This week is also all about filters. Last week was about filters for assigning apps, policies and profiles to specific devices in Microsoft Intune and this week is about filters for devices as a condition in Conditional Access policies. Filters for devices are a nice addition to Conditional Access policies to only target specific devices. A great option for addressing specific scenarios. This post starts with a short introduction about filters for devices, followed with the steps for configuring a filter within a Conditional Access policy. This post ends with the administrator experience.
Important: At the moment of writing, filters for devices are still public preview. For Azure AD features that means that the feature is provided without a service level agreement, and that the usage of the feature is not recommended for production environments.
Introducing filters for devices
Filters for devices are a great method for filtering devices based on Azure AD device properties. Within a Conditional Access policy it was already possible to filter devices from the policy by using the device state. Filters for devices are basically a super-super set of that capability. By using filters for devices it’s possible to not only filter devices based on the device state, but also on 10+ other device properties. Those device properties enable the IT administrator to specifically include, or exclude, devices based on the value of those properties. The different device properties that can be used in filters for devices are described in the table below.
| Device property | Property | Value | Description |
|---|---|---|---|
| Device identifier | deviceId | String | The unique identifier set at time of registration |
| Display name | displayName | String | The display name of the device |
| Manufacturer | manufacturer | String | The manufacturer of the device |
| MDM application identifier | mdmAppId | String | The application identifier used to register device |
| Model | model | String | The model of the device |
| Operating system | operatingSystem | String | The type of the operating system on the device |
| Operating system version | operatingSystemVersion | String | The version of the operating system on the device |
| Physical identifiers | pyhsicalIds | String | Used to store the unique value assigned to imported Windows Autopilot devices |
| Profile type | profileType | Selectable | The profile type set for the device |
| System labels | systemLabels | Selectable | The list of system labels applied to the device |
| Trust type | trustType | Selectable | The registered state of the device |
| Extension attribute | extensionAttribute1-15 | String | The optional configured extension attributes (1-15) |
Note: For the correct string values, of the different device properties, simply verify the different device resource type properties by using the Graph Explorer (or by using PowerShell).
Configuring and using filters for devices
Filters for devices are not reusable and are configured and used per Conditional Access policy. That doesn’t matter too much, as filters for devices are really meant for configuring special configurations. Exceptions. When configuring and using filters for devices, it’s important to keep in mind that those filters are based on Azure AD device properties. That means that when a device is not registered or joined in Azure AD, it’s not possible to work with positive operators for the different properties. That information is simply not available. Most of that type of behavior makes a lot of sense, but make sure to be familiar with the documented behavior.
Using filters for devices, enables IT administrators to differentiate the Conditional Access behavior based on the Azure AD device properties. That means differentiate the behavior based on the trust type of the device (which was already possible via the device state), or on more advanced properties like the manufacturer of the device, the model of the device, the platform of the device, or even extension attributes of the device. Either because some devices, like Surface Hub devices, need a different treatment, or because some devices are not supported (anymore) within the organization (or even prohibited). The following five steps walk through the creation of such a Conditional Access policy, with the focus on the filters for devices.
Note: The steps below show the creation of a Conditional Access policy for all users and all cloud apps with a filter for iPhone 8 devices. Those devices can be filtered by using a the Model device property.
Important: Filters for devices cannot be used together with the device state condition. That makes perfect sense, as filters for devices provide the same functionality and a lot more.
