This week is all around the Android Enterprise corporate-owned dedicated devices deployment scenario. That deployment scenario is designed to address the typical kiosk-type devices, which are often referred to as the corporate-owned, single-use (COSU) use case. This week is specifically focused on enrolling those devices in to Azure AD shared device mode. That mode will provide users with a single sign-on and single sign-out experience across all of the participating apps on the device. In other words, users will be able to sign in to the device and will automatically be signed in to any participating apps. That enables an organization to provide a little personalized experience across dedicated devices that are shared between multiple users. In this post I’ll have a look at the main configurations that are required for creating that experience and I’ll end by having a quick look at the created experience.
Important: At the moment of writing, this is still preview functionality and the participating apps are currently the Microsoft Teams and the Managed Home Screen app.
Enrollment profile for corporate-owned dedicated devices with Azure AD shared device mode
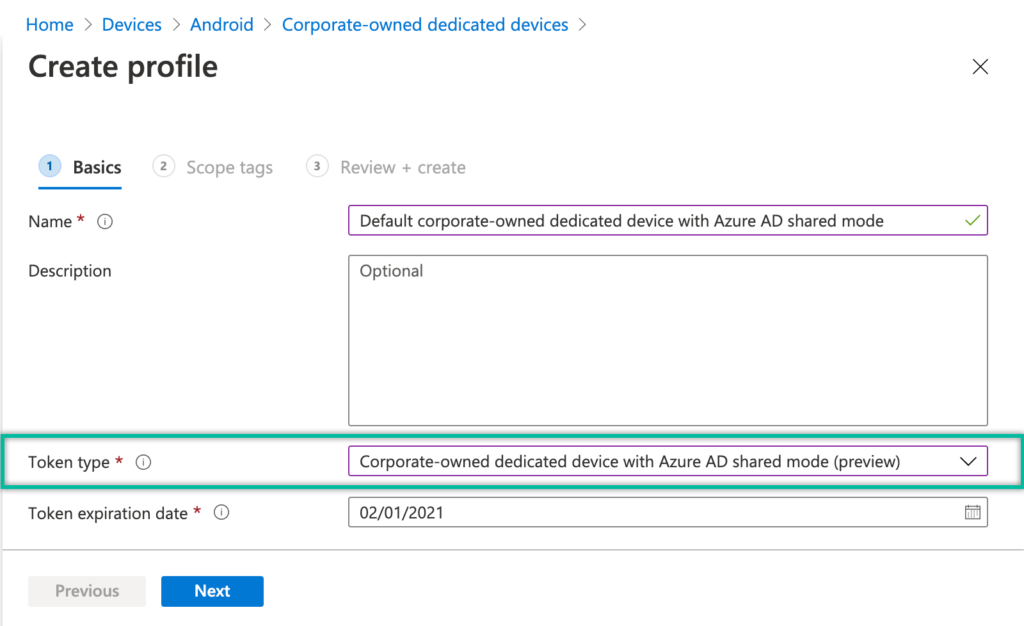
The first main configuration that is required, is the configuration of the enrollment profile for the corporate-owned dedicated devices. That’s not the most exiting configuration, but it contains an important configuration to trigger the enrollment in to the Azure AD shared device mode. That configuration is the toke type that should be configured. The following five steps walk through the process of creating an enrollment profile for corporate-owned dedicated devices with Azure AD shared device mode.
