This new year starts again with something completely new. That means, some of the technology hasn’t be part of any of the posts on this blog before. This post will provide a look at using Azure Logic Apps for querying Microsoft Intune (via Microsoft Graph) and posting the results in Microsoft Teams. That’s an awesome combination for automating administrative tasks and triggering IT administrators to perform actions. The idea of this post is to show the power of that combination and to show the simplicity to automate administrative tasks. This post provides a simple example that will query status information about the Apple MDM push certificate in Microsoft Intune and posts that information in an adaptive card in a Microsoft Teams chat, when action is needed. That example can be easliy extended to other connectors within Microsoft Intune. The following is provided and shown in this post.
- Creating an app registration to provide the permissions
- Creating a workflow to get the status of the Apple MDM push certificate
- Experiencing the adaptive card to get a feeling with the result
Note: Basic knowledge of the mentioned technologies is required, as this post won’t be completely step-by-step. Besides that, the information can be easily adjusted to retrieve information about different connectors.
Creating an app registration to provide the permissions
The first action is to create an app registration in Azure AD to provide the minimum required permissions to Microsoft Graph. That app registration contains two important configurations that are required for the workflow. The app registration needs (1) the correct permissions and (2) a client secret should be created for retrieving a token in the workflow. The bullets below go through the minimal configuration that is required and will make sure that the correct information is available when creating the workflow.
- Open the Azure portal, navigate to Azure Active Directory > App registrations to create a new app registration and save the Directory (tenant) ID and the Application (client) ID for usage within the workflow
- Navigate to API permissions, provide the app registration with at least the application API permissions of DeviceManagementConfiguration.Read.All and DeviceManagementServiceConfig.Read.All and grant admin consent for those permissions, to make sure that the workflow will have enough permissions
Important: The workflow is relying on the standard HTTP action. That standard action in combination with the scheduled automation idea, works the best and easiest (the idea of this post) with application API permissions. The required permissions are specifically and minimally scoped for the app registration.
Note: The DeviceManagementServiceConfig.Read.All permissions are required for querying status information about certificate connectors, Managed Google Play and more and the DeviceManagementServiceConfig.Read.Al permissions are required for querying status information about Apple MDM push certificates, Apple VPP tokens, Apple enrollment tokens, Windows Autopilot connectors, Microsoft Defender for Endpoint connctors and more.
- Navigate to Certificates & secrets, create a new secret and save the value in an Azure Key Vault
Important: The workflow is relying on Azure Key Vault for retrieving the secret when requesting a token.
Creating a workflow to get the status of the Apple MDM push certificate
The second action is to create a workflow in an Azure Logic App. Logic apps are very similar to Power Automate, especially when looking at the (work)flow that will provide the automation. The main differences are on the licensing and focus. Logic apps are more focussed on IT and automating IT processes. For a more extensive comparision, have a look at the docs. The workflow will use the created app registration to query Microsoft Graph with the minimal required permissions. The idea of the workflow is to query for the status of the Apple MDM push certificate in Microsoft Intune and to post an adaptive card in Microsoft Teams when an action is needed by an IT administrator. To get started, make sure that a Logic app and the related workflow are created. The main actions for that are described below.
- Open the Azure portal and navigate to Logic apps to create a new Logic app, by simply walking through the steps of specifying the Basics (Resource Group, Region and more), the Hosting (Storage, Plan and more), the Monitoring and the Tags. Once created, select the Logic app, navigate to Workflows and add a new Stateful workflow.
Once the framework (the Logic app and the workflow) is in place, it’s time to actually start with the configuration of the workflow. That workflow contains all the intelligence to query Microsoft Intune and to post in Microsoft Teams. An overview of that workflow is shown in Figure 1 and the details are explained below.
