This week still continues the journey through Windows Hello for Business. The last few weeks were all about direct Windows Hello for Business functionalities, while this week is all about providing alternatives besides Windows Hello for Business. When looking at standard Windows functionality, those alternatives are FIDO2 security keys and the relatively new combination of the web sign-in credential provider with Temporary Access Pass (TAP). The web sign-in credential provider itself is nothing really new, but the ability to use it in combination with TAP is something relatively new. Simply because TAP is relatively new. TAP is a time-limited passcode that basically temporarily enables users to sign-in. That sign-in is focused on getting users up-and-running with passwordless authentication and on helping users recover access to their account. And all of that without the usage of a password, as TAP satisfies the needed strong authentication requirements. The best thing is that – in combination with the web sign-in credential provider – TAP can even be used with the sign-in to Windows. That enables users to get quickly up-and-running and enables IT administrators with an alternative method to sign-in to a device when really needed. This post will provide the required configurations and the user experience, by going through the following.
- Enabling web sign-in as credential provider
- Enabling Temporary Access Pass as authentication method
- Creating a Temporary Access Pass for a user
- Experiencing web sign-in in Windows with Temporary Access Pass
Important: At the moment of writing, the TAP authentication method is still an Azure AD public preview feature.
Note (as mentioned by Daniel Stefaniak): The combination of web sign-in with TAP is supported only for bootstrap scenarios for other unlock methods. Web sign-in is not to be used as your daily driver for login. Also, unlocks/logins with web sign-in do not and will not get single sign-on to on-premises resources.
Enabling web sign-in as credential provider
The web sign-in credential provider is supported on Azure AD joined devices and is available with Windows 10 version 1809 and later. That credential provider enables support for credentials that are normally not available on Windows. It basically adds a web sign-in option via Azure AD that can be used with passwordless phone sign-in and, more importantly, that can be used with TAP. That would create an option for users to sign-in, without a password, to register their passwordless authentication method. And it’s also a more IT administrator friendly method, compared to My Security Info, as it doesn’t conflict with Conditional Access when assigning policies to All cloud apps. To enable the web sign-in credential provider by using the Settings Catalog of Microsoft Intune, follow the eight steps as described below.
- Open the Microsoft Endpoint Manager admin center portal and navigate to Devices > Windows > Configuration profiles
- On the Windows | Configuration profiles blade, click Create profile
- On the Create a profile blade, provide the following information and click Create
- Platform: Select Windows 10 and later to create a profile for Windows 10 devices
- Profile: Select Settings catalog to select the required setting from the catalog
- On the Basics page, provide the following information and click Next
- Name: Provide a name for the profile to distinguish it from other similar profiles
- Description: (Optional) Provide a description for the profile to further differentiate profiles
- Platform: (Greyed out) Windows 10 and later
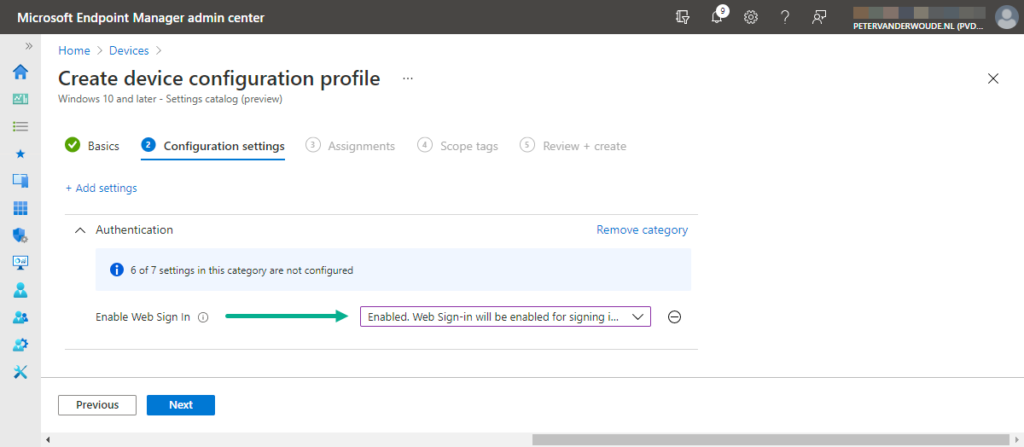
- On the Configuration settings page, as shown below in Figure 1, perform the following actions
- Click Add settings and perform the following in Settings picker
- Select Authentication as category
- Select Enable Web Sign In as setting
- Select Enabled. Web Sign-in will be enabled for signing in to Windows with Enable Web Sign In and click Next
- On the Scope tags page, configure the required scope tags and click Next
- On the Assignments page, configure the assignment and click Next
- On the Review + create page, verify the configuration and click Create
Note: Keep in mind that this is mainly a useful configuration when completely transitioned to passwordless authentication, as it currently also enables users to simply use username-password to sign-in.