- Open the Microsoft Endpoint Manager admin center portal navigate to Devices > Android > Android enrolment > Corporate-owned dedicated devices to open the Corporate-owned dedicated devices blade
- On the Corporate-owned dedicated devices blade, click Create profile to open the Create a profile wizard
- On the Basics page, provide the following information and click Next
- Name: Provide a valid name for the enrollment profile
- Description: (Optional) Provide a valid description for the enrollment profile
- Token type: Select Corporate-owned dedicated device with Azure AD shared mode
- Token expiration date: (Optional) Select a valid date for the token expiration
- On the Scope tags page, configure the required scope tags click Next
- On the Review + create page, verify the configuration and click Create
Device configuration profile for corporate-owned dedicated devices
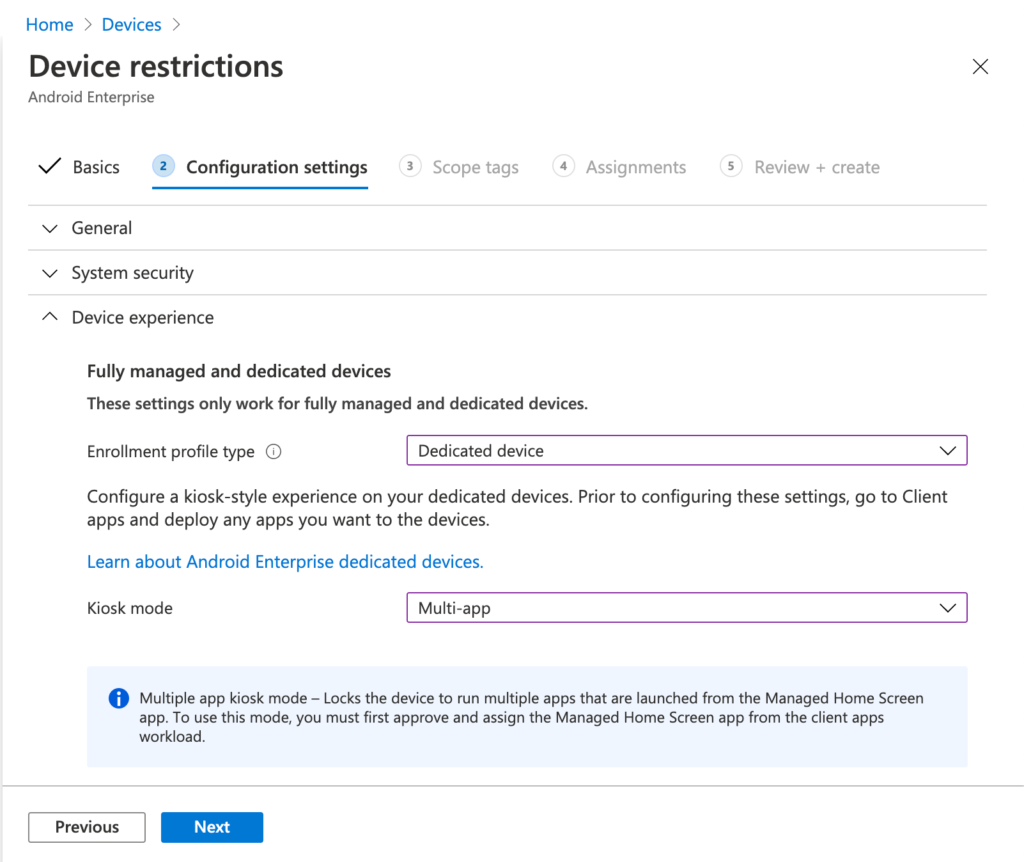
The second important configuration, is the configuration of the device configuration profile. It’s not a completely required step, but that’s the easiest method for performing a few basic configurations for a corporate-owned dedicated device. Even for a multi-app kiosk mode. The following eight steps walk through the creation of a device configuration profile that can be used for creating a multi-app kiosk mode.
Important: When creating a multi-app kiosk, keep in mind that the Managed Home Screen app is required for creating a multi-app kiosk experience.
- Open the Microsoft Endpoint Manager admin center portal navigate to Devices > Android > Configuration profiles to open the Android | Configuration profiles blade
- On the Android | Configuration profiles blade, click Create profile to open the Create a profile page
- On the Create a profile page, provide the following information and click Create to open the Device restrictions wizard
- Platform: Select Android Enterprise
- Profile type: Select Device restrictions
- On the Basics page, provide the following information and click Next
- Name: Provide a valid name for the device restriction profile
- Description: (Optional) Provide a valid name for the device restriction profile
- On the Configuration settings page, provide at least the following information and click Next
- Navigate to section Device experience
- Enrollment profile type: Select Dedicated device
- Kiosk mode: Select Multi-app
Note: The mentioned settings are only the settings to create a minimal multi-app kiosk device. Make sure to further configure any required setting for the multi-app kiosk device. That includes any further limitations, or any apps, for the multi-app kiosk mode, in this section of the configuration, but that also includes any other configurations in the other sections of the device configuration profile.
- On the Scope tags page, configure the required scope tags click Next
- On the Assignments page, configure the assignment to the required devices and click Next
- On the Review + create page, verify the configuration and click Create
Note: For the assignment of the device configuration profile, a dynamic device group can be used that only contains corporate-owned dedicated devices with Azure AD shared device mode by using the enrollmentProfileName property. That dynamic device group can be used for every assignment for this specific scenario.
