This week is about a very recent introduced feature around updating Windows devices and that feature is driver updates. Driver update management on itself is not that new, as that was introduced a few months ago as a part of the Windows Update for Business deployment service. However, being able to use Microsoft Intune to manage driver updates via that deployment service is definitely something new. That makes it a lot easier to use the driver management functionality. Microsoft Intune introduced a new Driver updates for Windows 10 and later profile that does all the heavy lifting for managing driver updates on Windows devices. This post will start with an introduction about Windows driver update management, followed with the steps for creating and assigning the profiles. This post will end with manually approving some drivers and experiencing the deployment.
Note: As Windows driver update management relies on the Windows Update for Business deployment service, at least one of the following licenses is required: Windows 10/11 Enterprise E3/E5, Windows 10/11 Education A3/A5, Windows Virtual Desktop Access E3/E5, Microsoft 365 Business Premium, or any license that includes one of those licenses.
Introducing Windows driver update management
Microsoft Intune relies on the Windows Update for Business deployment service for the Windows driver update management. From a high-level perspective, it might be fair to say that Microsoft Intune is the interface to the Windows Update for Business deployment service. The pretty layer on top of the under-appreciated technology. The beauty and the brains.
Microsoft Intune provides the Driver updates for Windows 10 and later profile that can be used to easily create the driver update configuration that determines which drivers can be installed on the managed Windows devices. That information is passed on to the Windows Update for Business deployment service. Based on that information the Windows Update for Business deployment service makes sure that Windows Update only provides the drivers to the Windows devices that are applicable. Like with any other update, the Windows device will identify which driver updates are applicable during the Windows Update scan cycle, and install the applicable and approved driver updates. The Windows diagnostics data is returned back to Microsoft Intune, via the Windows Update for Business deployment service. Based on that data, Microsoft Intune can provide fancy reports.
Note: The Windows Update for Business deployment service is available via the Microsoft Graph API and can be easily queried, as described in earlier blog posts here and here.
Configuring prerequisites for Windows driver update management
Before being able to successfully use Windows driver update management within Microsoft Intune, it is important that a few prerequisites are in place. Most of those prerequisites are device requirements and device configurations. Without those, the device might not report the required information (think about telemetry) or the device might not receive the updates (think about the wlidsvc service). So, make sure that the following prerequisites are met:
- The device is running a version of Windows 10/11 that is still in support.
- The device is enrolled in Microsoft Intune and (hybrid) Azure AD joined.
- The telemetry is enabled, on the device, with a minimum level of Required.
- The Microsoft Account Sign-In Assistant (wlidsvc) service, on the device, is not Disabled.
- The device has access to the network endpoints required for Intune managed devices.
- The Intune setting Windows drivers, in an update ring, is set to Allow.
- The Intune setting Enable features that require Windows diagnostic data in processor configuration in turned On.
Note: Most of these prerequisites should already be in place when using other services of the Windows Update for Business deployment service (such as, feature updates policies and expedite quality updates).
Creating and assigning the Windows driver update profile
When looking at the pretty layer that Microsoft Intune created on top of Windows Update for Business deployment service, it all starts with the new Driver updates for Windows 10 and later profile. That profile basically provides the IT administrator with the option to manually approve all Windows driver updates for the assigned devices, or to automatically approved all recommended Windows drivers for the assigned devices. Pretty straight forward. The following seven steps walk through the configuration of such profile and the decisions that must be made.
- Open the Microsoft Intune admin center portal and navigate to Devices > Driver updates for Windows 10 and later
- On the Devices | Driver updates for Windows 10 and later page, click Create profile
- On the Basics page, specify a valid name to distinguish the profile from other similar profiles and click Next
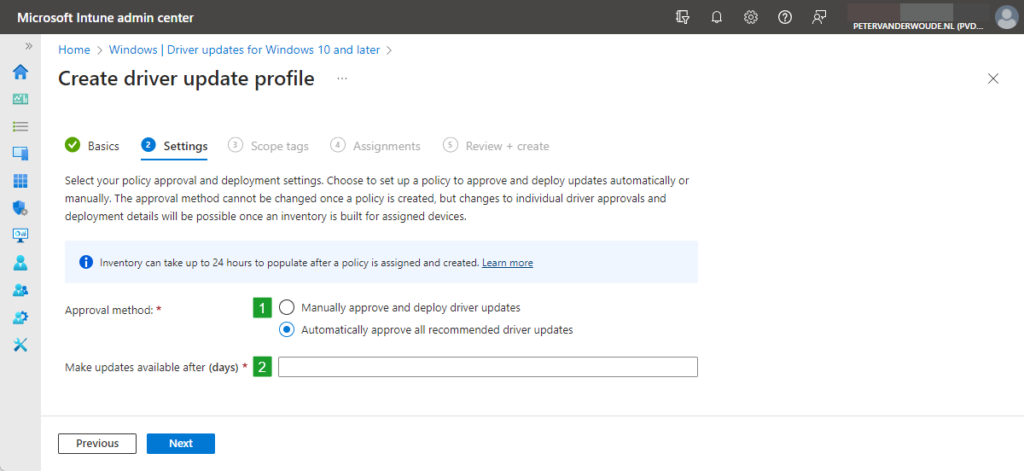
- On the Settings page, as shown below in Figure 1, choose between the following options and click Next
- Manually approve and deploy driver updates (1): Select this options when the IT administrator must manually approve and deploy each new driver in the policy that is released via Windows Update.
