This week my post is a few days later, as my post is an extension of my session at the Workplace Ninja Virtual Summit 2021. At the virtual summit I did a session about Why you might want to use corporate-owned devices with Work Profile. During that session I shared a summary about Android Enterprise and I zoomed in on the capabilities of corporate-owned devices with Work Profile. This post will provide a summary of that session about the different important components of Android Enterprise and how that integrates and works with Microsoft Intune, followed with a zoom-in on corporate-owned devices with Work Profile. Most of that information will be summarized in tables and slides. The slides (PDF) of that session are available for download here.
Android management APIs
The management of Android devices is done via a management API and a Device Policy Controller (DPC). The management API contains the different configurations options that can be enforced on Android devices via the DPC, which is basically the MDM agent. The following table provides an overview of the available management APIs for Android devices and the required DPC.
| Management API | Description |
|---|---|
| Device Administrator API | This is the legacy API that provides device administration features at a device level and allows organizations to create security-aware apps with elevated administrative permissions on the device. Can be any app. |
| Google Play EMM API | This is the initial API for Android Enterprise can be used to configure different enhanced policy settings for the managed devices and the custom DPC automatically enforces those policy settings on the device. |
| Android Management API | This preferred API for Android Enterprise can be used to configure different enhanced policy settings for the managed devices and the required standard DPC automatically enforces those policy settings on the device. |
Device Policy Controller management reach
The management reach of the DPC on an Android device, is related to the deployment scenario, and determines the level of control on the device. The following table provides an overview of the different levels of management reach of the DPC.
| Management reach | Description |
|---|---|
| Device owner | The DPC has permissions on the complete device |
| Profile owner | The DPC has only permissions within the Work Profile |
| Enhance profile owner | The DPC has permissions within the Work Profile and some device security policies |
Android Enterprise enrollment methods
The enrollment of Android devices can be achieved via different methods. The following table provides an overview of the different enrollment methods for Android Enterprise devices.
| Enrollment method | Description |
|---|---|
| Near Field Communication (NFC) | Configure a new device by bumping an NFC tag |
| Token entry | Configure a new device by entering afw#setup as token |
| QR code | Configure a new device from the setup wizard by scanning a QR code |
| Android Zero Touch | Configure a new device automatically by going through the out-of-box-experience |
| Samsung Knox Mobile Enrollment (KME) | Configure a new device automatically by going through the out-of-box-experience |
Android Enteprise deployment scenarios
Android Enterprise provides a few different deployment scenarios, that all serve their own purpose. Below is a quick summary.
- Personally-owned device with Work Profile – Personally-owned devices with Work Profile are supported with Android 5.0 and later in Microsoft Intune and are focused on providing access to company data on personal devices by using profile owner mode. In this scenario, the user enrolls the device and after enrollment a separate work profile is created on the device. This separate profile creates the separation between company data and personal data and can be easily identified by the user. The apps that are part of the work profile are marked with a briefcase icon and the company data is protected and contained within the work profile. If needed, the IT administrator can remove the work profile from the device. For managing the device the Company Portal app is used as the DPC and the Google Play EMM API is used as management API.
- Corporate-owned fully managed device – Corporate-owned fully managed devices – previously known as corporate-owned, business-only (COBO) – are supported with Android 6.0 and later in Microsoft Intune and are focused on providing corporate-owned devices, used by a single user exclusively for work, by using a device owner mode. In this scenario, these devices are enrolled via one of the mentioned enrollment methods and the devices are fully managed by the IT organization. To give the user a personal touch, the IT administrator can allow the user to add a personal account for the installation of apps from the Google Play store. However, the device will remain fully managed and there will be no differentiation between company data and personal data. If needed, the IT administrator can remove all (company) data of the device. For managing the device, the Android Device Policy app is used as the DPC and the Android Management API is used as management API.
- Corporate-owned dedicated device – Corporate-owned dedicated devices – previously known as corporate-owned, single-use (COSU) – are supported with Android 6.0 and later in Microsoft Intune and are focused on providing single purpose company-owned devices by using a device owner mode. This is often used for kiosk-style devices (example: devices used for inventory management in a supermarket). In this scenario, these devices are enrolled via one of the mentioned enrollment methods and locked down to a limited set of apps and web links, all related to the single purpose of the device. These devices are not associated with any specific user and are also not intended for user specific applications (example: email app). If needed, the IT administrator can remove any (company) data of the device. For managing the device, the Android Device Policy app is used as the DPC and the Android Management API is used as management API.
- Corporate-owned device with Work Profile – Corporate-owned devices with work profile – previously known as corporate-owned, personally-enabled (COPE) – are supported with Android 8.0 and later in Microsoft Intune and is focused on providing privacy for the user on corporate-owned devices by using an enhanced profile owner mode. In this scenario, these devices are enrolled via one of the mentioned enrollments methods as a corporate-owned devices and configured with a separate personal and work profile. That profile separation creates the separation between personal and work data and can be easily identified by the user. The apps that are part of the work profile are marked with a briefcase icon and the work data is protected and contained within the work profile. That provides the user with the required privacy in the personal profile. If needed, the IT administrator can remove all data of the device. For managing the device, the Android Device Policy app is used as the DPC and the Android Management API is used as management API.