App configuration policy for Managed Home Screen app
The third important configuration, is the configuration of the app configuration policy for the Managed Home Screen app. It’s a required step – at this moment – to configure the Azure AD sign-in experience to the corporate-owned dedicated device. That can be achieved by performing app configurations on the Managed Home Screen app, which are currently not available by using the previously described device configuration profile. The following seven steps walk through the creation of an app configuration profile that can be used for further configuring the multi-app kiosk mode.
- Open the Microsoft Endpoint Manager admin center portal navigate to Apps > App configuration profiles to open the Apps | App configuration policies blade
- On the Apps | App configuration policies blade, click Add > Managed devices to open the Create app configuration policy wizard
- On the Basics page, provide the following information and click Next
- Name: Provide a valid name for the app configuration policy
- Description: (Optional) Provide a valid name for the app configuration policy
- Device enrollment type: (Grayed out) Managed devices
- Platform: Select Android Enterprise
- Profile Type: Select Fully Managed, Dedicated, and Corporate-Owned Work Profile Only
- Targeted app: Select Managed Home Screen
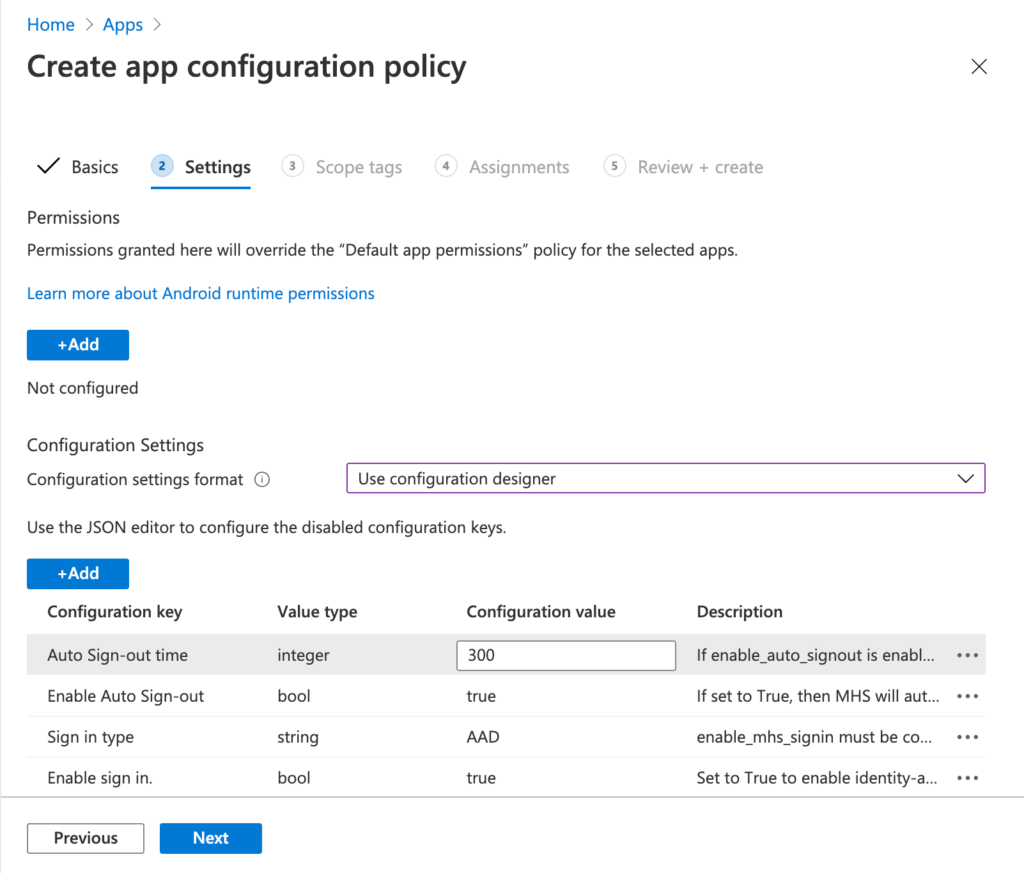
- On the Settings page, provide at least the following information and click Next
- Configuration settings format: Select Use configuration designer
- Click Add to add at least the keys and values as described in the table below to create a sign-in and sign-out experience for Azure AD accounts on the dedicated device.
