This week is all about safeguard holds. More specifically, the ability of opting out of safeguard holds. Safeguard holds prevents devices with a known compatibility issue from being offered a new Windows 10 feature update by using Windows Update. That protects the device and user from a failed or poor experience with the Windows 10 feature update. Starting with the October 2020 security update, devices running Windows 10, version 1809 and above, receive a new setting that can be used for opting out of safeguard holds. In this post I’ll start with an introduction to safeguard holds, followed with the steps of creating a device configuration profile for opting out of safeguard holds.
Important: Opting out of a safeguard hold can put devices at risk from known performance issues.
Introduction to safeguard holds
Safeguard holds prevents devices with a known compatibility issue from being offered a new Windows 10 feature update by using Windows update. Microsoft uses quality and compatibility diagnostic data to identify issues that might cause a Windows 10 feature update to fail or roll back. When such an issue is found, a hold can be applied to Windows Update. That hold is the safeguard hold and that hold will prevent affected devices from installing the Windows 10 feature update by using Windows Update. That will protect those devices from a failed or poor performance experience. In other words, safeguard holds prevent devices with a known compatibility issue from being offered a new Windows 10 feature update. All to ensure a good experience for the users.
A safeguard hold will be released once the issue is fixed and the quality and compatibility diagnostic data confirms it. Once a safeguard hold is released, Windows Update will resume with offering the Windows 10 feature update to the affected devices. This also means that safeguard holds only affect devices that use Windows Update (for Business). Feature updates that are delivered via other channels, like an installation media, or Windows Server Update Services (WSUS), are not affected by safeguard holds.
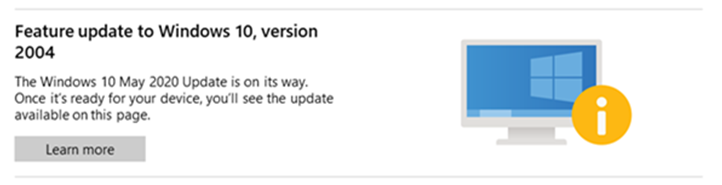
Figure 1: Example of a safeguard hold message (source: Microsoft docs)
For administrators it was already possible to use Update Compliance to see which devices are unable to install a new Windows 10 feature update due to safeguard holds. However, administrators did not have information on which particular hold was preventing the device from installing the Windows 10 feature update. That has changed. Update Compliance now contains queries to help administrators to retrieve the data related to the specific safeguard holds.
Configuration of opting out of safeguard holds
Before looking at the configurations for opting out of safeguard holds, keep in mind that the preferred path for validating new feature updates is the Windows Insider Program for Business Release Preview Channel. When that’s not an option (or was not an option), only opt out of safeguard holds for validation purposes. Don’t use it as a method to bring users to the new Windows 10 feature update. The hold is applied for a reason.
For opting out of safeguard holds, Microsoft has introduced a new ADMX-backed policy setting as part of the Update policies in the Policy CSP. That newly introduced ADMX-backed policy setting is DisableWUfBSafeguards and that policy setting can be configured to two different values that are further described in the table below.
