This week is all about a recently introduced profile in Microsoft Intune to configure shared PC mode on a Windows 10 device. That profile is named Shared multi-user device profile. Something similar has been available already for a while via Intune for Education. The main use case for this profile are school devices that are shared between multiple students. In this post I’ll provide a brief introduction regarding shared PC mode, followed by the configuration (and the configuration options) of the Shared multi-user device profile. I’ll end this post by looking at the end-user experience.
Introduction
Let’s start with a short introduction about shared PC mode and immediately address the main use case. Shared PC mode s designed to be management- and maintenance-free with high reliability. A good example of devices that benefit from shared PC mode are school devices. These devices are typically shared between many students. By using the Shared multi-user device profile, the Intune administrator can turn on the shared PC mode feature to allow one user at a time. In that case, students can’t switch between different signed-in accounts on the shared device. When the student signs out, the administrator can also choose to remove all user-specific settings.
End-users can sign in to these shared devices with a guest account. After users sign-in, the credentials are cached. As they use the shared device, end-users only get access to features that are allowed by the administrator. For example, the administrator can choose when the shared device goes in to sleep mode, the administrator can choose if users can see and save files locally, the administrator can enable or disable power management settings, and much more. Administrators also control if the guest account is deleted when the user signs-off, or if inactive accounts are deleted when a threshold is reached.
Configuration
Now that it’s known what the main use case is of the the Shared multi-user device profile, let’s have a look at the configuration of the Shared multi-user device profile. The following four steps walk through the creation of the Shared multi-user device profile, including a short explanation with the different configuration options. After the creation of the profile, it can be assigned to a user and/or device group (just like any other profile).
| 1 | Open the Azure portal and navigate to Intune > Device configuration > Profiles to open the Device configuration – Profiles blade; |
| 2 | On the Device configuration – Profiles blade, click Create profile to open the Create profile blade; |
| 3a | 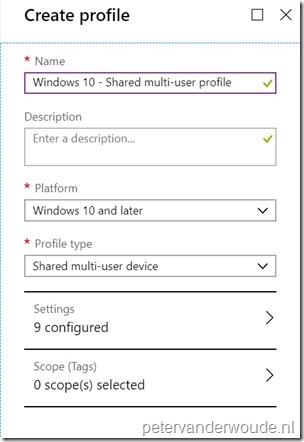 On the Create profile blade, provide the following information and click Settings to open the Shared multi-user blade; On the Create profile blade, provide the following information and click Settings to open the Shared multi-user blade;
|
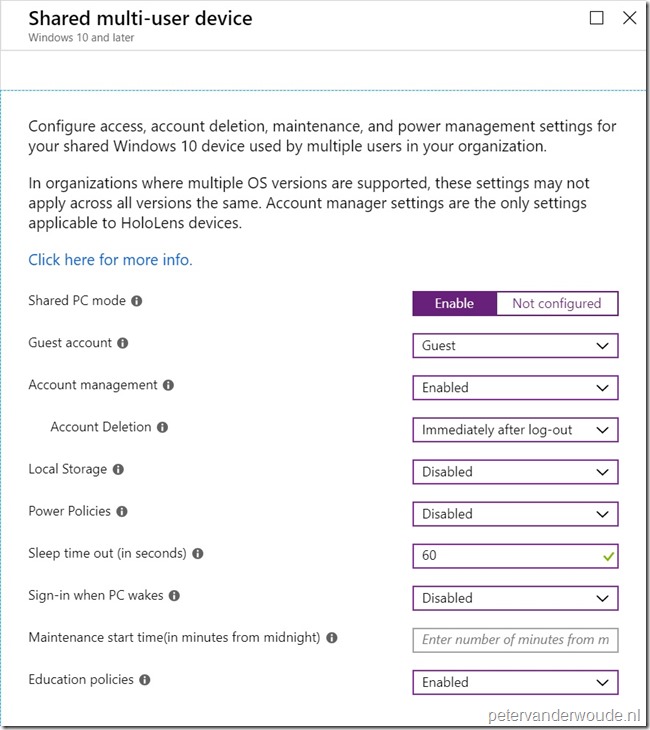
| 3b | On the Shared multi-user device blade, provide the following configuration and click OK to return to the Create profile blade (see screenshot below);
|
| — |  . . |
| 4 | Back on the Create profile blade, click Create. |
Note: Besides configuring Windows Update, it is not recommended to set additional policies on devices configured with shared PC mode. The shared PC mode is optimized to be fast and reliable over time with minimal to no manual maintenance required.
