This week is all around an Azure AD functionality that tightly integrates with Conditional Access (CA) and that provides a near real time experience with enforcing access to resources and applications. That functionality is Continuous Access Evaluation (CAE). CAE was introduced almost a year ago to Azure AD tenants with CA enabled and provides that near real time experience. That experience is created by enabling a communication between the different Microsoft services and Azure AD. That communication provides a lot of magic that results in the new real time experience. This post starts with a quick introduction in CAE, followed with the steps to enables this functionality (while in preview). This post ends with showing the near real time user experience.
Important: At the moment of writing this, CAE is still preview functionality.
Introduction to Continuous Access Evaluation
When introducing CAE, it’s good to first do a little step back. That step back is by looking at the industry standards and protocols that are being used by Microsoft services to maximize interoperability. Important for CAE is the usage of OpenID Connect (OIDC) for authentication and OAuth 2.0 for authorization. When connecting to a Microsoft service, the API requests are authorized by using an OAuth 2.0 access token. That token is by default valid for one hour. When that token expires, the session is redirected back to Azure AD to refresh the token. That refresh moment is also the moment to re-evaluate any (CA) policies for user access and to potentially determine not to refresh the token. A nice mechanism, conform existing industry standards and protocols. It does, however, provide a relatively long window in which something could happen.
That’s were CAE comes in to the picture. To make it a great mechanism. CAE is based on the Continuous Access Evaluation Protocol (CAEP) initiative, as part of the Shared Signals and Events working group at the OpenID Foundation, and enables Azure AD (as the token issuer) and a Microsoft service (as the relying party) to have a two-way conversation. That enables the Microsoft service to notice if something changed and to inform Azure AD, and that enables Azure AD to tell the Microsoft service to stop respecting the access token. Together that means that the token lifetime becomes less important, as the Microsoft service can notice any changes. When looking at the implementation, there are two scenarios that make up CAE, being:
- Critical event evaluation: This scenario is implemented by enabling Microsoft services (like Exchange Online, SharePoint Online and Teams) to subscribe to critical events in Azure AD. That subscription enables those Microsoft services to evaluate the critical events near real time and to enforce behavior accordingly. There is a list of supported events available.
- CA policy evaluation: This scenario is implemented by enabling Microsoft services (like Exchange Online, SharePoint Online and Teams) to synchronize key CA policies. That synchronization enables those services to evaluate the policies within the service itself. There is a list of supported Microsoft services and apps available.
Note: For the list of supported critical events and the list of supported Microsoft services with apps, have a look at the docs here for the latest status.
The last thing that is good to mention is that CAE also requires clients to behave a little bit different. As a Microsoft service can now reject a token, even when it’s not expired, the client needs to be aware that it has to bypass the cache even though the cached tokens are not expired. That behavior is achieved with a mechanism called claim challenge and is available within the latest versions of the different client apps.
Preview configuration of Continuous Access Evaluation
Using CAE in an environment, currently requires a CAE-capable client app and a tenant that is enabled for CAE. When looking at the CAE-capable client app, the latest versions of the Outlook, Teams, Office and OneDrive apps that are available for web, win32, iOS, Android and Mac, are all CAE-capable, with exception of the Office web app. At the moment of writing this post, CAE is still preview functionality. While this functionality is in preview, it must be manually enabled for the tenant. After manually enabling CAE, the functionality will be immediately available. The following two steps walk through the required steps.
