This week is all about creating some additional awareness for the capability of assigning app protection policies and differentiating between the management state of the devices of the user. Since recently it’s possible to assign app protection policies to either Intune managed devices or unmanaged devices. This can help with differentiating between Intune managed devices and unmanaged (MAM only) devices. For example, have more strict data loss prevention configurations for MAM only devices compared to MDM managed devices. In this post I’ll show the available configuration followed by results from an administrator perspective.
Configuration
Let’s start by having a look at the available configuration options. I’ll do that by walking through the steps for creating and configuring an app protection policy. These steps are shown below, with an extra focus on the targeted app types (see step 3a and 3b). After the creation of the app protection policy, simply assign it the applicable user group.
| 1 | Open the Azure portal and navigate to Intune > Mobile apps > App protection policies; |
| 2 | On the Mobile apps – App protection policies blade, click Add a policy to open the Add a policy blade. Depending on the platform continue with step 3a, or step 3b; |
| 3a |
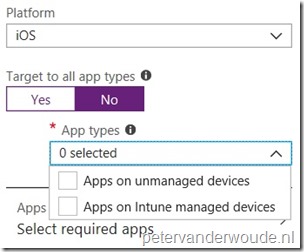
Note: This enables the administrator to differentiate between MAM only devices and MDM managed devices. |
| 3b | 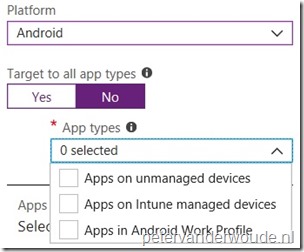
On the Add a policy blade, select Android as Platform and select No with Target to all app types. This enables the App types selection. In the App types selection choose between Apps on unmanaged devices, Apps on Intune managed devices and Apps in Android Work Profile; Note: This enables the administrator to differentiate between MAM only devices, MDM managed devices and MDM managed devices with Android Enterprise. |
| 4 | On the Add a policy blade, select Apps to open the Apps blade. On the Apps blade, select one or more apps from the list to associate them with the policy and click Select; |
| 5 | On the Add a policy blade, select Settings to open the Settings blade. On the Settings blade, configure the policy settings related to data relocation (data movement in and out apps) and access (access apps in work context) and click OK; |
| 6 | On the Add a policy blade, click Create; |
Note: This post is focused on iOS and Android devices, but for Windows 10 it’s also possible to differentiate between devices with enrollment and devices without enrollment.
Result
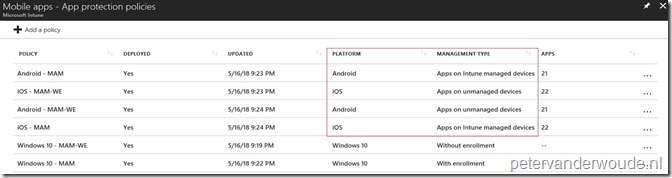
Now let’s end this post by looking at the results of the configuration. There are many things to look at, but it will be hard to show the difference in behavior via screenshots. That’s why an overview of my policies is the easiest way to show the difference in policies. Below is an overview of the different platforms and the different management types.
More information
For more information about app protection polices in combination with device management state, please refer to this article How to create and assign app protection policies – Target app protection policies based on device management state.
Hi Peter,
Is it required to set the MAM scope (under mdm/mobility) to users for this?
Hi RKast,
No. The MAM user scope is for Windows devices only.
Regards, Peter
Thanks!
How do you differentiate this for W10 ?
Cause the MAM/WIP scope is targeted on user.
A user can join azure ad so its mam with enrollment.
But a byod is not azure ad joined and when a user wants/needs to enroll for intune this is not possible because MAM/WIP is used over MDM.
So byod with enrollment is not possible anymore.
Hi RKast,
The differentiation for Windows 10 devices is indeed all about the enrollment. Once MAM is enabled for the user, the normal enrollment flow will prefer the MAM enrollment. Unless using a Azure AD join.
Regards, Peter
Thanks Peter.
Also the fact that home does not support wip is also a bit of a bummer.
And enrollment for Android is also a bit shaky.
This due to the fact that Android native is ‘EOL’ and the successor Android for Work creates two profiles on the device and all apps are double. A lot of customers get confused by this. The Android Device Owner is still not here after 5’ish months.
Sorry for this of track response 🙂
It’s hard being a Intune consultant sometimes 🙂
Hi RKast,
Being an Intune consultant makes sure you’ve got enough challenges.
Regards, Peter
Hi Peter,
Love the blog.A quick question about Intune App Protection Policy Targeting & unmanaged devices. I’d like to create a “catchall” App Protecion policy that would deliver an app protection policy for any/all users that would enter in their corp identity & creds to any MS apps. This way if they do do we have a DLP policy in effect.
Is there any way to target set and target a profile to all users by default.?This way I could:
1) have a default App Protection policy that would apply to all any/all users that don’t have a defined service level
2) Once a user subscribes to a proper service level, membership in the service delivery AAD group would exclude them for the default “catchall” policy & add them to the service specific one
Warmest regards,
M@
Hi Matt,
I could see something like that by using the include and exclude functionality. Include all users and exclude a specific group. That way the user will always be targeted, unless in that specific group.
Regards, Peter