This week is about something similar as last week. This week is all about the password reset option on the login screen. In other words, the Reset password option. Starting with Windows 10, version 1709, it’s possible to enable the Reset password option from the login screen for Azure AD joined devices. I know that a lot has been written already about this subject, but I have the feeling that this subject needs a place on my blog. My style and more details. In this post I’ll provide a short introduction about Azure AD self-service password reset (SSPR), followed by walking through the required configurations for SSPR and the Reset password option. I’ll end this post by looking at the end-user experience.
Introduction
Now let’s start this post with an introduction about Azure AD SSPR. With SSPR users can reset their passwords on their own when and where they need to. At the same time, administrators can control how a user’s password gets reset. That means that the user no longer needs to call a help desk just to reset their password. SSPR includes (the focus of this post is number 2):
- Self-service password change: The user knows their password but wants to change it to something new;
- Self-service password reset: The user is unable to sign in and wants to reset their password by using one or more of the following validated authentication methods:
- Send a text message to a validated mobile phone;
- Make a phone call to a validated mobile or office phone;
- Send an email to a validated secondary email account;
- Answer their security questions.
- Self-service account unlock: The user is unable to sign in with their password and has been locked out. The user wants to unlock their account without administrator intervention by using their authentication methods.
Configuration
Let’s continue by having a look at the required configuration, to enable the Reset password option from the login screen. As the configuration of the actual settings requires SSPR to be enabled, I divided the configuration into two steps. The first step is to enable SSPR and the second step is to configure the Reset password option.
Step 1a: Enable SSPR
The first step is to enable SSPR, as it’s the starting point for enabling the Reset password option from the login screen. Without SSPR enabled, and still configuring the Reset password option, the user will receive a message that SSPR is not enabled for the user and that the user should contact the administrator. The following seven steps walk through the relatively simple configuration to enable SSPR.
| 1 | Open the Azure portal and navigate to Azure Active Directory > Password reset; |
| 2 |
|
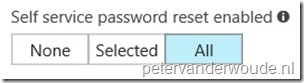
| 3 |
Note: Make sure that you have at least as many methods available to users as you have required to reset. |
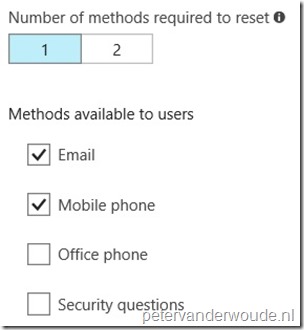
| 4 |
|
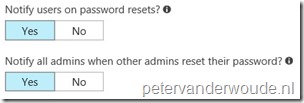
| 5 |
|
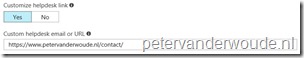
| 6 |
|
| 7 |
Note: This is required when using an on-premises directory and also requires the configuration of step 1b. |
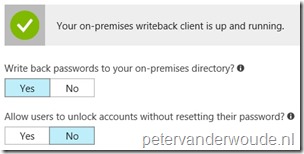
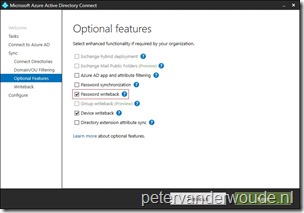
Step 1b: (Optional) Configure password writeback
Another part of the first step is the optional configuration of password writeback. This should be configured to write the passwords from Azure AD back to the on-premises directory. To achieve this, use the following seven steps to reconfigure Azure AD Connect.
Step 2: Enable Reset password option
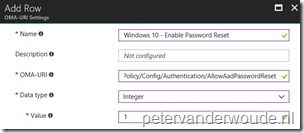
The second step is to configure the required setting to enable the Reset password option from the login screen. In other words, the second step is to configure a device configuration profile with at least a custom OMA-URI setting. The required setting is part of the Authentication node of the Policy CSP. It’s the AllowAadPasswordReset policy. That policy allows administrators to enable the self-service password reset feature on the windows logon screen. An integer value of 0 means not enabled and an integer value of 1 means enabled.
