This week I’m going for an end-user experience focused blog post. This week is all about the PIN reset option on the login screen. In other words, the I forgot my PIN option. Starting with Windows 10, version 1709, it’s now possible to enable the I forgot my PIN option from the login screen. When using Windows Hello for Business, which can be configured during the Windows enrollment, by using Microsoft Intune, the PIN is the fallback mechanism when it’s not possible to authenticate with biometrics. In other words, the PIN is really important.
In this post I’ll provide the required configuration to provide the user with the I forgot my PIN option from the login screen. I’ll do that by assuming that the user can use the Windows Hello for Business PIN recovery service to reset their PIN. I’ll end this post by looking at the end-user experience.
Configuration
Now let’s start by having a look at the required configuration to enable the I forgot my PIN option from the login screen. As the configuration of the actual settings requires the tenant ID, I divided the configuration into three steps. The first step is to find and introduce the required setting, the second step is to get the tenant ID and the third step is to use the tenant ID in the actual configuration.
Step 1: Get the required setting
The first step is to get and introduce the required setting. The PIN-related settings are part of the Windows Hello for Business settings, which can be configured by using the PassportForWork CSP. Starting with Windows 10, version 1703, that CSP contains the EnablePinRecovery node. With Windows 10, version 1703, this setting can be used to enable the I forgot my PIN option from the Settings panel and starting with Windows 10, version 1709, this setting can also be used to enable the I forgot my PIN option from the login screen.
This settings has a boolean value that enables a user to change their PIN by using the Windows Hello for Business PIN recovery service. This cloud service encrypts a recovery secret, which is stored locally on the client, and can be decrypted only by the cloud service. The default value of this setting is false. Once the administrator enables this setting, the PIN recovery secret will be stored on the device and the user can change their PIN if needed.
Step 2: Get the tenant ID
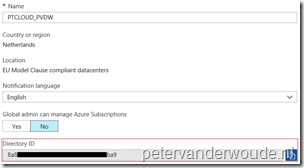
The second step is to get the tenant ID. This is super simple these days, but, as I’ve never provided the actual steps, I thought it would be smart to publish them once. To get the tenant ID, simply follow the two steps below.
| 1 | Open the Azure portal and navigate to Azure Active Directory > Properties; |
| 2 |
Note: Just to be clear, this should be used in the OMA-URI instead of {tenantID}. |
Step 3: Configure the required setting
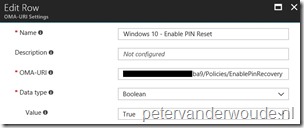
The third step is to configure the required setting to enable the I forgot my PIN option from the login screen. In other words, the third step is to configure a device configuration profile with at least a custom OMA-URI setting. The following three steps walk through the creation of a new device configuration profile, including the required OMA-URI setting. After that simply assign the created profile to a user group.
| 1 | Open the Azure portal and navigate to Intune > Device configuration > Profiles; |
| 2 | On the Devices configuration – Profiles blade, click Create profile to open the Create profile blade; |
| 3a |
On the Create profile blade, provide the following information and click Create;
|
| 3b |
|
End-user experience
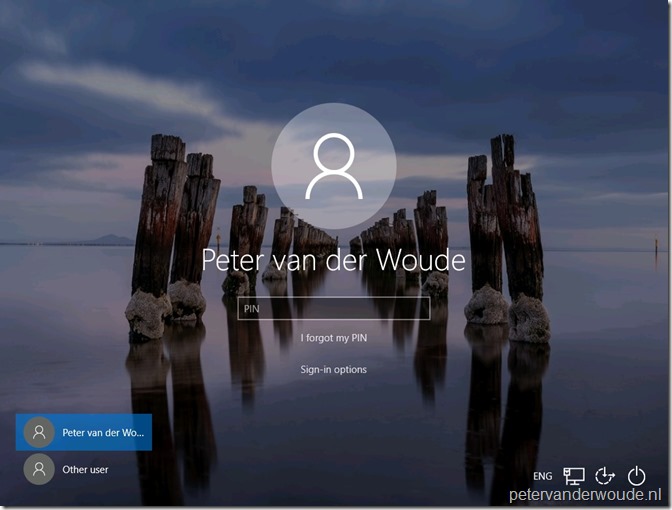
Now let’s walk through the end-user experience. On the login screen a new option is available when selecting PIN as the sign-in option, the I forgot my PIN option.