End-user experience
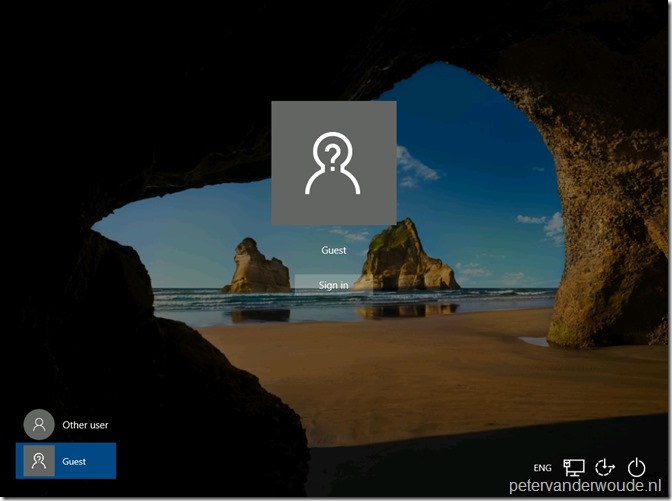
Let’s end this post by looking at the end-user experience after assigning the Shared multi-user device profile. The first thing the end-user will notice is that it can click on the guest user account icon and simply click sign-in. No password will be required.
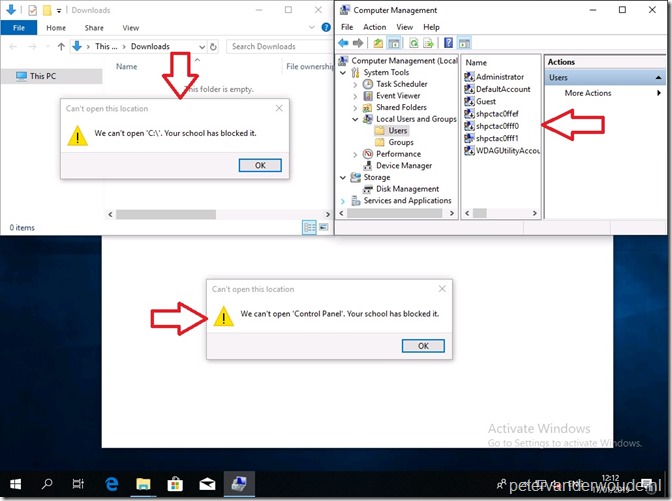
Once logged on to the device, there are many places to look for a limited experience and specific configurations. I choose to show an important configuration related to the guest account and and few configurations related to available options to the end-user. Below on the right is an example of the guest accounts that are created. Every time the user logs off, the account will be disabled and a new account will be created. Below on the left and on the bottom are two examples related to permissions. It shows that the guest user can’t access the local C-drive and the Control Panel. It also confirms a statement at the beginning of this post; the main use case is schools. It clearly shows in the messages.
More information
For more information regarding Windows 10 shared multi-user devices and configuring those devices in Microsoft Intune, please refer to the following articles:
- Windows 10 and later settings to manage shared devices using Intune: https://docs.microsoft.com/en-us/intune/shared-user-device-settings-windows
- Control access, accounts, and power features on shared PC or multi-user devices using Intune: https://docs.microsoft.com/en-us/intune/shared-user-device-settings
- Set up a shared or guest PC with Windows 10: https://docs.microsoft.com/en-us/windows/configuration/set-up-shared-or-guest-pc
- Windows 10 configuration recommendations for education customers: https://docs.microsoft.com/en-us/education/windows/configure-windows-for-education
How about OneDrive and shared multi user device. Can you lock a device for the C-drive but OneDrive is still available?
Hi Maurits,
Not sure what you’re looking for, as in this case I’m using guest accounts and those accounts don’t use the integrated OneDrive.
Regards, Peter
How does this work with with enrolled devices? Should we be using the DEM account to do this?
Hi Howard,
That depends on the scenario. You could also look at Autopilot self deployment. It really depends on the scenario.
Regards, Peter
Has anyone heard if you can make the Guest login option first in the login screen or even auto login?
