This week is a follow up on the post of last week. In that post there was a reference to the option to completely exclude the password credential provider to force the user in to using Windows Hello for Business. This week is all about that option to exclude the password credential provider – and basically any other credential provider – from use during authentication. Credential providers are the primary mechanism for authenticating users in Windows and to verify their identity. Those credential providers are shown as different small tiles to the user as different options to authenticate in Windows. With Windows 10 and later, credential providers are also used for authenticating users in apps, websites, and more.
By installation default, Windows already provides a long list of credential providers. Besides those default credential providers it’s also possible for third-parties to develop custom credential providers and integrate them in Windows. An overview of the available credential providers can be found in the registry. This post will focus on the technical implementation of excluding the password credential provider. The steps for the implementation, some technical challenges and the user experience.
Tip: The HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Authentication\Credential Providers registry key contains the available credential providers in the different subkeys.
Configuring the exclusion of the password credential provider
When looking at excluding the password credential provider – and basically any other credential provider – it’s important to keep in mind what the implications will be of that configuration. The exclusion of the password credential provider means that users can’t use username-password authentication in Windows anymore to verify their identity. And, even more importantly, everything that relies on the password credential provider can’t use it anymore either. Think about, for example, using the Remote Desktop Connection app or using the Run as different user functionality. Those functionalities won’t be able to use the password credential provider. That behavior makes it really important for an organization to know their users and to know the applications and authentication methods that are used.
When looking at the configuration options for excluding the password credential provider, there is an ADMX-back policy setting available. That policy setting is available via the Settings Catalog. The challenge, however, is that it’s only available for the Enterprise edition of Windows and, maybe even more importantly, it’s currently only available for Windows Insider Preview builds. The good thing is that this setting configures a registry value (ExcludedCredentialProviders) and that can be relatively easily scripted by using PowerShell. Both configuration methods are described below. Option 1 is by using the Settings Catalog and option 2 is by using PowerShell.
Option 1: Configuring the exclusion of the password credential provider by using the Settings catalog
The first and preferred option for configuring the exclusion of the password credential provider is by using the Settings Catalog. As mentioned earlier, the ADMX-backed setting that can be used does require the device to be running the Enterprise edition of Windows and is currently only available for Windows Insider Preview builds. That ADMX-backed setting is Exclude credential providers and is part of the CredentialProviders.admx. Once enabled, that setting requires the CLSIDs of the required credential providers as input. If needed, those CLSIDs can be found in the earlier mentioned registry key that contains all the available credential providers. The following six steps walk through the creation of a settings catalog with the setting to exclude the password credential provider.
Important: The configuration to configure the exclusion of any credential provider, by using the Settings Catalog, is currently only available for Windows Insider Preview builds.
- Open the Microsoft Endpoint Manager admin center portal and navigate to Devices > Windows > Configuration profiles
- On the Windows | Configuration profiles blade, click Create profile
- On the Create a profile blade, provide the following information and click Create
- Platform: Select Windows 10 and later to create a profile for Windows 10 devices
- Profile: Select Settings catalog to select the required setting from the catalog
- On the Basics page, provide the following information and click Next
