A while ago I did a blog post about managing Windows Defender of Windows 10 via OMA-DM. During that specific post I showed how to use OMA-DM, via Microsoft Intune standalone and hybrid, to configure Windows Defender. In this post I’ll do something similar for AppLocker. However, I have to admit that it was a bit more challenging for AppLocker. The main difference is that Windows 10 includes many different separate policy settings for Windows Defender, but provides a separate configuration service provider (CSP) for AppLocker.
During this post I’ll show how to create the required AppLocker XML, what the AppLocker XML looks like, what the AppLocker CSP looks like and how to combine the AppLocker XML and the AppLocker CSP. I’ll end this post with the end-user experience. During this post I’ll use the build-in Windows 10 app Candy Crush Soda Saga as an example.
Create the AppLocker XML
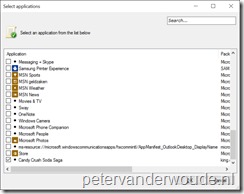
The required AppLocker XML can be created by using the Local Security Policy snap-in, the Local Group Policy Editor snap-in or the Group Policy Management snap-in. Any of these snap-ins will work in a similar way for creating the required AppLocker XML. It doesn’t matter which snap-in is used, as long as it’s being used on a Windows 10 device. That makes it easier with configuring and selecting the required apps. During the following twelve steps, I’ll use the Local Group Policy Editor snap-in for configuring the Candy Crush Soda Saga app.
Inside the AppLocker XML
Now let’s have a look at the AppLocker XML that I just created. That AppLocker XML should look like the one shown below. It should show a default allow rule and a specific deny rule on the Candy Crush Soda Saga app, both within the RuleCollection element of the Appx type. That element of the AppLocker XML is what’s required during the further configurations.
<AppLockerPolicy Version="1"> <RuleCollection Type="Exe" EnforcementMode="NotConfigured" /> <RuleCollection Type="Msi" EnforcementMode="NotConfigured" /> <RuleCollection Type="Script" EnforcementMode="NotConfigured" /> <RuleCollection Type="Dll" EnforcementMode="NotConfigured" /> <RuleCollection Type="Appx" EnforcementMode="Enabled"> <FilePublisherRule Id="a9e18c21-ff8f-43cf-b9fc-db40eed693ba" Name="(Default Rule) All signed packaged apps" Description="Allows members of the Everyone group to run packaged apps that are signed." UserOrGroupSid="S-1-1-0" Action="Allow"> <Conditions> <FilePublisherCondition PublisherName="*" ProductName="*" BinaryName="*"> <BinaryVersionRange LowSection="0.0.0.0" HighSection="*" /> </FilePublisherCondition> </Conditions> </FilePublisherRule> <FilePublisherRule Id="8ea1fe67-536d-4324-99e2-88f9c9c70321" Name="king.com.CandyCrushSodaSaga, version 1.58.0.0 and above, from king.com" Description="" UserOrGroupSid="S-1-1-0" Action="Deny"> <Conditions> <FilePublisherCondition PublisherName="CN=F80C3B33-B9E8-4F23-AB15- B97C700EFF2F" ProductName="king.com.CandyCrushSodaSaga" BinaryName="*"> <BinaryVersionRange LowSection="1.58.0.0" HighSection="*" /> </FilePublisherCondition> </Conditions> </FilePublisherRule> </RuleCollection> </AppLockerPolicy>
Inside the AppLocker CSP
Before using the AppLocker CSP it’s good to get a better understanding of the different nodes. The AppLocker CSP contains nodes for the different configuration components of AppLocker. Let’s go through these different nodes.
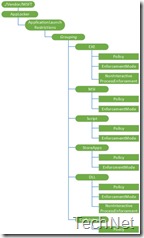 ./Vendor/MSFT/AppLocker – Defines the root node for the AppLocker configuration service provider;
./Vendor/MSFT/AppLocker – Defines the root node for the AppLocker configuration service provider; - ApplicationLaunchRestrictions – Defines restrictions for applications;
- Grouping – Defines dynamic nodes. These nodes contains a GUID naming that can be literally anything. That GUID makes sure that the un-enrollment of a device will behave as expected;
- EXE | MSI | Script | StoreApps | DLL | CodeIntegrety – Defines restrictions for launching executable applications, Windows Installer files, scripts, store apps and DLL files;
- Policy – Defines the policy for launching executable applications, Windows Installer files, scripts, store apps, and DLL files. The contents of this node is precisely the RuleCollection element as discussed in the previous paragraph.