- Open the Microsoft Endpoint Manager admin center portal navigate to Endpoint security > Conditional Access, or open the Azure portal and navigate to Azure Active Directory > Security > Conditional Access
- On the Conditional Access | Policies blade, click New policy
- On the Assignments section, configure the following for the different assignments sections
- Users and groups: Select All users as the users that should be assigned with this policy
- Cloud apps or actions: Select Cloud apps > All cloud apps as the apps that should be assigned with this policy
- Conditions: Select Filters for devices and switch the slider Configure > Yes to enable additional for this policy
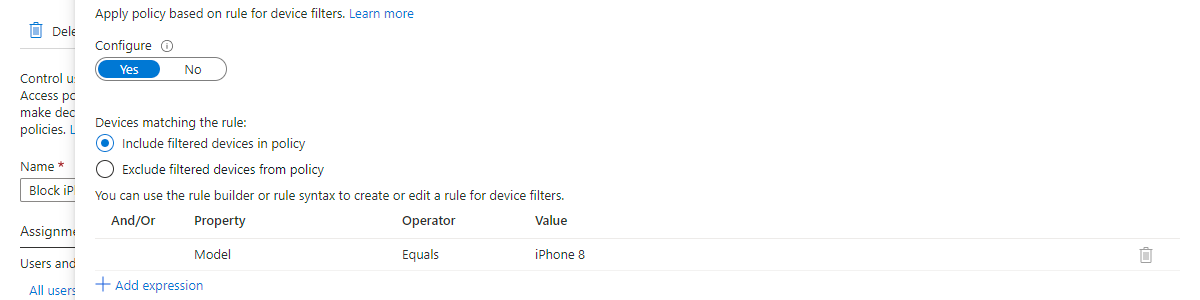
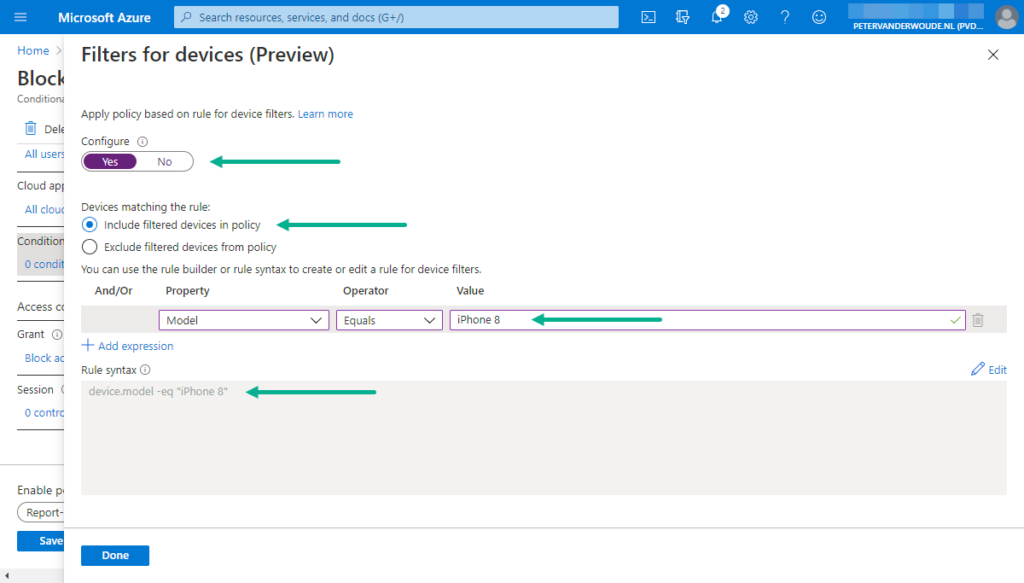
- On the Filters for devices page, as shown below in Figure 1, select Devices matching the rule > Include filtered devices in policy, configure the following expression and click Done
- Expression 1 – This expressions is used to filter devices based on the model
- And/Or: Not applicable
- Property: Select Model as value
- Operator: Select Equals as value
- Value: Specify iPhone 8 as value
- Expression 1 – This expressions is used to filter devices based on the model
- On the Filters for devices page, as shown below in Figure 1, select Devices matching the rule > Include filtered devices in policy, configure the following expression and click Done
- On the Access controls section, configure the following for the grant control
- Grant: Select Block access to block access for iPhone 8 devices to all cloud apps
- Session: Not applicable for this configuration
- Select Enable policy > On to enable the policy
Experiencing filters for devices
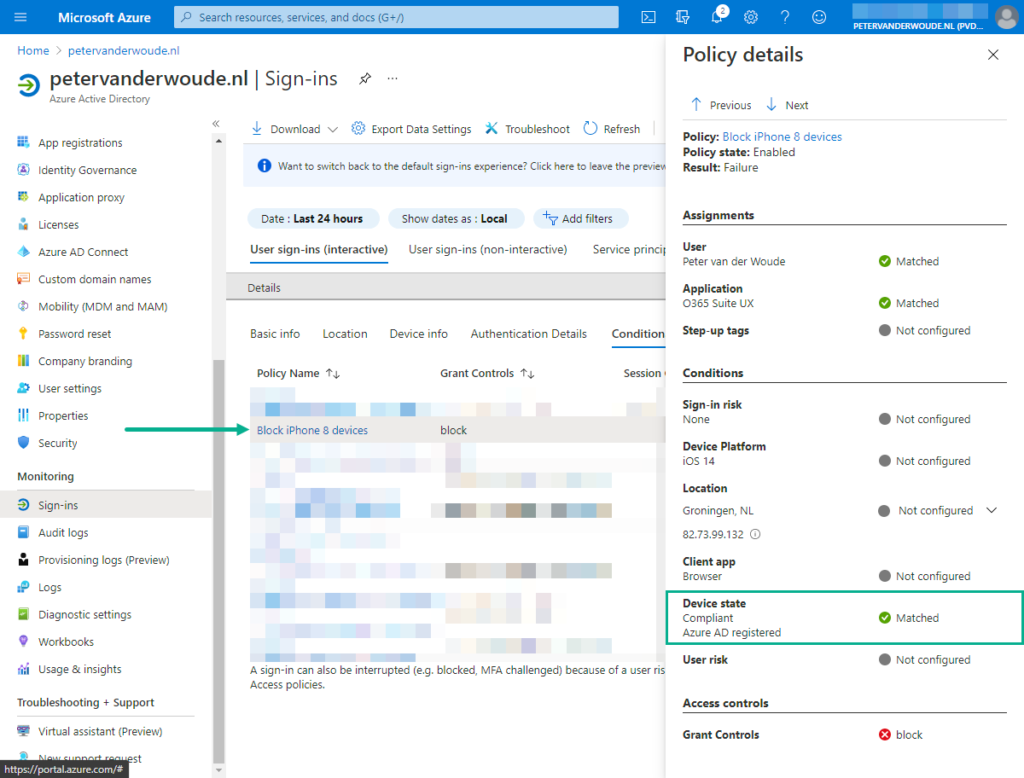
The best method to look at the results of filters for devices with Conditional Access policies, is by looking at Azure Active Directory > Monitoring > Sign-ins. That provides the information about the Conditional Access policies that are applied during the sign-in of the user. At this moment the information about a match is still logged with the Device state condition, as shown below in Figure 2. So, at this moment, that doesn’t provide the information about the exact properties that were matched.
