This week another post about (easily) predeclaring corporate-owned devices. Starting next week, I’ll introduce some new feature of Configuration Manager 1706. This post is basically a part 2 of my post about predeclaring corporate-owned devices. The big difference, this time it’s about Microsoft Intune standalone were this feature is just recently introduced. Predeclaring corporate-owned devices is an easy method to differentiate between corporate and personal devices and immediately tag those devices. I’ll start this post with a little bit information, followed by the configuration. I’ll end this post with the administrator experience.
Information
Let’s start with some information about predeclaring corporate-owned devices. An Intune administrator can now create and import a comma-separated values (.csv) file that lists International Mobile Equipment Identifier (IMEI) numbers or serial numbers. Intune uses these identifiers to set Ownership as Corporate. IMEI numbers can be declared for all supported platforms and serial numbers can be declared for iOS and Android devices only. Each IMEI or serial number can have details specified in the csv file for administrative purposes.
Configuration
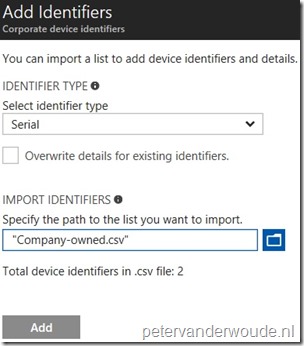
Before I’m going to walk through the required configuration steps, it’s good to provide some information about the format of the csv files that can be used. To create the list, create a two-column csv list without a header. Add the IMEI or serial numbers in the left column, and the device details in the right column. A csv file can only contain or IMEI numbers, or serial numbers. The device details are limited to 128 characters and are for administrative use only. Details aren’t displayed on the device. The current limit is 500 rows per csv file. An example for serial numbers would look like the following.
RF8xxxxRZP,Company-owned Android device
F9FxxxxxxHK9,Company-owned iOS device
With this information and the example, I’ll now walk through the configuration steps.
| 1 | Open the Azure portal and navigate to Intune > Device enrollment > Corporate device identifiers; |
| 2 | On the Corporate device identifiers blade, select Add to open the Add identifiers blade; |
| 3 |
Note: When importing IMEI numbers, simply select IMEI as Identifier type. Also, notice the message below the selected csv file, it already shows the total number of device identifiers that are found within the csv file. |
| 4 |
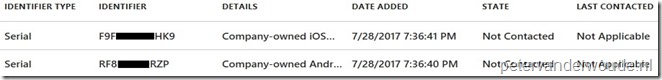
Back on the Device identifiers blade it will now provide an overview of the just imported device identifiers; |
Administrator experience
Let’s end this post with the administrator experience. After a device of the csv file is enrolled, there are a few good places to look in the Azure portal. The first place is Intune > Device enrollment > Corporate device identifiers. This location shows the imported device identifiers and will now also show Enrolled as the STATE of the imported device identifier.
The second place is Intune > Devices > All devices. This location shows all the enrolled devices and now also shows Corporate as OWNERSHIP of the device.
This is the easiest method for an administrator to differentiate between corporate and personal devices. It enables the administrator to target specific actions only to corporate-owned devices and even enables the administrator to create an easy road to blocking personal devices. More about that in a later post. Also, keep in mind that the ownership will not change for already enrolled devices. The corporate identifiers must be imported before the devices are enrolled.
More information
For more information about predeclaring corporate-owned devices, please refer to this article about adding corporate identifiers.

Just wanted to let you know this was a fantastic post that will help our IT quite a bit! Thank you! Looking forward to the “later post” you allude to!
Thank you, Graeme!
Yes, a fantastic post, very helpful. Is it possible to prevent Windows 10 (AAD Joined and managed by Intune). Looks like by default AAD Join is limited on user basis, not the device ownership and conditional access or compliance policies available do not have a way to recognize device ownership.
An Azure AD joined device is by default company-owned. You could try to make a dynamic group in Azure AD, based on the device owner, and use that with your policies.
Hey Peter,
I want to assign a device configuration based on two attibutes. First is it a corporate device (identified by a corporate identifier) and second, who is the person enrolling the device (or more importantly are they a member of x AD Group).
Dynamic Groups cannot process user and device attributes. Have you got any ideas how one could achieve this?
It will help me assign configuration restrictions based on BYOD or CYOD devices without having to resort to Enrollment Categories.
Great blog btw
Hi Ben,
Correct. You cannot combine user and device attributes in a dynamic group. What groups of devices do you have and how are they different from each other?
Regards, Peter
Hi Peter, during enrollment of an iOS device, the user is asked to complete the last 4 characters of the serialnumber. Will adding the device to the corporate device identifiers list skip this step, or is this still needed?
Thanks!
Hi Jan,
I don’t recall ever needing to provide the last 4 characters during a normal enrollment (see also: https://docs.microsoft.com/en-us/intune-user-help/enroll-your-device-in-intune-ios). At what point do you receive that request?
Regards, Peter
How to resolved if its more than 30days and the status still “Not Contacted”. I use to define the Corporate Identifiers using Serial#. Thanks!
Hi Ian,
Not sure what you mean, can provide some more details?
Regards, Peter
Is this becoming deprecated? All newer Android versions are not supported and Windows also not supported. In 2023 what is the use of corporate device identifiers?
Hi Eddy,
It’s still available for all Apple devices and can be useful for predeclaring devices as corporate. But the truth is that the usecases are limited.
Regards, Peter
Why would a device manually added to corporate identifiers and then enrolled by a user never then appear in All Devices?
Hi Craig,
The device should show just like any other device.
Regards, Peter
IOS device enrolled successfully via Company Portal app on phone and shows as enrolled under CDI but still never pulls through to the device overview – any other ideas why that might be?
And the device is successfully receiving policies? If so, don’t you have some filters on the UI that removes the devices from the UI?
Regards, Peter