Enabling Temporary Access Pass as authentication method
The TAP authentication method is currently in public preview. That authentication method provides users with a time-limited passcode that even satisfies the multi-factor authentication requirement in Conditional Access. That enables users to register or recover their passwordless authentication methods. To enable TAP as an authentication method for users, the IT administrator can enable the TAP authentication method policy. That authentication method policy contains defines the different settings of TAP, such as the users that can use TAP and the lifetime of TAPs. To enable the TAP authentication method, follow the four steps described below.
- Open the Azure portal and navigate to Azure Active Directory > Security > Authentication methods > Policies
- On the Authentication methods | Policies blade, select Temporary Access Pass
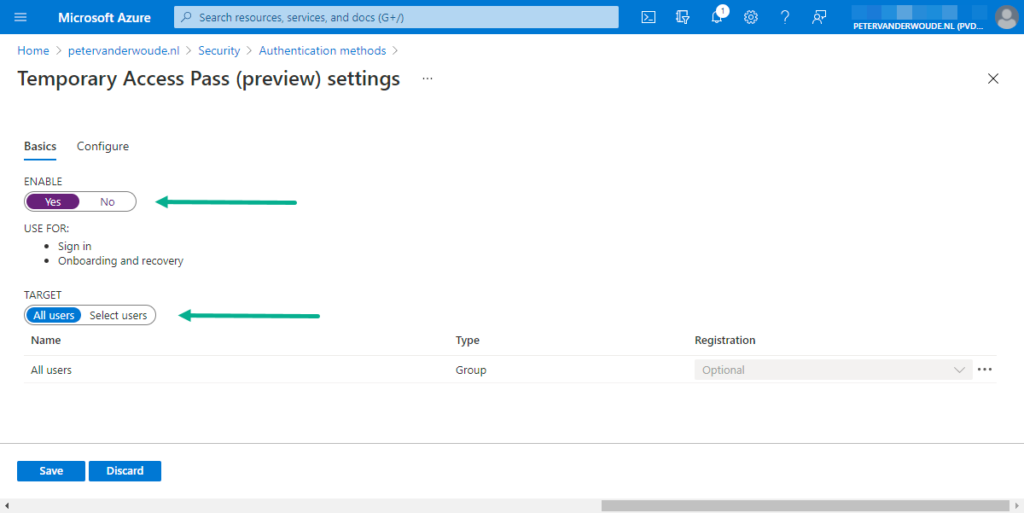
- On the Basics tab of the Temporary Access Pass settings page, provide the following information and click Save
- ENABLE: Select Yes to enable the use of TAP as an authentication method
- TARGET: Select All users or select Select users to specify the users that can use TAP as an authentication method
Note: Keep in mind that it’s possible to create a TAP for any user, but only users that are targeted with the authentication policy can actually sign-in with TAP.
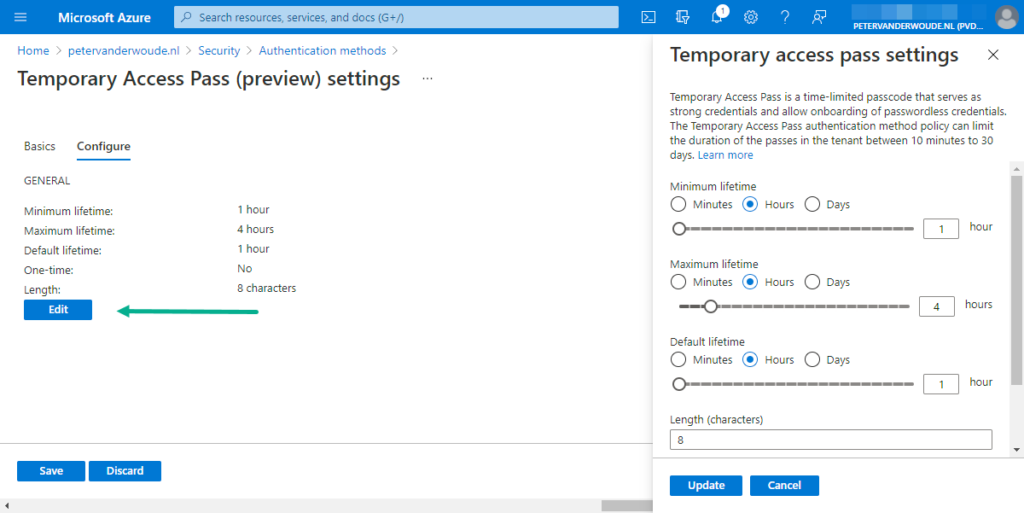
- On the Configure tab of the Temporary Access Pass settings page, provide the following information and click Save
- Minimum lifetime: Specify a value between 10 – 43200 minutes (default: 1 hour) as the minimum lifetime
- Maximum lifetime: Specify a value between 10 – 43200 minutes (default: 24 hours) as the maximum lifetime
- Default lifetime: Specify a value between 10 – 43200 minutes (default: 1 hour) as the default lifetime
- One-Time: Specify true or false (default: false) to define if it can be reused within it’s lifetime
- Length: Specify a value between 8 – 48 characters (default: 8) as the length
Creating a Temporary Access Pass for a user
The TAP can be created for users in Azure AD by any Global administrator, Privileged authentication administrator and Authentication administrator. To create a TAP for a user, the IT administrator can add an authentication method for the user. The following four steps walk through the manual creation of a TAP for a user in Azure AD.