The table below (Figure 2) provides an overview of the main properties of the different Android Enterprise deployment scenarios.
Android Enterprise corporate-owned devices with Work Profile
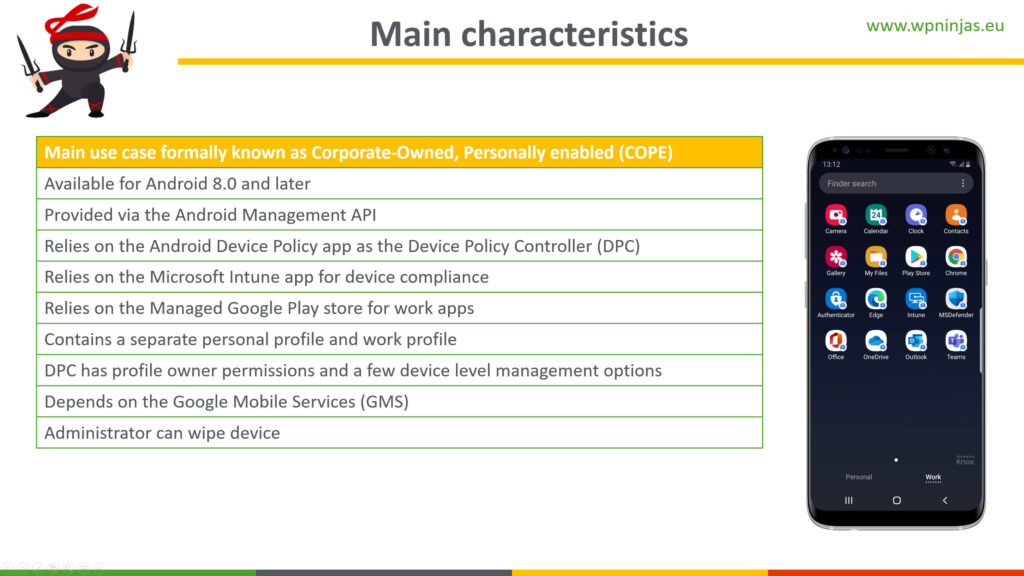
When looking at corporate-owned devices with Work Profile in a bit more detail, it’s good to start with some characteristics. These characteristics describe the main requirements, the permissions of the DPC, the used management API, the used managements apps and are summarized below (Figure 3).
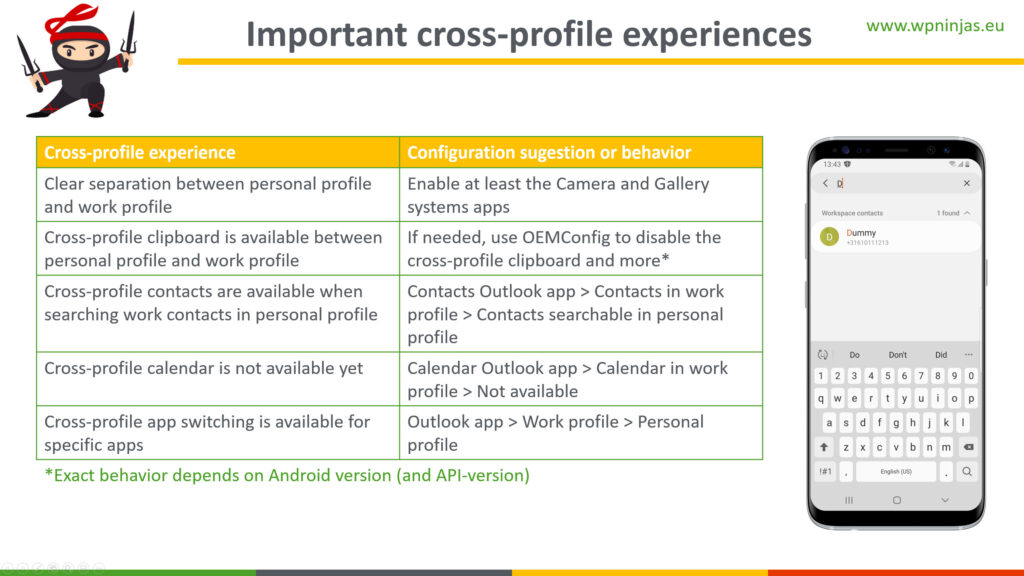
Besides those characteristics it’s also good to be familiar with the cross-profile experiences. The behavior of actions between the personal profile and the work profile. The most important experiences are summarized below (Figure 4) and sometimes even differ from the on personally-owned devices.
More information
The summaries in this post and the information provided during the session are based on experience and previous posts. For future reference those posts are summarized below.