Getting started with Azure Monitor agent on Windows client devices
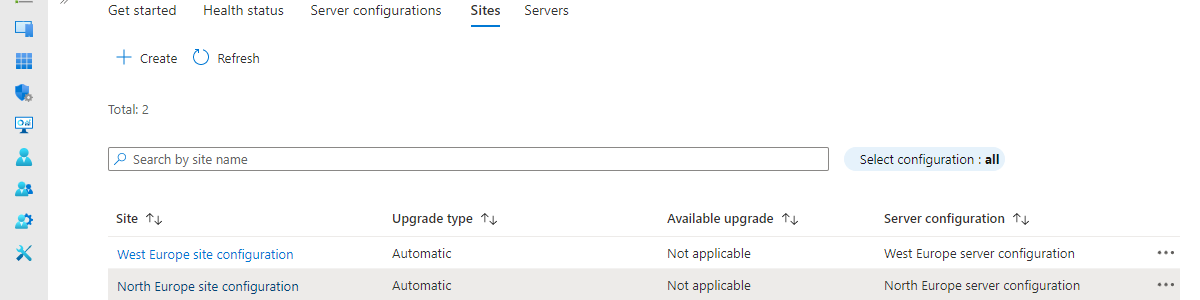
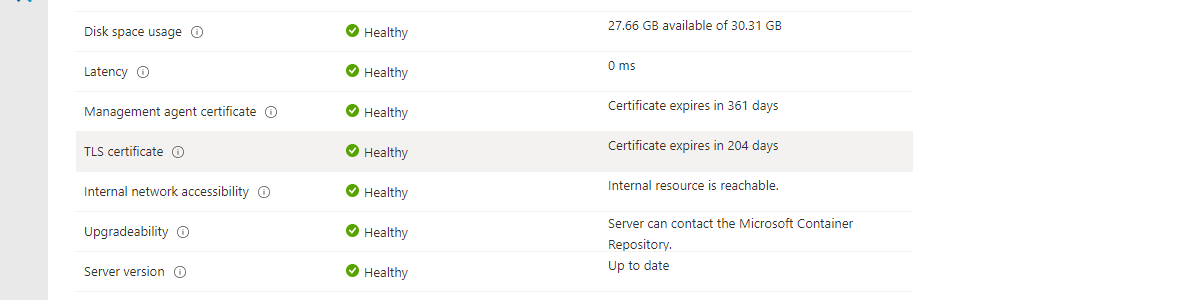
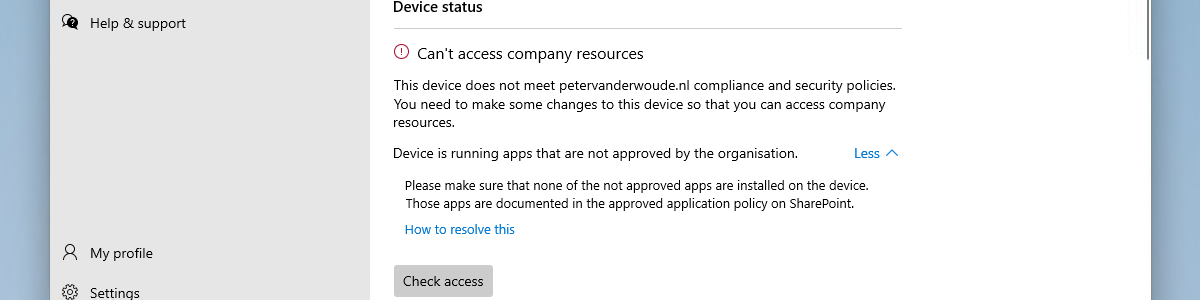
This week is about something totally different compared to the last weeks and maybe even months. There have been examples before about gathering additional data of Windows devices and using that information for dashboards and more. Those examples were mainly focused on existing data and custom scripting. This time the focus is on the Azure Monitor agent for Windows client devices. A few months ago Microsoft introduced the Windows client installer that can be used to collect data from desktops, workstations and laptops, in addition to the already existing options for servers and virtual machines. It enables the collection of Event Logs, Performance Counters and more. That could be useful with for example the introduction of AppLocker, to gather events about the behavior of apps. …