Create AppLocker OMA-URI
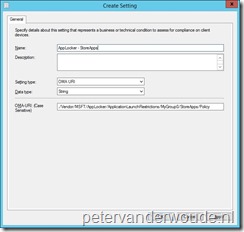
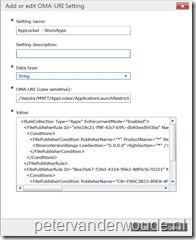
Now it’s time to use the created AppLocker XML for configuring Windows 10 devices. The key with this is that only the RuleCollection element is required that matches with the node in AppLocker CSP. With the RuleCollection element of the Appx type, I need the StoreApp node in the AppLocker CSP. This is applicable to Microsoft Intune hybrid and standalone.
Microsoft Inune hybrid
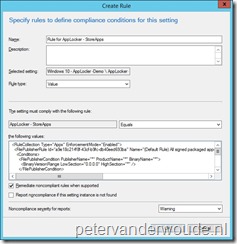
Let’s start with the configuration in Microsoft Intune hybrid. I’ll walk through the required steps to configure the required OMA-URI configuration item.
Note: This created a configuration item that can be deployed like any other configuration item, as a part of a configuration baseline.
Microsoft Intune standalone
Let’s continue with the same configuration within Microsoft Intune standalone. I’ll walk through the required steps to configure the required OMA-URI configuration policy.
End-user experience
Let’s end this post with the most important thing, the end-user experience. Actually, the end-user experience will be exactly the same as with a local or domain group policy configuration. The end-user will receive the message as shown below and the end-user can find messages in the Event Viewer. Those messages in the Event Viewer will wrongly indicate that the app is blocked by group policy.
| End-user message | Event Viewer message |
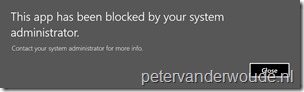 |
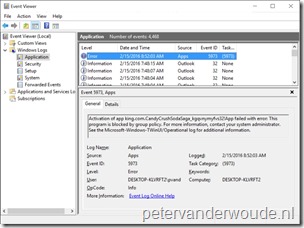 |
More information
Fore more information about how AppLocker works, AppLocker policies and the AppLocker CSP, please refer to:
- How AppLocker works: https://technet.microsoft.com/en-us/library/mt431786(v=vs.85).aspx
- Lock down Windows 10 to specific apps: https://technet.microsoft.com/en-us/library/mt592642%28v=vs.85%29.aspx
- AppLocker CSP: https://msdn.microsoft.com/en-us/library/windows/hardware/dn920019(v=vs.85).aspx
Are there any limitations to the applicability of this? I have been unsuccessful at getting this policy to apply to a Windows 10 Laptop. Looking at Microsoft’s list of settings that can be used in Custom Policies ( https://technet.microsoft.com/en-us/library/mt126215.aspx ); AppLocker is not among them. I see that your article pre-dates the last update to that document; does this guide still work for you?
Yes, it works like a charm. It’s not documented at that URL, because it’s part of the AppLocker CSP.
Hi Peter,
Will this work for non-Windows Store Apps? I am looking to block apps/files by using their hash. There appear to be options to do so under the Application Control Policies> Executables Rules. If so, do I just substitute the exported XML or are there other steps?
Niles
Hi Niles,
Yes, you can also use this for the different supported app types (see also the CSP documentation mentioned in the more information section).
Regards, Peter
Hi Peter,
We are trying to build an EMM solution and want to expose the App-Locking solution to our customers. Meaning the administrators can choose what apps to lock from a UI as you have shown.
However where we are stuck is when we query for App Inventory, we get the Product-Ids and not the Product Names.
Like for example we get this king.com.CandyCrushSaga_kgqvnymyfvs32 and not Candy Crush Saga.
Ofcourse we can apply some patterns and get an approximate name and allow the administrators to choose , however instead of guessing the Product Name from the Product Id, is there a better way to get the actual name of the application that is installed.
Thank you,
Sriram
Hi Sriram,
How and what are you querying? Something like Get-AppXPackage will get you the information.
Regards, Peter
Hi Peter,
Thank you for quick response. Actually we are trying to build an EMM solution for our customer to manage Windows devices. Like you have described in this blog even they want the App-Locker feature.
As you have shown in your article, there is a dialog where user can select the list of applications that they can choose to allow/block. How do we as a solution provider come up with list of names is the question?