The following three steps walk through the creation of a new device configuration profile, including the required OMA-URI setting. After that simply assign the created profile to a user group.
| 1 | Open the Azure portal and navigate to Intune > Device configuration > Profiles; |
| 2 | On the Devices configuration – Profiles blade, click Create profile to open the Create profile blade; |
| 3a |
On the Create profile blade, provide the following information and click Create;
|
| 3b |
|
Note: For testing purposes it’s also possible to configure the Reset password option by using the HKLM\SOFTWARE\Policies\Microsoft\AzureADAccount registry key with the value, type and data of AllowPasswordReset, REG_DWORD and 1.
End-user experience
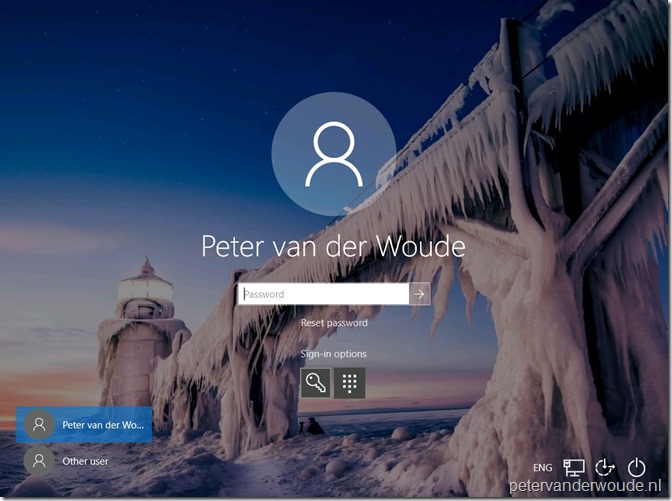
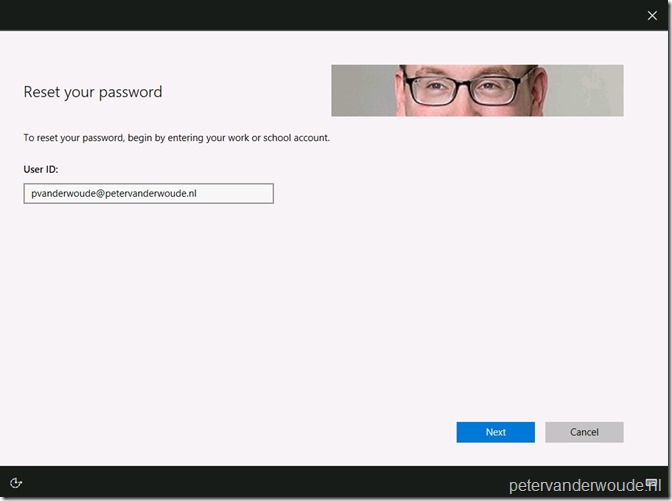
Now let’s end this post by walking through the end-user experience. On the login screen a new option is available when selecting password as the sign-in option, the Reset password option.
When the user selects Reset password, the user will be redirected to the Azure AD self-service password reset service.
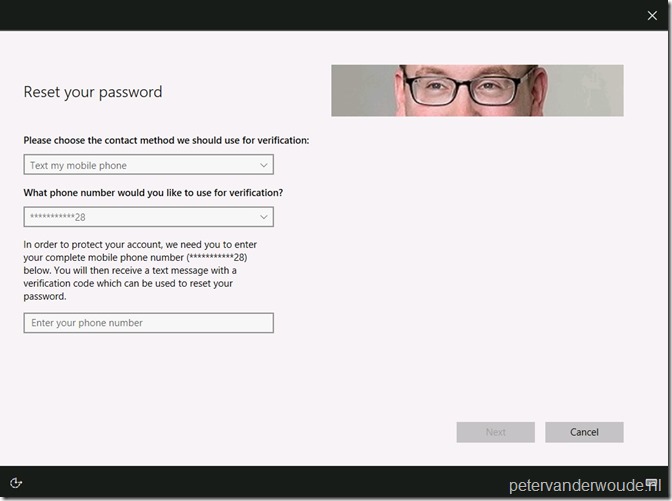
The User ID is already prepopulated and when the user clicks on Next, the user should choose a verification method. In my case a text to my mobile phone.