Hi Nigel,
With the KIOSK configuration you’ve got the option to use auto login.
Regards, Peter
Hi Peter, how would this work from a licensing view point. Since the user would not be getting any intune user policy would you recommend licensing the user or the device?
Hi Misho,
I think that really depends on the usage of the device.
Regards, Peter
We have some devices we need to setup with shared=pc mode.
the users wants to sync there own onedrive.
is this possible with custom shared-pc?
Hi Nobi,
Not integrated with Windows if you are using guest accounts.
Regards, Peter
Hi Peter,
Are the apps accessible to all users on a sharedPC?
I distribute a specific exe/MSI standalone application to a user using MDM on a shared pc and is installed. When the first user logs out and the next user logs in, will the second user have access to the app that was distributed to user 1 and installed by him?
Hi Prasad,
It all depends on the complete setup. How are you using and configuring the shared device?
Regards, Peter
This mode is super powerful and very useful in a school environment like ours. However, we’re having issues with users unable to hear audio from any type of video. It also seems that when a new user logs in or an existing user, the sound is immediately muted until you unmute it yourself. If you have this configured in 2024 on any laptop you can replicate what I’m saying.
The only way around this that I have found is to disable the power option for a multi-user device and instead use your own power actions such as shutdown on lid closed and do nothing when power button is pressed. A full restart or shutdown is the only thing that remedies the issues with sound. The biggest issue is that in a school environment, especially during standardized testing. The immediate solution to restart in order to restore audio for video is time consuming and frustrating.
Thank you for sharing, Michael. That is good information. I personally I hadn’t experienced that behavior yet.
Regards, Peter
What would be your suggestion for this scenario. I have setup the shared device profile and the self deploying autopilot profile however the autopilot profile is unable to assign because the pc doesn’t have tpm 2.0 chip in it. So when the devices is wiped what would be the best way to join that device to Azure because if we use a standard user account I believe the device will be assigned to that user which we wouldn’t want since it’s a shared pc.
Hi Brent,
Have you looked at using device enrollment manager accounts?
Regards, Peter
Update – I have gone with the Multi-App SelfDeploying Kiosk mode for my solution. I do wish I could leverage the account maintenance with my Kiosk account (delete/re-create on log out and maintenance etc) but it does not appear to be possible (no affect applying shared pc mode after or with Kiosk mode).
Thanks for the great articles!
Cheers
Thank you for the update, Nigel!
We are seeing that licensed users with full domain accounts log into Shared Devices cannot use OneDrive, it either does not load or when run as admin causes a “Blocked” message. Where can we change this config? Can see no options via Azure Portal to Block Apps or Unblock them – we do no blocking of OneDrive on our network but it has enabled somehow for these users.
Is this by design? Please advise where i can change this configuration. Thanks!
Hi Oli,
What type of message are you referring to? Is it conditional access?
Regards, Peter
Hi Oli & Peter,
I have just experienced the same issue with a test deployment of Multi-User Devices via an Autopilot rollout. It appears that even when leveraging the new Per Machine Install of OneDrive, the users cannot load the OneDrive App. I did notice that the old OneDrive for Business (Groove.exe) does operate however this is a legacy application and does not support Known Folder Move, Autoconfiguration and other InTune based ADMX configurations, which is not ideal.
From what I can see from other discussions and Microsoft documentation is that only Windows 10 VDA via Azure or VDI with persistent profiles is supported. This would, I believe, rules out Multi-User Devices.
Happy for your thoughts, experiences and knowledge, as I hope I am incorrect with these findings.
Best Regards,
Brad Vander Reest
Hi Brad,
Thank you for your reply. Similar to Oli, what message do you get and what is shown in for example Event Viewer?
Regards, Peter
Hi ,
I have came across a scenario to Migrate from work space one to Intune where IPADs and Android devices are shared between multiple users , please suggest if InTune support this scenario & can we configured Devices in Shared Mode.
Regards
MSB
Hi MSB,
Based on that little information, I would say that it’s possible. But like with everything, the challenge is in the details.
Regards, Peter
Shared PC could be great but why have MS blocked OneDrive! It’s nuts.
Now I’ve basically re-created most of the shared pc manually.
Let’s hope this changes in the future.
Agree, Joe!
