This week is a short post about configuring the default credential provider and this is basically a small addition to the blog posts of about two years ago around configuring credential providers. That time the focus was around actually making it impossible to use specific credential providers. This time the focus is around configuring the default credential provider. That can be a powerful combination, but that can also be a step in the direction of guiding users away from using username-password. So, guiding users instead of forcing users. From a technical perspective that could make it a bit easier, as it doesn’t involve removing functionalities. In this case, it simply provides the configured credential provider as the default credential provider. That default credential provider will be available when using the Other user tile on the Windows login screen. This blog post will show the steps for configuring the default credential provider, followed with the user experience.
Tip: The HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Authentication\Credential Providers registry key contains the available credential providers in the different sub-keys, on a Windows device.
Configuring the default credential provider
Before looking at configuring the default credential provider on Windows devices, it start with being familiar with the available credential providers. The initial tip already provides the location that can be used to see which credential providers are available on the devices within the environment. The table below provides an overview of the most common providers.
| Credential provider | GUID | Description |
|---|---|---|
| PasswordProvider | {60b78e88-ead8-445c-9cfd-0b87f74ea6cd} | Credential provider that is used for username-password. |
| NGC Credential Provider | {D6886603-9D2F-4EB2-B667-1971041FA96B} | Credential provider that is used for the PIN of Windows Hello for Business. |
| FIDO Credential Provider | {F8A1793B-7873-4046-B2A7-1F318747F427} | Credential provider that is used for FIDO2 security keys. |
When the credential providers are known, it’s time to have a look at the configuration of the default credential provider. That configuration can be achieved by using the Settings Catalog profile in Microsoft Intune. The Settings Catalog contains the setting Assign a default credential provider that can be used to configure the default credential provider. That setting is an ADMX-backed setting that is based on the CredentialProviders.admx. The following eight steps walk through the creation of a Settings Catalog profile that contains the required setting to configure the default credential provider.
- Open the Microsoft Intune admin center portal and navigate to Devices > Windows > Configuration profiles
- On the Windows | Configuration profiles blade, click Create profile
- On the Create a profile blade, provide the following information and click Create
- Platform: Select Windows 10 and later to create a profile for Windows 10 and Windows 11 devices
- Profile: Select Settings catalog to select the required setting from the catalog
- On the Basics page, provide the following information and click Next
- Name: Provide a name for the profile to distinguish it from other similar profiles
- Description: (Optional) Provide a description for the profile to further differentiate profiles
- Platform: (Greyed out) Windows 10 and later
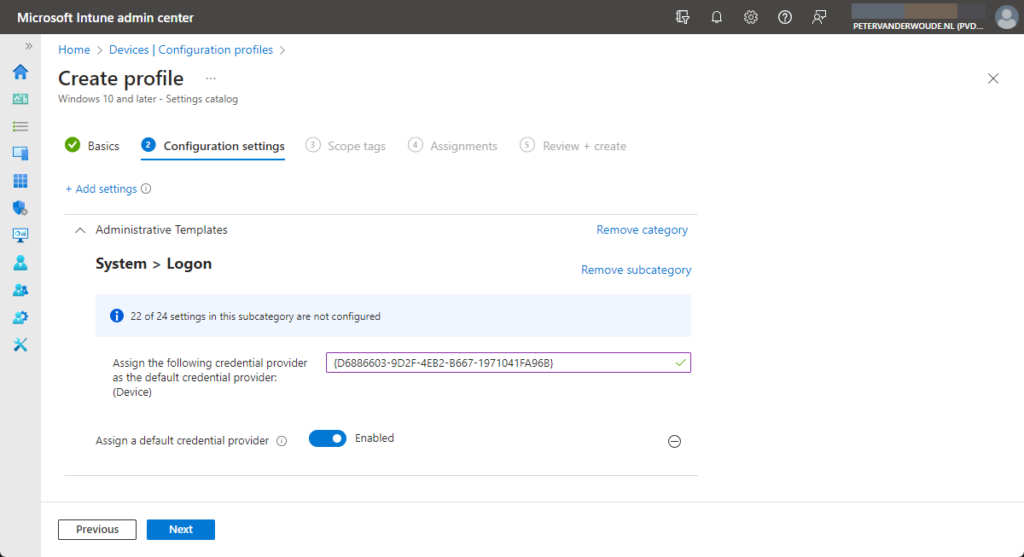
- On the Configuration settings page, as shown below in Figure 1, perform the following actions
- Click Add settings and perform the following in Settings picker
- Select Administrative Templates as category
- Select System > Logon as subcategory
- Select Assign a default credential provider as setting
- Switch the slider with Assign a default credential provider to Enable, provide the CLSID of the required credential provider with Assign the following credential provider as the default credential provider and click Next
- On the Scope tags page, configure the required scope tags and click Next
- On the Assignments page, configure the assignment and click Next
- On the Review + create page, verify the configuration and click Create
Note: As the configuration is ADMX-backed, it can also be found in the registry of the related setting. In this case that means that it can be found in DefaultCredentialProvider at HKLM\Software\Policies\Microsoft\Windows\System.