- Open the Azure portal and navigate to Azure Active Directory > Security > Continuous Access Evaluation
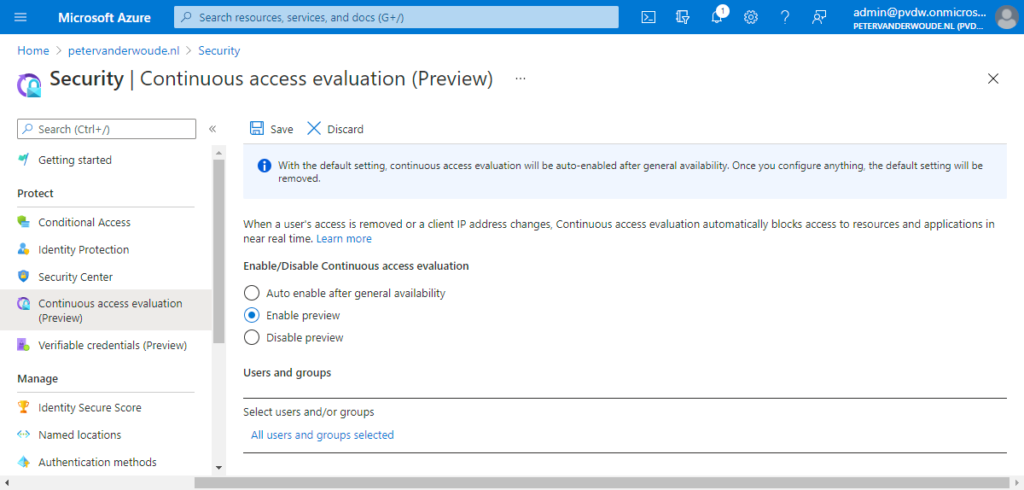
- On the Security | Continuous access evaluation page (as shown below in Figure 1), select Enable preview and assign the users and/or groups that should take advantage of CAE
Note: When this configuration is not touched within the tenant, the default configuration will be to auto enable the functionality after general availability. Once configured, the default configuration option will disappear.
User experience with Continuous Access Evaluation
