This week is all about Smart App Control and Windows Defender Application Control (WDAC). Starting with Windows 11, version 22H2, Microsoft introduced Smart App Control for additional protection for consumers against threats by blocking apps that are malicious, untrusted, or potentially unwanted. Smart App Control is based on WDAC and works in a similar way. It provides basic protection rules that can also be reused within an enterprise environment. Smart App Control on itself is only available on a fresh installation of Windows 11, version 22H2, and not after an upgrade. On enterprise managed devices, Smart App Control is automatically turned off. That doesn’t mean, however, that Smart App Control doesn’t provide any useful standard configurations. Smart App Control can be an excellent starting point, as it includes most of the Microsoft recommended block rules that are well-suited for lightly managed devices. The best part of it is that Microsoft provides a WDAC example base policy that is based on Smart App Control. This post is all about using that base policy as the starting point for a WDAC policy. It starts by walking through the creation of the WDAC policy, followed with the steps to distribute the WDAC policy. This post ends with experiencing the applied WDAC policy.
Note: To actually use Smart App Control within an enterprise organization, the VerifiedAndReputablePolicyState registry value can be used that is available under HKLM\SYSTEM\CurrentControlSet\Control\CI\Policy.
Creating Windows Defender Application Control policy
When looking at distributing the WDAC policy, by using Microsoft Intune, it starts with constructing that policy. Those policies were formerly known as Code Integrity policies, and a lot in the configuration is still referring to Code Integrity, or CI. When getting back to the connection with Smart App Control, the latest versions of Windows 11, version 22H2, contains an example template for a WDAC policy that is based on Smart App Control. That example is named SmartAppControl.xml and is available in the folder %OSDrive%\Windows\schemas\CodeIntegrity\ExamplePolicies. With a few small adjustments that example policy can be used via Microsoft Intune. The first adjustment is the removal of the conditional Windows lockdown policy rule, as that is unsupported for enterprise WDAC policies. The removal of that rule, requires a manual action.
<Rule>
<Option>Enabled:Conditional Windows Lockdown Policy</Option>
</Rule>Besides that adjustment, it’s advised to make sure that the WDAC policy doesn’t require a restart during the enrollment of a Windows device in Microsoft Intune. That can be achieved by adding an additional rule option. Adding a new rule option can be achieved by using the Set-RuleOption cmdlet and is extensively described in this post.
Set-RuleOption -FilePath .\SmartAppControl.xml -Option 16Those were the most important adjustments to the example WDAC policy based on Smart App Control. After that, it’s a good practice to create a new policy ID for the WDAC policy. That can be achieved by using the Set-CIPolicyIdInfo cmdlet.
Set-CIPolicyIdInfo -FilePath .\SmartAppControl.xml -ResetPolicyIDThat generates a new policy ID that is required for constructing the OMA-URI setting in Microsoft Intune. After that, another good practice is to set a new version for the WDAC policy. That can be achieved by using the Set-CIPolicyVersion cmdlet.
Set-CIPolicyVersion -FilePath .\SmartAppControl.xml -Version "1.0.0.0"Converting Windows Defender Application Control policy
Before being able to distribute the WDAC policy, by using Microsoft Intune, it’s required to first convert the policy. To distribute the WDAC policy, it must be converted from a XML-file to a BIN-file. That can be achieved by using the ConverFrom-CIPolicy cmdlet. That cmdlet can be used to convert a Code Integrity policy, which basically is the WDAC policy, into a binary format. That binary version of the policy can be installed on Windows 10 and later devices and can be distributed via Microsoft Intune. Below is an example of how to convert the XML-file of the Smart App Control policy example.
ConvertFrom-CIPolicy -XmlFilePath .\SmartAppControl.xml -BinaryFilePath SmartAppControl.binDistributing Windows Defender Application Control policy
When looking at distributing the WDAC policy, by using Microsoft Intune, it’s a two steps process. The first step is to construct the OMA-URI setting and the second step is actually creating and assigning a custom device configuration policy.
Constructing OMA-URI setting for custom Windows Defender Application Control policy
The distribution of the custom Windows Defender Application Control policy can be achieved by using the ApplicationControl CSP. That CSP was added with Windows 10, version 1903, and provides extended diagnostics capabilities, support for multiple policies and it supports rebootless policy deployment. Within that CSP the following OMA-URI can be used for distributing custom WDAC policies: ./Vendor/MSFT/ApplicationControl/Policies/{PolicyID}/Policy. Within that OMA-URI, the PolicyID should be the PolicyID of the WDAC policy. That PolicyID is easily generated and provided after resetting the policy ID (third action of creating the WDAC policy). Below is an example of the constructed OMA-URI setting for the WDAC policy.