Our idea was to use the EnterpriseModernAppManagement CSP and query the Windows machine of the end users, for all the installed applications and from this make a list that we can show to the Administrators so that they can choose which ones to allow.
Although EnterpriseModernAppManagement CSP is exhaustive, it does not give the friendly name of the application, so wanted to know if there is a CSP that gives the friendly name so that we can build a similar UI like you have shown in the Step 8 (application box) and do that remotely?
Get-AppXPackage is a cmdlet but that needs to be executed on the host machine , is it something that can be pulled via CSP.
Thanks
Hi Sriram,
Are you saying that the Name node doesn’t actually contain the name?
Regards, Peter
Yes Peter. It contains the package name and not the name.
Thanks,
Sriram
Hi Sriram,
The full package name node should contain a name node. I would expect that to be the actual name. If not, you might want to ask Microsoft as that information should be available. The discovered apps (in Intune) for Windows 10 devices contains exactly that information that you’re looking for.
Regards, Peter
Thank you Peter. As you could see in this CSP it is not there, https://docs.microsoft.com/en-us/windows/client-management/mdm/enterprisemodernappmanagement-csp
There are couple of forums questions but without any answers. We will get in touch with Microsoft.
Contacting Microsoft would be the best at this point, Sriram, as the information should be available somewhere. Please let met know if you find something.
Regards, Peter
Hi Peter great article and thanks for sharing… I’ve been struggling with this a bit despite everything being exactly as it should be in terms of the Intune Configuration we’re working with AutoPilot and Azure only joined Windows 10 devices. I am wondering if the reason why the policy won’t apply is due to us running Windows 10 Professional instead of Enterprise. Despite logging an Intune call with microsoft it’s proved pretty fruitless including the MS person being even less knowledgeable than me. All other intune policies work fine all except for this one, all we are trying to do is to prevent user beings able to open up CMD / REGEDIT etc.
Hi Jim,
The AppLocker CSP should be available on Windows 10 Pro also. Only managing AppLocker with GPO is not supported on Windows 10 Pro. For more information, see also: https://docs.microsoft.com/en-us/windows/security/threat-protection/windows-defender-application-control/applocker/requirements-to-use-applocker
Regards, Peter
Hey Peter,
I want to restrict apps/software which is not part of the Microsoft store. Could you recommend which OMA URI needs to be used?
And how can i get the xml for that ?
Hi Harsh,
You can follow similar steps for creating the AppLocker XML, just use a different rule (probably a Windows Installer or Executable rule).
Regards, Peter
Hi Peter,
I have created an OMA-URi and implemented to my client machines, i have changed the policy once and updated it in the same OMA- URI. Now the problem is it’s blocking all the .exe’s regardless of the XML script.
Can you guide me here??
Hi Shabin,
I’m not sure I’m following your current issue? Can you provide some more details about what you’ve configured and what you’re currently seeing?
Regards, Peter
Has anyone tried to put Azure AD Group SIDs into the Applocker XML policy, and does it work?
I can get Applocker to recognize rules that have SIDs from local Windows groups like the Administrators group, but if I add a SID for an Azure AD group to an AppLocker rule, the AppLocker CSP doesn’t seem to honor it.
For example, I might want a group in Azure AD to be allowed run all exe’s or appx’s as an override. Doing the same via Group Policy and an AD group is quite easy.
Hi Ben,
I haven’t tested AppLocker with Azure AD groups yet. What is the behavior that you’re seeing?
Regards, Peter
I’m attempting the same thing here…
K12 school district – trying to restrict our dynamic “All Students” group from Settings, griefing by changing display configuration/wallpaper, etc etc. Machines are Azure AD joined only, non-hybrid environment.
Trying to deliver AppLocker policies via OMA-URI and by using the Azure AD Group SID for that dynamic students group in the XML.
Policies get downloaded to System32\AppLocker\MDM but aren’t working.
A copy of the same XML with SID changed from Azure AD group to S-1-1-0 and delivered via Intune works as expected (everything in the policy is applied and blocked). So definitely seems to not like Azure AD group SIDs.
Looking for any thoughts or clever ideas on how I can implement this. Checked several blogs re: AppLocker deployment and I’ve seen similar recent questions in the comments, no one seems to be having any luck.
Hi Joe,
I still have to test this. Have you contacted Microsoft about this?
Regards, Peter