This blog post uses Containers-DisposableClientVM, to enable the Windows Sandbox feature on Windows 10 devices. This is available in Windows 10 Insider build 18305 or later.
This week is all about enabling a recently introduced Windows Feature. That Windows Feature is Windows Sandbox. Windows Sandbox is a lightweight desktop environment that is specifically created for safely running applications in isolation. It provides an isolated, temporary, desktop environment where users can run untrusted software without the fear of lasting impact to their device. Any software installed in Windows Sandbox stays in the sandbox and cannot affect the host. The installed software is permanently deleted, once Windows Sandbox is closed. Windows Sandbox is part of Windows 10 (Pro and Enterprise) Insider build 18305 or later. In this post I’ll show how to use Microsoft Intune to enable Windows Sandbox, followed by the end result.
Script
Let’s start by looking at the PowerShell script that can be used to enable the Windows Sandbox feature. The following PowerShell script can be used to basically enable any Windows Feature, but will be used in this post to specifically install the Windows Sandbox feature.
[gist https://gist.github.com/pvanderwoude/2bca050e6173809b86f95415c9f2cb47 /]
Note: When using a virtual machine, nested virtualization must be enabled for that virtual machine. That can be achieved by using the following PowerShell cmdlet on the host machine: Set-VMProcessor -VMName <VMName> -ExposeVirtualizationExtensions $true.
Configuration
The next step is to configure the PowerShell script in Microsoft Intune. The script must run in SYSTEM context to easily install new Windows Features. To upload the script, follow the five steps below. After uploading the script, simply assign the script to the required devices. I deliberately mentioned devices, as I’m using a security group that filters on the version of Windows 10. The good thing is that nowadays these scripts can be assigned to devices and that users are not required to be logged on first.
| 1 | Open the Azure portal and navigate to Intune > Device configuration > PowerShell scripts; |
| 2 | On the Device configuration – PowerShell scripts blade, click Add script to open the Script Settings blade; |
| 3a | 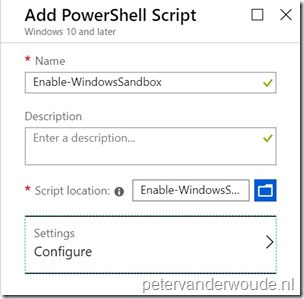 On the Add PowerShell script blade, provide the following information and click Settings to open the Script Settings blade; On the Add PowerShell script blade, provide the following information and click Settings to open the Script Settings blade;
Note: The script must be less than 200 KB (ASCII) or 100 KB (Unicode). |
| 3b | 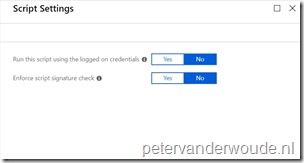 On the Script Settings blade, provide the following configuration and click OK to return to the PowerShell script blade; On the Script Settings blade, provide the following configuration and click OK to return to the PowerShell script blade;
|
| 4 | Back on the Add PowerShell script blade, click Create. |
End result
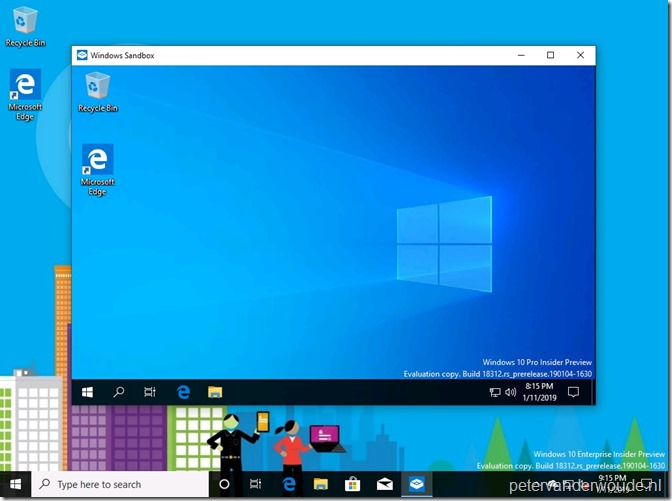
Now let’s end this post by looking at the results. To verify a success, simply start Windows Sandbox. That Windows Feature should be available now. To verify a success from a Microsoft Intune perspective, either check the status of the PowerShell script in the Azure portal , or look at the AgentExecutor.log and IntuneManagementExtension.log on the device.
Note: By using PowerShell, at this moment, Windows Sandbox can also be enabled on not supported devices (devices without virtualization capabilities), .
More information
For more information regarding Windows Sandbox and PowerShell scripts in Microsoft Intune, please refer to the following articles:
- Windows Sandbox: https://techcommunity.microsoft.com/t5/Windows-Kernel-Internals/Windows-Sandbox/ba-p/301849
- Manage PowerShell scripts in Intune for Windows 10 devices: https://docs.microsoft.com/en-us/intune/intune-management-extension
Cool feature. I understood there were problems with it in the insider preview versions and has been fixed in the latest. Handy feature for the cracks 😀
It’s indeed a cool feature!
Would be interesting to setup a Kiosk style solution – perhaps a single assigned access app kiosk launching Windows Sandbox with a configuration wsb file.