- Name: Provide a name for the profile to distinguish it from other similar profiles
- Description: (Optional) Provide a description for the profile to further differentiate profiles
- Platform: (Greyed out) Windows 10 and later
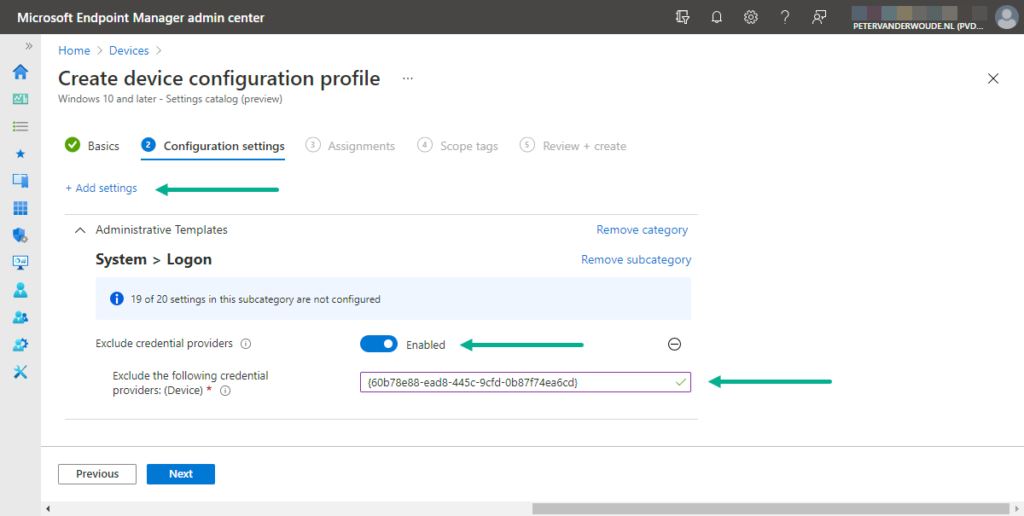
- On the Configuration settings page, as shown below in Figure 1, perform the following actions
- Click Add settings and perform the following in Settings picker
- Select Administrative Templates as category
- Select System > Logon as subcategory
- Select Exclude credential providers as setting
- Switch the slider with Exclude credential providers to Enable, provide the CLSID of the password credential provider ({60b78e88-ead8-445c-9cfd-0b87f74ea6cd}) with Exclude the following credential providers and click Next
Note: When multiple credential providers should be excluded, add the different CLSIDs separated with a comma.
- On the Scope tags page, configure the required scope tags and click Next
- On the Assignments page, configure the assignment and click Next
- On the Review + create page, verify the configuration and click Create
Option 2: Configuring the exclusion of the credential provider by using proactive remediations
The second option for configuring the exclusion of the password credential provider is by using the PowerShell. For PowerShell scripts, the best controlled method to distribute the required configuration is by using proactive remediations. As the required setting is an ADMX-backed setting, it relies on the registry and can be easily configured by using PowerShell.
Note: The provided information for this configuration option is similar to last week. Only a few small adjustments to provide some information and to configure the correct registry key with the required value and data.
Constructing the PowerShell script to detect the credential providers configuration
When using proactive remediations, there should be a detection script. That detection script should detect the excluded credential providers configuration. Below is a snippet of a PowerShell script that performs the required detection. That snippet verifies the existence of the registry key, the registry value and the registry data, that are required for the excluded credential providers configuration. That verification is achieved by checking the existence of the registry key (line 5), by checking the availability of the registry value (line 6) and by verifying the registry data (line 7).
$registryPath = "HKLM:\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System"
$registryValueName = "ExcludedCredentialProviders"
$registryValueData = "{60b78e88-ead8-445c-9cfd-0b87f74ea6cd}"
if((Test-Path $registryPath)) {
if(Get-ItemProperty -Path $registryPath -Name $registryValueName -ErrorAction Ignore) {
if((Get-ItemPropertyValue -Path $registryPath -Name $registryValueName -ErrorAction Ignore)-eq $registryValueData) {
Write-Host "Specified credential provider is already excluded"
exit 0
}
else {
Write-Host "Specified credential provider is currently not excluded"
exit 1
}
}
else {
Write-Host "Specified credential provider is currently not excluded"
exit 1
}
}
else {
Write-Host "Specified credential provider is currently not excluded"
exit 1
}Tip: The HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Authentication\LogonUI registry key contains the LastLoggedOnProvider value with as data the credential provider that is used for the current sign in. That information can be used to verify the usage of Windows Hello for Business.
Note: When multiple credential providers should be excluded, add the different CLSIDs separated with a comma as the value of the $registryValueData variable.
Constructing the PowerShell script to remediate the credential providers configuration
When using proactive remediations, there should also be a remediation script. That remediation script should remediate the excluded credential providers configuration. Below is a snippet of a PowerShell script that performs the required remediation. That snippet creates the registry configuration that is required for the excluded credential providers configuration. That creation is achieved by checking the existence of the registry key. When the registry key doesn’t exist (line 6), the registry key (line 7), the registry value and the registry data are created (line 8). When the registry key does exist (line 11), only the registry value and registry data are set (line 12).