| Policy | Description |
|---|---|
| DisableWUfBSafeguards | This policy setting can be used for opting out of safeguard holds and is an ADMX-backed policy setting. The value for this policy setting is 0 and enables the safeguard hold functionality. The alternative value for this policy setting is 1 and is used for opting out of any safeguard holds. |
To apply the DisableWUfBSafeguards setting, a custom device configuration profile can be used. The following 9 steps walk through the required steps to create that custom device configuration profile, with that policy setting.
- Open the Microsoft Endpoint Manager admin center portal navigate to Devices > Windows > Configuration profiles to open the Windows | Configuration profiles blade
- On the Windows | Configuration profiles blade, click Create profile to open the Create a profile page
- On the Create a profile page, provide the following information and click Create to open the Custom wizard
- Platform: Windows 10 and later
- Profile type: Custom
- On the Basics page, provide the following information and click Next
- Name: Provide a valid name for the custom device configuration profile
- Description: (Optional) Provide a valid description for the custom device configuration profile
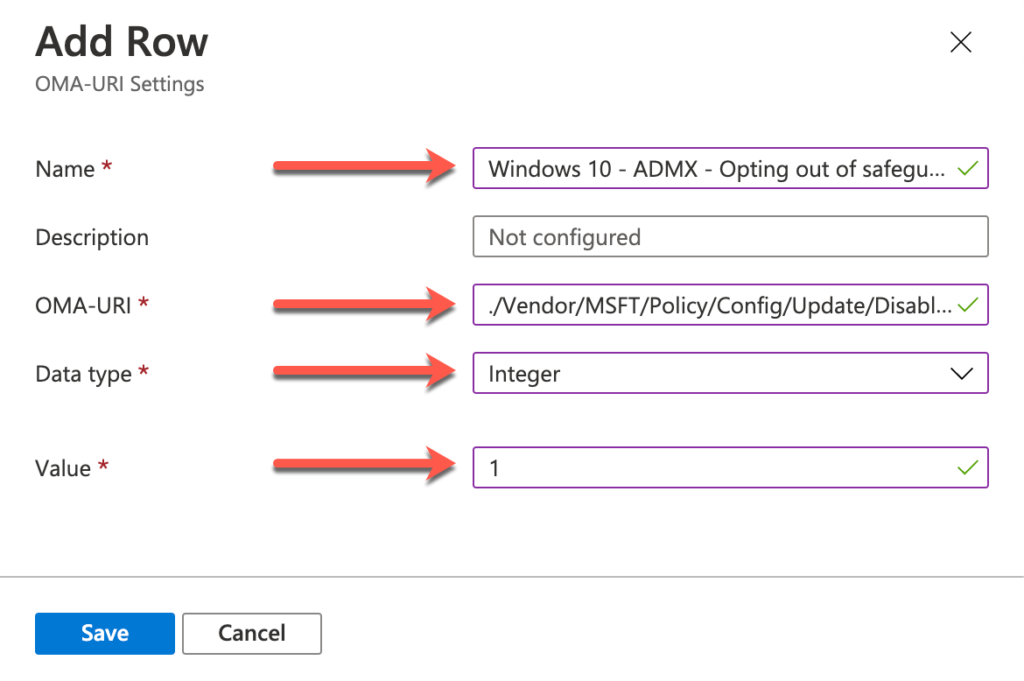
- On the Configuration settings page, click Add to open the Add Row page. On the Add Row page, provide the following information and click Add (and click Next back on the Configuration settings page)
- Name: Provide a valid name for the OMA-URI setting
- Description: (Optional) Provide a valid description for the OMA-URI setting
- OMA-URI: ./Vendor/MSFT/Policy/Config/Update/DisableWUfBSafeguards
- Data type: Select Integer
- Value: 1
- On the Scope tags page, configure the required scope tags click Next
- On the Assignments page, configure the assignment to the required users and/or devices and click Next
- On the Applicability rules page, configure the applicability rules (think about the existence of this setting for only the Pro, Business, Enterprise and Education edition and the existence of this setting for only the 1809 version and later) and click Next
- On the Review + create page, verify the configuration and click Create
Note: At some point in time this configuration will probably become available in the Microsoft Endpoint Manager admin center portal without the requirement of creating a custom device configuration profile.
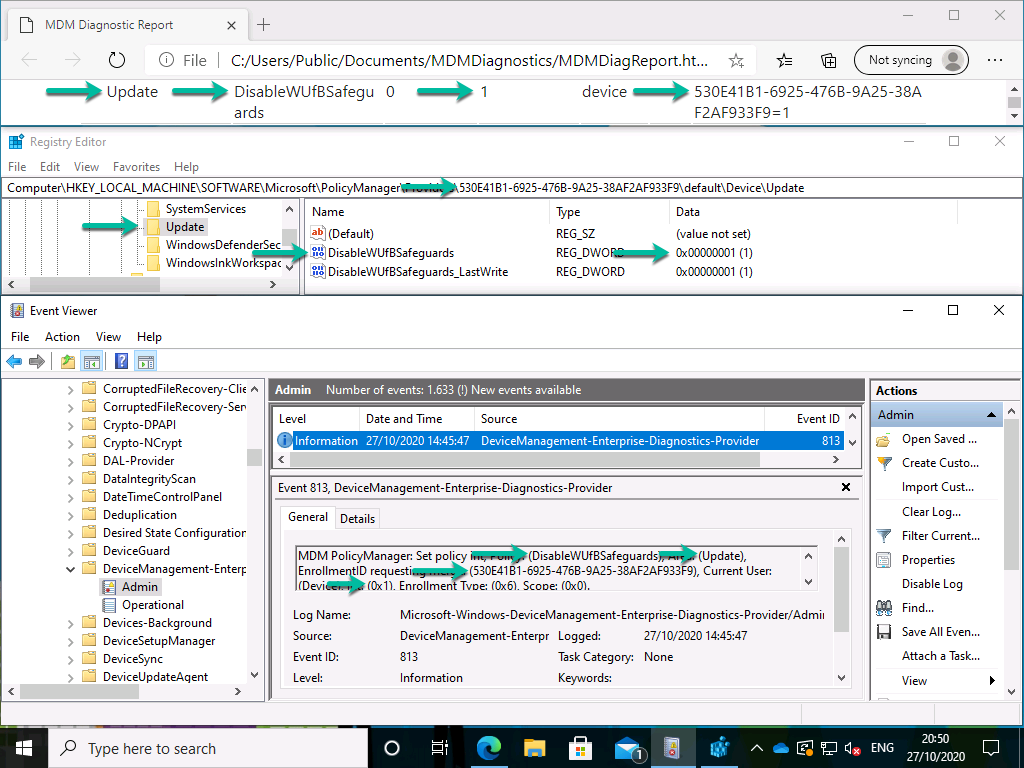
After applying the custom device configuration profile for opting out of safeguard holds, there is not a real difference in end-user experience to show. So, to verify the results, look at the familiar places for verifying configurations. The most common are shown below. The Advanced Diagnostic Report, the Registry and the Event Viewer. For convenience, I’ve marked the different values to look at and how those locations are related.
Note: After installing a new Windows 10 feature update, the value of this policy will revert to Not configured.
More information
For more information about (opting out of) safeguard holds, refer to the following docs.