@Joe Matthews. Did you manage to get a work around for getting OD working on a shared PC? I can’t believe this doesn’t appear to work
OneDrive for Business is blocker by default in the Shared PC config. You can enable it by using a powershell script which adds the DWORD ‘DisableFileSyncNGSC’.
# Author: Revesh Manbodh
# This script will enable OneDrive for business.
# Value 1 is enable | Value 0 is disable
$registryPath = “HKLM:\Software\Policies\Microsoft\Windows\OneDrive”
$Name = “DisableFileSyncNGSC”
$value = “0”
IF(!(Test-Path $registryPath))
{
New-Item -Path $registryPath -Force | Out-Null
New-ItemProperty -Path $registryPath -Name $name -Value $value `
-PropertyType DWORD -Force | Out-Null}
ELSE {
New-ItemProperty -Path $registryPath -Name $name -Value $value `
-PropertyType DWORD -Force | Out-Null}
Revesh Manbodh I tried adding this in Intune but it fails to deploy the PowerShell script. Any ideas?
Hello Peter,
Do you have a solution for printing? For guest users we want to add a printer automatically. How do you manage this?
Thank you,
Wietse
Hi Wietse,
Are you looking for the Cloud Printer configuration options, or for an external solution like Printix?
Regards, Peter
Hi Peter,
I’ve enabled these features through Intune on some devices, major issue that I’m currently facing is that the computer isn’t responding to the shutdown & restart button in the start menu anymore. The only way the shutdown works is by doing this from PowerShell (restart-computer -Force). Pressing ALT+F4 also works, the shutdown window notifies me about other users being logged in and after that I’m able to continue anyway.
Is this expected behaviour?
Hi Michel,
Shared PC pre-configures some settings for you. For a list of those settings, have a look here: https://docs.microsoft.com/en-us/windows/configuration/set-up-shared-or-guest-pc
Regards, Peter
Hi Peter,
You mention “Power Policies: Select Disabled to prevent users from turning off hibernation, overriding all sleep actions, and changing the power settings”
Should that not be set to Enabled to have the mentioned restrictions applied?
Also it appears the “Sleep time out (in seconds)” setting is ambiguous in its description and function. There is a discussion going on about this here: https://github.com/MicrosoftDocs/IntuneDocs/issues/2916
Dan
Thank you, Daniel! I’ve updated the Power Policies configuration.
Regards, Peter
I don’t get it and this is mainly due to the completely confusing documentation from Microsoft. Do I understand that it is not possible to manage policies for deleting the local guest accounts independently from the cloudbased Azure user accounts? For example, why can’t I set up policies so that guest accounts are always deleted immediately after logging off, but Azure user accounts are only deleted after the hard drive has become 90% full? If I set that the guest accounts should be deleted immediately after logging off, I lose the ability to make settings for the other cloud based user accounts. Also, it seems that the Azure user accounts are not deleted after logging out, but only the guest accounts, which I find even more confusing. Am I getting something wrong here? What do you think?
Hi Tobias,
It sounds accurate that only the guest accounts are removed after logging out (I haven’t tested all the scenarios yet).
Regards, Peter
Hi Peter, thanks a lot. But which rules are applied to the Azure Accounts then? What happens, if C:\ runs out of space, are there any automatic deletions then?! Is there anybody who tested this?
Hi Tobias,
How are you using those devices? Are you using it with a guest account, or can anybody logon to those devices with their own account?
Regards, Peter
Hi Peter, great tutorial and thank you for providing a good explanation of some of the features. I may be asking a silly question and I’d like to apologise in advance if I’ve completely missed the boat here, but I have the following scenario and I’m not 100% sure which way to set it up.
We have a small team of 15 users, each with their own managed W10 PC. Everything works as expected. However, sometimes some of the team travel and take one of the company laptops with them. We have 4 which are shared among the staff. People simply grab one when they need it and put it back when they’re done.
Could you please advise me if a shared policy on the laptops is the right way to deal with this. The laptops are shared, but a Guest account would never be used (or setup) because the only people using them would be staff via AzureAD. If a shared policy is the correct way to go: how would you configure it? It not, could you please advise.
Hopefully this makes sense and any help and advice would greatly be appreciated.
Thank you
Hi Paul,
Depends on what you want to achieve. When you want those users to have the best experience, the multi-user configuration might not be the best option.