Note: Most of the other keys and values can be configured by using the device configuration profile. Together with these new keys and values a few more new keys and values are introduced for configuring a sign-in wallpaper, custom privacy statement, session PIN and more. These keys and values are shown when using the configuration designer.
| Configuration key | Value type | Configuration value | Description |
|---|---|---|---|
| Enable sign in | bool | true | Enable sign-in to dedicated device |
| Sign in type | string | AAD | Configure AAD account sign-in when sign-in is enabled |
| Enable Auto Sign-out | bool | true | Enable auto sign-out of dedicated device |
| Auto Sign-out time | integer | 300 | Time (in seconds) until auto sign-out is determined when auto sign-out is enabled |
| Count down time on auto Sign-out dialog | integer | 60 | Time (in seconds) until sign on auto sign-out dialog is shown when auto sign-out is enabled |
- On the Scope tags page, configure the required scope tags click Next
- On the Assignments page, configure the assignment to the required devices and click Next
- On the Review + create page, verify the configuration and click Create
Note: At some point in time, I expect that this configuration will become available in the device restrictions profile for dedicated devices with a multi-app kiosk.
End-user experience for corporate-owned dedicated devices with Azure AD shared device mode
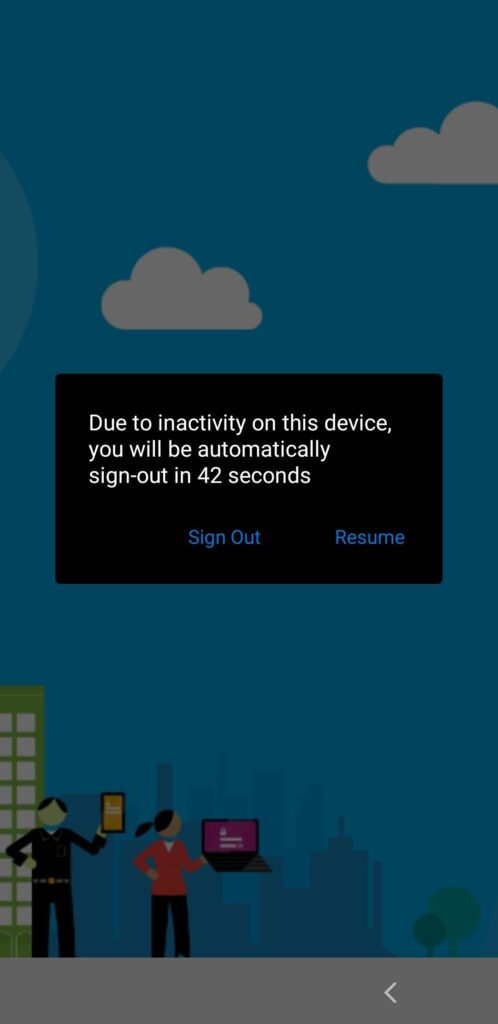
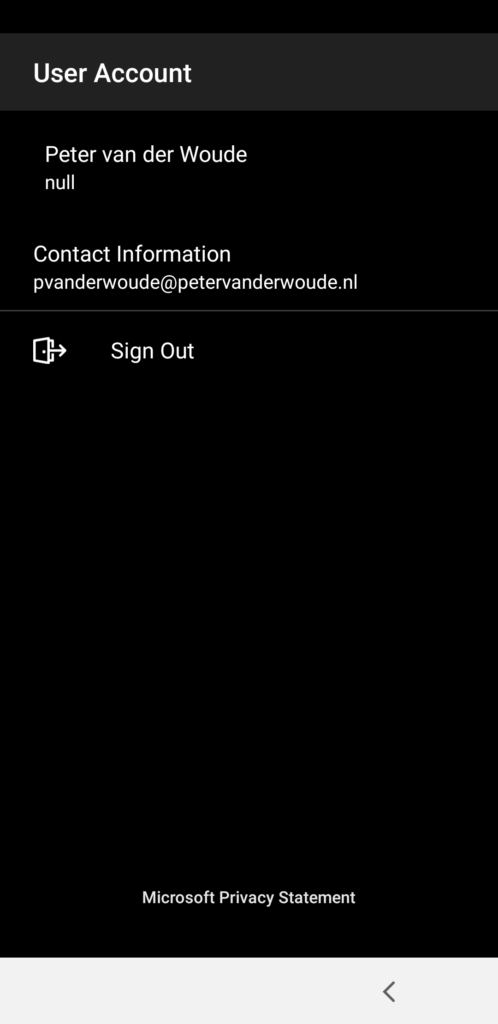
Now let’s end this post by having a quick look at the end-user experience. Below are a few examples of the created behavior. When the users get their device at the beginning of their shift, they can sign in to the device (as shown in Figure 4). After sign-in, the users receive an awesome single sign-on experience with any participating app. At this moment that includes Microsoft Teams and the experience is as smooth as advertised. Can’t wait for more apps to follow. After the users become inactive on their device, the auto sign-out timer will start and will eventually show a countdown timer in a dialog box (as shown in Figure 5). At the end of their shift the users also always have the ability to sign-out manually by using the account section of the Managed Home Screen app (as shown in Figure 6). That will completely sign off the user of the device and the participating apps. As shown throughout the different figures, the look-and-feel can be completely customized.