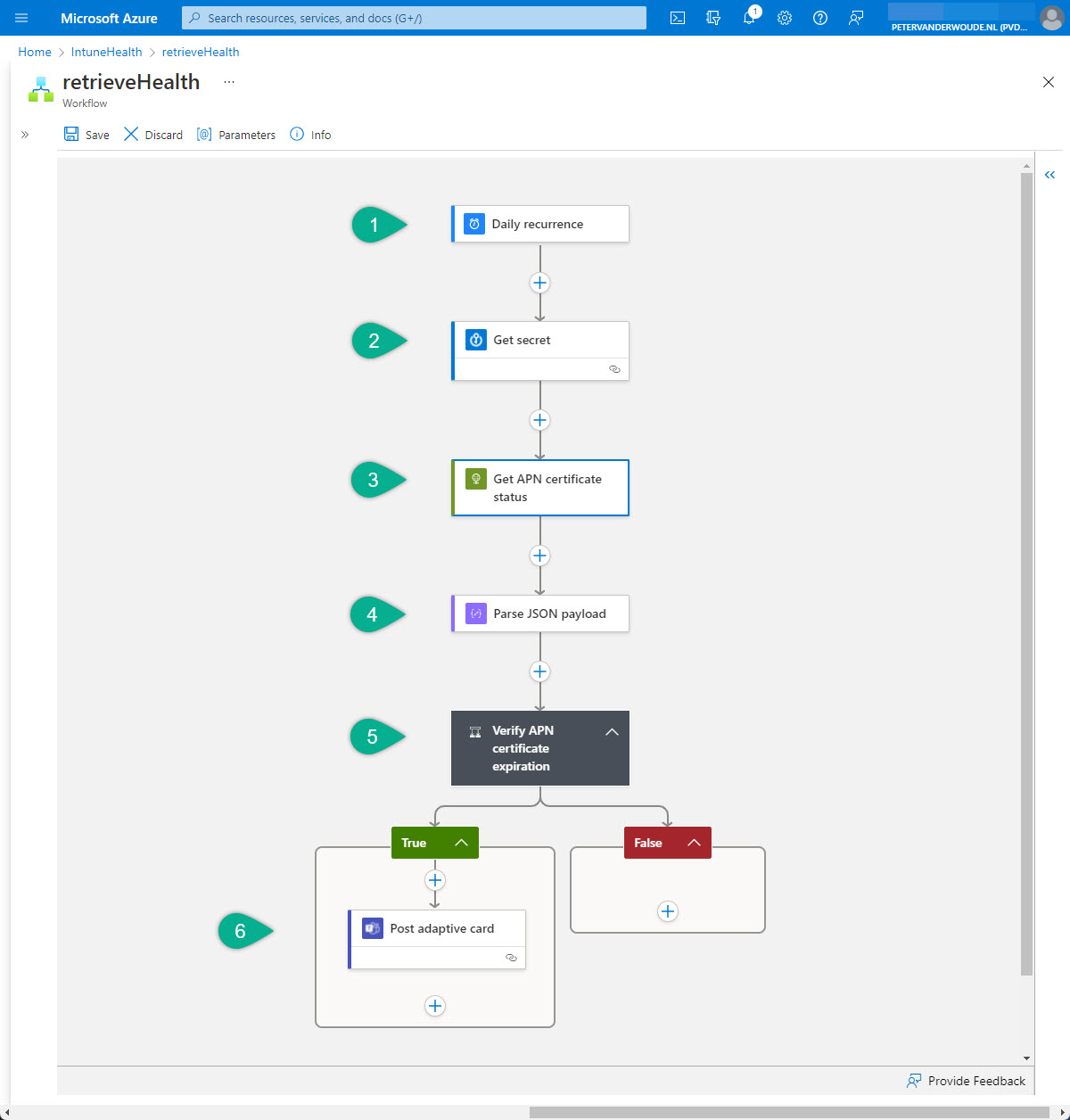
- The first step of the workflow is the Schedule – Recurrence trigger. That trigger will be used to trigger the workflow, based on a daily interval, and needs the following configurations of the different values.
- Interval: Specify 1 as value
- Frequency: Select Daily as value
- The second step of the workflow is the Azure Key Vault – Get secret action. That action will be used to retrieve the secret – to request a token – from the Azure Key Vault and needs the following configurations of the different values.
- Name of the secret: Select the name of the secret as value
Tip: To prevent the secret from being showed in the output, configure Settings > Secure Outputs to Yes.
Note: To be able to select the correct value, make sure that the managed identity of the Logic app has the required permissions to the key vault. Alternativly, connect with a user account with the required permissions.
- The third step of the workflow is the HTTP – HTTP action. That action will be used to query Microsoft Graph for the status of the Apple MDM push certificate and needs the following configurations of the different values.
- Method: Select GET as value
- URI: Provide https://graph.microsoft.com/beta/deviceManagement/applePushNotificationCertificate as value
- Authentication: Select Active Directory OAuth as value
- Tenant: Provide Directory (tenant) ID – as shown in the first bullet of creating the app registration – as value
- Audience: Provide https://graph.microsoft.com/ as value
- Client ID: Provide Application (client) ID – as shown in the first bullet of creating the app registration – as value
- Credential Type: Select Secret as value
- Secret: Select Dynamic content > (Get secret) value as value
- The fourth step of the workflow is the Data Operations – Parse JSON action. That action will be used to specify the schema of the returned JSON content of the query and needs the following configurations of the different values.