Regards, Peter
Hi Peter,
Great article. From what I understand this functionality is mainly targeted at guest and multi user devices, however I am wondering if this is also applicable for the following scenario:
I have a compliant MacBook that is registered with my user account. However, when I log in with an admin account AAD refuses access because the device is not registered with this particular admin account.
Is there also a way to create some kind of “dual login” for a user account and an admin account?
Thanks, Kees
Hi Kees,
Not sure if I’m completely following the scenario. The article is about Windows functionality and is not applicable to MacBooks.
Regards, Peter
Hi Peter,
Thanks for your answer, I understand. I think I will just drop the question at Microsoft an hear what they say.
There is not very much to find regarding this topic on the internet. 😉
Hi Kees,
That sounds like a good plan. I’m not familiar with this functionality in Microsoft Intune for MacOS yet.
Regards, Peter
Peter,
Our Shared PC config would be used in a classroom setting, where a device could be grabbed by any student, used for an hour, and logged out. I think this was the original intent of the profile from Microsoft’s perspective. All logins are Microsoft AAD logins. No guest accounts are used. OneDrive functionality is needed for all. The local profiles are not removed at logout as expected or is that expectation incorrect? Also the company portal is not functional for user2 through user999 – only the first user. How can I make this more functional for every student? Thanks!
Hi PattyR,
What does your configuration look like?
Regards, Peter
We also experience the same issue regarding Shared multi-user device in a hybrid-joined Autopilot setup.
We use the DEM (Device Enrollment Manager) account for the initial OOBE AzureAD logon (Welcome to…login prompt) and a normal AD user account (whomever enrol the device) for the windows login that precedes domain join.
We also push a “Shared multi-user device” Configuration Policy from intune to these Shared PC devices (using “Group Tag” and dynamic group to differentiate the Shared-PCs from normal PCs)
Everything seam to work fine, except that company portal only shows applications for the first logged in user (the AD user, not the DEM account wich is a AAD-only account).
Also we have issues with company portal not showing up at all for user accounts not being the one used under the Windows login in the enrollment process..
Hi odd,
Are those devices identified as shared devices?
Regards, Peter
Hi Peter
I have the same issue as PattyR. Shared PC policy is in place with the following:
Shared PC mode: Enable
Local Storage: Enabled
Power Policies: Enabled
Sign-in when PC wakes: Enabled
Education policies: Disabled
Yet any user outside the user that enrolled the device cannot access anything in the Company Portal. The portal displays a message of, ‘This device is already assigned to someone in your organisation. Contact company support about becoming the primary user. You can continue to use Company Portal but functionality will be limited.
Hi Andy,
Follow up question based on the message that you receive: is there no primary user assigned to the device?
Regards, Peter
can a kiosk profile and a multi user share profile be applied on a single device ?
and if possible please share any article as per your answer.
Thanks
Hi Parminder,
Not sure what the use case would be. Why would you want to have that combination?
Regards, Peter
Hi Peter,
first of all, thanks for the amazing posts regarding Intune. I really have gotten a lot of information from your site which helped me further in our Intune-quest.
I do have a question for you regarding this post.
I’ve setup multi-user in EM+S for our regular desktops. These are so called flexible work machines. What I do notice is that when I log off the Guest account on a machine with that policy and logon with our DEM (admin) account it has the same restricted access as the Guest account. So I cannot open File Explorer of open the Control Panel. I would have expected that this should be possible because I use an Admin account to logon to this machine. What are your thoughts about this? Is this normal or should I have more local rights when I logon with the DEM account?
Thank you for your reply.
Hi Robert,
I would expect administrator access to be available. See also: https://docs.microsoft.com/en-us/windows/configuration/set-up-shared-or-guest-pc#guidance-for-accounts-on-shared-pcs
Regards, Peter
Hi Peter, thank for this article. This is 100% what I need to configure in my school.
2 questions:
At each connection, a new profile directory is created under C:\Users (shpctac0fff8, shpctac0fff9, etc).
In your article, you say that the account is disabled at each logoff but it is not deleted. And it takes about 250 Mb.
I expected that these directories to be deleted automatically at logoff but it seams it is not the case.
In our school, a lot of different people will use these share computers. A directory like shpctac0fff8 takes about 250 Mb.