Experiencing the default credential provider
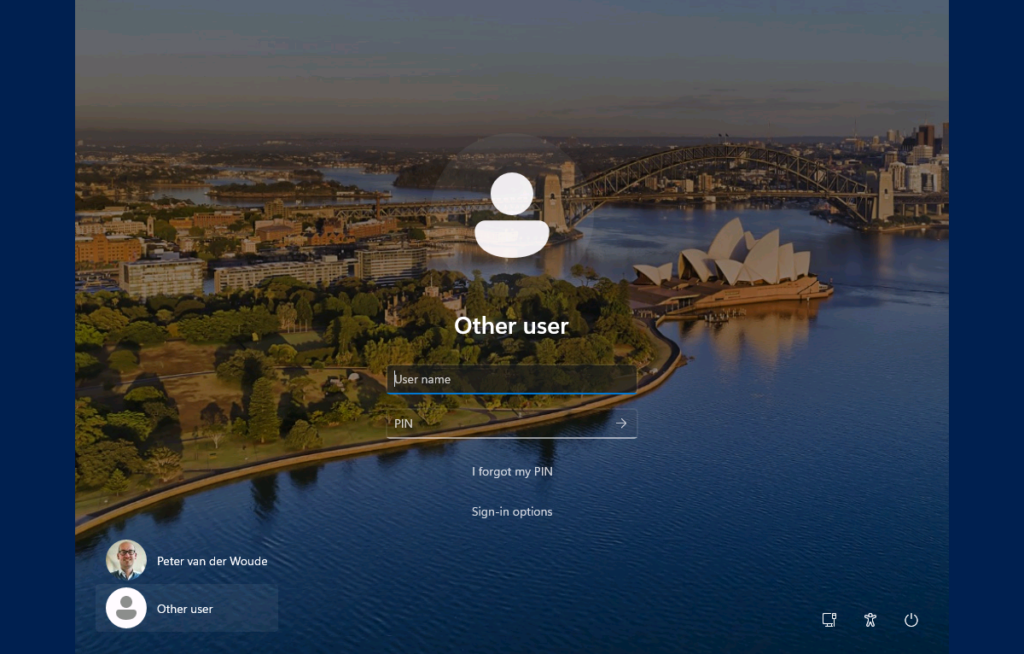
The best method for experiencing the configuration of the default credential provider, is by using the Other user tile on the logon screen of Windows (as shown below in Figure 2). For the clarity of the configuration on a VM, the used configuration for the example requires the NGC Credential Provider. In other words, it requires the PIN that is configured for Windows Hello for Business. Not the most obvious configuration, as a new user has no PIN configured, but a good configuration to show the behavior on a VM. When selecting Other user, the user will be prompted by default to use the PIN. In the real world, a logic configuration could be to have FIDO2 security keys configured as the default credential provider. That could be the first step in the passwordless journey.
More information
For more information about the passwordless strategy of Microsoft and and the different configuration options for the credential providers, refer to the following docs.
Is there a way to enable the web credentials provider (and so login with TAP) without Intune? So, registry or local security policy. I’m trying to create a password less tenant, unfortunately without Intune. The first user on a new machine can use TAP as part of the OOBE but any subsequent user, when selecting ‘other user’ only has the options of Password or PIN.
Hi Huw,
Yes, that’s possible. It’s an ADMX-backed policy, so it’s based on a registry key.
Regards, Peter
Thanks but as you pointed out, this is a terrible experience for the user. They need to give us a WHfB default provider. When you default to pin, as you said, the user doesnt have a pin if they never logged in! So its very confusing for the user, they will try to enter their entra password over and over.
If they made a provider that was the default behavior it would do Pin password for “other user” but pin if the user already is logged in. however using the password provider just basically disables the pin.
Hi Mike,
It also depends on what you want to achieve. If you want to go passwordless, there is an easier method nowadays. For that, see: https://www.petervanderwoude.nl/post/easily-hiding-the-ability-to-use-passwords-for-signing-into-windows/
Regards, Peter
Please provide an example with the OMA-URI.
URI: ./Device/Vendor/MSFT/Policy/Config/ADMX_CredentialProviders/DefaultCredentialProvider
Type: string
Value:
Above doesn’t work and result in MDMDiagReport.html: ADMX_CredentialProviders – DefaultCredentialProvider (No default value)
But what is wrong with it? What will work?
Hi Björn,
I haven’t looked at those specific requirements yet. Why would you want to configure that by using a custom URI when you have the setting available in the catalog?
Regards, Peter
Because I don’t use Intune as MDM but an other MDM provider. In my case I use Google as MDM.
It can do almost the same but not as user friendly as Microsoft itself voor their own product.
Adding custom ADMX files is no problem. But all values must be specified as OMA-URI / CSP.
Ah, that makes sense. I haven’t tested it, but I can imagine that it has to do with the setting being ADMX-backed. So, make sure that you enable it the right way.
Regards, Peter