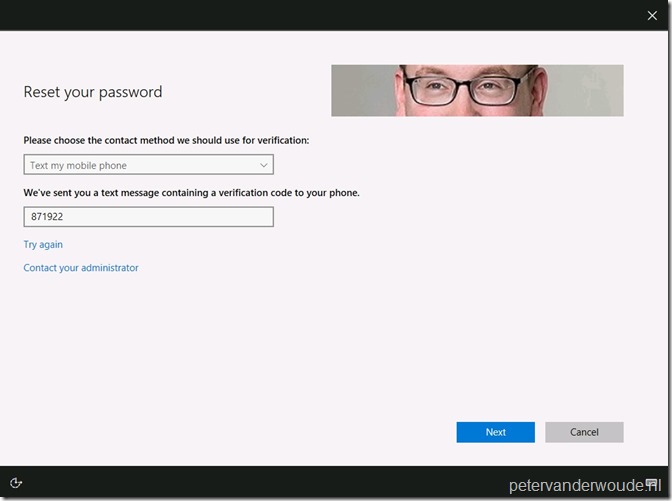
When the user provides the correct mobile phone number and clicks on Next, the user must provide the actual verification code of the text message.
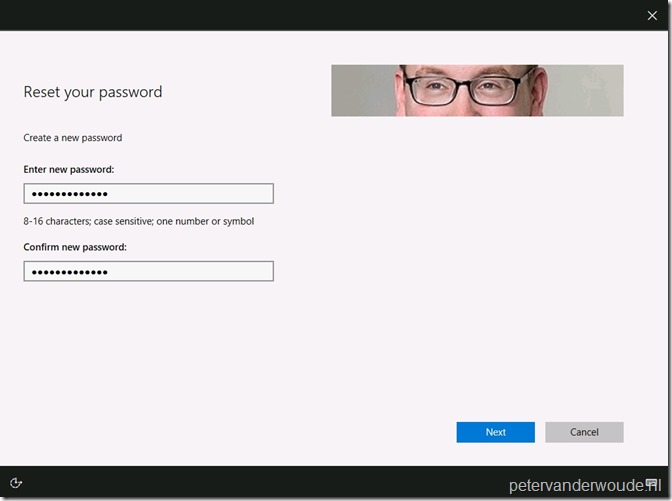
When the user provides the correct verification code and clicks on Next, the user must provide a new password.
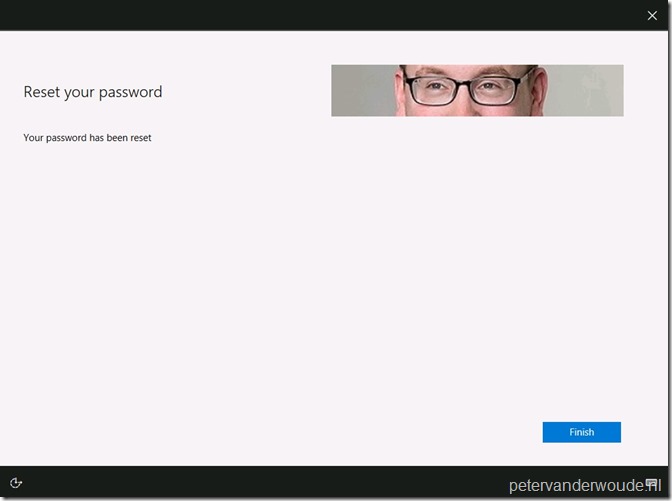
When the user provides a new password and clicks Next, the user will be provided with the message that the password has been reset. When the user than clicks on Finish, the user will be redirected to the login screen.