Note: The Microsoft Intune app and the Microsoft Authenticator app are automatically installed during enrollment of a dedicated device with Azure AD shared device mode.
More information
For more information about Android Enterprise corporate-owned dedicated devices and Azure AD shared device mode, refer to the following docs.

Excellent post!
Tested the setup last week and wasn’t particular impressed with the current state. Apps such as Edge aren’t yet compatible with the setup and the sign-in experience was pretty flaky on a Samsung Galaxy Tab 5SE with Android 10.
Thank you, John!
I have to say that I didn’t have much issues with the sign-in experience on a Samsung Galaxy S8. I do, however, agree about the apps. I would love to see a lot more. That being said, when the experience for other participating apps will be similar to the experience with Microsoft Teams, it has a lot of potential!
Regards, Peter
Hi Peter,
Great post as always. Do you know if it is possible to set up Universal Print by geolocation from an Android corporate-owned dedicated device?
Thanks!
Hi Brian,
Is there even already a mobile print for Microsoft Universal Print?
Regards, Peter
Hi Peter, that’s great stuff. I got a question
about license though. For those dedicated devices, how do you manage InTune license? Traditionally we use company portal to enroll devices as long as the users are licensed. However in the dedicated kiosks mode, no user account is needed? So how do we allocate license?
Hi Kang Du,
It depends. That the answer for every licensing question. Depending on the situation you can look at device-based licenses, but again it all depends on the licenses you have.
Regards, Peter
Hi Peter, we have setup this, but somehow the Managed Home Screen isn’t started automatically anymore (looks like after an update of android) Is this by behavior? Added the settings mentioned in your post, but unfortunately. When the app is started manually it’s working.
Hi Arno,
What version of Android are you using? If just used this configuration earlier today with success on a device with Android 9.
Regards, Peter
Hi, this was very helpful for getting over the last few hurdles we were facing setting up the multi-app kiosk. However we’ve noticed the the credentials for the previously logged in accounts are stored on the device, meaning that when the next user comes along it can just log on to other accounts freely.
I’m struggling to find settings to regulate this. Is this something you’ve experienced?
Best regards
Kristoffer
Hi Kristoffer,
Are you referring to apps in general, or apps that are supporting Azure AD shared device mode (currently only Teams)?
Regards, Peter
Hi Peter,
Thanks for the reply. I’m referring to the login into the Managed Home Screen using AAD credentials, for some reason this is stored. So if you log out from the device when your shift ends lets say, the next person can potentially just click your user in the list and get logged into the Managed Home Screen. Can’t for the life of me find a way to regulate this.
Maybe its possible to prevent this with app policy for the browser used for AAD-signin, but haven’t had the chance to test this yet, even if it should work it doesn’t feel like a real solution to this issue we’ve been experiencing.
Best regards
Kristoffer
Hi Kristoffer,
I’ve done some testing over the weekend and I don’t have the issue that I can select another user when signing in to the device. I do see challenges with apps that are not supporting this functionality yet. Those apps do cache credentials that can be used by the next user that signs in. So, only using supported apps is really important.
Regards, Peter
Hi,
I think I might have the same, or a similar issue. Sign off, manual or by triggered by inactivity all launch a browser window that informs about the sign-off.
However, after this the user is still logged on. I’m only presented with the login window at the very first logon. From that point the user is logged on at all times. After reboot. After sign-off. After exiting and re-launching MHS.
