Getting familiar with the Intune Management Extension log files
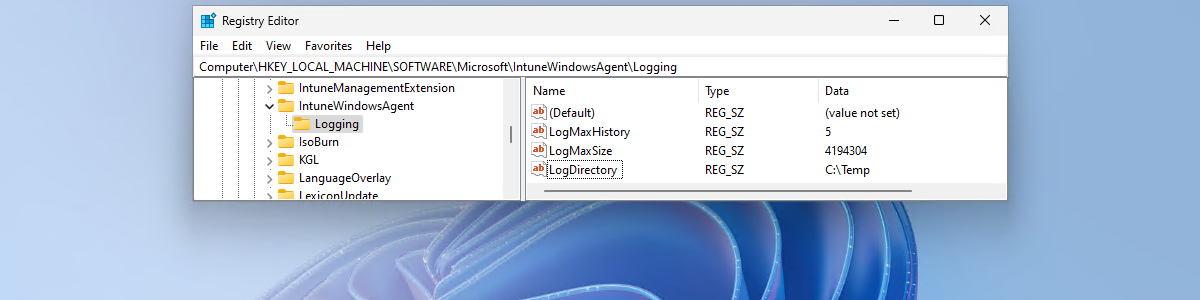
This week is another post about the Intune Management Extension (IME). This week the focus is on the log files of the IME. Probably not the most interesting subject, but definitely an important subject. Especially as an IT administrator, it’s important to be familiar with the available log files of the IME and to understand the usage of those log files. Besides that, it can also be interesting to be familiar with the configuration options for those log files. Together that will help with a better understanding of the logging capabilities of the IME and the log files that should be used to find the information related to a specific problem. This post will have a closer look at the IME log files and the …