Enhance inventory reporting with local administrator information
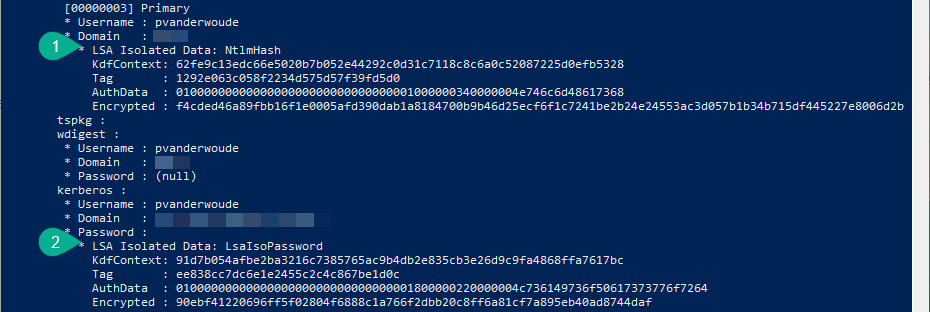
This week is all about enhancing inventory reporting with information about the local administrators on the managed Windows 10 devices. This time is not about managing the different local administrators on those Windows 10 devices, but this time is about creating a report that provides insights to the different local administrators that are configured on those Windows 10 devices. The solution to enhance the inventory reporting, relies on PowerShell, Log analytics, Workbooks and the Azure Monitor HTTP Data Collector API. PowerShell is used to gather the information on the local device and uses the Azure Monitor HTTP Data Collector API to write the gathered information to Log analytics. Workbooks are used to visualize the gathered data from Log analytics. This solution is inspired and based …