If there are 20 different sessions created a day, it makes 20 x 250 Mb = 5Gb a day.
After one month the disk will be full.
This is strange because in the configuration profile, I configured it to have the account deleted at logoff.
Did I miss something? How to force the deletion of these profile directories? Or maybe it is deleted during maintenance? Or at the next reboot after maintenance? Can you clarify this?
In the configuration profile, I selected ‘guest account and Domain accounts’. I see that it is not possible to connect with my Domain account anymore. Is it not the goal of this option?
Thanks for you help,
Laurent Gousenbourger
Hi Gousenbourger,
You can find the behavior in the account management section as described here: https://docs.microsoft.com/en-us/mem/intune/configuration/shared-user-device-settings-windows#shared-multi-user-device-settings
Regards, Peter
Hi Peter,
Thanks. I read the documentation. Indeed, I understand now better the difference between ‘guest’ accounts and ‘domain’ accounts.
Nevertheless, I don’t understand yet how the account deletion happens for the local directories shpctac0fff8, shpctac0fff9, etc. is it never deleted? If you say that the account is disabled, the best solution to delete it physically is to add a task on the device to delete the directory at logout? Do you have another solution?
Thanks,
Laurent
Hi Gousenburger,
It’s been a while since I really looked in to those details. According to this doc, the account deletion is verified during the sign-off and maintenance times. Are you see anything like that on your devices?
Regards, Peter
Hello, we are in the same situation, same setup. Did you find a solution to clearing out the students C:\users folders on Intune shared devices? My testing with shared device/account management profile never deletes anything…
Hello Peter
Thanks for this post.
I have now implemented it and it works pretty well.
But I have the problem, that the customer need to use the Office 365 Apps (Word,PowerPoint).
So, is there a possibility to activate Office? If I register Office with an Account it got saved in the userprofile and on the next logoff it got deleted because of the guest rule. Do you manage this?
Thanks
Noah
Hi Noah,
Did you have a look at shared device activation (see: https://docs.microsoft.com/en-us/deployoffice/overview-shared-computer-activation)?
Regards, Peter
Nice article. Thanks for writing it.
Thank you Keven!
Hello Peter, Finally I find a post that intelligently walks me through the steps. Thank you.
I have one issue. “Guest” user is not showing up on the Welcome Screen. Not sure how to make this happen. I’m logged in as the admin via AAD. My Device configuration policy has Succeeded and my setting is Guest account = guest,domain
Hi David,
Maybe a stupid question, but have you enabled the guest account in the configuration.
Regards, Peter
Is it possible to set a password to your guest account on a sharedPC ?
Hi Emotino,
That’s not possible via this configuration. That would require something like scripting.
Regards, Peter
I am using shared device in an Education environment. I am running into a problem when I logoff or shutdown the device. Windows seems to terminate all processes, even an logoff script (tested in local policy). We want to forget the wifi setting (netsh command) but the logoff terminate all services. In a “normal” Intune device this is not the case. You can test this with Notepad. type sommething and then logoff. Normally Windows ask to save the document and prevents the logoff. In shared device mode you don’t get the question
Hi Marcel,
I expect that to be part of the behavior created by the standard policies for those shared devices.
Regards, Peter
We created an WiFi profile in Intune which overrides standard behavior to cache the credentials. Furthermore run a script within a scheduled task at logon to remove all WiFI profiles except our standard WiFi profile and current Profile. This does the trick
Thank you for sharing that, Marcel!
Regards, Peter
Hi Peter
Many thanks for your article.
We are a medium sized business and want to move about 20 PC/NUCs to a shared device policy in Intune.
Is there a way for us to have pre-installed (non-M365) programs/apps on the machines permanently, and not have to rely on the device installing when a user signs in each time?
Or, would this have to be something that we do locally/by other means, and then add the devices to the shared device policy?
Hopefully that makes sense.
Hi OllieG,
You can just install apps to the device (instead of the user). That makes it available for all users.
Regards, Peter
Hi Peter,
we face exact the same issue.
Each time an Intune licensed user logs into a shared multiuser device, the user assigned applications starts to install and the device reboots (because of the app installation).
Is there a way to prohibit this individual app installations and allow only the device group assigned applications to be installed?
Thank you Peter!
Hi Sam,
You could use an filter to exclude shared devices from the app assignment.