I thought this was tied to the browser I used at first, (Microsoft Edge) but I experience the same issue with Google Chrome. Are configuration of the browsers needed? Forced into Private/Incognito mode or some other method of controlling them from remembering the credentials.
Regards,
Johan
Hi Johan,
If you can recreate that behavior, I would create a support ticket.
Regards, Peter
What license is required for this, do you need a device license running azure ad shared device or will the users intune license be enough?
Hi Jimmy,
For the management of the functionality, I would expect a user license to be sufficient. That being said, I’m no licensing expert. So you might want to check with your licensing partenr.
Regards, Peter
Hi Peter,
can you tell me if there is any officail documentation regarding the “participating apps”. (As you say currently only teams and MHS)
Kind regards,
Patrick
Hi Patrick,
Have a look at the linked articles.
Regards, Peter
HI Peter,
thank you for the infos.
I try to e.g. log out with the current user but when i try to press on the icon on the managed home screen it disappeared and im on the homescreen again, no chance to log out. did i miss anything?
-Hotte
Hi Onkel,
Not sure what you mean. Do you mean that you can’t sign out at all and get back to the login screen? Not even via Teams?
Regards, Peter
Hi Peter,
Great article.
I am trying to exclude Edge logons from our MFA conditional Access policy (by ‘device marked as compliant or AD registerd’) however it seems that Azure does not recognize the Kiosk device, and therefore enforces MFA.
Any idea what might be the reason for Azure to not recognize the device (state)?
Hi T.Dykstra,
Can you provide some more details about your configuration and the results in the sign-in logs?
Regards, Peter
Hi, did you figure this one out? I think I have a similar situation. When the device is enrolled as Android Enterprise Dedicated Devices, a Conditional Access with Compliant Device is not possible to achieve, even if the device is marked as compliant in Intune. Any user-less device can not be used this way with Conditional Access. I was looking for a solution for this, and my search sent me to this article.
Hi Thomas / Peter,
i noticed the sam. Since enrolment of CODD (Corporate-owned dedicated devices) is user-less therefore we noticed none of conditional access can be applied to our devices in this category. Appreciate if any of you able to find answer/solution to this. Thanks.
Are you being blocked on every logon attempt? If so, your only option might be to explicitly exclude those devices from specific scenarios..
Regards, Peter
Thanks for your tip, PEter. I think the solution would be to exclude these devices from Conditional Access. I am reading you blog post now regarding filter for devices in CA setup.
Hi Peter,
Thank you for your amazing work, I’m testing the configuration on a A32. Does the MHS is supposed to be launched automatically? When I launch and log me in it’s empty but I’ve installed Teams. Is there a settings where I can push teams into MHS?
Thank you for your help
Regards
Hi Julian,
When using the Azure AD shared device mode, the sign-in page should be the start page of the device. And within your configuration profile you can configure the apps that you would like to appear (with the custom app layout).
Regards, Peter
Hi Peter,
Thanks for your answer, I didn’t see the layout, it’s fine now :).
Thank for your help.
Regards
Hello!
When the users log in the Manged home screen and tries to open any application it seems like it get open in fullscreen, meaning they will not see the clock,date or the battery % it completly vanish.
Anyone know how to fix this?
Hi Michael,
You can find an overview of the available settings here: https://learn.microsoft.com/en-us/mem/intune/apps/app-configuration-managed-home-screen-app
Regards, Peter
HI Peter,
Great article and very clear, but I’m experiencing some issues.
I’m trying to configure a dedicated android device in shared mode, and used your blog to set the app config settings on the Managed Home Screen app, but when I deploy it to the targeted devices I get a conflict on the AndroidForWorkMobileAppConfiguration.PayloadJson & AppConfig:com.microsoft.launcher.enterprise settings.
I also read in the Microsoft articled that a Cloud device administrator should register the device first with the authenticator app, but I thouhgt the enrollment would do this for you.
Have you seen these issues before?
Regards Michael
Hi Michael,
The first message seems to be an overlap in what you configure in the device configuration profile and the app configuration profile. Nowadays the device configuration profile contains nearly all the settings that you might need. The second message is not something from the Intune docs. The Intune docs state that Intune handles the enrollment automatically (see intro: https://learn.microsoft.com/en-us/mem/intune/enrollment/android-kiosk-enroll).
Regards, Peter