- Automatically approve all recommended driver updates (1): Select this option when all recommended driver updates are automatically approved and deployed and the IT administrator must manually approve and deploy other drivers. Once configured, use Make updates available after (days) (2) to configure the deferral period for driver updates.
- On the Scope tags page, configure the required scope tags and click Next
- On the Assignments page, configure the required assignment by selecting the applicable group and click Next
- On the Review + create page, review the configuration and click Create
Important: As with the distribution of any Windows updates, make sure that a solid driver update deployment plan is the starting point for the configuration of Windows driver updates.
Note: The inventory of driver updates can take up to 24-hours to populate after a policy is created and assigned.
Reviewing driver updates of the Windows driver update profile
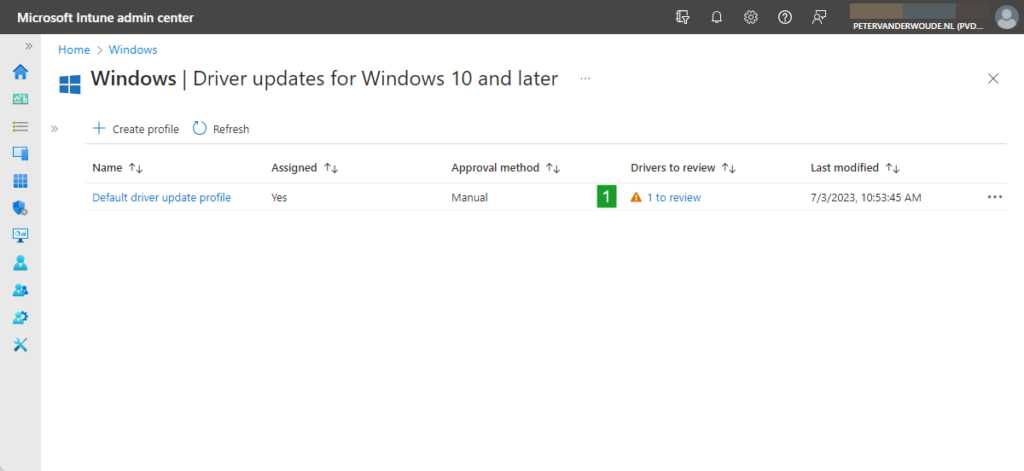
Once the Driver updates for Windows 10 and later profile is assigned to Windows devices, the waiting game begins. It can take up to 24-hours before the inventory of the Windows driver updates starts to populate. After that it becomes interesting. Especially when manually approving the available Windows driver updates. Luckily, the Driver updates for Windows 10 and later profile provides an easy overview of the drivers that need a review. The following steps walk through the steps of approving a Windows driver update within such a Driver updates for Windows 10 and later profile.