- Open the Azure portal and navigate to Azure Active Directory > Users > Select the required user > Authentication methods
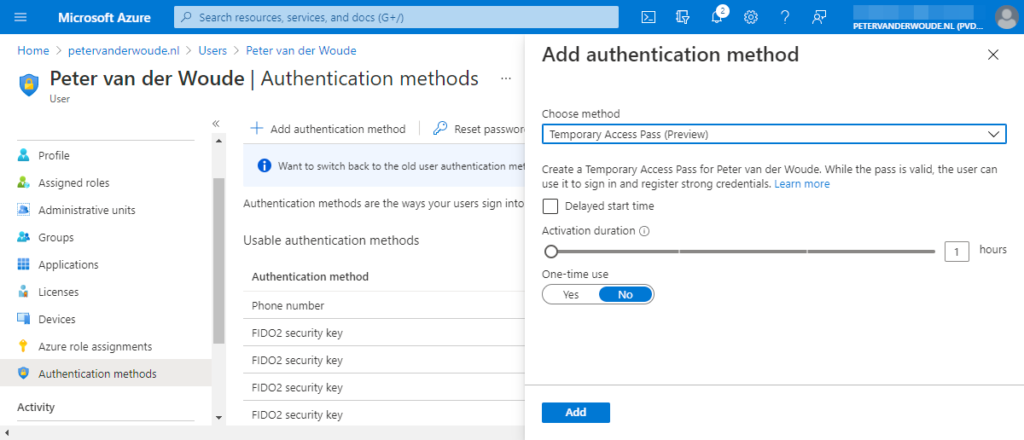
- On the Selected user | Authentication methods page, click Add authentication method
Note: At this moment it’s required to switch to the new experience by clicking on Switch to the new user authentication methods experience! Click here to use it now.
- On the Add authentication method blade, provide the following information and click Add
- Choose method: Select Temporary Access Pass to add the authentication method for the user
- Do not select Delayed start time unless the usage is not directly required
- Activation duration: Specify the activation duration when the default is not long enough
- One-time use: Choose wether the user can use it more than once within its lifetime
- On the Temporary Access Pass details blade, copy the TAP and click OK
Important: Keep in mind that it’s not possible to view a TAP after it’s been created.