$registryPath = "HKLM:\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System"
$registryValueName = "ExcludedCredentialProviders"
$registryValueData = "{60b78e88-ead8-445c-9cfd-0b87f74ea6cd}"
try {
if(!(Test-Path $registryPath)) {
New-Item -Path $registryPath -Force
New-ItemProperty -Path $registryPath -Name $registryValueName -Value $registryValueData -PropertyType String -Force
Write-Host "Successfully excluded specified credential provider"
}
else {
New-ItemProperty -Path $registryPath -Name $registryValueName -Value $registryValueData -PropertyType String -Force
Write-Host "Successfully excluded specified credential provider"
}
}
catch {
$errorMessage = $_.Exception.Message
Write-Error $errorMessage
exit 1
}Note: When multiple credential providers should be excluded, add the different CLSIDs separated with a comma as the value of the $registryValueData variable.
Using proactive remediation to detect and remediate the credential providers configuration
After constructing the different PowerShell scripts to detect and remediate the excluded credential providers configuration, it’s time to look at the best method for applying those scripts. That best method is proactive remediations. Proactive remediations are script packages that can detect and remediate any scriptable challenge, as long as those challenges can be addressed by using PowerShell. The nice thing about script packages is the ability to schedule the execution and to configure recurring behavior. That provides a lot of control and flexibility. For deploying those script packages, Microsoft Intune relies on the Intune Management Extension (IME). The following six steps walk through the creation of a script package to detect and remediate the excluded credential providers configuration.
- Open the Microsoft Endpoint Manager admin center portal navigate to Reports > Endpoint analytics > Proactive remediations
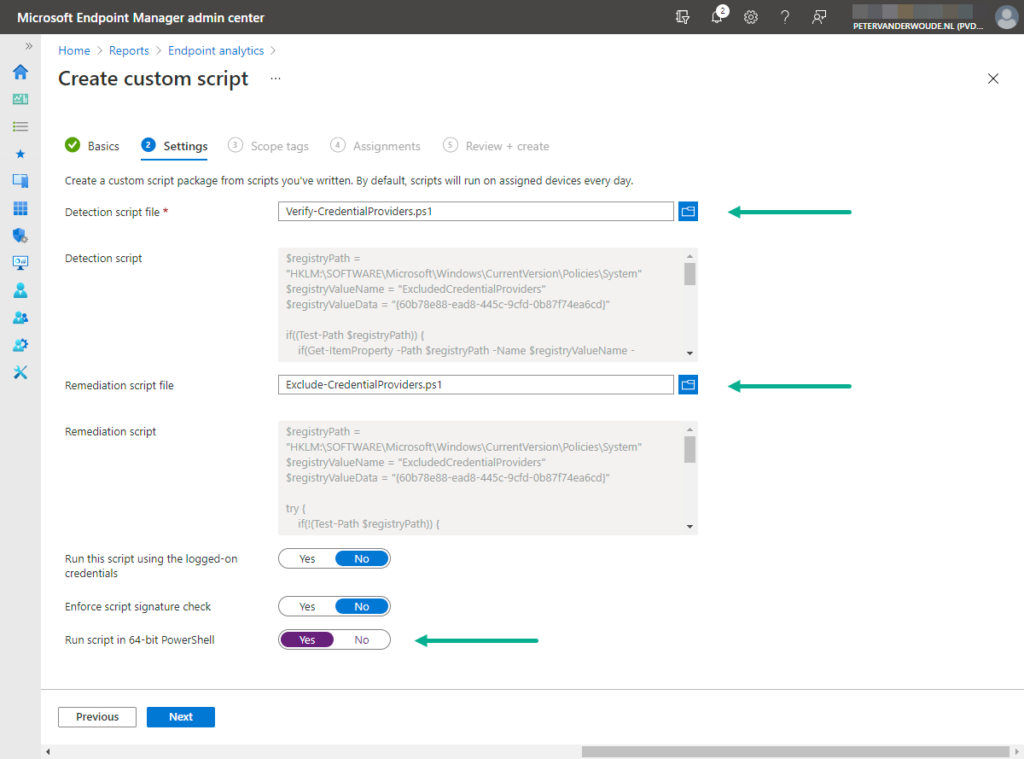
- On the Endpoint analytics (Preview) | Proactive remediations blade, click Create script package to open the Create custom script wizard
- On the Basics page, provide the following information and click Next
- Name: Provide a valid name for the custom script package to distinguish it from other similar script packages