- Open the Microsoft Intune admin center portal and navigate to Devices > Driver updates for Windows 10 and later
- On the Devices | Windows 10 and later updates page, as shown below in Figure 2, click on <number> to review (1) with the created Driver updates for Windows 10 and later profile
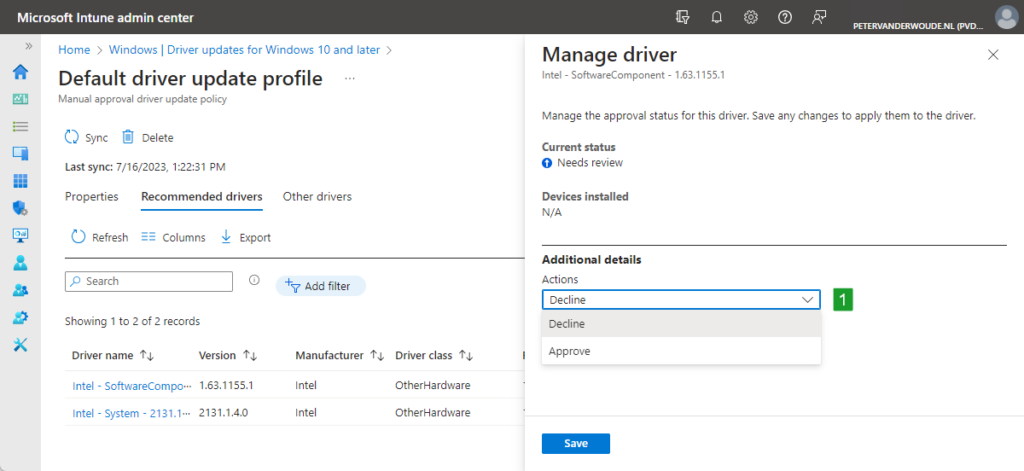
- On the Manual approval driver update policy page, as shown below in Figure 3, select a driver that needs a review, provide the following information and click Save
- Actions (1): Select Approve to actually approve the Windows driver update
- Make available in Windows Update: Select the date when the Windows driver update becomes available
Experiencing Windows driver updates
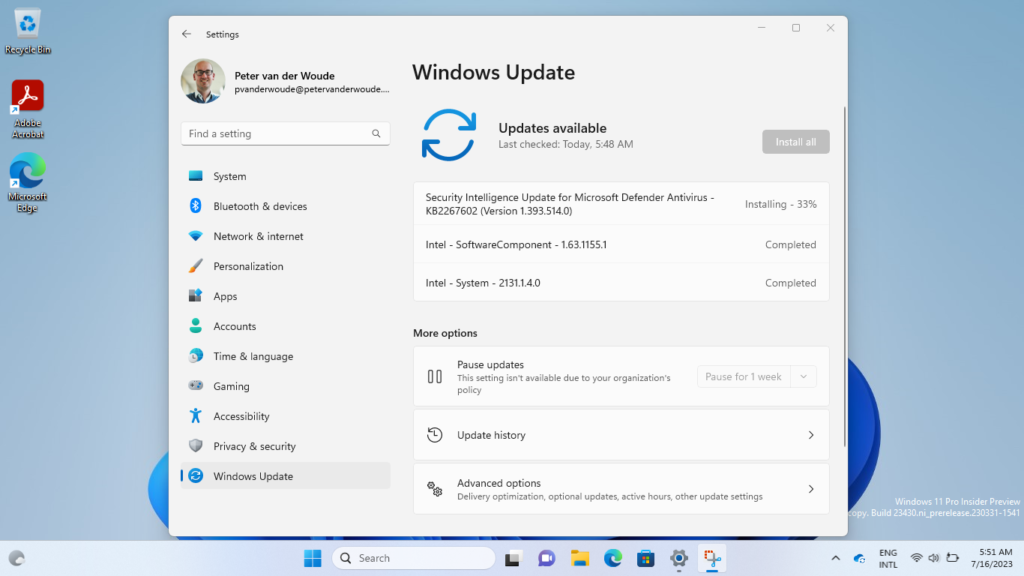
When the Driver updates for Windows 10 and later profile and the drivers are approved, there are multiple places to look for a success. That can be the Microsoft Graph and the Windows device itself. When looking at the Windows device itself, the device will start showing the approved driver updates in the Windows Update section after approving the drivers. Below in Figure 4 is an example that shows exactly the approved drivers as shown above in Figure 3.
Besides looking at the Windows device, the other option is to look in Microsoft Graph. Microsoft Graph contains a section that contains the Microsoft Intune configuration, which can be found by using the query below. That will provide the information about the created Windows driver update policies, by using the Driver updates for Windows 10 and later profile.