Tip: The New-MgUserAuthenticationTemporaryAccessPassMethod cmdlet can be used for scripting the creation.
Experiencing web sign-in in Windows with Temporary Access Pass
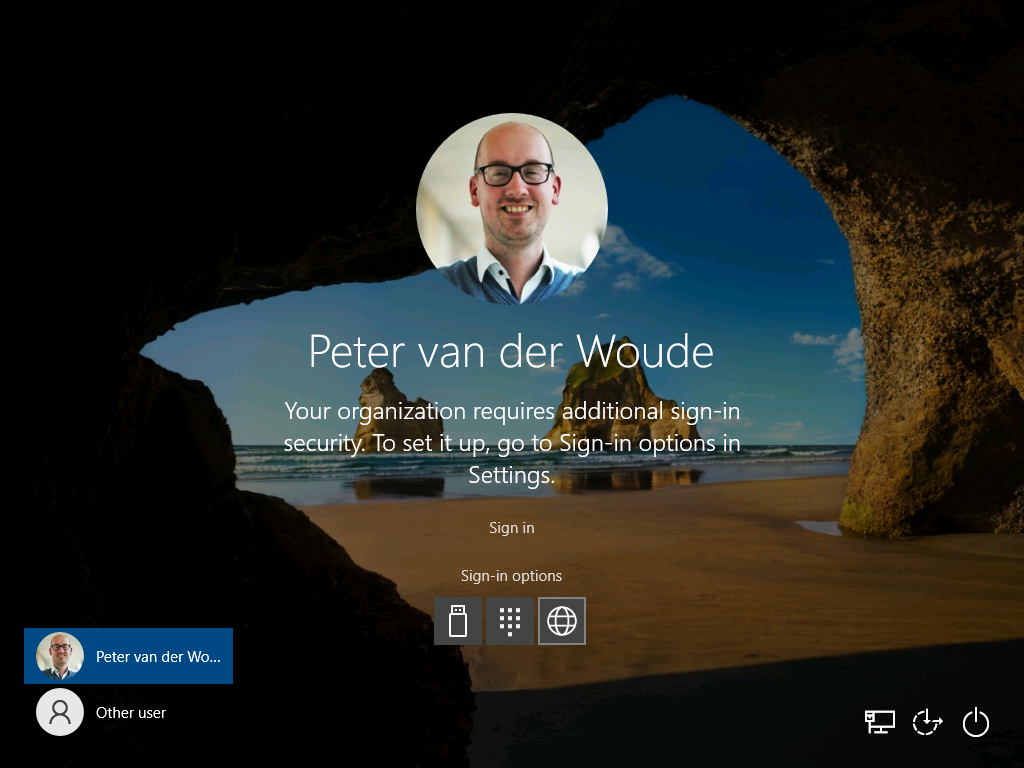
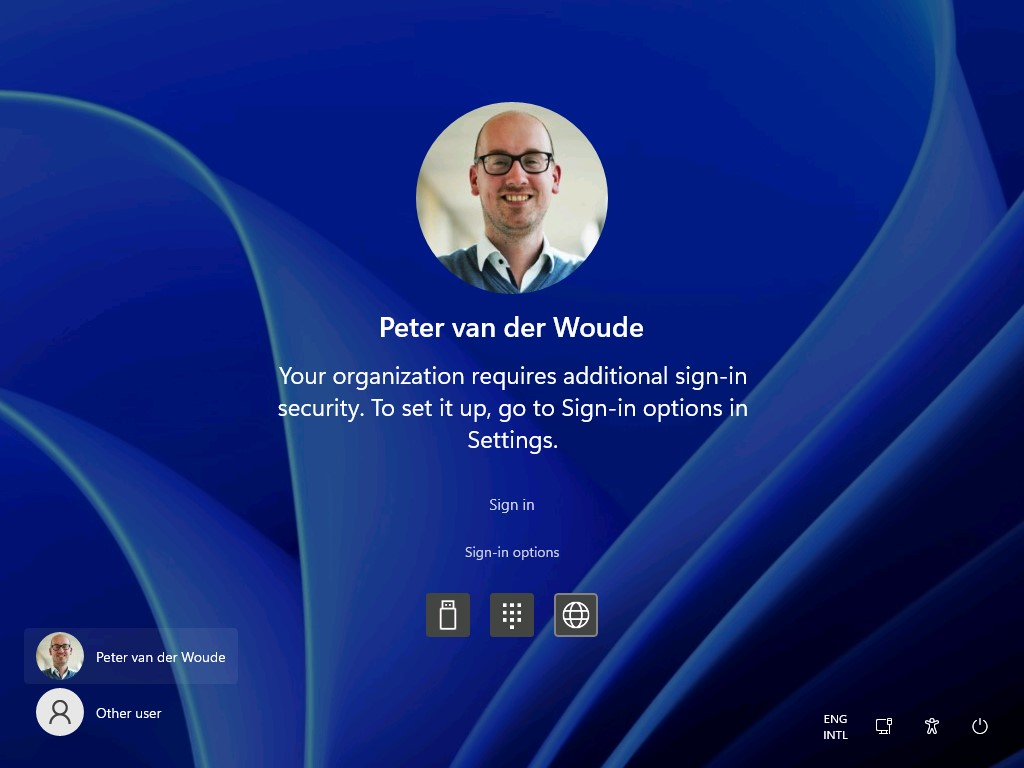
Experiencing the behavior with the web sign-in credential provider in Windows in combination with TAP is pretty straight forward. Simply start a configured Windows 10 device, or Windows 11 device, and click on Sign-in options. That will show the available credential providers, including the web sign-in credential provider. Figure 5 shows an example of a Windows 10 device and Figure 6 shows an example of a Windows 11 device. Both after clicking on the web sign-in credential provider. As these devices also have Windows Hello for Business multi-factor unlock, there will be an additional message stating that the organization requires additional sign-in security. That additional sign-in security can also be configured after signing in with a TAP.
