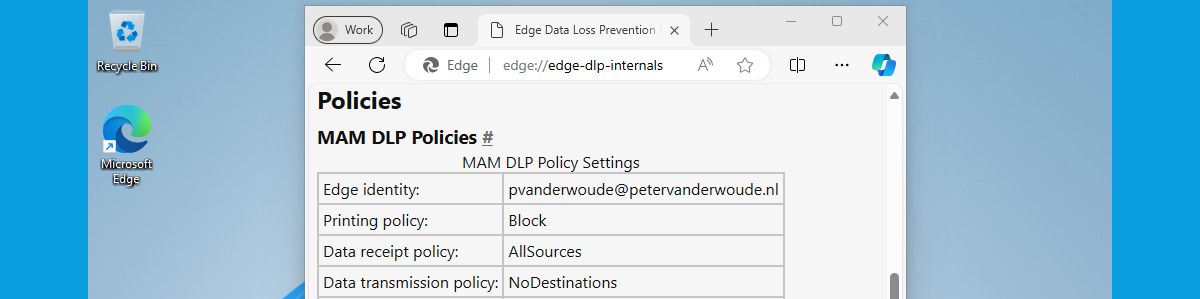
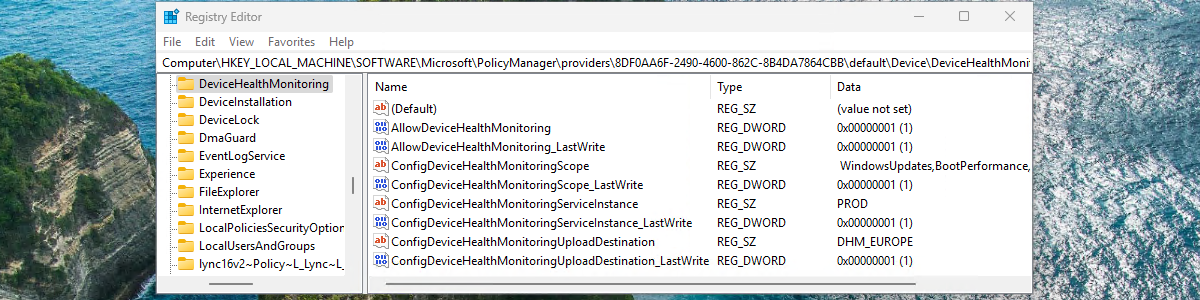
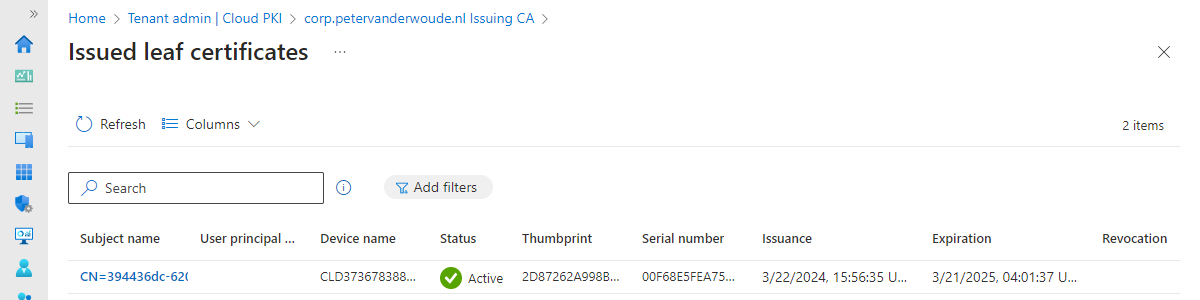
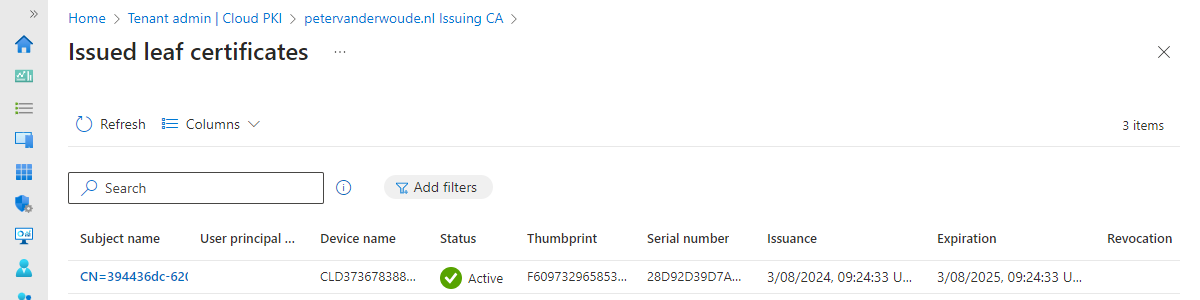
Working with personal Windows devices
This week is kind of a follow up on my post of a couple of weeks ago about why enrolling personal Windows devices might be a really bad idea. That post was focussed on advising against allowing enrolling personal Windows devices into Microsoft Intune (or any other MDM provider). The logic follow up question would be: what are the alternatives? And that’s of course a fair question. This post will be about answering that specific question. And to be quite honest, the answer might come very close to a blog post of about four years around supporting unsupported platforms. The main difference will be what Microsoft has provided over the years. And that’s a lot, especially for the Windows platform. This post will focus on …