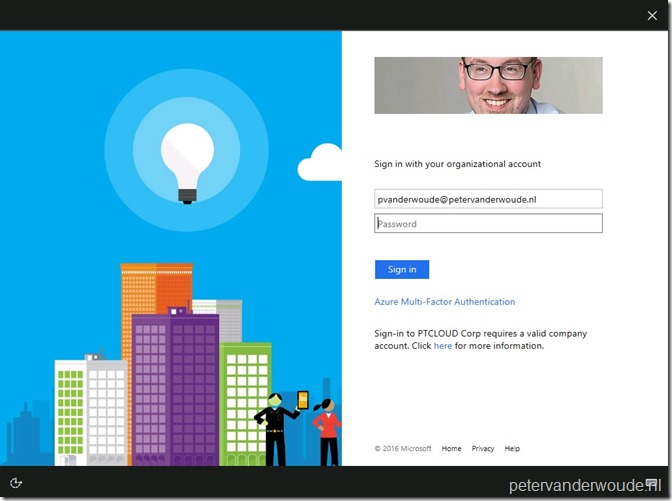
When the user selects I forgot my PIN, the user will be redirected to the login experience of the identity provider. In my case ADFS.
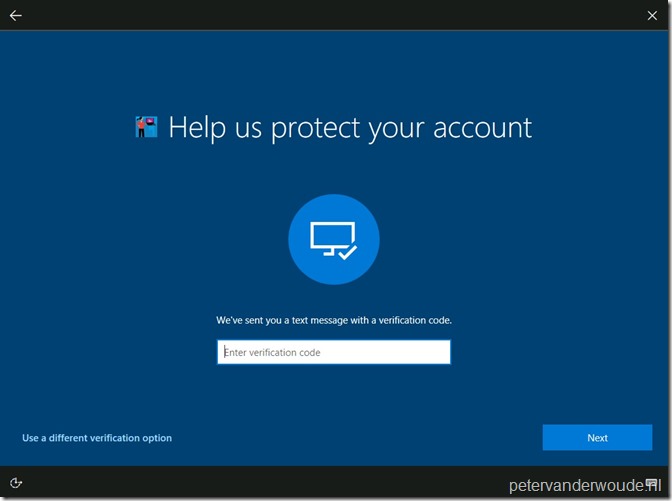
When the user provides a password and clicks on Sign-in, the user needs to provide an additional verification option, on an Azure AD branded page. In my case a text message.
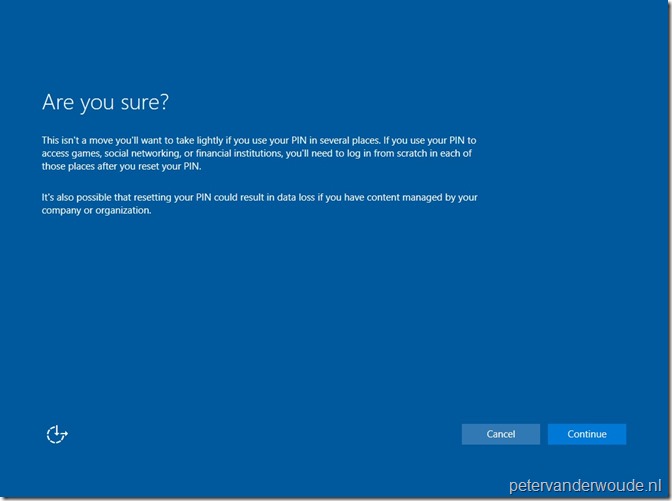
When the user provides the additional verification and clicks on Next, the user will be provided with an additional notification to make sure that the user is aware of the impact.
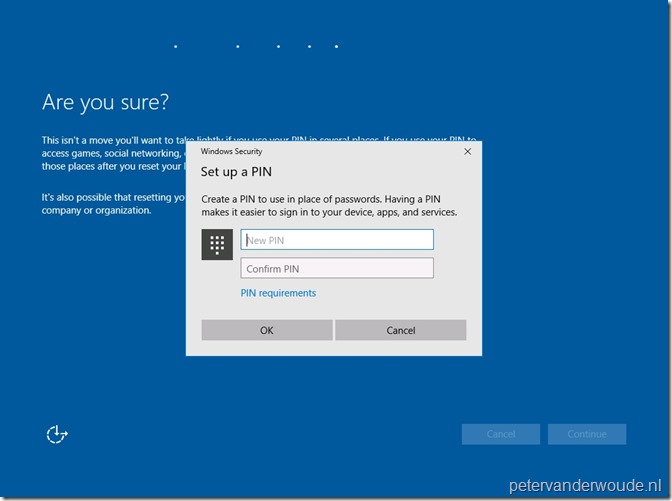
When the user accept the impact of resetting the PIN and clicks Continue, the user will be provided with a dialog box to create a new PIN. Also, the user can click on PIN requirements to view the requirements for the new PIN. In my case it will show the Windows Hello for Business settings as configured in the Windows enrollment section of Microsoft Intune.