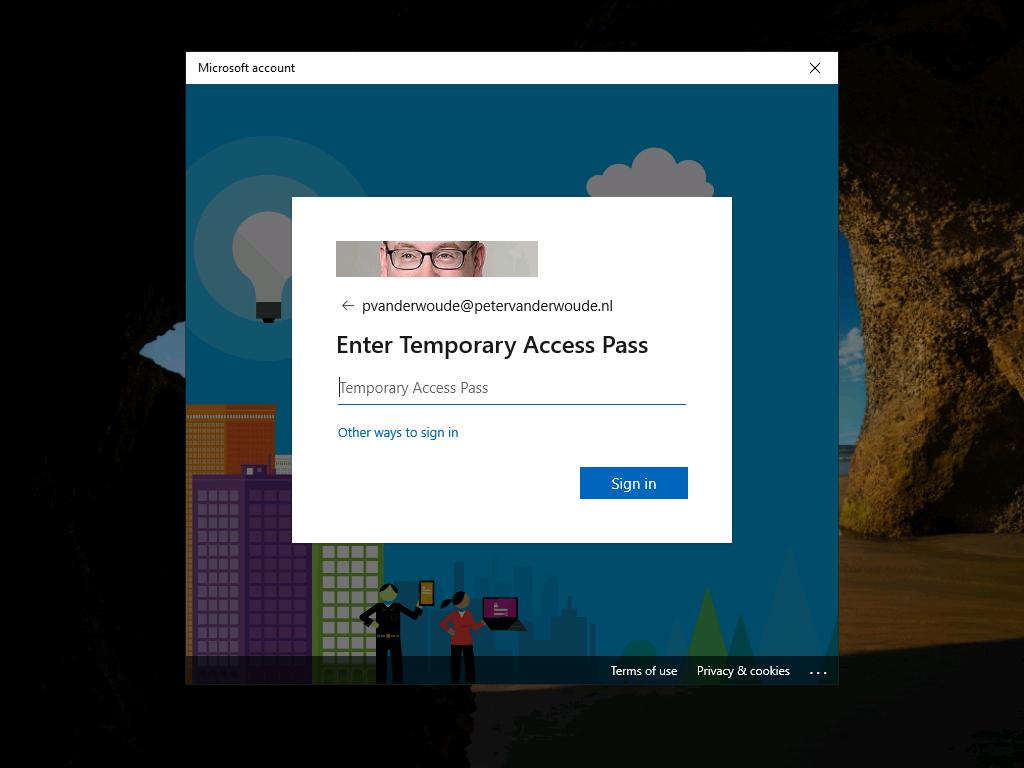
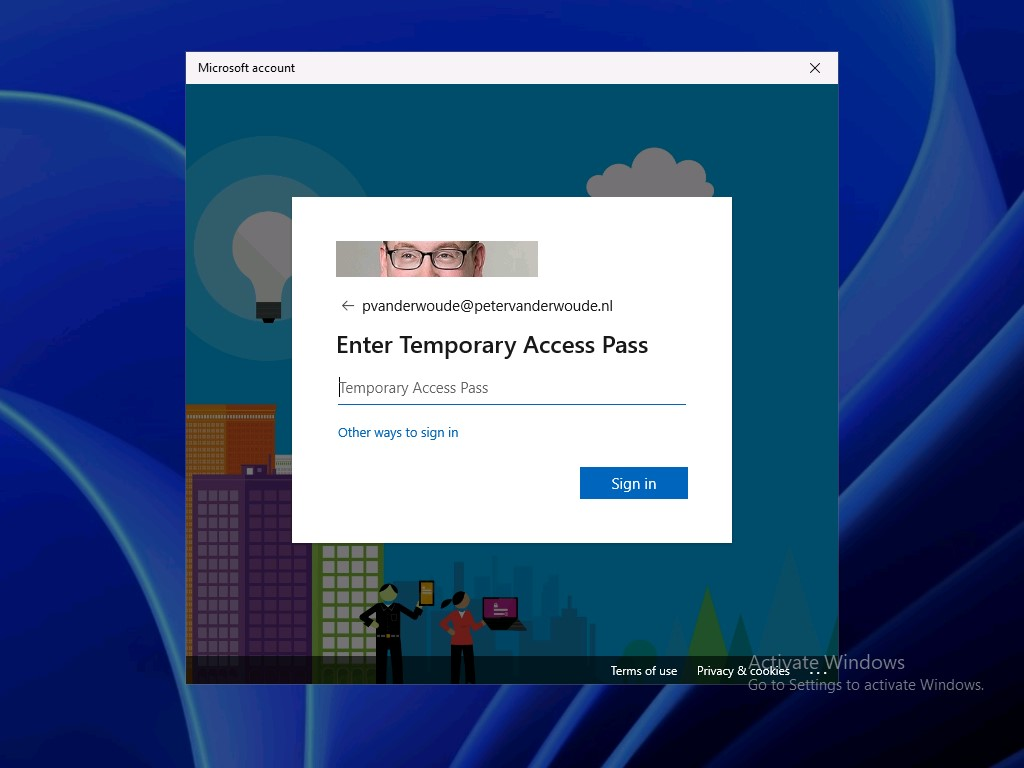
To actually use the web sign-in credential provider, the user should click on Sign-in. That will open a browser dialog that will enable the user to sign-in. When a TAP is available for the user, that sign-in dialog will automatically ask the user to enter a TAP. Figure 7 shows an example of that behavior on Windows 10 and Figure 8 shows an example of that behavior on Windows 11. When no TAP is available for the user, that sign-in dialog will just ask for a password.