More information
For more information about SSPR, Windows 10 and the Reset password option, please refer to the following articles:
- How to successfully roll out self-service password reset: https://docs.microsoft.com/en-us/azure/active-directory/active-directory-passwords-best-practices
- Azure AD password reset from the login screen: https://docs.microsoft.com/en-us/azure/active-directory/active-directory-passwords-login
- Policy CSP – Authentication: https://docs.microsoft.com/en-us/windows/client-management/mdm/policy-csp-authentication

Hi! Is there a way to redirect to a custom Password Reset Portal? My organization does not use AAD for password reset, but we have Azure AD Premium. We want to redirect to a custom URL though… thanks! JJ
Hi Jose,
At this moment this is AAD SSPR only.
Regards, Peter
Dont forget if you used Custom AD Connect installation with a service account, you need to set permissions for this account. Change Password,Reset Password,Write Lockout,Write PwdLastSet
That is correct, Rkast!
Hi Peter
Nice blog post, as usual from you!
We have some issue regarding this function. Our customer has the following update scenario from 1511 to 1607 and further to 1703. This ‘reset password’ option is not even appear on the login screen!
MSFT support answer: “We have been continuously working and researching with our TA’s on this issue but as we currently are not able to replicate the issue at our end we are unable to provide a definite resolution.
We have involved the Directory services team in this regard for which you might receive calls from various tech engineers.”
Did you already have this symptom? What would you recommend us?
Thanks for your kindly answer & greetings from Switzerland, Ákos
Hi Akos,
The latest version you mentioned is 1703. This functionality requires an Azure AD joined Windows 10, version 1709, or later, device.
Regards, Peter
I see you have OMA-URI: ./Device/Vendor/MSFT/Policy/Config/Authentication/AllowAadPasswordReset
On blog post below Per does not append ./Device/
Can you elaborate the difference please ?
on https://osddeployment.dk/2017/11/02/how-to-enable-password-reset-from-windows-10-login-screen/
Hi RKast,
It’s the same. For device wide configuration the Device/ portion may be omitted from the path, see also: https://docs.microsoft.com/en-us/windows/client-management/mdm/policy-configuration-service-provider
Regards, Peter
Sir Peter, thanks but what is the meaning of ‘device wide’ in this case? With /device we assign to device group is this different when leaving out the /device ? i simply dont understand.
Hi RKast,
There is no difference. Both configurations trigger the device configuration.
Regards, Peter
Nice Blog Peter!
Is this functionality supported with Hybrid AzureAD joined devices?
Hi Steve,
Not at this moment. At this moment it’s Azure AD joined only.
Regards, Peter
Hi Peter,
On the Official Microsoft doc about this, it’s explicitely mentioned that Hybrid AD Azure joined devices are supported.
https://docs.microsoft.com/en-us/azure/active-directory/authentication/tutorial-sspr-windows
In my environment, it’s not working with a 1803 W10 device. Why does Microsoft tell that while it’s not possible ?
Hi Gerem,
Correct. Starting with Windows 10, version 1803, it should be supported for hybrid Azure AD joined devices. Haven’t tested that myself yet. What problems are you running into? And what does your setup look like?
Regards, Peter
IS it possible to redirect to our own SSPR tool instead of Azure SSPR
Hi Jijo,
Not via this configuration.
Regards, Peter
Hi Peter,
Is it necessary to configure the AD permissions noted in this article as part of the seven steps for password writeback? https://docs.microsoft.com/en-us/azure/active-directory/authentication/howto-sspr-writeback
Hi Mitch,
Yes! The account specified in Azure AD Connect should have the correct permissions to write that information.
Regards, Peter
Hi Peter,
Thanks for the article :
I have question, how do enforce password change on device enrollment for a new user who has never reset his password ?
1. We have new users who would be issued new laptops (MS AutoPilot) and these users enroll into these Laptop with their Azure AD accounts.
2. In this process, device would be joined to Azure AD, followed by Intune enrolment.
3. The plan is to create these users in on-premise AD and sync them to Azure AD.
4. The expectation now is to enforce password change, since this is users first login.
In General, How do we force password change for new/first time user who is using Azure services like Office365 webportal or Intune who gets authenticated on Azure AD ?? And if these AAD accounts are synced from on-prem AD ?