- Content: Select Dynamic content > (HTTP) Body as value
- Schema: Provide the schema as shown below as value
{
"properties": {
"@@odata.context": {
"type": "string"
},
"appleIdentifier": {
"type": "string"
},
"certificate": {},
"certificateSerialNumber": {
"type": "string"
},
"certificateUploadFailureReason": {},
"certificateUploadStatus": {},
"expirationDateTime": {
"type": "string"
},
"id": {
"type": "string"
},
"lastModifiedDateTime": {
"type": "string"
},
"topicIdentifier": {
"type": "string"
}
},
"type": "object"
}Note: An easy method to get the correct payload schema is by either doing a test run of the workflow, or by using the query in Graph Explorer, and using the response body as a sample payload to generate the schema.
- The fifth step of this workflow is the Control – Condition action. That action will be used to verify the status of the Apple MDM push certificate and needs the following configurations of the parameter to check the experiation date.
- Choose Dynamic content > (Parse JSON payload) expirationDateTime as value
- Select is less than as value
- Provide Expression > addToTime(utcNow(),31,’day’) as value
- The sixth and final step is the Microsoft Teams > Post adaptive card in a chat or channel action, when the result of the previous condition is true. That action will be used to post the status of the Apple MDM push certificate, when the expiration date is near, and needs the following configuration of the different values
- Post as: Select Flow bot as value
- Post in: Select Chat with Flow bot as value
- Recipient: Specify the recipient as value
- Adaptive Card: Provide the configuration as shown below as value to create an adaptive card that provides an overview to the IT administrator, including two buttons (a button that links to the Microsoft Endpoint Manager admin center and a button that links to the Microsoft docs)
{
"$schema": "http://adaptivecards.io/schemas/adaptive-card.json",
"type": "AdaptiveCard",
"version": "1.0",
"body": [
{
"type": "TextBlock",
"text": "Apple MDM push certificate is almost expired",
"weight": "bolder",
"size": "medium",
"wrap": true,
"id": "acTitle"
},
{
"type": "TextBlock",
"text": "Please take action by renewing the Apple MDM push certificate",
"weight": "bolder",
"wrap": true,
"id": "acSubHeader"
},
{
"type": "TextBlock",
"text": "The Apple MDM push certificate is almost expired and the information below provides an overview of the certificate and the expiration date. Have a look at the documentation to get a refresher of the actions to perform and take imediate action",
"wrap": true,
"id": "acDescriptionArea"
},
{
"type": "FactSet",
"facts": [
{
"title": "Apple ID:",
"value": "@{body('Parse_JSON_payload')?['appleIdentifier']}"
},
{
"title": "Subject ID:",
"value": "@{body('Parse_JSON_payload')?['topicIdentifier']}"
},
{
"title": "Last modified:",
"value": "@{body('Parse_JSON_payload')?['lastModifiedDateTime']}"
},
{
"title": "Experiation:",
"value": "@{body('Parse_JSON_payload')?['expirationDateTime']}"
},
{
"title": "Serial number:",
"value": "@{body('Parse_JSON_payload')?['certificateSerialNumber']}"
},
{
"title": "Days until experation:",
"value": "@{div(sub(ticks(body('Parse_JSON_payload')?['expirationDateTime']),ticks(utcNow())),864000000000)}"
}
],
"id": "acFactSet"
}
],
"actions": [
{
"type": "Action.OpenUrl",
"title": "Take action",
"url": "https://endpoint.microsoft.com/"
},
{
"type": "Action.OpenUrl",
"title": "Documentation",
"url": "https://docs.microsoft.com/en-gb/mem/intune/enrollment/apple-mdm-push-certificate-get#renew-apple-mdm-push-certificate"
}
]
}Important: The different values all contain dynamic content that is parsed from the JSON. Besides that, the last value contains a quick expression to calculate the days until experiation.
Note: This example simply posts a message directly to my IT administrator about the status of the Apple MDM push certificate. That message could also be posted in a Teams Channel. Something similar is applicable to the connected user that is used for posting the adaptive card. That user name will be shown in the posted message.