Note: The good thing is that a TAP can even be used during Windows Autopilot. On Windows 11 that’s a seamless experience, as the initial sign-in automatically detects that the user has a TAP available. On Windows 10 that’s currently a slightly less experience, as it requires the user to provide a wrong password and to manually select a different sign-in method.
More information
For more information about the web sign-in credential provider and the Temporary Access Pass authentication method, refer to the following docs.
- What’s new in Windows 10, version 1809 for IT Pros – Web sign-in to Windows 10 | Microsoft docs
- Policy CSP – Authentication – EnableWebSignIn | Microsoft docs
- Temporary Access Pass is now in public preview | Microsoft Tech Community
- Configure Temporary Access Pass in Azure AD to register Passwordless authentication methods | Microsoft docs

Is there a way to make password sign-in the default while having the web sign-in as an available option? In my testing, enabling web sign-in makes it the default. If you check the registry password sign-in is still the default but that is not the experience to the user. This may be a Windows 10 glitch. What is your experience with this?
Hi George,
I’m at least not seeing that behavior with newly deployed devices. I do know that there is a GPO setting (Assign a default credential provider) that could be used to set a default credential provider.
Regards, Peter
Is there a way to use this now? If we configure this we always must logon with Temporary Access Pass otherwise the logon failed. In our scenario we want to use this with MFA (Pushnotifciation or SMS). That’s not possible any longer? Users wil get: Access Pass must be used for Web Sign In. Contact your admin to get an Access Pass.
Hi Rick,
Web sign-in is not meant to be used as an alternative method for MFA. The main scenario is Temporary Access Pass to get a user up-and-running.
Regards, Peter
Hi! Encountered this: AADSTS130506: Access Pass must be used for web sign in. Contact your admin to get an access pass. have been using web sign in as a option for a while now and all of a sudden when trying to log in with web sign in we suddenly get this error forcing TAP for web sign in. no clue as to why.
Hi hasse,
Web sign-in is meant to be used with TAP. See also the note here: https://docs.microsoft.com/en-us/windows/client-management/mdm/policy-csp-authentication?WT.mc_id=EM-MVP-5001447#authentication-enablewebsignin
Regards, Peter
MFA for Windows log-in is an expectation of auditors and cyber insurance providers. Web login was previously able to achieve this (https://www.stephanvdkruis.nl/2019/03/configure-windows-10-web-sign-in/) . Has this functionality been deprecated? I know MS is pushing passwordless authentication but industry standards have not changed for authentication methods yet.
Hi Patrick,
As mentioned in the docs (https://docs.microsoft.com/en-us/windows/client-management/mdm/policy-csp-authentication?WT.mc_id=EM-MVP-5001447#authentication-enablewebsignin), web sign-in is focused on TAP. To my knowledge it’s not meant to be used as an alternative to MFA.
Regards, Peter
Hi Peter,
I’m hoping you can help me / point me in the right direction.
We were previously using Web Sign-In exclusinvely with passwordless for PC’s in Meeting Rooms and other Shared PC’s.
With recent changes, Web Sign In has stopped working with Passwordless and now only works with Temporary Access Pass.
This has broken ALL shared Win10 PC’s across our entire client base, requiring an urgent change of direction.
If we are in a true passwordless environmment, how should we be targeting User authentication on shared Windows 10 devices that are used infrequently by Users?
We’re in a sticky situation with this and currently issuing TAP’s to all Users until we identify and implement the solution.
Any help would be greatly appreciated.
Cheers
David
Hi David,
Have you looked at security keys?
Regards, Peter
Hi David, did you find a way to reanbel phone sign-in with the web sign.in feature?
Hi Fabian,
Keep in mind that web sign-in was not made for that.
Regards, Peter
hello,
thanks for this explanation of TAP. I try to use in autopilot/intune scenario but they doesn’t works.
It works after enrollement and intune deployement, but not just after the autopilot configuration.
I’m on the loggin password text box and i have not the “sign in option”, even with a bad password.
If i’m loggin, the intune deployment continue, if i lock the session, i have sign in option directly.
i’m on win10 20h2
no mfa on my user
Hi Davzell,
Currently the web sign-in feature is still in preview. And I’ve noticed difference in behavior over time.
Regards, Peter
Does this also work when forcing the Security login as you scribed in your previous posts: https://www.petervanderwoude.nl/post/requiring-the-use-of-windows-hello-for-business-for-interactive-logons/
We implemented the that in our organization, but we want to have a work around when users lost/forgot their security key. Web sign in is a possible option, but when forcing the use of a security key this may not work.