There are many methods to look at the user experience for CAE. This example will look at the user experience with Outlook on the web, via Microsoft Edge, on an Android device. For a nice user experience – that can be easily shown in a GIF – a CA policy is configured that will require MFA when the user is accessing from an untrusted network.
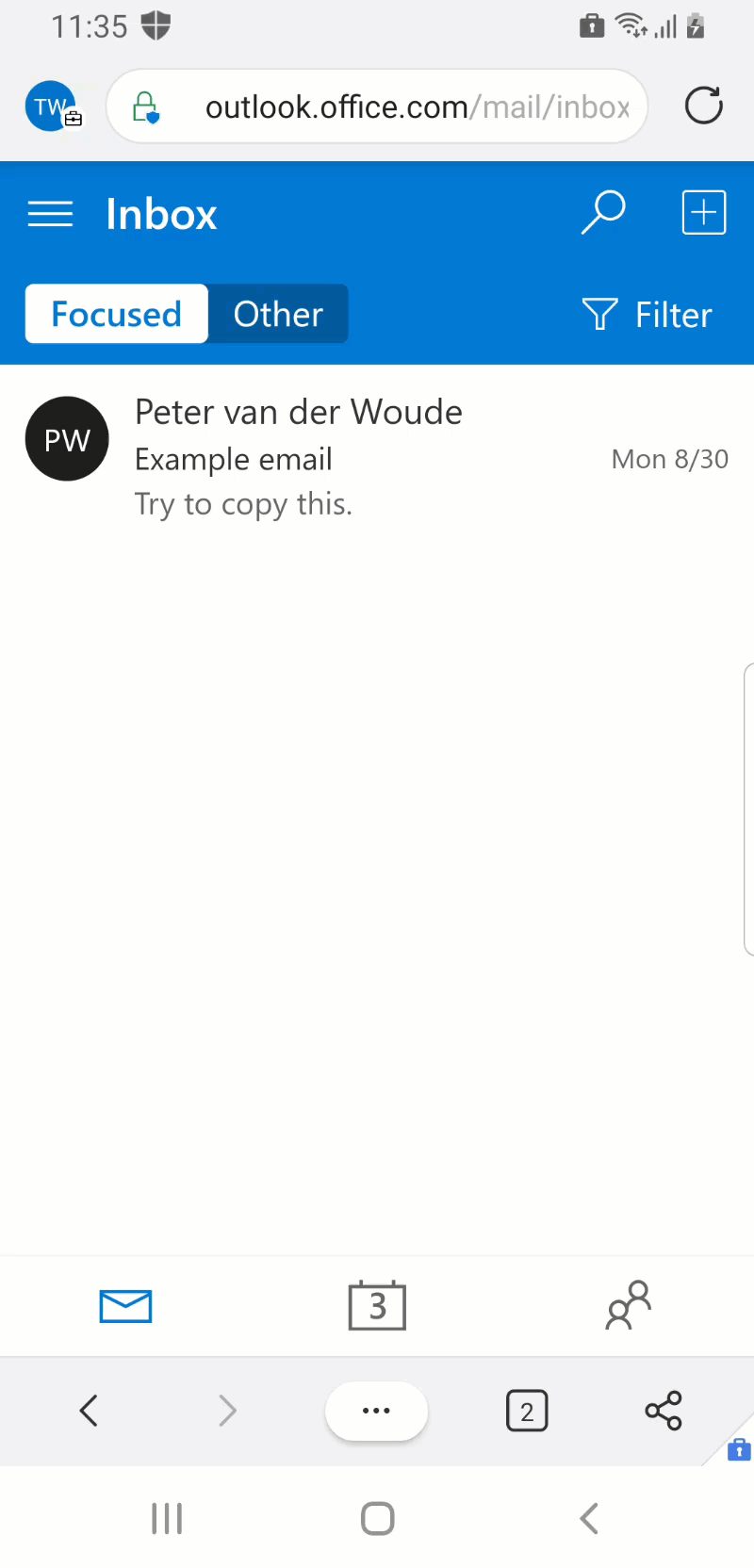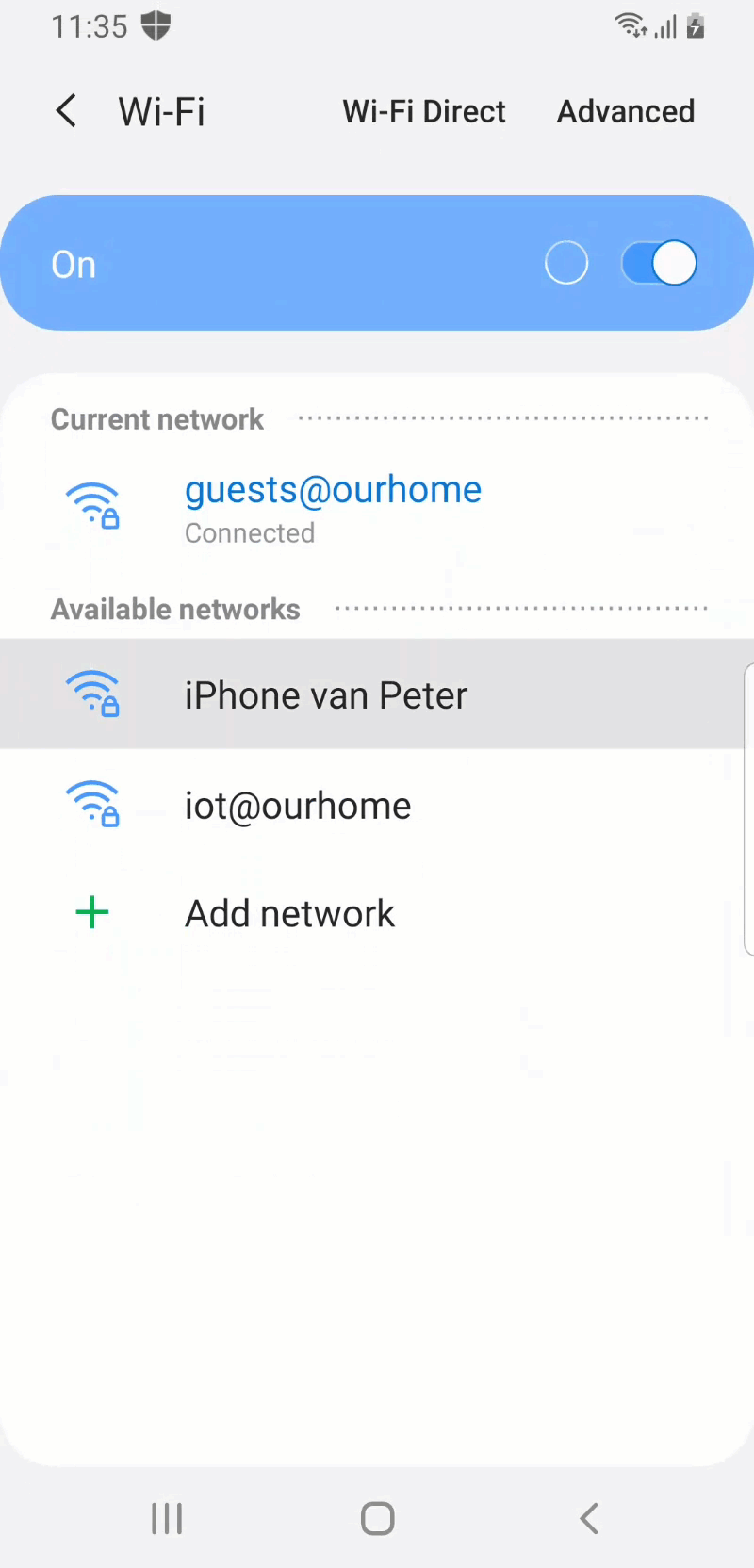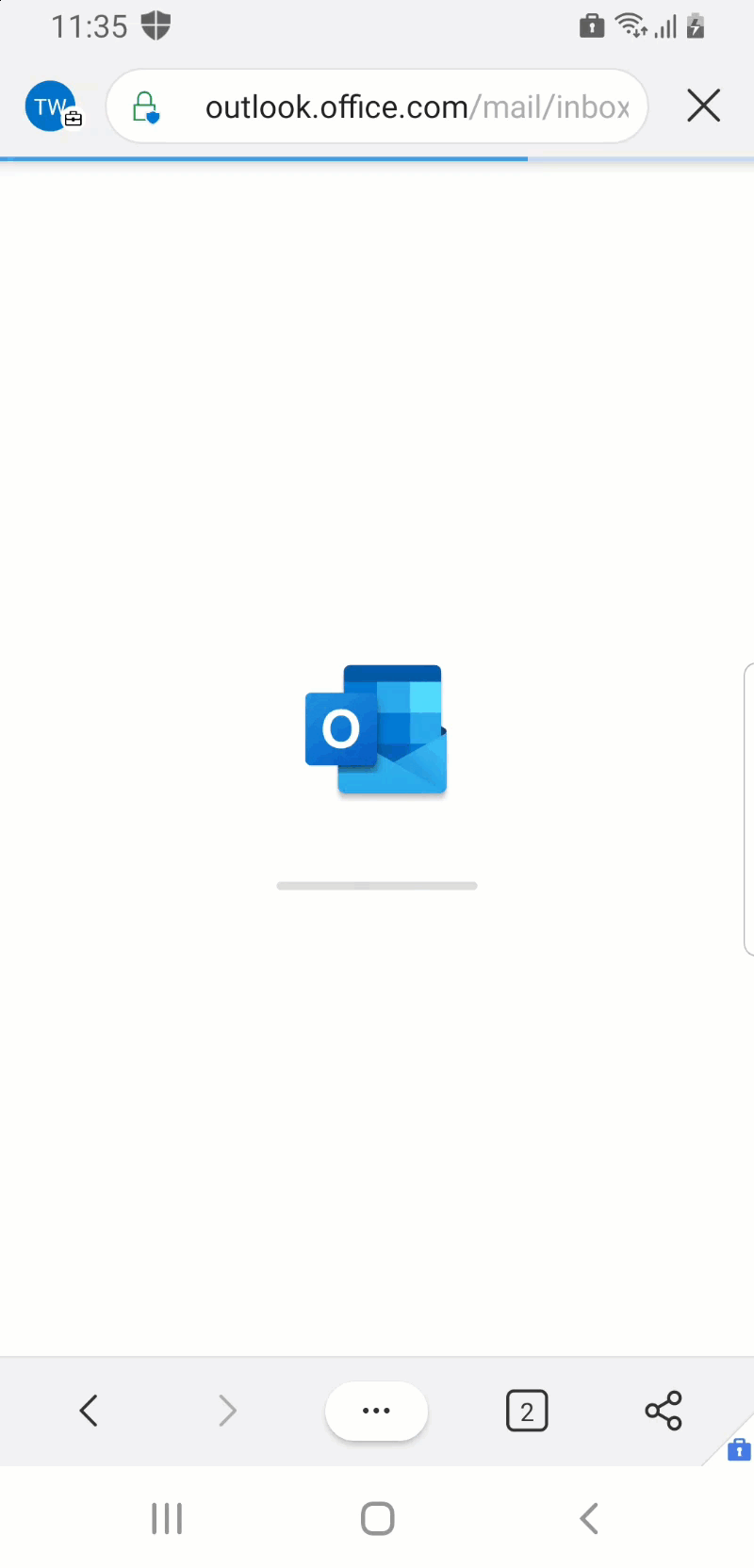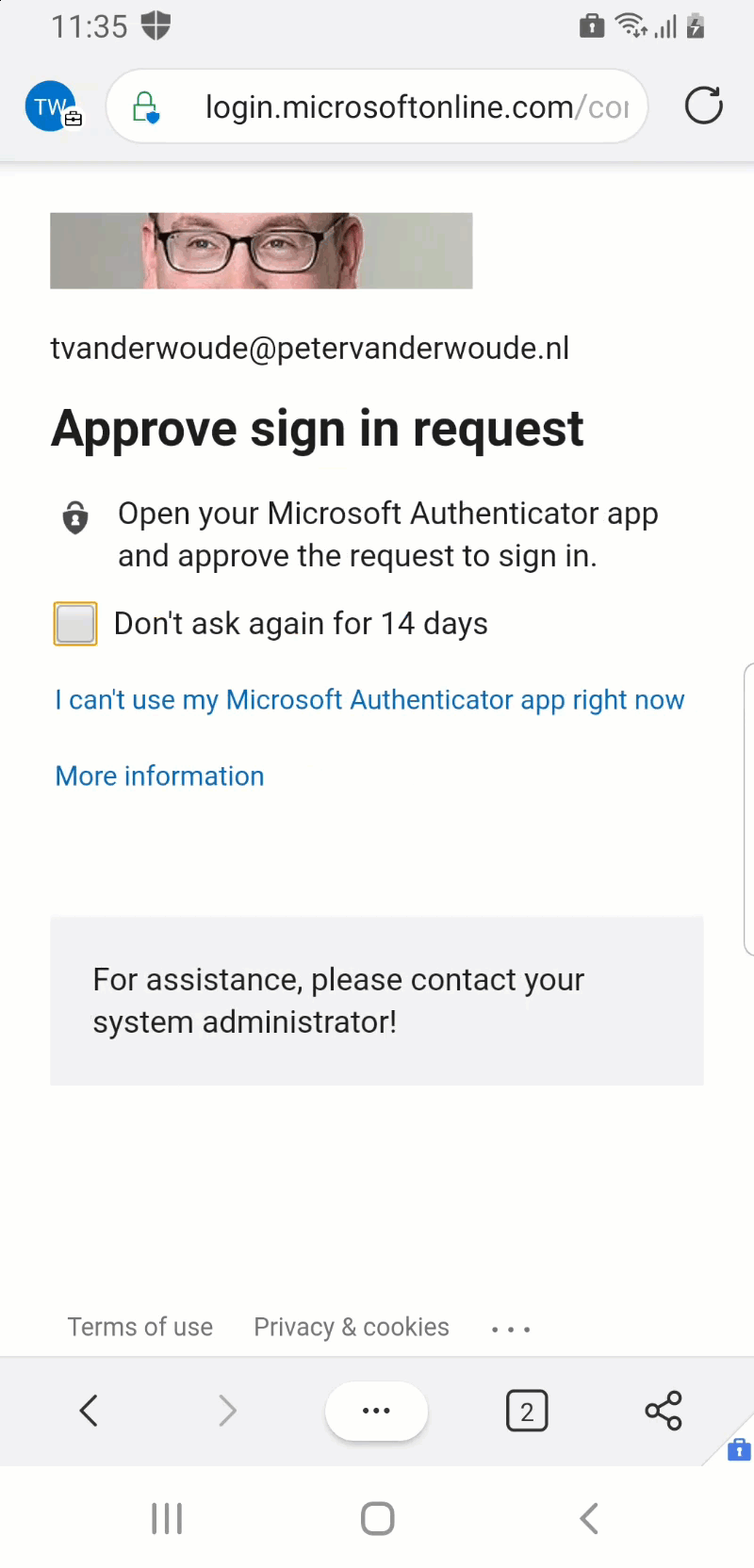
Figure 2 (on the right) provides a quick view on how quickly the user will be required to provide MFA after switching from network. In less than 30 seconds that examples goes through the following to show the behavior.
- The user is on the Wi-Fi network that is considered a trusted location
- The user has Microsoft Edge open on Outlook on the web
- The user has access and can sent and receive emails
- — Next – the user switches network —
- The user connects to a hotspot that is considered an untrusted location
- The user opens Microsoft Edge and navigates to Outlook on the web
- The user tries to refresh the email and is immediately prompted to approve the sign in request (MFA)
Together that example shows the near real time experience that is introduced with CAE, as something as simple as switching from location can immediately impact the behavior for the user.
More information
For more information about OpenID Connect and CAE, refer to the following docs.
Thank you for the explanation!
Can’t see the GIF/Figures under User Experience
Hi Sandeep,
I just checked and it’s just there. If it’s not working for you, here is the direct link: https://www.petervanderwoude.nl/post/getting-started-with-continuous-access-evaluation/#jp-carousel-15101
Regards, Peter