Regards, Peter
Hi,
Thanks for the great article. How do you handle compliance here?
Kind regards
Tim
Hi Tim,
It depends. What are you looking for/at?
Regards, Peter
Hi Peter, We have the exact same problem with Student accounts not deleting at logout. We have 60 Surface Go’s shared between a school of 450 students. So my devices are filling up, even though ive the shared policy applied exactly as in your tutorial. Ive opened a case with MS which is ongoing for nearly 3 weeks now. Just wondering have you heard of any more issues like this, i see some people have had similar issues like me above. When does it delete or supposed to delete the AAD account, on logout or when it a device goes into maintenance mode.
Thanks maurice
Hi Maurice,
Only the issues posted here. Nobody really responded with an answer of Microsoft.
Regards, Peter
Longshot but I have tried everything I can think of, so maybe people commenting here may have an idea
WE have sharedPC computers mode on an AD domain, for public use computers in an office. They sign in with a single domain account (the same for everyone).
The account is being removed fine (documents etc disappear) but the Calculator appx won’t work unless the user goes into settings and resets it. Then it works… until the next sign on what is a presumably new profile.
However it seems that not everything is removed.
Some data somewhere is stored for the APPX and for the life of me I can’t figure out where or what it is. Once the APPX is corrupt, or no longer working, or w/e is happening here, it is corrupt FOREVER for that that account. I have gone through and removed everything from the registry to do with the profile’s SID, removed every temporary file, every breadcrumb possibly relating to that profile that I can find… still the app is broken on sign in until the user resets it.
The opaque nature of APPX is incredibly frustrating.
Any ideas?
Hi CS,
Are you saying that the app is broken from the beginning? Also in a clean OS installation?
Regards, Peter
Hey nope, the app is fine otherwise.
One way to replicate this behaviour is to do this on a domain joined machine (not sharedPC mode yet):
– log in with USER1
– use the calculator (or any appx)
– log out
– enable shared mode
– that appx will no longer work for that account unless it is reset by the user first, each time that user logs in
This is 100% repeatable!
So the solution obviously is to not allow any domain user to sign in until SharedPC mode is deployed. Which is what we did. The other work around is to (after hours) delete the domain user being used as the guest, and re-make the account with the same username (but different SID). Obviously not ideal but a new SID does seem to do it. In this particular case though, it just seems this Calculator app on the one computer is corrupt or has some corrupt cached info stored somewhere that it is pulling when it generates the profile on login. I haven’t been able to figure out where this is
To be honest, I don’t think SharedPC mode is really meant for domain joined machines and we have been switching to Intune managed, non-domain joined machines, as the Guest account is a new account each time (different SID) and thus not prone to this issue
I indeed to say that I didn’t encounter this behavior and scenario yet. It indeed sounds like it’s related to the account-app combination. Did you already contact Microsoft about this behavior?
Regards, Peter
Hi Peter,
This is great. But configuring this limits the computer, how would you log in as an administrator with full rights without adding a local admin?
Hi Liam,
Can you describe a bit more about the scenario, like why you need the permissions?
Regards, Peter
Hi Peter,
I work in an education setting, where the students need to be limited a lot on the computers to prevent them from changing anything.
However, in case something breaks, or happens, etc. I want to be able to log in with my own account. With full admin rights to change settings, delete stuff etc.
Hi Liam,
When it’s for all devices, you can look at using the Azure AD Joined Device Local Administrator role. If not, you can look at something like this: https://www.petervanderwoude.nl/post/even-easier-managing-local-administrators/
Just keep in mind that you should never provide to much permissions to a single account.
Regards, Peter
i am having this same issue as well. all the systems that i deployed the Shared PC Profile to work as expected until i need to log on as Admin and everything is still blocked. did you figure out a way around this?
One of the settings this changes is to auto deny elevation requests. I think the only option is to recreate these policies one by one and leave out the probematic one.
Good Day Peter, and thanks so much for your blog posts, which I often refer to when looking for solutions to my everyday challenges.
I am trying to configure a shared multi-user device with these features:
1. when the Guest account signs in, the taskbar should not show pinned apps such as Word, Excel, but should only show Edge.