What I’ve heard so far is , selecting “change password at next logon” on On-prem AD, and then sync those accounts up to Azure AD using AD Connect is not a possibility ? As the sync would fail because these are temp passwords.
For synced AAD users is there a way for users to be prompted to change their password on the O365 web portal and then write those changes back to the on-premise AD ?
Hi Rajesh,
Completely depends on the configuration. For example, you shouldn’t have an issue when using pass-through authentication.
Regards, Peter
Hi Rajesh, Peter, is this part solved, a procedure to get this working? (“What I’ve heard so far is , selecting “change password at next logon” on On-prem AD, and then sync those accounts up to Azure AD using AD Connect is not a possibility ? As the sync would fail because these are temp passwords.”)
Hi Nico,
Are you referring to the note here: https://docs.microsoft.com/en-us/azure/active-directory/hybrid/how-to-connect-password-hash-synchronization#synchronizing-temporary-passwords-and-force-password-change-on-next-logon
Regards, Peter
Hello, I ran into the following issue in a LAB, if you have and advise/suggestions please let me know, thanks
I have up Azure SSPR from the logon screen, by setting the following registry key via a group policy preference (as I could not see a builtin GPO setting, if there is a GPO please let me know its path)
HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\AzureADAccount
This works fine as long as the user does not reboot the computer. If the computer is rebooted the “reset password” link does not appear on the logon screen. If the user then performs a logon and logoff, then a logon again the “reset password” does appear.
So in summary it works fine unless the user reboots, as the ‘reset password’ link is always missing at the first logon following a reboot of the computer.
I should mention I am using a LAB environment (Hyper-V) when a Windows 10 VM (which in effect means I am RDP into the VM) is that the issue? as I do not have a physical computer to test with at the moment. However as stated above the ‘reset password’ link does appear following a logoff without a reboot.
Thanks
Ernest
Hi Ernest,
It sounds like you’re applying the setting as a user setting and not as a computer setting.
Regards, Peter
Hi Peter,
I noticed that the ‘8-16 characters; case sensitive; one number or symbol’ message in the create new password dialog is hard-coded by Microsoft. This can be misleading if you have an AD DS password policy that requires – for example – more than 8 characters.
Any idea if this will be fixed by Microsoft?
Thanks…
Ronald.
Regarding my previous comment: Microsoft has acknowledged the hard-coded password policy message in the SSPR dialog to be an issue and is working on a fix: ttps://feedback.azure.com/forums/169401-azure-active-directory/suggestions/36320743-ability-to-to-remove-or-customise-the-default-mess
Thank you for answering your own question, before I could, Ronald 🙂
Regards, Peter
hi Peter,
The password change in a Hybrid joined laptop scenario the user is able to change the password via above SSPR method but that does not save/cache the password on that laptop and so had to use old password to login ..
any Idea what we can do here.
Also in a Hybrid (Company on-prem domain + AAD joined) setup do we need to have different policies matching on-prem gpo in Intune ?
Hi Dheeraj,
Have a look at the mentioned limitations about the line-of-sight: https://docs.microsoft.com/en-us/azure/active-directory/authentication/howto-sspr-windows#general-limitations
Regards, Peter
Hi Peter,
We are testing Hybrid Azure AD for Reset Password /SSPR functionality from the logon screen of Windows 10 (1809). We do have the reset password option visible on the logon screen, but the functionality doesn’t work.
When i try to reset the password of my account by using domain\username or UPN from the logon screen the screen changes to ‘just a moment..’ after when it locks the PC and I’m back at the logon screen. At that point I am unable to login, I have to use ‘other user’ to switch before I am able to login with my account. The computer seems locked by user ‘defaultuser1’. I have also noticed that for every attempt i make to use ‘reset password’ a user profile named ‘defaultuser1..000’, ‘…001′,’….002’ is created. Do you have any idea what could be the problem here?
Regards, Ewout
Hi Ewout,
First of all keep in that you must have line of sight to a domain controller to use the new password and update cached credentials. That being said, are you receiving any error message (in the Event Viewer)?