./Vendor/MSFT/ApplicationControl/Policies/eed0fbcc-b4c6-449c-a42c-20341d5f9021/PolicyCreating custom device configuration policy for Windows Defender Application Control policy
After constructing the OMA-URI setting, the next step is creating the custom device configuration policy for distributing the WDAC policy. The following nine steps walk through the process of creating that custom profile.
- Open Microsoft Endpoint Manager admin center navigate to Devices > Windows > Configuration profiles
- On the Windows | Configuration profiles blade, click Create profile
- On the Create a profile blade, provide the following information and click Create
- Platform: Select Windows 10 and later as the platform for the configuration profile
- Profile type: Select Templates as the profile type for the configuration profile
- Template name: Select Custom as the template name for the configuration profile
- On the Basics page, specify a valid Name and optionally a Description and click Next
- On the Configuration settings page, as shown below in Figure 1, click Add to add rows for the following custom settings and click Next
- OMA-URI setting 1 – This setting is used to apply the created binary file
- Name: Provide a name for the OMA-URI setting to distinguish it from other similar settings
- Description: (Optional) Provide a description for the OMA-URI setting to further differentiate settings
- OMA-URI: Specify /Vendor/MSFT/ApplicationControl/Policies/eed0fbcc-b4c6-449c-a42c-20341d5f9021/Policy
- Data type: Select Base64 (file) as data type of the configuration
- Value: Select the created binary file as the value of the configuration

- On the Scope tags page, configure the required scope tags click Next
- On the Assignments page, configure the required assignment and click Next
- On the Applicability rules page, configure the required applicability rules and click Next
- On the Review + create page, verify the configuration and click Create
Experiencing Windows Defender Application Control policy
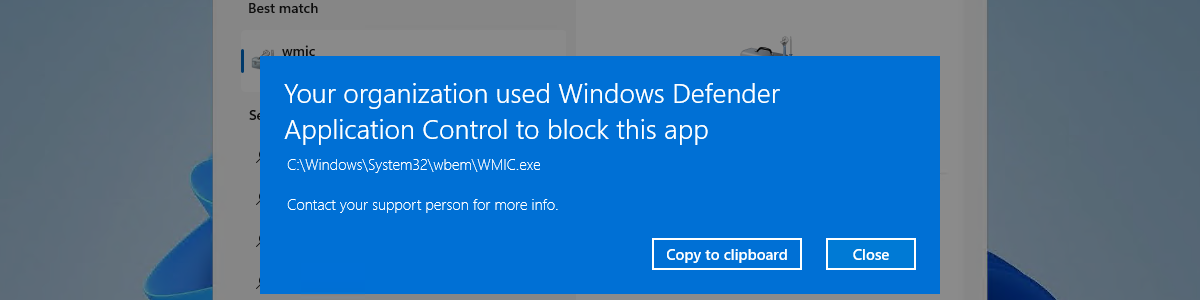
After distributing the WDAC policy, it’s good to have a look at the user experience. Once the WDAC policy is applied, experiencing the behavior is pretty straight forward. The device doesn’t request a reboot during the Windows Autopilot experience and when the users wants to start an app that doesn’t comply with the WDAC policy that action will be blocked. Below in Figure 2 is an example of a user that wants to start WMIC that is blocked by WDAC. By default, the Smart App Control configuration contains many tools and scripts that are denied.

More information
For more information about Smart App Control and Windows Defender for Application Control, refer to the following docs.
I have downloaded the latest ISO for Windows 11 and have checked through all the SKUs (Home, Education, Pro) in the WIM file, but none of them contain the SmartAppControl.xml policy template.
Do you know which edition of Windows this template can be obtained from? I am trying to test WDAC and would be interested to use this as a starting point for a base template.
Hi Steven,
I just checked a random device running Windows 11 Enterprise and the templates are available, as described and also documented here: https://learn.microsoft.com/en-us/windows/security/application-security/application-control/windows-defender-application-control/design/example-wdac-base-policies?WT.mc_id=EM-MVP-5001447
Regards, Peter
Hi Peter.
Thanks for responding. I have done a clean install on Windows 11 22H2 from the Microsoft installation media and do not get the SmartAppControl.xml file created as per the document.
If I am reading the information correctly https://learn.microsoft.com/en-us/windows/security/application-security/application-control/windows-defender-application-control/design/example-wdac-base-policies?WT.mc_id=EM-MVP-5001447 is the %ProgramFiles%\WindowsApps\Microsoft.WDAC.WDACWizard*\SignedReputable.xml included in the WDAC wizard the same as the SmartAppControl.xml file?
Hi Steven,
It indeed seems to be the same file (and configuration).
Regards, Peter