Windows 10. Is this normal behavior?
I can see in Microsoft’s documentation:
“Here are the predefined assigned access AppLocker rules for desktop apps:
Default rule is to allow all users to launch the desktop programs signed with Microsoft Certificate in order for the system to boot and function. The rule also allows the admin user group to launch all desktop programs.
https://learn.microsoft.com/en-us/windows/configuration/lock-down-windows-11-to-specific-apps#create-the-xml-file
How would forcing these to run in a kiosk be a desired feature? Isn’t the point of a kiosk to whitelist what applications can be run? I sincerely hope Microsoft doesn’t think Edge is necessary to “boot and function”.
Hi Mitch,
I only know that there were some design changes indeed and I can imagine that Edge is now often integrated with many sign-in experiences etc. Besides that, I can’t say a lot about why it is the way it is..
Regards, Peter
good article thanks, I’ve noticed that even though we apply what seem to be the correct power settings our kiosks, sleep – which is annoying. we have tried all sorts – have you seen this issue?
Hi David,
No, I can’t say that I have seen that behavior. Can you provide some more details about your configuration?
Regards, Peter
Hi Peter,
Again a very interesting article. What do you advice on recommended deployment method and what intune license
Only self deploying with a device license?
Since the login user isnt AAD aware?
regards,
Tom
Hi Tom,
It really depends on the specific use case, but often when there is no user account involved it makes sense to look at device licenses.
Regards, Peter
Hoi Peter,
Bedankt voor je uitleg, alleen als ik het probeer op mijn Windows 11 23H2 dan krijg ik in intune te zien:
AssignedAccessConfigurationRS5 – conflict
Hi Chris,
Do you have any other kiosk configurations applied to that device? A conflict usually means that there are conflicting policies applied.
Regards, Peter
I know that this is all intune based but wanted to test randomly on a singular machine, I have 2 issues one is if you have a local account which yourself and microsoft both say can be used how would I get the profile ID or would I use the SID from the whoami. Secondly if you use the WMI bridge powershell where would be best location for the xml.
As I say know it’s mostly intune based – I’m just seeing if I can workaround for a few standalone machines.
Hi Eugnene,
The profile ID is a GUID that you can generate yourself and use within your configuration.
Regards, Peter
Hello Peter,
I was wondering if it’s possible to deploy a win32-app to a KIOSK-pc? or can you push a powershell-script to a kiosk pc via Intune?
What I need to do is to put a certificate in the personal -store of the auto-logged-on user to make a website work.
Thx
Hi Lieven,
Yes, you can deploy apps and scripts to those devices. Just keep in mind that it by default will run in SYSTEM-context.
Regards, Peter
You have any more information on why they got rid of the tablet ui? The changes makes kiosk look worse on Windows 11 + now we have to do this XML manually instead of right from the GUI. Don’t understand why Microsoft would do this.
No, I don’t have information on why they’ve made these changes. I wish I did.
Regards, Peter
I have tried the above XML, and the profile is failing from Intune. I am testing this on a Microsoft Surface Pro 9, which we want to roll out. Any idea why the profile is failing?
Error code -2016281112
Hi Andy,
Make sure that the quotes are all correctly formatted, as that’s often the problem with copy-paste.
Regards, Peter
Hi Peter,
I wish to publish the System app so the users can manually set the display-settings to Duplicate. You mention to make sure to scope the available functionality to only what’s really needed. However, is it possible to do this within the XML, or will I have to configure this by Configuration Profile? Because I don’t think it’s possible to set anything in regard to Display Settings in that way.
Thanks!
Hi Rik,
If that’s the only thing that the user is allowed to do, you can limit the experience in the Settings app to just that specific option.
Regards, Peter
Hi!
Thanks for a great article.
We are trying to add a part in the script where the account is deleted after use.
To you have any suggestion? We have tried this code but get error code 0x87d101f4
Setting #2:
Name: “Add to Guests”
Description: “Adds the kioskUser0 to the Guests group.”
OMA-URI: “./Device/Vendor/MSFT/Policy/Config/LocalUsersAndGroups/Configure”
Data Type: String (XML File)
Hi Julia,
I think part of the script fell out of the comment. Can you try again or sent it via email (using the Contact form).
Regards, Peter
Here it is:
Hi Julia,
I’m afraid the content is being filtered. Can you try the Contact form?
Regards, Peter
Hi Peter:
Very helpful article. Do you know how we can hide or disable the recycle bin in Kiosk mode. We’ve found that users are able to access the file system from the recycle bin as another user noted and we need to prevent that.
Thanks.
Hi Michael,
That setting is Remove Recycle Bin icon from desktop, if I’m not mistaken. That is not specific to kiosk mode, but does the job.
Regards, Peter
Hi, but how Can you deploy a user policy to an kiosk local user account? I have created the local user by your oma-uri manual.
Hi Joerke,
You can’t deploy a policy specifically to a local user. The only option would be to deploy it to the device, including that user.
Regards, Peter
I’ve used a setting from settings catalog which hides all the icons on the desktop and locks it. That way the experience is closer to the one had with win10
I’ve had to do this too, but I used a CSP to do that so it’s all in the same custom policy.
It’s a shame that it doesn’t work the same as Win10 and the MS documentation doesn’t state otherwise. According to the doc, Assigned Access should apply GPOs for things like hiding desktop icons and the task view button on the taskbar but it doesn’t work. I’ve had to add in half a dozen extras for disabling OneDrive sync, turning off co-pilot, restricting access to Docs/Downloads/Pictures, etc. The only issue is that as I’ve used the device scope it applies to all users, including admins, whereas Assigned Access settings would only be for non-admins.
Hi Matt, we’re having trouble with the same issues on win 11 multi app kiosk mode. Could you please post your settings for disabling all the extra features like taskbar, onedrive etc.? Was ist all through intune/admx?
Was anybody having the 0x87d1fde8 error able to fix that?
formatting and quote marks looks correct, I’ve just changed the user to kioskUser0 (existing as local user with no password on the client).
I’ve also tried the WMI bridge route by deploying the XML via powershell script, but despite the script seems to do fine the only thing happening is the autologon with the correct user, for the rest there’s no trace of multiapp kiosk settings.
Hi Max,
So, there are no typos in the configuration and the user already exists when the configuration is applied?
Regards, Peter
The error was apparently given by the AssignedAccessConfiguration tag on multiple lines, once I moved them on the same line it started to work
Thank you for the update, Max!
Regards, Peter
Still a great article Peter, and used your XML multiple times already! Now I’m dealing with an application that’s installed in the %localappdata%\Programs folder of the KioskUser0.
Application will not start, I think because it trows me an error that the %localappdata% location is not allowed to access.
Do you have a workarround for this? Would be great!
Regards, Michiel
Hi Michiel,
What are you trying to achieve for which user?
Regards, Peter
Thanks for this write up! I tried executing it but i must be doing something wrong. Here’s what i did:
1) Took your complete configuration and adjusted: ProfileID, Account, and DefaultProfileID
2) ProfileID & DefaultProfileID are both randomly generated and match
3) Account is the account name of the service account i want to use for this kiosk (not display name and not UPN)
I get an 0x87d1fde8 error in Intune and i’m wondering if you can suggest where i should look?
Hi Mike,
More details will be available in the Event Viewer. Is that account already available before applying the configuration?
Regards, Peter
Ok i’ll dig through the event viewer next time i try this. The account is indeed already available, its an Entra ID account, could that be why? does it have to be a local account?
Hi Mike,
In that case make sure that the notation is correct. It must be like AzureAD\{UPN}
Regards, Peter