Regards, Peter
Hello, thanks for a great article. We finally have Azure P1 in our hybrid Active Directory environment. I have set up self-service password reset with write-back to AD. This works great from the Microsoft web portal. I can reset my password, and it writes back to our AD. The final step for me is to try to get the Reset Password link to appear on our Windows 10 Pro logon screen. We don’t use Intune, so I have pushed out AllowPasswordReset DWORD under Computer\HKLM\SOFTWARE\Policies\Microsoft\AzureADAccount. Unfortunately, the reset link does not appear. I’m baffled why this doesn’t work.
Hi Jonathan,
Are you seeing any errors in the Event Viewer? Also, do keep in mind that a hybrid Azure AD joined device does require a line of sight with a domain controller.
Regards, Peter
Peter, I finally figured out the issue. My machines were Azure AD registered and not Hybrid Azure AD joined. I made some changes to the Azure AD Sync tool, and my Windows 10 machines started converting to Hybrid Azure AD joined. Password Reset started appearing at the logon screen. Yay!
You bring up a good point, though, with line of site to the DC’s. If a user is remote from the office (needing VPN to connect) and needs to reset the password, how will the self-serve reset link work in that situation? I was hoping that the user could use the reset link, and they could reset their password. Then the user could use the network logon option to make the VPN connection with the new credentials.
Hi Jonathan,
Great to hear that you figured out the issue! That will be challenging with hybrid Azure AD joined devices, as you need to have network connectivity line of sight to a domain controller to use the new password and update cached credentials.
Regards, Peter
Hello Peter,
I have managed to enable reset link on the sign in page using registry value and able to reset the password without any issues. However it gives the reset option only if a user logged in. If its fresh session. It doesn’t give the option. So how exactly the user can use this sspr function here?
The machines are hybrid AAD joined.
Hi Haj,
Are you familiar with the limitations of hybrid Azure AD joined devices: https://docs.microsoft.com/en-us/azure/active-directory/authentication/howto-sspr-windows
Regards, Peter
Hi Peter,
Any suggestions or ideas how to shoot an email to the user about password expiry, when using the Azure AD SSPR. I have an environment where writeback is configured and password reset is done via windows screen.
Hi Ravi,
That would require some custom scripting.
Regards, Peter
Hi Peter, do you know the Azure SSPR Credential provider code? or where I can find it please? We use Cisco Duo agent on desktops for MFA, and need to enter the azure SSPR code in the registry so it’s allowed. Thanks!!
Hi Glen,
I’m sorry, but Microsoft doesn’t provide any customization options on that part.
Regards, Peter
Hello,
A lot of helpful information here, I have a quick question and perhaps it is already answered in this forum I just missed it.
Is it possible to change the verbiage from “Reset Password” to “Reset Password or Unlock Account” or “Click here if you need assistance signing in”?
Many people simply lock their account and call support because they are under the impression Reset Password is the only option.
Thank you,
Carl
Hi Carl,
At this moment you can’t customize that.
Regards, Peter
Hello Peter,
Thank you for this article. The option to reset the password through the logon screen was very usefull. Didn’t know about that.
I am dropping this message not because the above isn’t working (I had no problem getting it running) but I was wondering if it is still not possible that the local cached password is changed also when I do an SSPR?
Or is still a line of sight with the DC’s necessary?
I even get a message that when I try to change to local password seperately that the DC is not available and I cannot change the cached password.
Also when I set up an VPN connection it doesn’t work.
Do you have any ideas about this problem?
Thank you in advance.
Regards,
Ron Beugeling
Hi Ron,
Are those hybrid Azure AD joined devices? If so, that requires a line of sight (see also: https://learn.microsoft.com/en-us/azure/active-directory/authentication/howto-sspr-windows).
Regards, Peter
Hi Peter,
Sorry for my late response.
Yes, those are hybrid Azure Ad joined devices.
Thank you for the article.
I’m considering a permanent VPN connection on our laptops but I am not sure if that is something that is secure all the time.