In my testing, when applying a taskbar layout to an AD user group, the taskbar layout is retained also when “Guest” signs in, which causes a problem because Guest doesn’t have any of the MS365 licenses required to use Office. I can apply a different taskbar to these devices, but in this case the AAD users will not have those apps pinned, which is also not ideal.
2. When the Guest account signs in, the printer (which I deploy via app-packaged powershell script) should be hidden (the guest should not be able to print to it or see it). I am unsure if there is a way to do this.
3. When the Guest account signs in, Teams should not auto-launch. I have been unable to stop this from happening, even when “Enabling” the “Prevent Microsoft Teams from starting automatically after installation” setting on the Devices in question.
4. When the Guest account signs in and launches Edge, Edge should launch in InPrivate mode (this is mainly to stop the 3 pages of “do you want to sync”/ accept/import browing data). Similarly to point 1, I can either get Edge to force start InPrivate for all users of the machine (AAD users included, who will no longer be able to sync), or no users of the machine.
Do you have any ideas, pointers for any of the above challenges?
Once again thank you for your service to the IT community.
Regards,
Giovanni
Hi Giovanni,
That sounds like everything is configured for your default user, which is used for every (new) user that sign-ins. Have you looked at that?
Regards, Peter
Dear Peter,
I followed your guide but I set the “Guest account” option with only Guests.
When logging in windows allows me access even with domain users. how can i disable it leaving only guests allowed ?
Hi Alessandro,
At what point are you allowed to use domain accounts?
Regards, Peter
If you set the awake time for some odd reason it sets both the monitor and the computer to sleep the same. So if you set it to 0 so it never sleeps, that means your monitor never goes off either! Crazy right?
Also, I have seen the same issue as Alessandro above. No matter what you set Guest Account option to, it allows domain users as well in my experience (windows 11).
Combined with the fact this also disables elevation, I think the best optiin might be to stay away from this config template and replicate each individual settings ourselves? What do you think Peter? MS gives us the list of each CSP that is included in this shared setting, I am not yet sure if all of them are available though outside of using shared device.
This whole thing is a real mess imo.
Thanks for the great work here as always.
Thank you for that, Mark!
I have to say that I haven’t looked at the separate settings, yet. But I it would definitely be worth a shot to manually configure those via a separate configuration profile. Just to be sure. On the other hand, I would expect that behavior to come from one of those settings. It might also make it easier to troubleshoot and to determine the setting that cause that behavior.
Regards, Peter
If set to 0 it would sleep device after 60minutes. However, it’s best to disable the power option altogether and manage power settings through another config profile. The reason we did this is because when enabled this setting oversides all existing power settings. For us, we have the student devices set to shutdown on lid close. But because the power setting was enabled our intended config never took place.
Hello Peter,
Do you know of a way to allow a shared multi user device to navigate to a file share / ntfs location?
Hi Bernard,
Do you mean, without allowing access to local drives?
Regards, Peter
Yes we have some users that use a shared windows device that needs to access a certain file share. but because we have local drives blocked we are wondering if there is a config that allows a user to browse to a file share without changing this setting.
Yeah, the challenge is that Shared PC mode configures a lot of stuff automatically. That is described here: https://learn.microsoft.com/en-us/windows/configuration/shared-pc/shared-pc-technical
You could see if it’s maybe even easier to create your own configuration.
Regards, Peter
Mr. Van der Woude,
Have you heard of any issues when using this Multi-User Policy/Settings that creates issues with sound?
We have an issue where students attempt to play videos and the sound stops working unless the user restarts.
I think it has something to do with the multiple active profiles running on the machine. Any thoughts?
Hi Michael,
I do not directly have an idea. Why do you think that it’s related to the profiles?
Regards, Peter
Has someone figured out how to prevent Guest users locking their screens? If someone presses “windows+l” the screen locks, and presents username/password field (and no icon to continue as guest)
Since a new user is generated with a random username, there is no way to get back into the account?
I’ve disabled locking on idle to work around this, but Windows+l still locks people out. I feel like I’m missing something here.
Hi Jeroen,
Which settings are you currently using to disable the locking?
Regards, Peter
Have you had any issues where the guest account is missing on the login screen after a domain login (azure login)?
When i logout of my account the guest account button is missing and i can’t understand why it’s missing.
Hi Martijn,
I don’t recall seeing that behavior. Could it be related to different policies assigned to that account?
Regards, Peter