Experiencing the adaptive card to get a feeling with the result
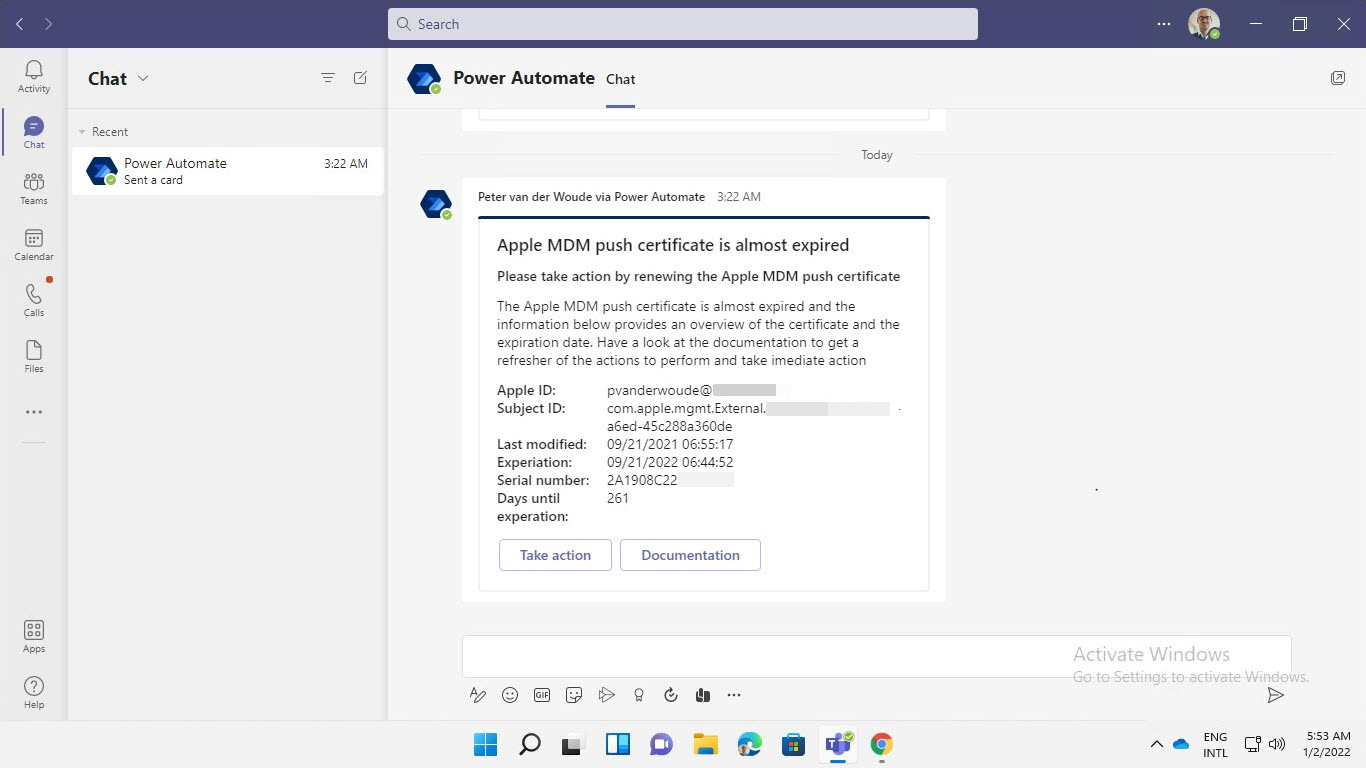
The best method to experience the adaptive card in Microsoft Teams, is by simply looking at it. The minor challenge is that my Apple MDM push certificate is not near its experation data. So, to get a feeling with the result, the conditions are switched. That will make sure that the IT administrator gets a trigger when the experation date is not near. The experience for the IT administrator is shown below in Figure 2. It provides an overview of the details of the Apple MDM push certificate and a button to take action (a link to Microsoft Endpoint Manager admin center) and a button for the documentation (a link to the Microsoft docs about renewing the Apple MDM push certificate).
More information
For more information about the different subjects that are used throughout this post, refer to the following docs.
- Adaptive Cards | A whole new way to deliver UI
- Power Automate vs Logic Apps | Microsoft Docs
- Using Power Automate to notify admins on Intune Connector health – Microsoft Tech Community
Hi Peter, thank you for your work to create this content.
Could I ask you a support? When I put in in the text cell the code related to adaptive card I am receiving the follow error: Workflow validation failed
Workflow saved successfully. Workflow validation failed for the workflow ‘MonitoringAppleCert’. The template validation failed: ‘The action(s) ‘Parse_JSON_payload’ referenced by ‘inputs’ in action ‘Post_adaptive_card_in_a_chat_or_channel’ are not defined in the template.’. do you know why and how to solve the issue?
Thank you
Hi Emanuele,
That sounds a bit like you’re using the JSON example, but using different names for the actions in the workflow.
Regards, Peter
The Client Secret has an expiration date, so will this monitoring fail when the Secret expires? Do we need monitoring for the Secret expiring as well?
Hi Stephen,
Yes! Once the secret is expired, it can’t be used anymore. Alternatively, you can also look at different methods for authentication and authorization (like a managed identity).
Regards, Peter
In that case, do you have any tips for monitoring the expiration of the client secrets? Or an example of how Managed Identities would work with this certificate monitoring, for those of us who are not Azure experts?
Hi Stephen,
I did a session with Pim Jacobs during the Nordic Virtual Summit, in which he showed an example. You can find his code here: https://github.com/IdentityMan/AzureAD/tree/master/NordicVirtualSummit
Regards, Peter