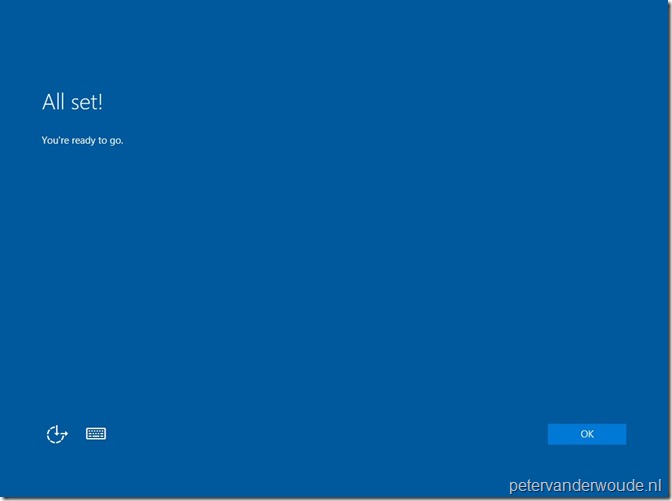
When the user provided a new PIN and clicks OK, the user will be provided with the message that it’s all set. When the user than clicks on OK, the user will be redirected to the login screen.
More information
For more information about Windows 10 and the (remote) PIN reset functionality, please refer to the following articles:
- Windows Hello for Business Features – PIN reset: https://docs.microsoft.com/en-us/windows/access-protection/hello-for-business/hello-features#pin-reset
- Windows 10 PIN reset: https://docs.microsoft.com/en-us/intune/device-windows-pin-reset
Thanks for the detailed information!
Good to know that this option is available.
Not sure if its very helpful since if a user forgets their PIN they can still login with their password and rest the PIN.
Thanks Egert. It’s all about making it easier for the user. With the abilities of Windows Hello, it’s getting easy to forget passwords (and PINs).
I did these steps. Thanks for the walk through. The pin reset still doesn’t work. It still says its not available in my organization.
My org uses a Hybrid key trust without ADFS, we use hash password sync. Users are licensed with Azure MFA through 365. We do not have an AAD Premium enabled if that matters for this.
Hi Micah,
Which version of Windows 10 are those devices running?
Regards, Peter
Ver 1709.
Side note: Some users did not have the option to check the box to use letters. They had to create a pin using numbers only. I had to remove PIN complexity from group policy so they could log in with their pins.
In AAD Hello is configured to not configured (it’s configured through GP)
Thanks,
Micah
None of the computers in AAD are managed by intune. It shows none under MDM except for a new user. We just setup a new user and provisioned a PIN and this new user’s workstation is showing a being managed by Intune and compliant. I don’t know why this one user’s computer is compliant. This computer/user is also the only one showing it is assigned to the PIN Reset Profile I created using this guide. Unfortunately PIN reset is not working even on this new user. So I think I have two problems.
1. Workstations are not registering to Intune
2. Even the one registered to Intune does not allow PIN reset from login screen.
Hi Micah,
What’s the error that you get on the Intune registered device?
Peter
Is it possible to disable login via password and use PIN only.
Why would you want that? It’s good to have a fallback..
Microsoft is telling me that the PIN Reset above the lock screen only works with 10 Enterprise and not Pro. What version did you get it to run on? We have Pro 1803.
Hi Micah,
I used Windows 10 Enterprise.
Regards, Peter
Hi Peter,
Thank you for sharing this amazing topic on Hello For Business.
I do have a question because I’m going crazy with a simple thing and I assume I should miss something big.
I’ve set Hello For Business on Hybrid AD-Joined laptops in a Key trust model with Azure Device Registration. Everything is working fine, HfB is enrolled and I can log into the session with the factors that I have configured in Group A and Group B policies.
One stupid thing is that is still possible to log into the session with AD password. I tried several things like disable password into Credential Providers and/or Enforce “Smart Card” logon GPO on the machine (not the user). Both solution works as it’s not possible to log with the password anymore but I have bad side effects like:
– not possible to use Forget PIN (password is requested and not accepted)
– not possible to log another account on the device as HfB is not enrolled yet for the new account
What is your recommendation to avoid this kind of situation ? Do you know if there is a setting that allows password only if HfB is not enrolled for the user but disallow it after ?
Thank you very much in advance for your kind help
Best Regards
Quan
Hi Quan,
The challenge is that it’s Windows functionality and when you take it away, it’s away everywhere. Including RDP for example.
Regards, Peter