Well it’s something to think about.
Regards,
Ron
No problem, Ron. Let me know if you have any further questions.
Regards, Peter
Hello Great article,
when I try to reset the password i get “the sign-in method you ‘re trying isn’t allowed error” Hybrid join devices environment.
Hi Jose,
Have you seen the documented limitations: https://learn.microsoft.com/en-us/azure/active-directory/authentication/howto-sspr-windows#general-limitations?
Regards, Peter
Hi there!
Just to let you know that the way to get the custom profile is a bit different now. You have to go to Devices -> Configuration Profiles and make a new one there. And then take “Template” and take “Custom”.
Thank you for that Pieterjan.
Regards, Peter
Hey! everything back end is configured already, have tested SSPR on webbased site
1 issue remaining… getting the stupid reset password on windows login
I have set the correct registry setting what else could it be?
only thing here https://learn.microsoft.com/en-us/azure/active-directory/authentication/howto-sspr-windows
would be that we do use RADIUS for the option to connect using windows creds to our WIFI but other than that everything else is not conflicting can you help?
Hi Mitchell,
Can you provide some more details about your configuration?
Regards, Peter
So i Received a PowerShell script from Microsoft called SsprDiagnosticsTool.ps1 ran it had to use it like so:
Set-ExecutionPolicy -ExecutionPolicy bypass -Scope process
powershell -noexit C:\Users\Owner\Desktop\Scripts\SsprDiagnosticsTool.ps1
and it gave me these results:
WARNING: Script is not running as NT AUTHORITY\SYSTEM. Results may not be accurate
WARNING: Unrecognized Credential Provider found. Some 3rd party Credential Providers may prevent SSPR from working.
Name : OnexCredentialProvider
Path : HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Authentication\Credential
Providers\{07AA0886-CC8D-4e19-A410-1C75AF686E62}
WARNING: Unrecognized Credential Provider found. Some 3rd party Credential Providers may prevent SSPR from working.
Name : OnexPlapSmartcardCredentialProvider
Path : HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Authentication\Credential
Providers\{33c86cd6-705f-4ba1-9adb-67070b837775}
WARNING: Current device is neither AAD-Joined nor Hybrid-Joined. This is a requirement for SSPR from the logon screen
WARNING: 3 issue(s) found that may prevent SSPR on the logon screen from working!
any info on the credential providers?
Hi Mitchell,
It sounds like you’re using a custom credential provider (Onex) on your device.
Regards, Peter
Actually Microsoft told me not to worry about those 2 credential providers the main issue being that my device is not Azure Hybrid AD Joined only registered
Thank you for the update Mitchell.
It’s indeed correct that the device must be joined.
Regards, Peter
The article is superior to all other non MS documentation – kudos to you.
Two remaining uncertainties I still face (meanwhile it is fall 2023 and MS Authenticator has been added as a MFA method)
MS Authenticator App can be unlocked by lazy employees (app lock) provided we aim for MAM going FWD and not MDM (because in scope are only employee personal mobiles) – The same lazy employee may even leave his or her mobile device unlocked forever (no pin/Bio gesture set) – It sounds far fetched but I cannot wholly exclude it as a risk.
Official MS documentation states that a second method of MFA (which is basically your only real trustworthy factor – the UPN of an employee can be all to easily guessed ) — can be requested. Say I want to send an email to the private email address of the user, as second method next to the MS Authenticator App . Will it be a real second method – I.e. I need to provide correct code generated by MS Authenticator App provide code sent by email – or…. is the code sent by email just a fallback should my MS Authenticator not be available ?
Second challenge is more related to keep line of sight to the on-prem DC for home workers – with our current always-on VPN solution there seems to be a glitch in Start Before Logon (unable to activate WiFi in time) – not necessarily related to SSPR but more a gneric question whether more astute solutions are recommendable (domainless in Win11 for instance)
Kind regards
Rik
Hi Rik,
You can set Number of methods required to reset to a level appropriate to your organization. One requires the least friction, while two may increase your security posture (quote from the docs).
Regards, Peter