Also, when testing filters for devices, keep the explained behavior in mind. The provided configuration is extra interesting with that behavior in mind. Positive operators (like equals) in filters for devices, won’t apply for the different Azure AD device properties when it’s an unregistered device. So, in the provided configuration, a user would still be able to enroll an iPhone 8 device, because before the enrollment the device is not registered in Azure AD and the configured filter does not apply. That, however, doesn’t mean that an iPhone 8 device can be used to access company resources. After the enrollment, the device is registered in Azure AD and the configured filter applies for every attempt to access company resources.
More information
For more information about using filters for devices with Conditional Access policies, refer to the following docs.
Great explanation as usual, thanks.
Do you have any information regarding browser requirements to have device information into sign-in log? We are planning to filter devices by “Azure AD registered” status.
I know that firefox is not supported, chrome needs the Windows 10 accounts extension. What about Edge? after several attempts I think that sign-in in into browser with the Azure AD account is needed, but I couldn’t find any evidence of that on MS documentation.
Thanks!
Hi Mike,
For CA to work, you need to sign in to the browser. See also: https://docs.microsoft.com/en-us/deployedge/ms-edge-security-conditional-access
Regards, Peter
thanks Peter, it’s definetly what I was looking for!
Mke
Thanks for the info.
Perhaps you can help with a question I have.
I am trying to exclude certain mobile devices that are already registered with our mdm solution from a CA policy using the “mdmappid” property. It sounds like this is unique to each device, but perhaps not? I’m not sure where to find this property. I’m wondering if we can find one property that would apply to all of the mobile devices we want to exclude, or if we have to exempt each device using unique identifier.