Hi SteveAdmin,
I’m sorry but I haven’t had the need to test that combination yet. It does make sense though. Curious what the results were that you’ve seen.
Regards, Peter
Peter,
I’ve tried setting it up, but i’m running into a problem when enrolling a new device.
The first time logon screen works fine and asks for the TAP.
The second time however we need to use the web sign-in function.
The policy itself works fine, but new devices don’t receive the policy before the second login.
Did you run into this issue and if so, how did you fix it?
Thanks in advance
Hi Wouter,
Are you saying that the login is defaulting to web sign-in all the time?
Regards, Peter
Hello Peter,
The button wasn’t available yet.
We changed the assignment from a user group to All Devices and it worked immediatly.
I’m guessing that user policies only apply once the user has succesfully logged in, though i have not tested it any further.
Regards,
Wouter
Ah, okay. Yes, when you’re using a user assignment, the configuration will be applied to late.
Regards, Peter
Hi Peter:
Thank you for this article. It has been very helpful.
We are able to use TAP using Web sign in after initial onboarding using Auto Pilot. However, the option to use TAP and web sign in logo do not appear as part of Auto Pilot.
We are able to login using Security Key as part of the Autopilot.
Is TAP supposed to work with Autopilot? We appreciate your help and expert guidance.
Hi Ashwin,
Are you saying that you have TAP enabled for your user, but you don’t get the sign-in for using a TAP?
Regards, Peter
Hi Peter:
We have enabled TAP for all users. Here is what we are seeing.
– TAP works for web app sign in
– TAP works **AFTER** logging into Windows device for the first time.
– TAP does NOT work while trying to login to the device fir the first time.
The only option we see is Security Key (which works) and Password based authentication. If it helps we are also using third party IdP with Azure AD tenant in a federated mode.
Regards,
Ashwin
Hi Ashwin,
I don’t have recent experience with that combination. What I can do is run some tests after my vacation, to see what the current behavior is in an (Azure) AD only environment. Even in that scenario, the behavior has been on and off..
Regards, Peter
Thank you Peter for help and insight.
Regards,
Ashwin
We have been testing this for a few months now, until today …… a number of Users on different computers all of a sudden are unable to sign-in with a “New User” login and no option to do anything on device. The username behind this display name is DefaultUser100000. Only fix is to shutdown and turn on again a number of times before getting option for “Other User” then signing in.
I have seen a few reports that this is due to the Web Sign-in, but wanted to get others feedback on this.
Hi David,
Are you using web sign-in only for TAP?
Regards, Peter
Nice Peter! Didn’t know you had an article about this 🙂
Thank you, Jop!
Does this work at all for hybrid joined devices? Out IAM team would love to move to passwordless in general, but the being able to log onto a device in the first place to configure your MFA/Win Hello/ Fido2 key is a bit of a blocker- especially as we require you to set those up from a company device behind Conditional Access rules.
Thank You
Hi Paul,
Not completely yet. See also: https://learn.microsoft.com/en-us/azure/active-directory/authentication/howto-authentication-temporary-access-pass?WT.mc_id=EM-MVP-5001447#windows-device-setup
Regards, Peter
Hi,
trying to use TAP during the device enrollment to Intune (AAD only) without providing the password to the users.
During the first sing-in screen it allows me to enter TAP (so far so good). On the following sign-in, only password and smart card option are provided as sign-in method.
As a workaround I have enabled web sign-in, but I still don’t get the web sign-in option on the second sign-in during the device enrollment. Once the device is enrolled, the Web- sign-in is available.
Any help would be appreciated!
/BR
Hi S Kremic,
I would say that it depends on how the policy is assigned (user versus device). Besides that, how many sign-ins do you have during your Autopilot experience?
Regards, Peter
This is cool, but has some weird behaviour.
Login fails, because its asking for TAP…which I didnt set up. But I got passwordless phone sign in, and the auth app rings the bells and whistles asking me to input code on screen. But there is no code on screen…only error asking for TAP after inputing my UPN.
(Client is windows 11)
Hi Eirik,
Are you trying to use it for something else? Nowadays it’s only supported for TAP.
Regards, Peter
aha ok, since it triggered the authenticator app I have setup I thought it was supposerd to work with passwordless setup. I understand if only TAP is supported, but its weird that the app sends a notification as well when I have no TAP on the user.
Totally agree that it’s weird behavior, Eirik.
Not sure why it would be doing that..
Regards, Peter
Hey Peter, Microsoft posted an article mentioning Windows 11 22H2 with the September update can work with more then just TAP, but I haven’t been able to make it work yet: https://learn.microsoft.com/en-us/windows/security/identity-protection/web-sign-in/?tabs=intune
Hi Sepa,
I actually just posted a new blog post about: https://www.petervanderwoude.nl/post/working-with-web-sign-in-on-windows-11/
Regards, Peter
Hi Peter. I hope all is well in your world!
