Managing security policies for Dev Drive
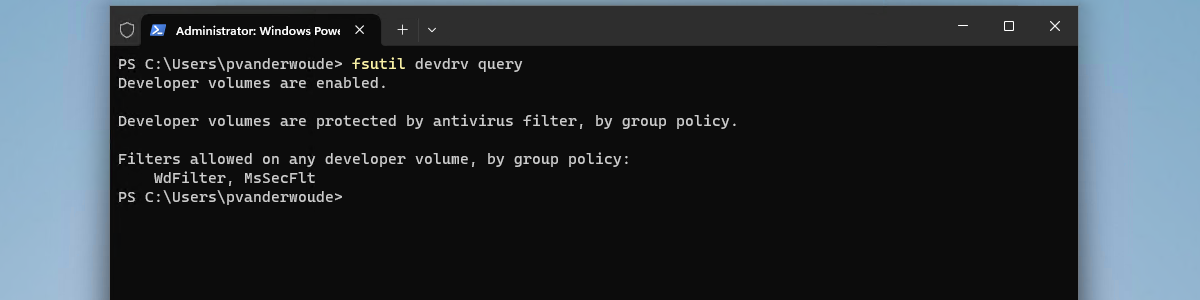
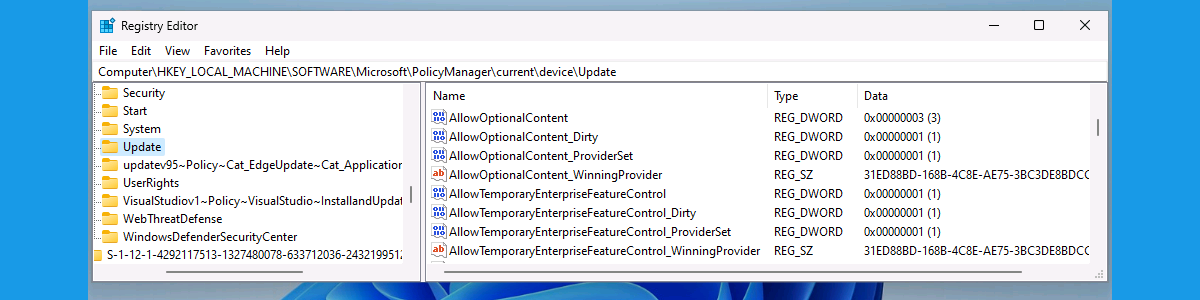
This week is all about another new Windows 11 features and that feature is Dev Drive. Dev Drive is a new form of a storage volume that is aimed at improving performance for key developer workloads. It enables users to create a separate volume on their device that will improve the performance for disk-bound operations such as cloning, building, copying files, and package restore. To gain that performance, Dev Drive builds on ReFS technology. That technology provides file system optimizations and more control over storage volume settings and security. That includes trust designation, antivirus configuration, and administrative control over what filters are attached. All of that, could also be a reason to make sure that some security-minded Dev Drive configurations are in place. To make sure …