Thanks,
Alex
Hi Alex,
No, that represents the MDM that’s been used to enroll the device.
Regards, Peter
Hi Peter,
Thank you for the info! If I am looking to exclude particular dynamic group, How can I achieve this?
Hi Gianelli,
Are you looking for a user group or a device group? When the latter, what is it that you’re filtering for?
Regards, Peter
I would like to exclude a group of devices that is enrolled with a specific enrollment profile. I was hoping I could use the same property I do when I create a dynamic Azure Ad group ( “enrollmentProfileName eq”). Unfortunately, I don’t find this property when creating the filer setting.
Hi Thomas,
Sadly that property is currently not yet available in filters for CA…
Regards, Peter
hi all – has anyone figured out how to configure a device filter to utilize device physicalid info to allow only devices registered by specific user GUIDs? for AzureAD groups, the rule would look like this — “device.PhysicalIDs -any _ -match “2a6a60be-0a74-4018-870e-f7938b2febb7″”. it seems the variable name is different and it also might not accept this type of rule either. thanks for any advice on how to do this with CA.
Hi David,
To my knowledge you can’t use that type of advanced queries within filters.
Regards, Peter
This more general but I have written some of the device owner information to the extension attributes of the device after it is enrolled. I used a runbook script to add this post enrollment. Once I populated the extensionattributes of the device then I could filter using the Conditional Access Device filter. The primary use case for me was to write the users ScopeID to their device (extensionattribute5) and filter on the string (in my case I have scopes for each location NewYork, Chicago ….) You can write whatever you want into the attribute and once there you can use the device filter logic.
Great Article. Thanks for posting.
I have a customer with multiple MDM vendors. Is there different values for the mdmAppId other than for InTune or is the example I’ve seen or is this a generic value for all enrolled devices (“0000000a-0000-0000-c000-000000000000”)
Hi Daniel,
The idea is that different MDM providers have different app IDs.
Regards, Peter
Hi Peter, we are using two different MDMs in our environment. I’d like to filter out the devices being managed by the other MDM. Is there a way to find the mdmAppID value for a specific app other than Company Portal or Microsoft Authenticator?
Hi Jennifer,
It’s not an id of the client app.
Regards, Peter
Is it possible to filter by device categories? I want to apply access policy only when you are logged into a specific intune device category.
Hi Tom,
Sadly, you can’t filter on Intune properties at this moment.
Regards, Peter
* Device State previously in Preview has now been deprecated.
* Also, found the “What If” feature in Conditional Access to be an effective monitoring and troubleshooting tool.
* We have a filter to block unenrolled Android/iOS device.mdmAppId -eq “0000000a-0000-0000-c000-000000000000” -or device.mdmAppId -eq “00000002-0000-0000-c000-000000000000”
but the need is to not block personal devices accessing O365. Any thoughts on that would be appreciated.
Hi Ed,
You could just block personal device enrollment and require a compliant device. In that case, you can’t get compliant any more with a personal device.
Regards, Peter
Hey Peter I have a question sort of on this topic. We use Citrix as our VPN provider. Using the Citrix SSO app on iOS……We want to only allow Corporate (Compliant) devices to access this VPN. Is there a way we can keep personal unmanaged devices out from the Azure Cloud App (the vpn). We are using SAML authentication with Microsoft as our IDP. When we test this in the Sign-in logs it doesnt appear that the device ID is being passed so the Conditional access policy is not applying. Trying to think outside the box on maybe a different solution where we can only allow the Corporate Devices on the VPN. Any ideas at all? I was thinking maybe device filtering but cant think of a way to get that working. Thank you in advance for any thoughts!
Hi Steve,
I don’t think that filters will help you with that, as that will only help you with applying a CA policy to a device or not. So, unless that’s your goal, it won’t help you.
Regards, Peter
how to add 3 to 4 devices ID
You could use multiple lines with different IDs and an OR-statement. Otherwise you could look at using In or Not in as operator.
Regards, Peter
Hi Peter,
I try to restrict, that User can only log on Microsoft Teams on AD-joined devices. which settings are necessary for this?
Best regards,
Martin
Hi Martin,
That’s in the Grant control, were you can configure what you require for the access.
Regards, Peter