- Description: (Optional) Provide a valid description for the custom script package to further differentiate script packages
- Publisher: (Optional) Provide a valid publisher for the custom script package, by default the creator of the script package
- Version: [Greyed out]
- On the Settings page, provide the following information and click Next
- Detection script file: Select the created detection script to detect the status of the excluded credential providers configuration
- Detection script: [Greyed out]
- Remediation script file: Select the created remediation script to remediate the excluded credential providers configuration
- Remediation script: [Greyed out]
- Run this script using the logged-on credentials: Select No as value to make sure that the script runs in SYSTEM context
- Enforce script signature check: Select No as value to make sure that the signature of the script is not checked
- Run script in 64-bit PowerShell: Select Yes as value to make sure that the script runs in 64-bit, if possible
- On the Scope tags page, configure the required scope tags click Next
- On the Assignments page, provide the following information and click Next
- Assign to: Select the assigned group and configure the schedule by clicking on the three dots
- Schedule: Select the recurrence frequency by choosing between Once, Daily, or Hourly
- When choosing Once, a specific date and time should be configured
- When choosing Daily, a frequency and daily time should be configured
- When choosing Hourly, a frequency should be configured
- On the Review + create page, verify the information and click Create
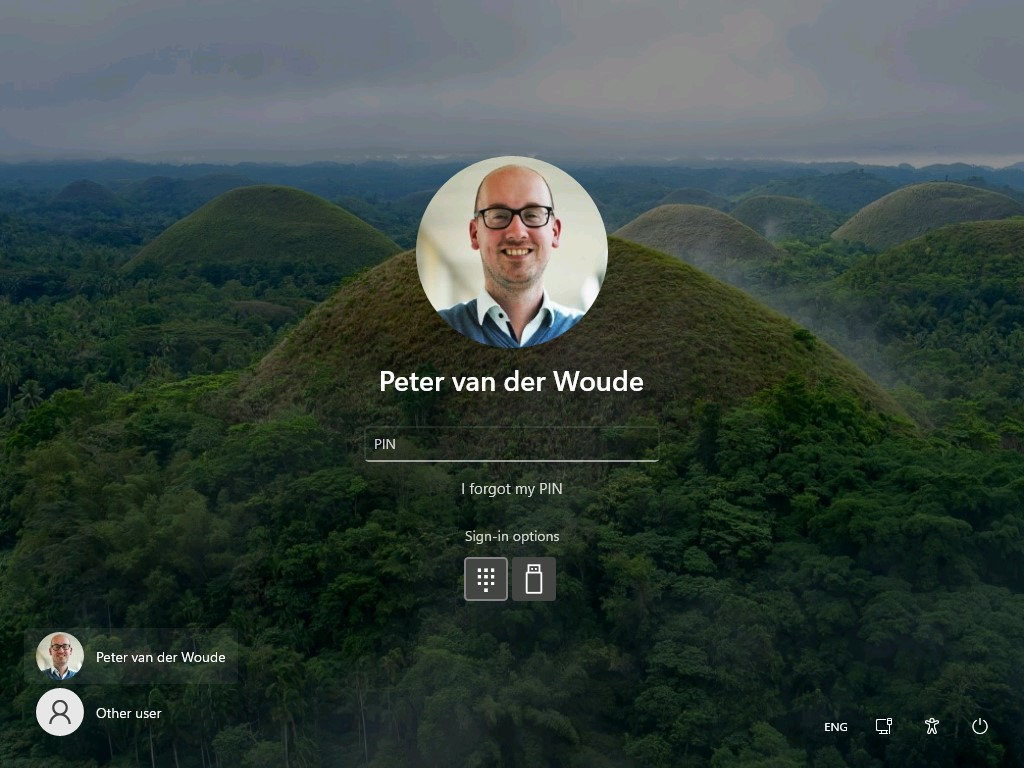
Experiencing the excluded password credential provider
Experiencing the behavior with the excluded password credential provider is pretty straight forward. Simply start a configured Windows 10 device, or Windows 11 device, and click on Sign-in options. That will show the available credential providers, based on the excluded credential providers configuration. Figure 3 shows an example of a Windows 10 device with the configuration of option 2 and Figure 4 shows an example of a Windows 11 device with the configuration of option 1.