https://graph.microsoft.com/beta/deviceManagement/windowsDriverUpdateProfiles "@odata.context": "https://graph.microsoft.com/beta/$metadata#deviceManagement/windowsDriverUpdateProfiles",
"value": [
{
"id": "37ece334-6c0c-4e1a-9af9-c5689ca2cf84",
"displayName": "Default driver update profile",
"description": "",
"approvalType": "manual",
"deviceReporting": 0,
"newUpdates": 0,
"deploymentDeferralInDays": null,
"createdDateTime": "2023-07-03T08:53:45.5815755Z",
"lastModifiedDateTime": "2023-07-03T08:53:45.5815755Z",
"roleScopeTagIds": [
"0"
],
"inventorySyncStatus": null
}
]
}Those Windows driver update policies will create an update profile, and anything related to that, within the Windows Update for Business deployment service. That information can be found by using the query below. The easiest link between both, for the IT administrator, is probably the creation date of both profiles. The profile within Microsoft Intune will be just a fraction earlier.
https://graph.microsoft.com/beta/admin/windows/updates/updatePolicies{
"@odata.context": "https://graph.microsoft.com/beta/$metadata#admin/windows/updates/updatePolicies",
"value": [
{
"id": "21116e76-12ab-4d7a-b6c7-70e02c71d658",
"createdDateTime": "2023-07-03T08:53:45.8553908Z",
"autoEnrollmentUpdateCategories": [
"driver"
],
"complianceChangeRules": [],
"deploymentSettings": {
"schedule": null,
"monitoring": null,
"contentApplicability": null,
"userExperience": null,
"expedite": null
},
"audience@odata.context": "https://graph.microsoft.com/beta/$metadata#admin/windows/updates/updatePolicies('21116e76-12ab-4d7a-b6c7-70e02c71d658')/audience/$entity",
"audience": {
"id": "bbd70e77-8e54-4247-98a6-0f48e65eb492",
"applicableContent": []
}
}
]
}More information
For more information about Windows driver update management, refer to the following docs.
- Learn about Windows Driver updates policy for Windows 10 Windows 11 devices in Intune | Microsoft Learn
- Create Windows Driver updates policy for Windows 10 Windows 11 devices in Intune | Microsoft Learn
- Windows updates API overview – Microsoft Graph | Microsoft Learn
- Deploy a driver update using the Windows Update for Business deployment service – Microsoft Graph | Microsoft Learn
Hi Peter
As a total novice in AAD, but having muddled through, I have managed to set up a Windows Update Ring for my tenant, with a deployment schedule across devices, which is working, because the OS Version for my PC’s changes on on monthly basis.
My question is if the OS Version is updating do the feature, quality and driver updates automatically install as a consequence of the Windows Update Ring or do I need to set up Windows Drive Update Profile as described above as well.
In essence is my Windows Update Ring Profile the pretty interface for the under-lying Windows Update for Business deployment service?
I notice in Endpoint Manager that I have neither Quality or Driver Update Profiles set-up.
Hi Richard,
Apologies for the late reply, as I was enjoying my vacation. With the Update Ring you can configure the locale device with the update installation behavior. The specific feature update deployment profile, for example, can control the deployment of a specific feature update. The latter relies on the WUfB deployment service.
Regards, Peter
Hello Peter,
How about when a update ring is specified with windows drivers allowed or blocked? My experience is that when a update ring with windows drivers blocked a driver update policy with a device group which also has that update ring assigned does nog get those updates.
When specifying only a computer model (group) for a update driver policy (and the update ring with windows drivers allowed) only those devices are “driver managed” and all other are not. Assigning one update driver ploicy for all devices gives a very long list of drivers, so one policy per device model can become cumbersome whit many device models.
Hi Arthur,
Apologies for the late reply, as I was enjoying my vacation. As mentioned in the prerequisites, the Update ring must allow the installation of Windows drivers.
Regards, Peter
Hello Peter,
Would the driver updates we see here be there same as the user could find with his Windows Updates?
With all the other Update Rings in place without this one, would it mean that without setting this up, all the other updates would be force installed for example, but driver updates would sit still in Windows Update setting?
Im trying to figure out what the advantage of configuring this is.
Hi Peter,
It’s just about more control. When you allow driver updates in your update ring, the device will just get all the applicable driver updates.
Regards, Peter
Hello Peter,
When using driver updates from intune and the rest with a different product like Ivanti Endpoint Manager, does that work?
We have a hibrid enviroment and devices are in intune but still the updates comes from Ivanti Endpoint Manager (we makeing a shift to complete Intune) I have Windows driver updates activated within Intune and a group assigned to it with all devices that are getting the updates from Ivanti Endpoint Manager, doest it then get the driver updates?
Hi Andre,
Eventually Intune is just relying on Windows Update for Business for handling the updates. I’m not sure how Ivanti works with updates, but I can imagine that they eventually would intervene with each other. Especially when Ivanti also relies on Windows Update.
Regards, Peter