I’m running into an unusual problem with web sign-in that I’m hoping you can assist with. We’re using TAP as a method to setup machines for users before putting it in their hands.
On Windows 11 when we manually set the registry value to enable web sign-in, the options appear on the login screen as expected.
On Windows 10, even with the registry value in place, we’re not seeing the web sign-in option at the login screen.
Shame on us but we ran into this issue a few months ago but it apparently wasn’t documented, so I don’t recall exactly what we did. But, it had something to do with Windows Hello for Business, like enabling it for the user and setting up a PIN.
Are you aware of any prerequisites that would prevent the web sign-in option from appearing on Windows 10, even though the registry value is in place?
Any help is greatly appreciated!
Hi Julius,
I’m not familiar with anything else then just an Azure AD joined device.
Regards, Peter
If a DeviceLock policy is enabled as part of ESP, it can produce what you are describing.
Read more in the known issues here. https://learn.microsoft.com/en-us/mem/intune/enrollment/windows-enrollment-status#known-issues
I tried pushing this to 3 different computers and while I can go into Azure to create a PIN for a user, I never get the globe icon in my Sign-in options. I even tried to do this all through OMA-URI Settings in Intune:
./Device/Vendor/MSFT/Policy/Config/Authentication/EnableWebSignIn = 1 (Integer)
./Device/Vendor/MSFT/Policy/Config/Authentication/PreferredAadTenantDomainName = my domain name (String)
I can’t for the life of me figure out how to get the web icon to pop up to even test if the sign in code works.
Hi Michael,
Is the device Azure AD joined?
Regards, Peter
Could Web Sign-In/TAP an option for Administrators to “Run as Administrator” during a remote session on a device which has disabled the password credential provider?
Hi Thilo,
Apologies for the late reply, as I was enjoying my vacation. Not sure what you mean. You mean that when you use Run as admin that it would rely on Web Sign-in?
Regards, Peter
Hi,
For all IT Engineers out there who are trying to enable WebSignIn, you can do this without Intune.
We are on a project where we are trying to enroll AAD Devices with a Temporary Access Pass, which means we no longer need to rely on the user’s password. You can enroll the Device to AAD with a TAP password, but to enroll the device in Intune, you need to sign in to the user’s profile. TAP only works if WebSignIn is enabled. To enable WebSignIn without the need for Intune (Setting Catalog or OMA-URI won’t work as the device is not yet in Intune 🙂 ) you can follow the steps below:
While you are still signed in as the local admin, you need to add the below Key on the Registry to enable WebSignIn:
Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\PolicyManager\current\device\
You need to add a new key: Authentication
and inside the Key you need to add DWORD – EnableWebSignIn with the value 1. This will enable WebSign In.
Enjoy 🙂
That is the registry key as configured by Intune. So, be aware of potential conflicts when doing something like this.
Regards, Peter
I have defined this within InTune for some testing purposes. I have validated that these registry settings are indeed being set yet I do not have the Web Sign In icon available at the desktop login prompt. It refuses to show.
Hi Grant,
Can you provide some more details around you the configurations that you’re using, the Windows version, when it’s not showing, etc.?
Regards, Peter
So I believe I have determine the issue. I have two testing laptops – one that was provisioned with Windows 11 23H2 and was an existing laptop on my Active Directory domain. It is showing as Microsoft Entra Hybrid Joined. The other is also a Windows 11 23H2 and was provisioned using Autopilot – it was not on the domain and is now showing as Microsoft Entra Registered.
The laptop that is Entra Hybrid joined does not show the Web Sign in component. The one that is Entra Registered is showing the component and TAP works as expected.
So, the issue appears to be with hybrid joined devices.
Hi Grant,
According to the docs web sign-in is only supported on Entra joined devices.
Regards, Peter
This doesn’t work for me randomly, it sometimes does but mostly it doesn’t and it throws this event when trying to use the web sign in (and just goes back to the login screen):
Security-Kerberos Error 11 “The Distinguished Name in the subject field of your smart card logon certificate does not contain enough information to identify the appropriate domain or a non-domain joined computer”
Any ideas? I am wondering if OpenIntuneBaselines has something that is blocking it but I havent found anything, I went through it line by line.
What type of Windows Hello for Business hybrid are you using?
Regards, Peter
I’m also seeing similar behaviour. I find it’s hit and miss as to whether it will sign in.
I go through the sign in process goes to a black screen as if it’s going to login then it just goes back to the login screen. Sometimes the screen will just go black but I can still move my mouse cursor.
Did you find any more information on this or are there any logs I can check to see what’s happening during the web sign in process.