More information
For more information about the passwordless strategy of Microsoft and and the different configuration options for the credential providers, refer to the following docs.
How do we accomplish this if we don’t have E3 or E5? I need to only set this key after user has enrolled in whfb.
Hi David,
You mean in a scenario that you’re not licensed to use proactive remediations? If so, you could create a scheduled task to run the script until the user is ready.
Regards, Peter
If we do the settings catalog option. And we install the PC by Intune they sey the configuration profile is Not Appliciable
Hi Peter,
What version of Windows are you using?
Regards, Peter
Hello we are use Windows 10.
Hi Peter,
I understand, but which version of Windows 10? The mentioned policy setting is not available for every version of Windows 10.
Regards, Peter
The Enterprise Version we Use 21H1
Hi Peter,
As we speak the version doesn’t matter anymore (as it was preview). It’s now available with the September update (see: https://techcommunity.microsoft.com/t5/intune-customer-success/the-latest-in-group-policy-settings-parity-in-mobile-device/ba-p/2269167).
Regards, Peter
Hi Peter,
Thanks for this post !
I am trying to implement passwordless for my company, with a mix of WHFB and Yubico Fido2 key.
My question is what happens when the password of the user expires when the use of username password is remove please ?
How its experiencing by users ?
Many thanks, Regards, Nicolas
Hi Nicolas,
If you’re using passwordless, what password expiration configuration are you using?
Regards, Peter
The computer is still join to a traditional active directory so the password of the user will expires.
I have to admit that I haven’t looked at that behavior recently. I expect the user to be prompted in Windows before it happens and when it happened.
Regards, Peter
Hoi Peter,
ik heb een omgeving waar we zonder wachtwoord inloggen ( yubikey en pin ) alles is geimplementeer via intune.
Wachtwoord optie hebben we ook verwijderd met de onderstaande regkey
$Path = “HKLM:\SOFTWARE\Microsoft\Windows\CurrentVersion\Authentication\Credential Providers\{60b78e88-ead8-445c-9cfd-0b87f74ea6cd}”
$Name = “Disabled”
$Value = “1”
Het probleem waar ik nu tegen aan loop is dat als ik met RDP een ander willekeurig systeem wil overnemen ik ook niet meer de mogelijkheid heb om een wachtwoord in te voeren.
Ik heb wel de workarounds maar dat is niet wat de gebruikers willen.
Is de RDP applicatie in Windows op 1 of andere manier uit te sluiten zodat we daar nog wel de wachtwoord optie krijgen met inloggen
Hi Kees,
I’m affraid that’s not an option. When excluding the the credential provider, you can’t use it anymore.
Regards, Peter
Hi Peter, I noticed that if you try to use the “I forgot my pin” option, you can still use your password if you have one assigned. Do you know if you can remove that option as well?
Hi Federico,
Is that authentication method still available for the user?
Regards, Peter
Thank you
So, seeing as some of our users need to RDP, some users have admin elevation accounts, and IT need to elevate using a LAPS account, there is basically no way then to remove the password field from the sign-in screen?
Hi Steve,
You would have exclude those different user types, as you will otherwise break their scenarios. Otherwise, you also might want to look at this: https://www.petervanderwoude.nl/post/easily-hiding-the-ability-to-use-passwords-for-signing-into-windows/
Regards, Peter